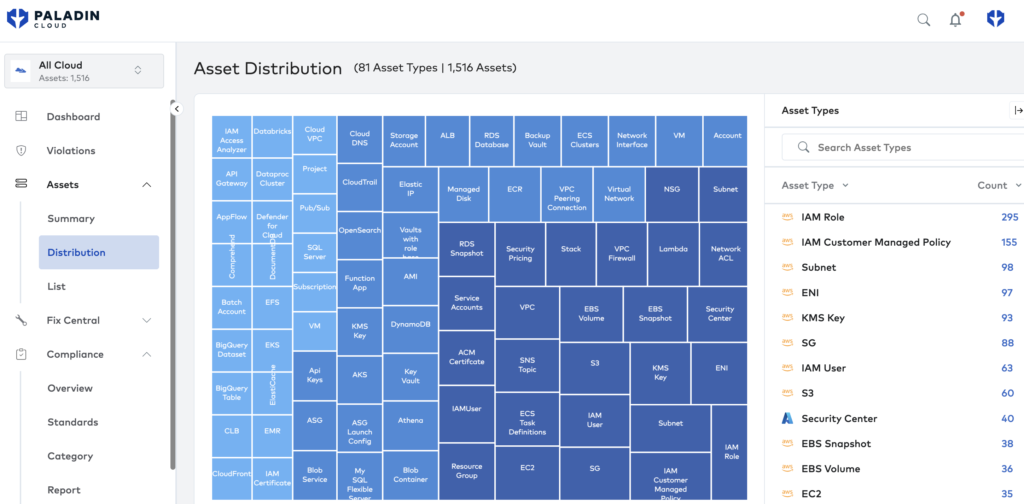
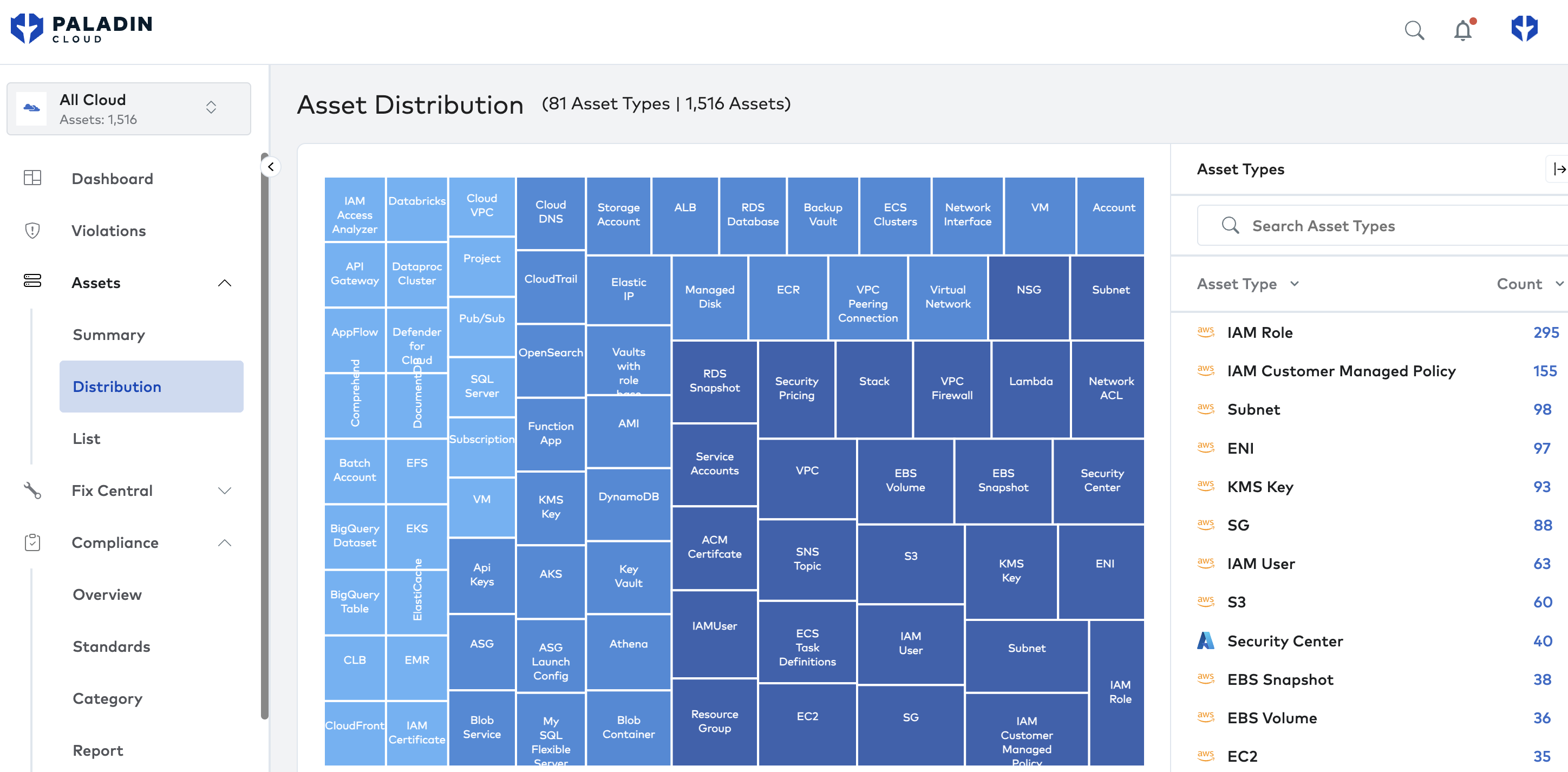
CAASM is more than just another acronym; at its core, Cyber Asset Attack Surface Management is about a holistic approach to your attack surface. Without centralized visibility into your assets, attackers can exploit blind spots to access systems and data through unprotected routes.
Why Attack Surface Management Matters
Over the last decade, many companies have undergone a significant transformation of their information technology (IT) landscape. With new technologies and concepts such as cloud infrastructure, digital identities, and software-as-a-service (SaaS) solutions, traditional asset management tools have become increasingly inadequate to manage and control these new digital assets.
Cloud infrastructure has revolutionized how businesses store, manage, and deliver computing resources. Companies now store their data and applications on virtual servers hosted in the cloud. This has made it easier for companies to scale their operations and reduce the costs associated with maintaining physical hardware. That scale has also meant that organizations often need help understanding the full scope of their cloud footprint as it spans multiple clouds, services, and accounts.
With the proliferation of online services and the increasing use of social media, digital identity management has become a critical issue for businesses. Traditional asset management tools are not equipped to manage these identities, which can lead to security breaches and other issues.
Finally, software-as-a-service (SaaS) solutions have become increasingly popular in recent years. SaaS solutions provide businesses access to software applications and tools hosted in the cloud. This eliminates the need for businesses to purchase and maintain their software and hardware, which can be costly and time-consuming. However, this interconnected nature means security teams must also understand the SaaS vendor’s access and permissions. Otherwise, attackers may exploit this 3rd party source to access company assets.