In today’s fast-paced digital landscape, cloud computing has revolutionized business operations. As the second largest cloud provider Microsoft Azure offers many useful services. But when using these capabilities, it is crucial to remember the Azure Shared Responsibility Model. Let’s delve into understanding this model and the best practices needed to ensure optimal security while working in the Azure environment.
What is the Shared Responsibility Model?
Every cloud user, from startups to Fortune 500 companies, needs to understand the nuances of the shared responsibility model. But what is it exactly? At its core, this model is an arrangement where both Microsoft Azure and the user have defined obligations to maintain security in the cloud. While Azure secures the overarching infrastructure, users have critical responsibilities, including data protection, access controls, and account management.
Azure’s Dual-Pronged Approach to Security
Imagine a scenario where you rent a safety deposit box. The bank ensures the security of the vault, while you decide who gets access to your box’s key. This analogy describes Azure’s approach to shared cloud security. With Azure, you’re getting a secure environment, but there are several elements that you, as the user, must proactively manage to prevent potential breaches.
Exploring the Azure Responsibility Matrix
What exactly is the Azure shared responsibility model? Azure, the cloud service provider, shares the mantle of ensuring the safety of assets with the end user. How these responsibilities split depends on the specific cloud service model in play: be it Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS).
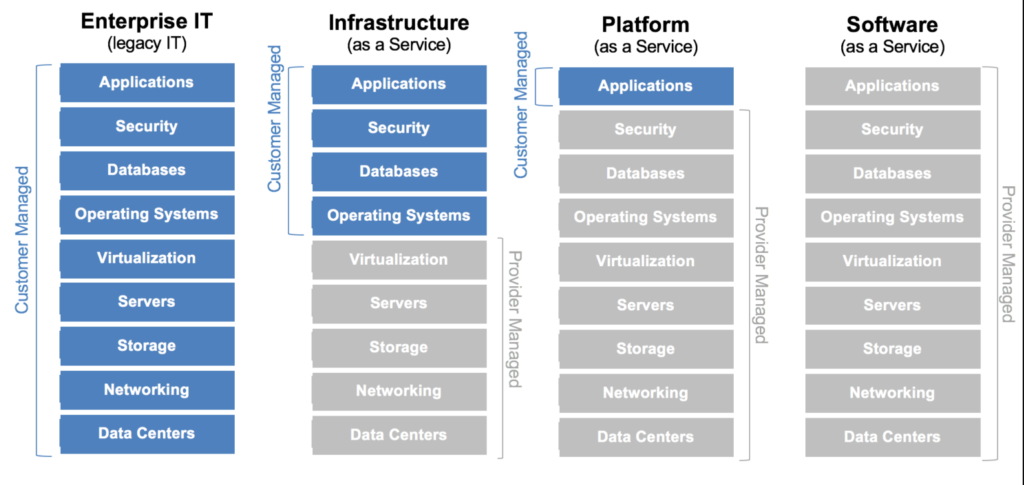 Within the IaaS framework, Azure handles the core infrastructure security—think of aspects like Azure VMs and Blob Storage. However, the user takes the lead in safeguarding other components, from the operating system to applications and data.
Within the IaaS framework, Azure handles the core infrastructure security—think of aspects like Azure VMs and Blob Storage. However, the user takes the lead in safeguarding other components, from the operating system to applications and data.
Switch to the PaaS model, and Azure extends its protective arm over the runtime and middleware segments, leaving the user to focus on the security of their applications and data.
And for the SaaS model? Here, Azure oversees the application and its underlying infrastructure, with the user only responsible for data protection and access control.
A Collaborative Effort
Let’s look at two example asset types, data storage and virtual machines.
Data Storage
Azure is like the guardian of a fortified castle, ensuring that the walls, towers, and gates remain impervious. But what do you store inside? That’s up to you. While Azure handles physical security and infrastructure, users are at the helm of data security, classification, encryption settings, and access controls.
Virtual Machines
Virtual machines are akin to apartments in a high-rise building. Azure guarantees the building’s stability, but the security inside each apartment? That’s the resident’s duty. Azure ensures VM service resilience, but users control access, network settings, and the OS.
Best Practices in Upholding Shared Responsibilities
Embrace the model
This model isn’t unique. The specifics can vary based on the provider’s offerings and policies, but the concept is common among nearly all cloud providers. By dividing responsibilities, both Azure and the users can focus on securing the items that are their responsibility, leading to a comprehensive security approach
Regular reviews
Organizations should regularly review their responsibilities under this model. Incorporating reviews yearly and when integrating new Azure services or making significant changes to existing deployments is recommended.
Multi-cloud approach to risk management
For the many organizations using multiple cloud providers, it’s important to take a multi-cloud approach to their security efforts. Tracking, correlating, and prioritizing risks across platforms leads to alert fatigue and notification blindness. A central location is needed to properly risk score issues in the context of multiple clouds and tools. Using a prioritization engine like Paladin Cloud, risks can be monitored, prioritized, and remediated holistically across cloud providers.
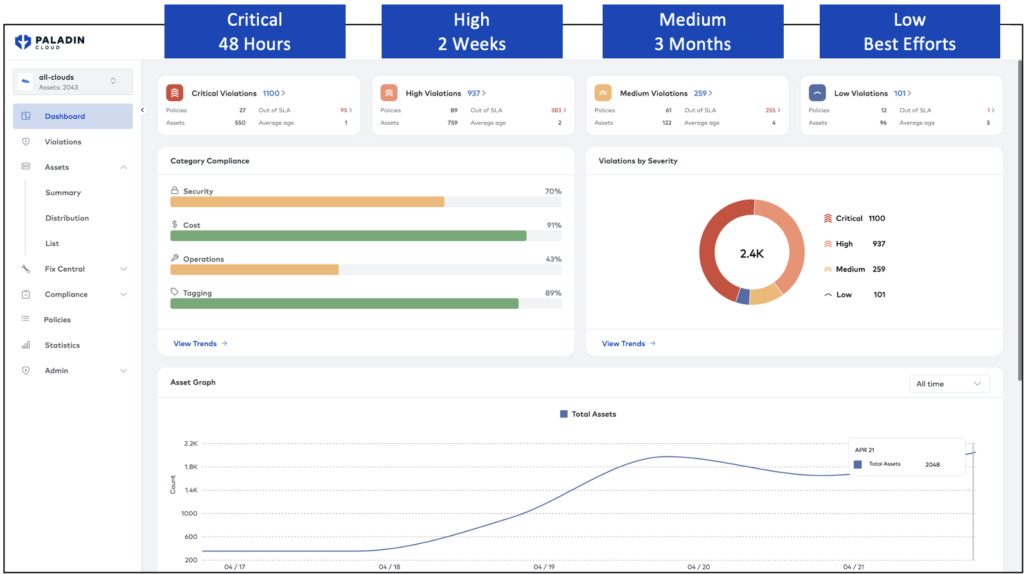
Verify runtime reality
Shifting left is about implementing security earlier and earlier in the development lifecycle process. However, at the same time, organizations are shifting security left, it is vital to shield right. To know if your security efforts are working, you need to be able to verify the state of your runtime. What is the reality of the assets being deployed? That’s where Paladin Cloud’s Cloud Security Posture Management (CSPM) module can save you time and provide peace of mind. By scanning your infrastructure for common misconfiguration and risks, flagging them when found, and even kicking off automated remediation workflows, teams can be confident they are upholding their part of the shared responsibility model.
From Risk Assessment to Incident Response
While Azure provides the tools and foundations, users must have their security playbook. This playbook should entail risk assessments, stringent network security measures, regular security monitoring, and a robust incident response process. Embracing services like Azure Security Center and Azure Policy can further bolster defenses.
Conclusion
The Azure Shared Responsibility Model is not just a framework; it’s an agreement between Azure and its users. By understanding and adhering to this model, businesses can maximize the benefits of offloading some of their security to the cloud providers while maintaining a holistic security posture over the elements that are their responsibility.