In today’s rapidly evolving cloud ecosystem, achieving cohesive and comprehensive security is more essential than ever.
Paladin Cloud and Red Hat Advanced Cluster Security represent a holistic answer to this challenge. Together, they bridge the gap between multi and hybrid cloud environments across infrastructure and Kubernetes, delivering a unified platform tailored to managing cloud security risks effectively. By combining the two platforms, DevOps and security teams are empowered to visualize, identify, prioritize, and address vulnerabilities and misconfigurations across their entire stack.
Benefits of a Unified Approach
Red Hat Advanced Cluster Security Cloud Service delivers consistent security coverage across Kubernetes environments. This includes managed Kubernetes offerings like Amazon EKS, Microsoft AKS, Google GKE services, and of course, Red Hat OpenShift. Yet, the infrastructure supporting these containers requires protection too. Paladin Cloud, with its Cloud Security Posture Management (CSPM) module, fills the gap, safeguarding the infrastructure where Kubernetes operates.
Paladin Cloud begins by identifying your multi and hybrid cloud assets, including your Kubernetes deployments, through the Red Hat Advanced Cluster Security plugin. Findings from Paladin Cloud, Red Hat Advanced Cluster Security, and other security tools are risk-scored and then correlated to identify top risks. Paladin Cloud’s prioritization engine focuses your team on the most critical vulnerabilities and misconfigurations. Reduce the time to remediate with SLA management, triage support, automated workflows, and auto-fixes.
By vigilantly monitoring clouds and the infrastructure Kubernetes runs on, Paladin Cloud complements Red Hat Advanced Cluster Security, helping organizations take a comprehensive approach to security. This collaboration is more than the sum of its parts—it represents a consolidated security approach that provides organizations with asset discovery, improved coverage, reduced alert noise, and a consolidated platform to prioritize key risks to drive swift remediation.
Connecting Red Hat Advanced Cluster Security with Paladin Cloud
Connecting is simple and secure. Here’s a step-by-step guide:
1. Prerequisites
- To set up a connection between these security platforms, you will need to have a Paladin Cloud instance and be running Red Hat Advanced Cluster Security.
- Next, you need two pieces of data so they can talk to one another. This is your Red Hat Advanced Cluster Security instance ID & an Authentication Token. The ID lets Paladin Cloud know where to pull the data from, and the authentication token makes sure Paladin Cloud has the needed access.
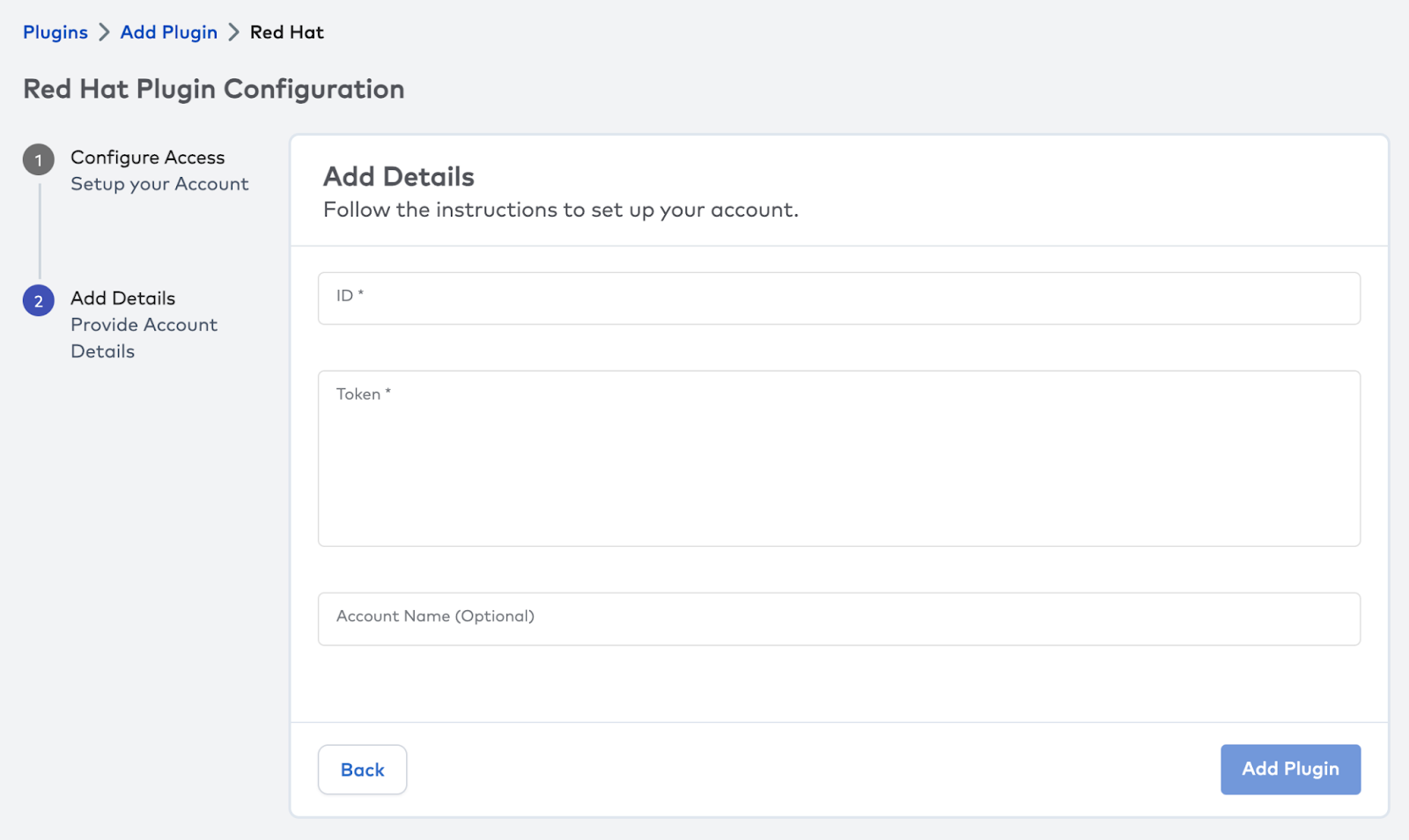
- In Paladin Cloud, go to the plugin page under Admin (You will need Admin permissions)
- Choose Add Plugin and select the Red Hat Advanced Cluster Security plugin.
- This will give you the latest instructions to configure the account.
2. Retrieve your ACS instance ID
- Log in to the Red Hat Console.
- Access the ACS Instance page by selecting `Advanced Security Cluster` in the side menu. Click on the ACS instance you want to link with Paladin Cloud.
- Copy the `ID` from the `Instance Details` card inside the chosen Red Hat Advanced Cluster Security instance.
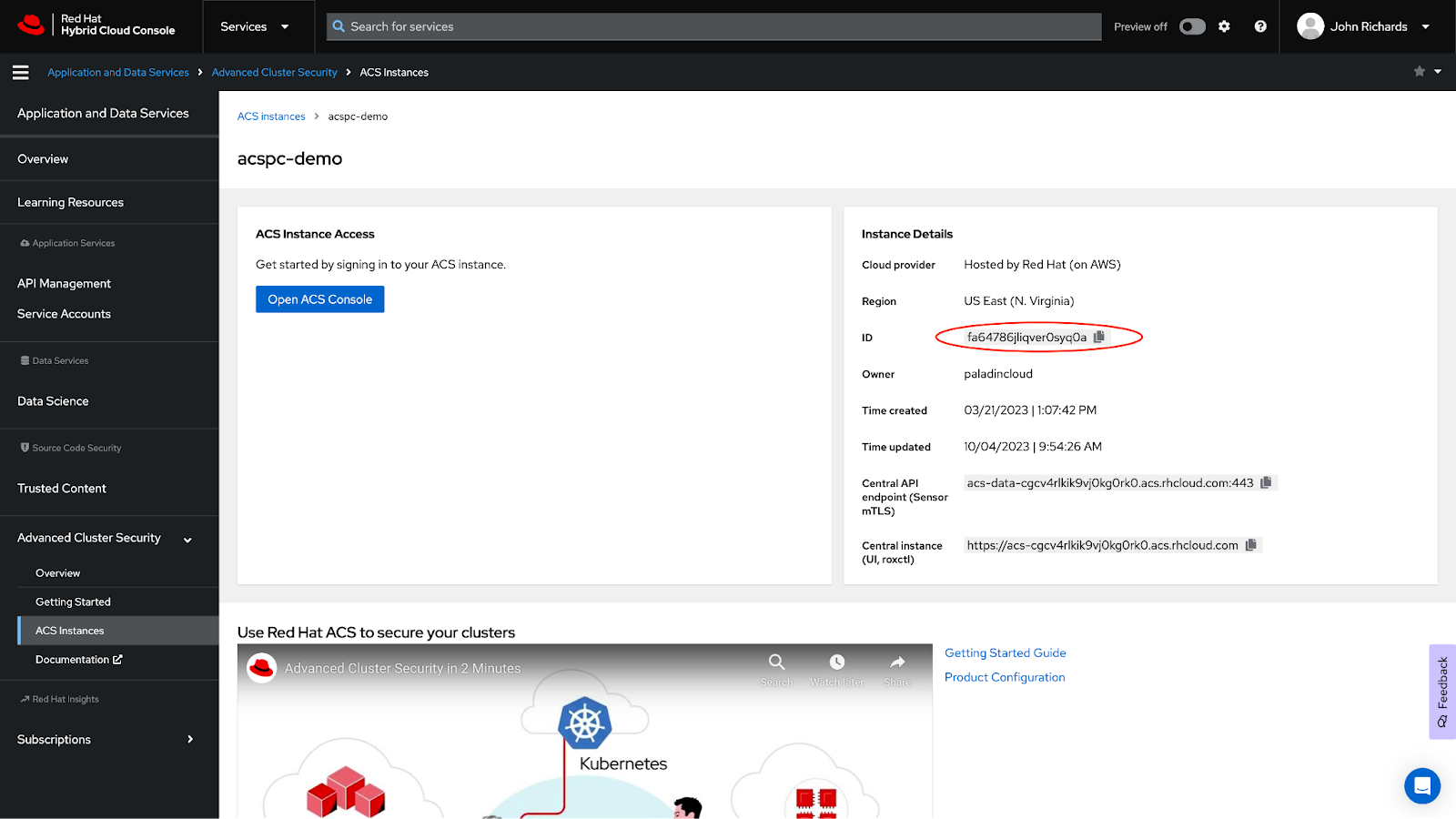
- Switch to the Paladin Cloud application, and hit next to go to the Add Details page. Paste in the copied `ID` into the `ID Field`.
3. Setup an authentication token
- Return to the Red Hat Advanced Cluster Security Instance page and click the “Open ACS Console” button.
- Access Platform Configuration from the side menu and choose the ‘Integrations’ option.
- Scroll down to the ‘Authentication Tokens’ section.

- Select ‘API Token’. You’ll be taken to the ‘Integration API Tokens’ page, which lists previously generated tokens (if any).
- Click the ‘Generate Token’ button.
- Name the token and choose the Analyst role.
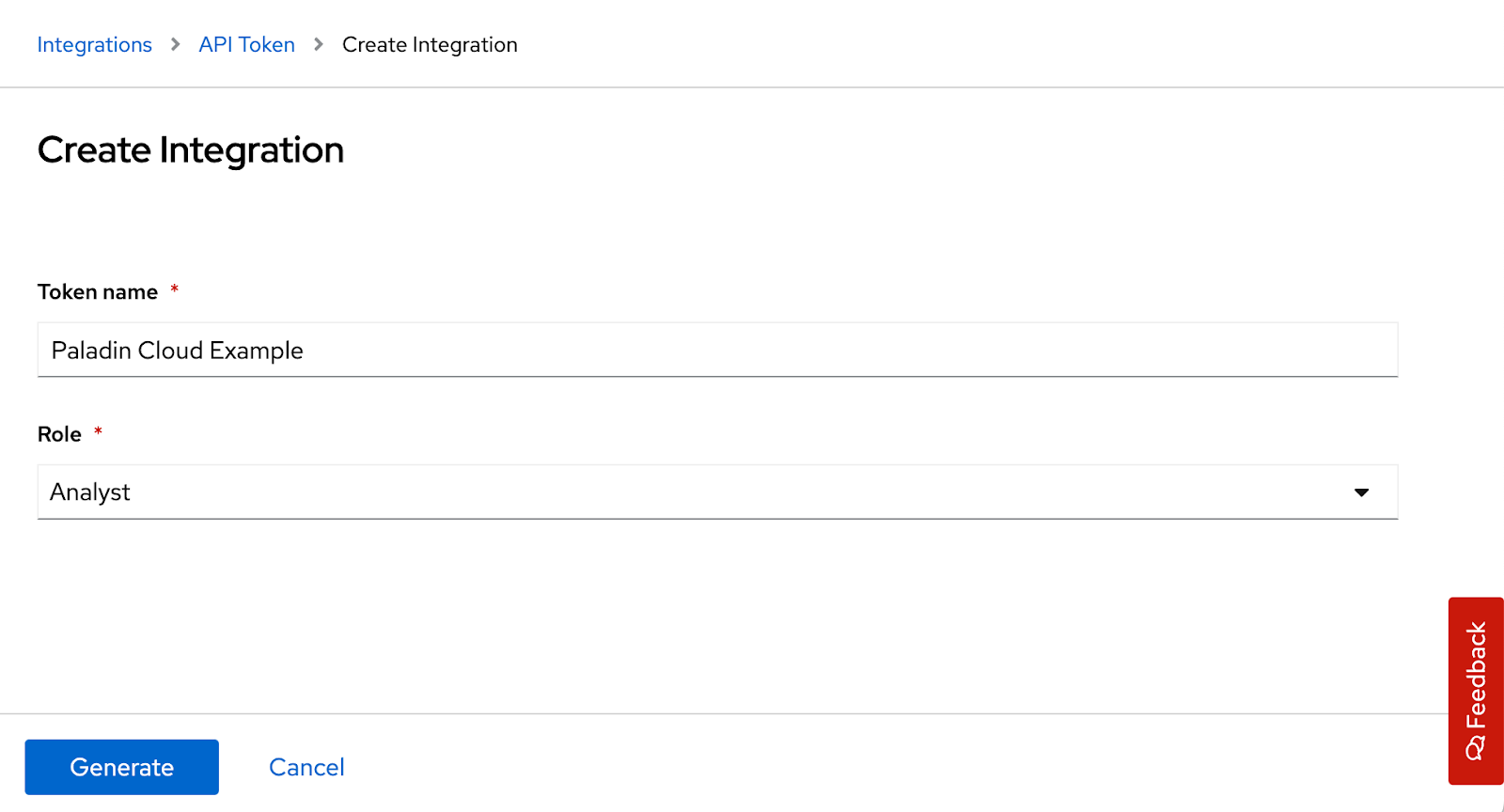
- Copy and paste the generated token into the token input field within the Red Hat Plugin in the Paladin Cloud application.
IMPORTANT: Be sure to store the copied token safely. Once generated, it won’t be visible again for security reasons.
4. Validate the configuration
- Hit the ‘Validate’ button to confirm the setup was successful. If so, this will add the plugin to Paladin Cloud.
- If you get a success message, you should see data begin to populate within 30 minutes.
- Go to the Asset Group Selector and choose Red Hat to see a dashboard on your OpenShift assets.
- You can view your Kubernetes deployments and the risks Red Hat Advanced Cluster Security has identified.
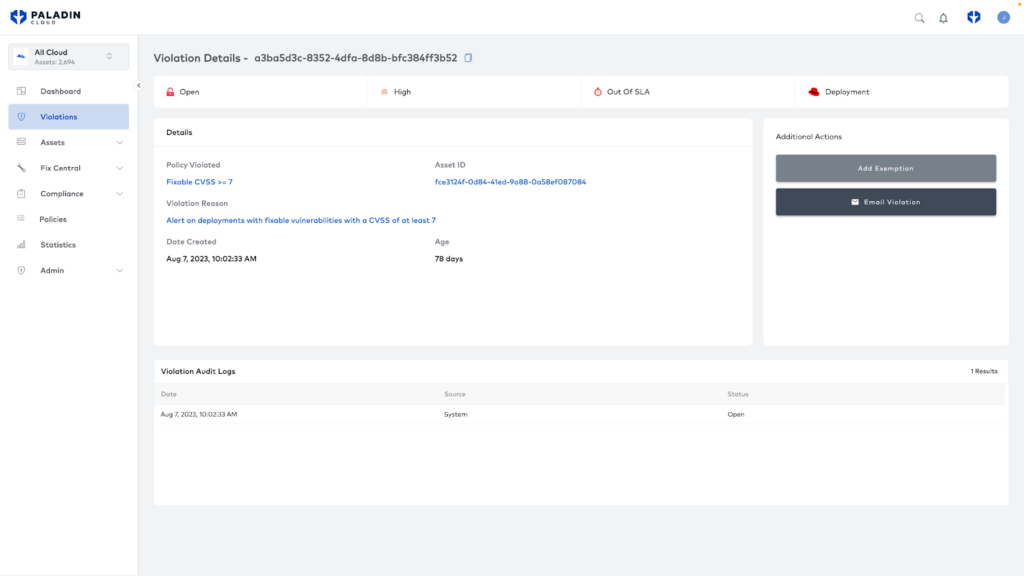
- For any Advanced Cluster Security violations, you can click through the corresponding link to go directly to that finding in Advanced Cluster Security for further details on risk and steps on remediation.
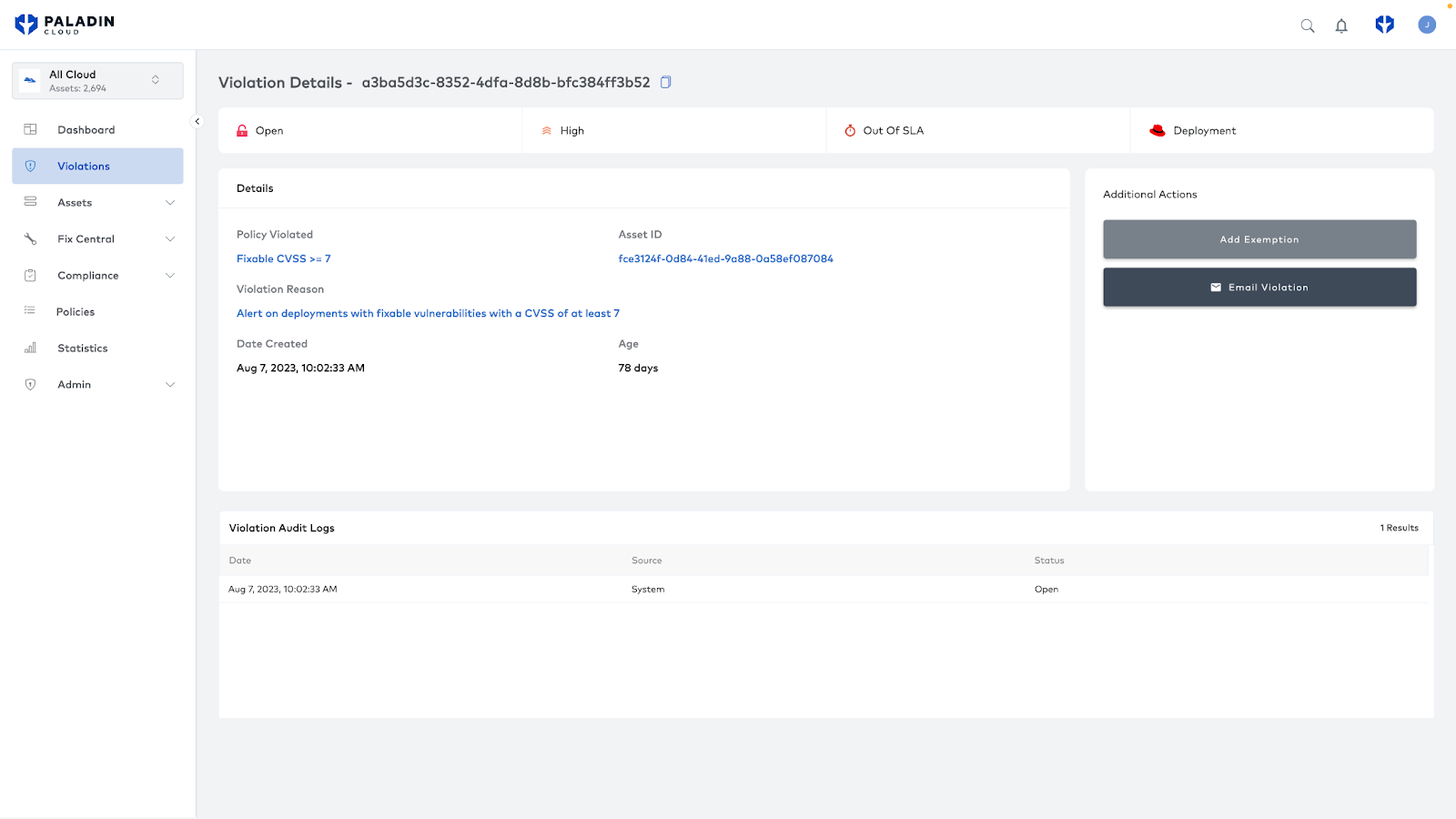
What’s Next?
The provided Red Hat dashboard lets you view these assets and violations in isolation, but it is also possible to integrate these findings alongside your other assets and risks. You can view all your security findings in one place by creating a shared view across multi-cloud and Red Hat OpenShift assets. Here, you can holistically view your overall security profile.
Keep an eye out for further collaborative features in both Paladin Cloud and Red Hat Advanced Cluster Security coming soon.
Conclusion: Maximizing Cloud Security
Connecting Paladin Cloud with Red Hat Advanced Cluster Security delivers enhanced protection. It consolidates findings, streamlines remediation efforts, and bolsters an organization’s security posture against threats.
To discover more about Paladin Cloud’s capabilities and how it complements Red Hat solutions, Get a Paladin Cloud Demo. For insights into Red Hat Advanced Cluster Security, visit Red Hat’s official page.