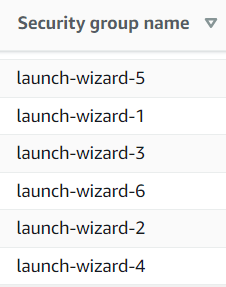
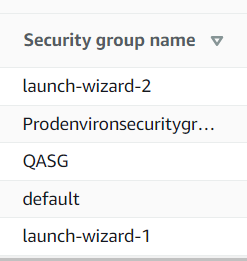
Trying to come up with a unique name on the spot leads to a jumbled mess as each developer uses a different naming pattern.
Thankfully, we aren’t alone in this naming challenge. The need for good naming schemes has been around for a long time. There are even whole fields of study dedicated to naming things. The solution is to define consistent, logical nomenclature that packs valuable information into the semantics of the name.
Significant Part Numbering System
Manufacturing engineers refer to this as a significant part numbering system.
From Wikipedia:
In a significant part numbering system, the part numbers are assigned intelligently, according to an encoding system, and thus they give an indication of salient characteristics of the component. For example, a screw may have the part number “HSC0424PP”; in this case, the letters indicate characteristics of the component:
- H = “Hardware”
- S = “Machine Screw”
- C0424 = “4-40, 3/4″ long”
- PP = “Panhead Phillips”
Setting Conventions
To save time, reduce mistakes, and increase security, a security group naming convention needs to do a few things.
Be consistent across your organization.
Once trained, anyone at the organization coming across the name should know what it does.
Be easily identifiable
The name should be simple enough that developers don’t need reference material to understand.
Provide enough information to be useful
Reduce misconfigurations due to misunderstanding of a group’s purpose. For example, a wrongly assigned security group could stop an asset from working correctly or provide overly permissive access creating a security risk.
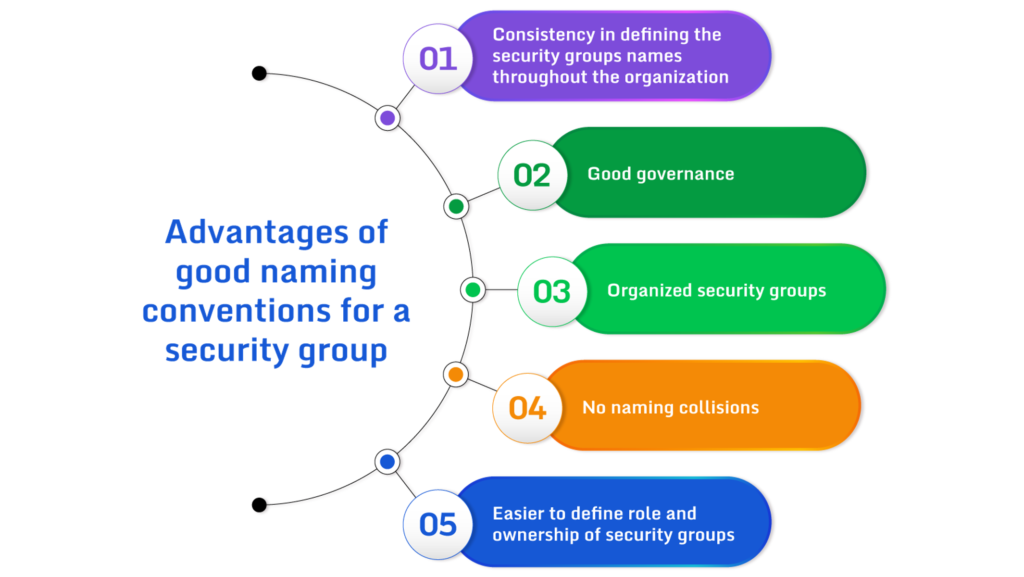
Advantages
Using a significant security group numbering system provides several advantages.
- Consistency
- Good Governance
- Organized groups
- No collisions
- Easier ownership
Examples
Let’s look at how others tackled their naming conventions. Organizations use various naming strategies for security groups. Below is an example strategy shared by the co-founder of Invisibl Cloud.

An example of AWS security group naming conventions. (Source)
Below is another example of a naming convention that is somewhat descriptive, revealing information about the type of application and its streaming methodology.
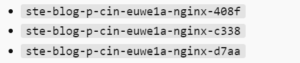
An organization should consider what is important to them and then define code for applications that are well understood internally. When using an application code, the organization must have a written naming strategy that defines the mappings. Such as Blog = A001, and Gaming Application = A002. Avoid getting too complicated, or the process can become unwieldy.
Once defined, the next step is to automate and audit the use of the naming convention.
Automation
Automating the creation of security groups reduces errors and increases consistency. For example, teams can use Infrastructure-as-Code, like a CloudFormation template or a free, open-source Terraform script, to define their security groups. These templates or scripts create security groups the same way every time.