AI-Powered Risk Prioritization
Our AI‑Powered Prioritization Engine generates policy and asset-based risk scores by ingesting data from vulnerability scanners, CSPM, application security, and endpoint protection tools to correlate risks and map them to your business applications.
Leverage Generative AI to drive prioritization
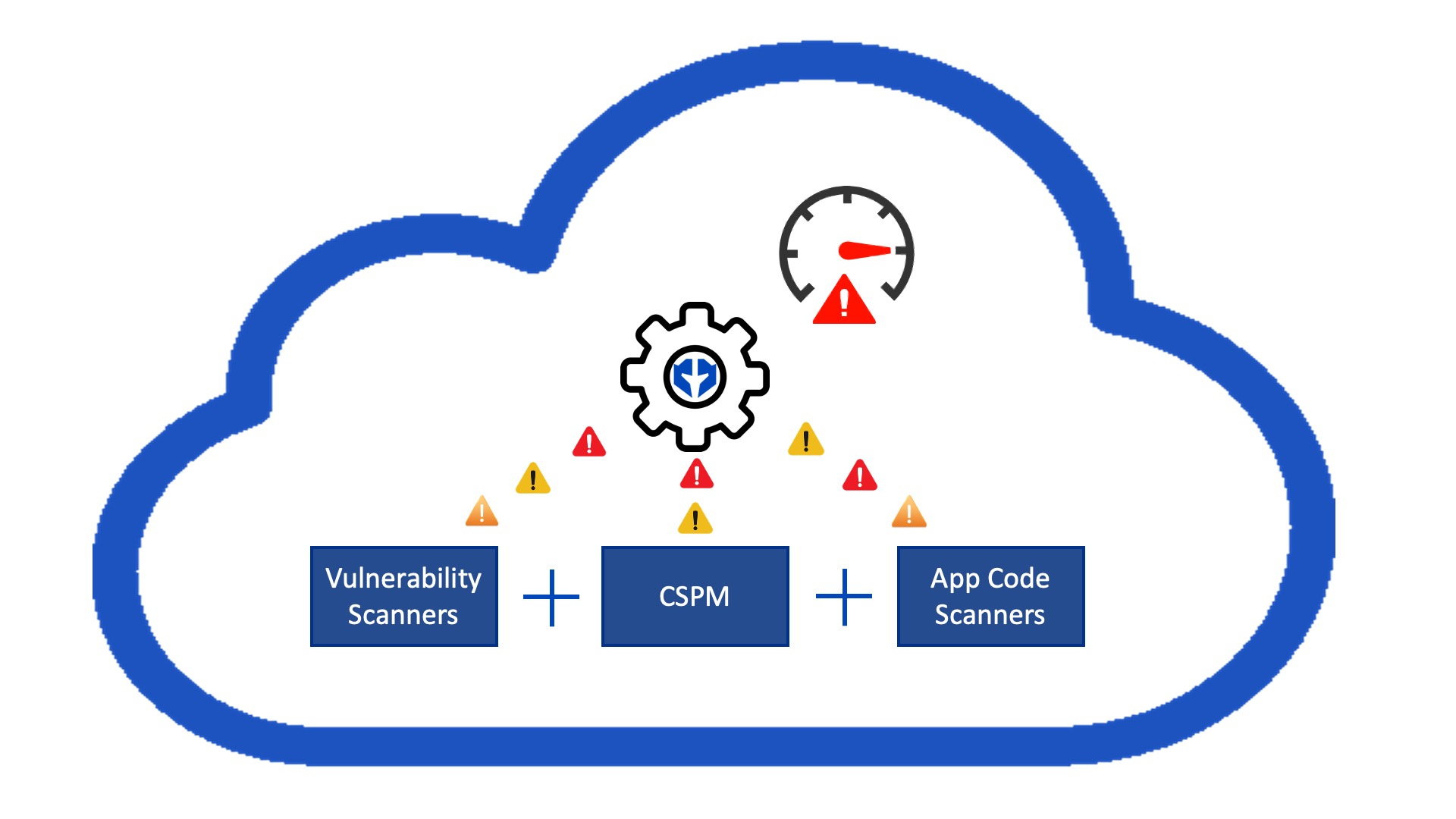
Reduce the Noise
Stop wasting time investigating every individual alert. We risk score and contextualize findings across your security ecosystem to enhance the prioritization of vulnerabilities.
35% of security alerts are false positives
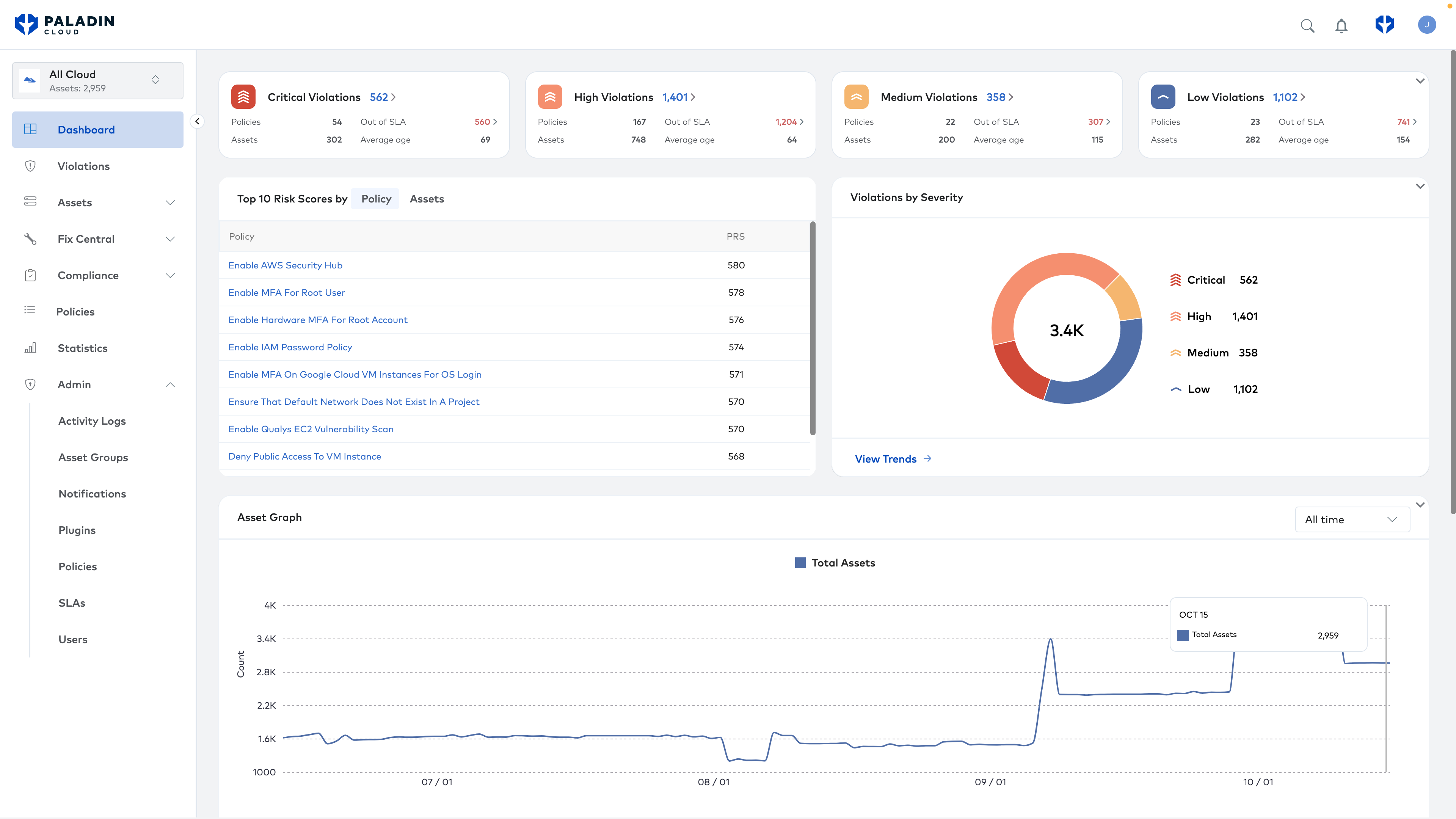
Visualize your attack surface
Create a full asset inventory to identify and track your cyber assets. Map your attack surface in real time. Drill down to detailed asset information. Zoom out to a unified view of your attack surface.
Reduce your attack surface by up to 30%
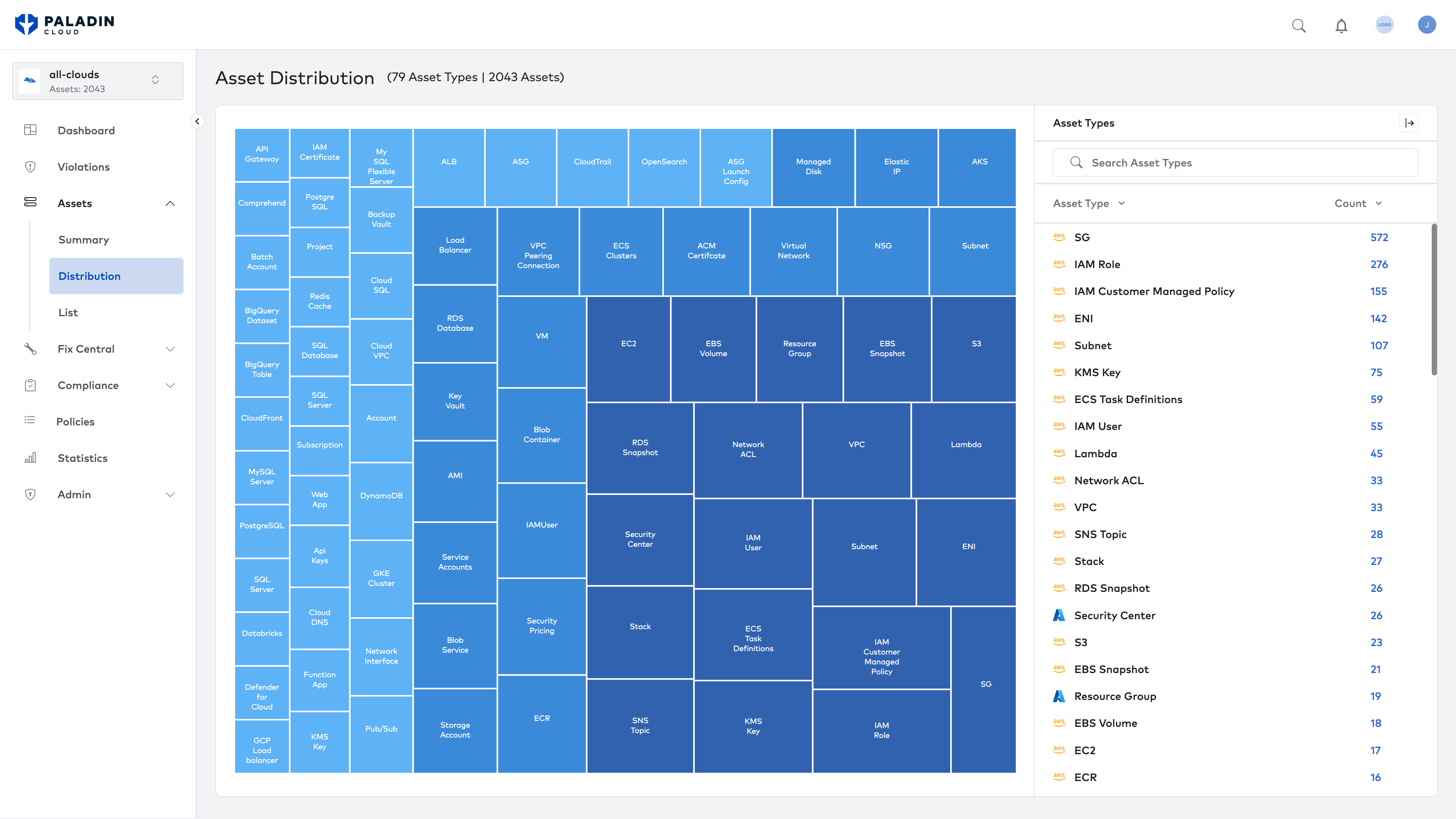
Eliminate gaps in coverage
Verify the implementation of security controls across your cloud environments. Identify security risks and gaps in coverage. Ensure security tools provide their intended protection.
Increase your security hygiene by up to 50%
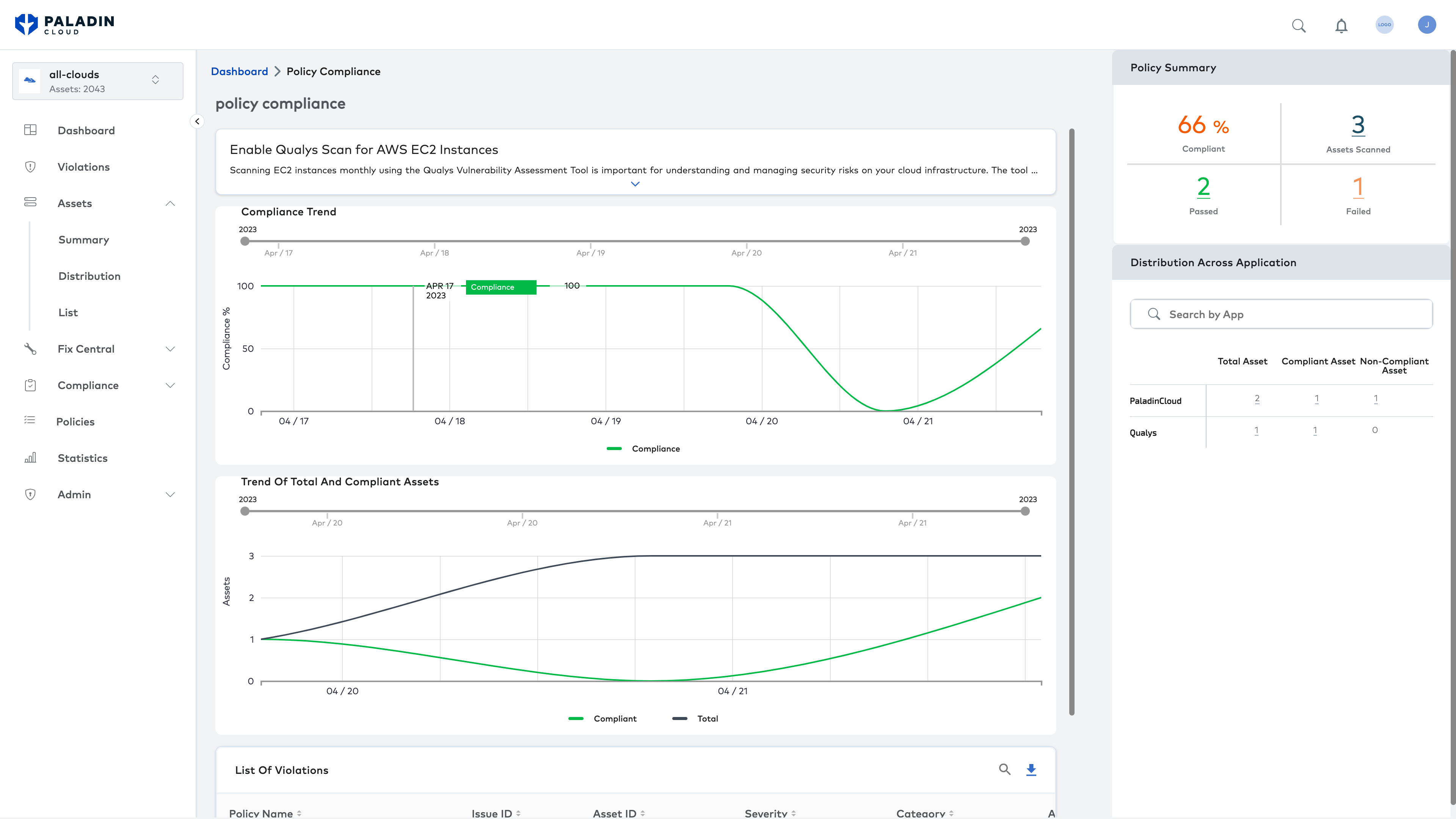
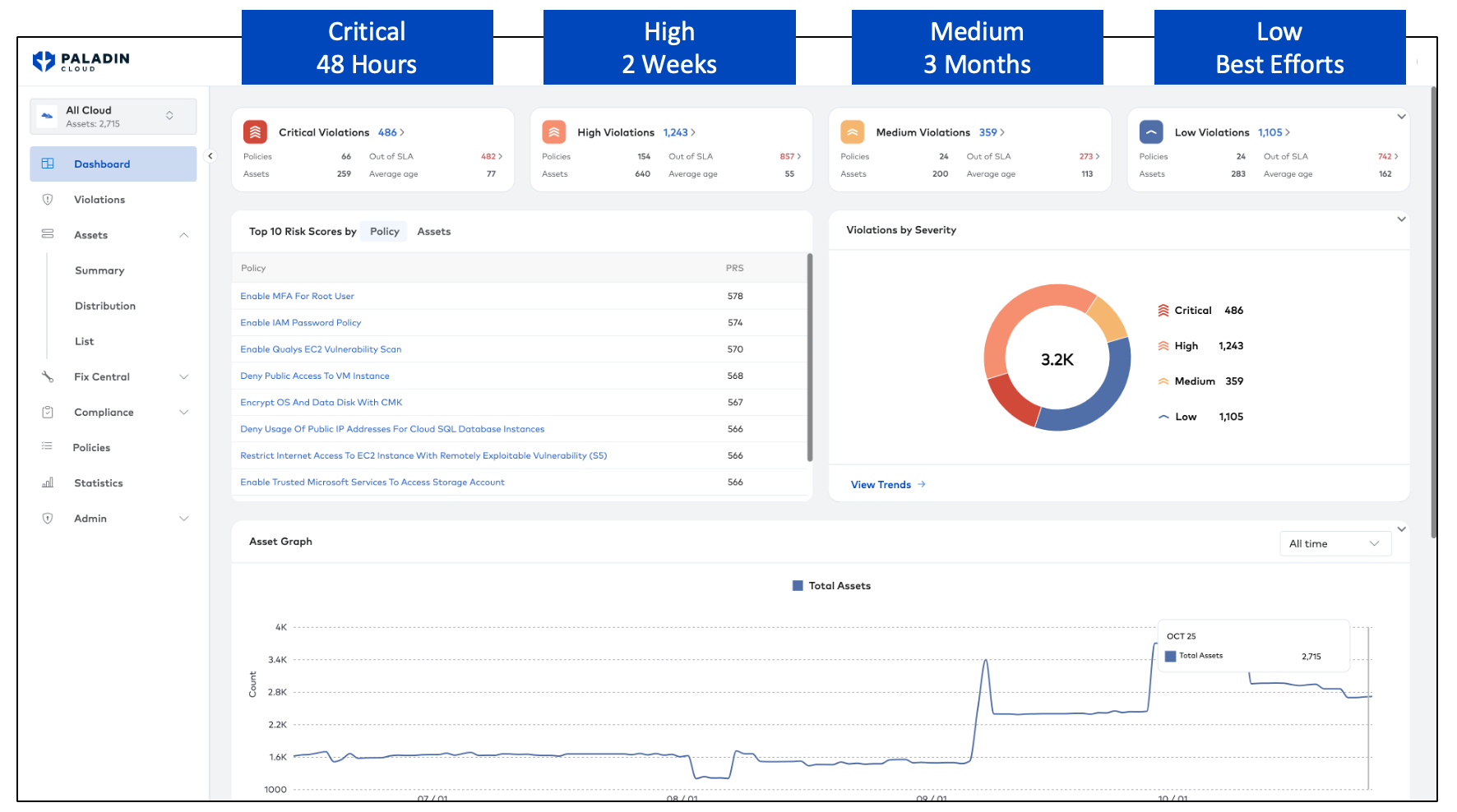
Implement SLAs to reduce resolution times
Assign company SLAs to severity-based categorization of vulnerabilities and misconfigurations. Reduce the time to remediate by specifying resolution times by severity level. Monitor compliance with organizational SLAs across departments.
Decrease your exposure time to security risks
Reduce time to remediate security risks
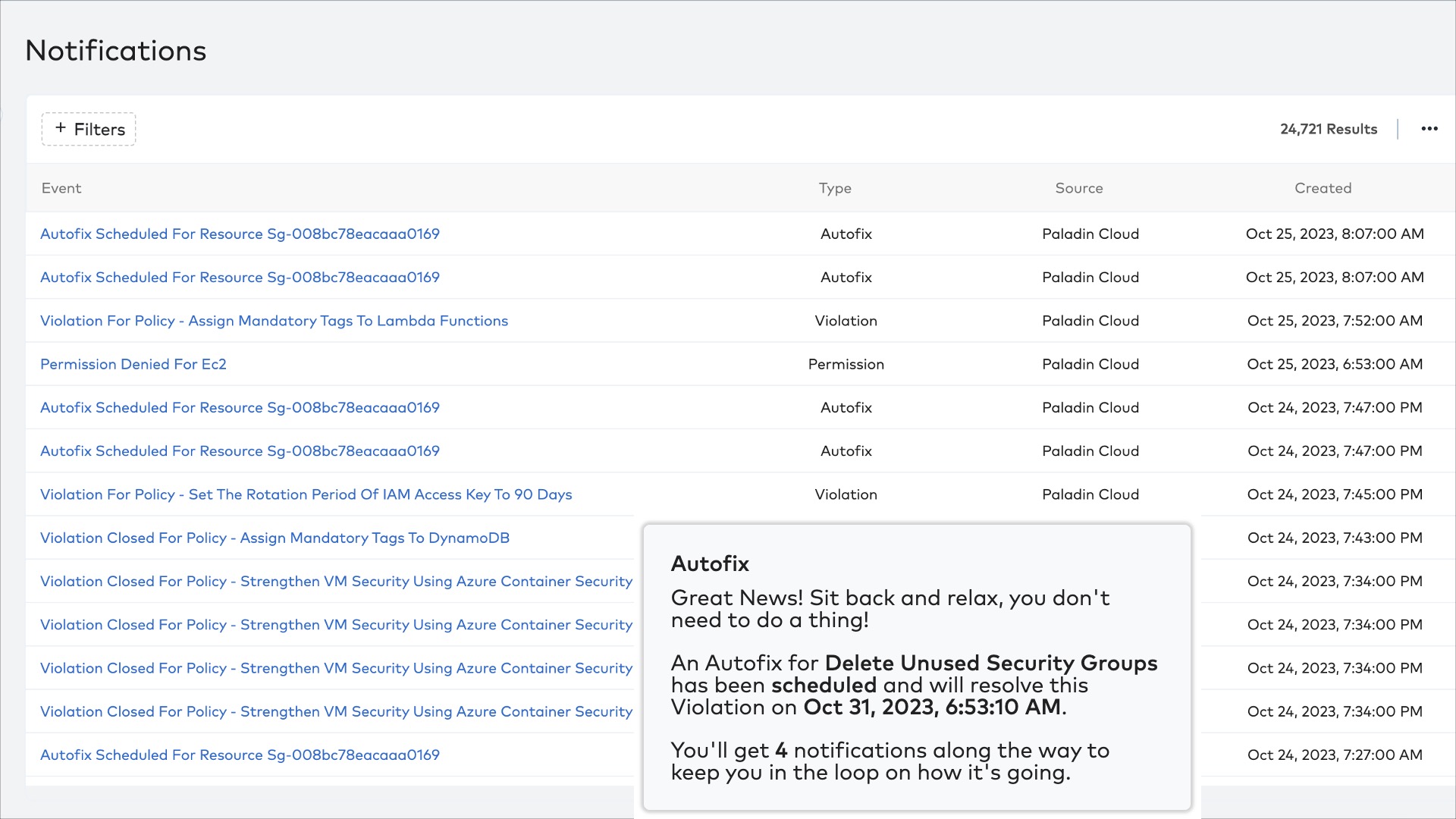
Automate workflow and remediation with Jira multi-targeted notifications, one-click fixes, and auto-fixes. Health notifications give you one place to view recommendations and map out a plan to take corrective action.
Save time with automated ticketing workflows
By the numbers
Prioritize top security risks
Reduce your risk profile by up to 30%
Reduce alert fatigue
Reduce the noise by up to 50%
Remediate issues faster
Improve resolution times by up to 25%
Lower operational costs
Save up to 25% of your resources
Prioritization Engine for Cloud Security
Unify findings across tools to protect your cloud assets
Compute
Networking
Storage
Database
Identity
Logging
Monitoring
Kubernetes
Get a Demo or
Free Prioritization Assessment
