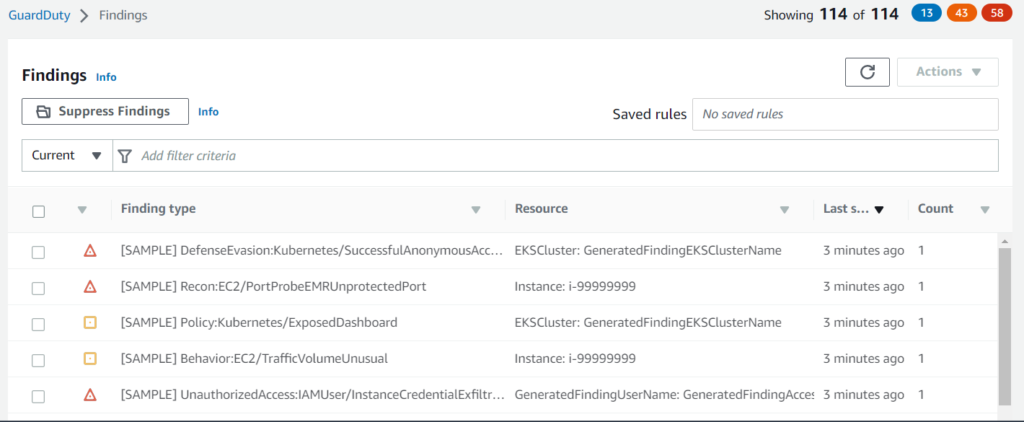
AWS GuardDuty is a service that continuously monitors an AWS account’s security and detects threats using data from multiple sources.
In this article, we’ll look at the data sources used by GuardDuty, the protections it provides, the types of findings it generates, and best practices for using the service.
Data Sources
The first thing we need to do is get data into Guard Duty. Guard Duty can pull data from multiple logging sources and evaluate block storage.
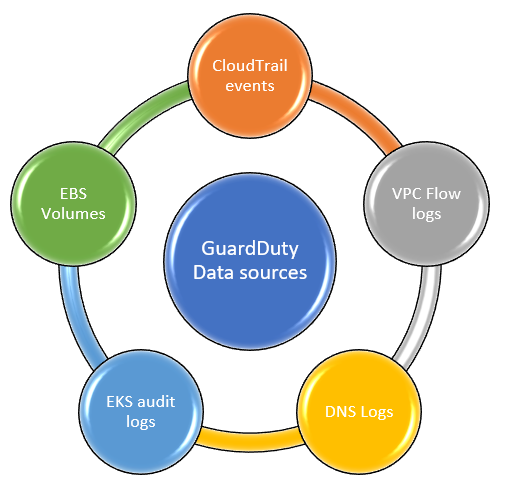
CloudTrail Logs
CloudTrail logs API calls made to AWS from the management console, command line tools, or AWS SDKs. The history and the IP source address for API calls are sent to GuardDuty to look for patterns of suspicious activity or IPs. CloudTrail logs are the foundation of GuardDuty and will automatically feed data to GuardDuty once enabled.
DNS Logs
If you use AWS DNS resolver (Amazon Route 53), GuardDuty can review that data. If it detects requests to DNS known to be bad actors, those will be flagged by GuardDuty, as that’s often a sign of bot activity. If you use a different DNS, you can skip this, as GuardDuty does not support the logs from other DNS providers.
VPC Flow Logs
The logs from your virtual private cloud will allow GuardDuty to watch inbound and outbound traffic requests. This information enables GuardDuty to identify unauthorized IP addresses and destination ports.
Kubernetes audit logs
Kubernetes audit logs are an optional data source, but if you are using Kubernetes, you will want to ensure that logging is enabled and flowing into GuardDuty. These logs contain the history of the Kubernetes API from the Amazon EKS control plane and allow GuardDuty to monitor and identify suspicious activity.
Elastic Block Storage volume
GuardDuty Malware Protection can scan Elastic Block Storage (EBS) to locate malware. First, it creates a snapshot of the volume and an encrypted replica, then scans the replica to look for known malware. The replica is deleted after the scan, but be sure to configure GuardDuty so that the snapshot is retained for remediation and further action if it finds malware.