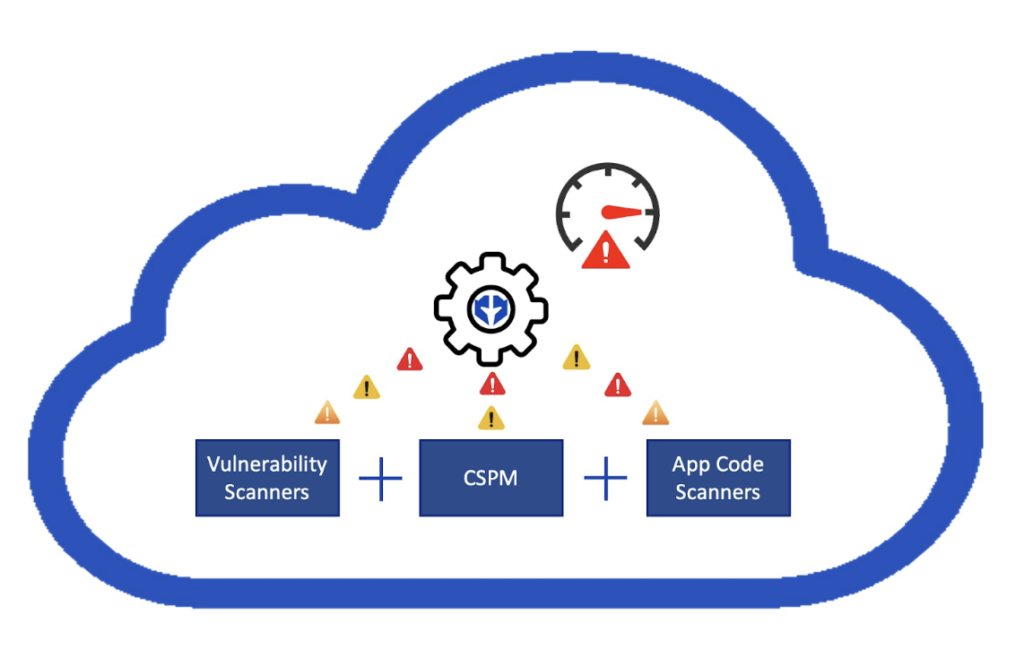
The cybersecurity landscape has evolved dramatically over the past decade, with threats becoming more sophisticated and pervasive. Traditional vulnerability management strategies are struggling to keep up with the rapid pace of new vulnerabilities, data proliferation, cloud migrations and remote workforces. Unified Vulnerability Management (UVM) emerges as the comprehensive solution for organizations looking to stay ahead of threats. UVM offers a unified, proactive, and continuous approach to securing an organization’s infrastructure, making it a key enabler of the future of cybersecurity.
This article will explore the challenges faced by traditional vulnerability management, the core principles of UVM, and how it can drive organizations toward improved security posture and operational resilience.
The Shortcomings of Traditional Vulnerability Management
Traditional Vulnerability Management (VM) focuses on scanning specific assets at scheduled intervals (hourly, daily, weekly or monthly) to identify known vulnerabilities. However, as organizations have grown more complex, traditional VM has encountered multiple limitations:
- Siloed Operations: Traditional VM tools often focus on individual asset classes (e.g., network infrastructure or applications) rather than providing a holistic view.
- Inconsistent Coverage: Different tools are needed for cloud environments, endpoints, containers, and on-prem infrastructure, leading to blind spots.
- Delayed Remediation: VM scans happen periodically, which creates a time gap where attackers can exploit vulnerabilities before they are detected.
- Manual Processes: Legacy VM systems often rely heavily on manual assessments, creating delays in identifying, prioritizing, and fixing issues.
- Lack of Integration: With the expansion of DevSecOps, remote work, and hybrid cloud infrastructure, isolated vulnerability management systems struggle to integrate seamlessly with continuous delivery pipelines and security operations centers (SOCs).
These limitations highlight the need for a more adaptive and comprehensive approach, which UVM offers.
What is Unified Vulnerability Management (UVM)
UVM is an advanced, integrated, and continuous security framework that provides full visibility and remediation strategies for vulnerabilities across assets, including multi-cloud platforms, applications, data, identity and endpoints. UVM platforms plug into existing security tools and clouds to collect data from these systems to provide a holistic approach to an organization’s security risks and exposures. Unlike traditional VM, UVM centralizes all security findings, ensuring no asset or vulnerability goes unnoticed.
Key features of UVM include:
- Unified Visibility: Centralizes vulnerability data from asset types (multi-cloud, applications, network infrastructure, and endpoints) into a single dashboard.
- Continuous Monitoring: Enables real-time tracking of vulnerabilities rather than relying on periodic scans.
- Automated Remediation and Prioritization: Leverages machine learning to automatically prioritize critical vulnerabilities and recommend remediation steps.
- Integration with DevSecOps and Cloud Tools: Seamlessly integrates with CI/CD pipelines, allowing vulnerabilities to be detected and mitigated during software development.
- Governance and Compliance Monitoring: Ensures organizations remain compliant with regulatory standards such as GDPR, HIPAA, and SOC 2.
Benefits of UVM for Organizations
Holistic Security Posture
UVM ensures that all areas of an organization’s digital footprint—applications, data, networks and cloud resources—are included in vulnerability scans and monitoring. This eliminates blind spots and improves overall security.
Proactive and Continuous Monitoring
Unlike traditional VM, UVM relies on continuous monitoring rather than scheduled scans. As vulnerabilities emerge, UVM tools immediately detect them and trigger alerts or automated responses, reducing the attack surface.
Improved Risk Prioritization
Given the massive volume of vulnerabilities reported in large enterprises, prioritization is essential. UVM tools use advanced analytics, risk scoring and contextual data to identify which vulnerabilities pose the most significant risk based on exploitability, asset criticality, and threat intelligence feeds.
Faster Remediation through Automation
UVM integrates with IT automation platforms and can initiate self-healing processes. This ensures that critical patches and updates are applied in near real-time without human intervention.
Seamless Integration with DevSecOps
In the age of continuous software delivery, security needs to be built into every stage of the development lifecycle. UVM tools integrate with CI/CD pipelines, enabling automated security checks before deployment and ensuring developers receive timely alerts about vulnerabilities.
Compliance and Governance Alignment
With strict regulatory standards becoming a norm, UVM ensures that organizations can continuously monitor and report on compliance with frameworks such as NIST, PCI-DSS, and ISO 27001. This reduces the risk of non-compliance fines and reputational damage.
How UVM Addresses Emerging Cybersecurity Challenges
Multi-Cloud and Hybrid Environments
Enterprises today increasingly operate across hybrid cloud and multi-cloud infrastructures. Traditional VM tools often struggle with the dynamic nature of cloud workloads. UVM provides real-time visibility and vulnerability management across all cloud environments, ensuring that no workload is overlooked, even as assets scale or move across clouds.
Remote Work Challenges
The rise of remote work has expanded the attack surface, with more devices accessing corporate networks from outside traditional perimeters. UVM solutions monitor and manage vulnerabilities on remote endpoints, ensuring security even when devices are not on corporate networks.
Ransomware Mitigation
Ransomware attacks have surged, targeting vulnerabilities in networks and endpoints. UVM tools identify weaknesses that ransomware groups often exploit and help organizations remediate these vulnerabilities proactively.
Challenges in Adopting UVM
While UVM presents a promising solution, its adoption is not without challenges:
- Initial Complexity: Integrating UVM tools with existing infrastructure and processes can be complex and may require changes in organizational workflows.
- Cost of Implementation: UVM solutions can be expensive, particularly for smaller organizations with limited cybersecurity budgets.
- Skilled Workforce Requirement: Successful implementation of UVM requires a skilled workforce capable of managing automated security processes and understanding the insights provided by advanced analytics.
Despite these challenges, organizations that adopt UVM are likely to see significant improvements in their security posture and operational efficiency.
The Future of Cybersecurity: UVM as the New Standard
The pace at which vulnerabilities are discovered and exploited is accelerating. The need for real-time, automated, and comprehensive security management has never been greater. As organizations adopt more complex IT environments, the future of cybersecurity will depend on solutions like UVM that can address evolving challenges efficiently.
UVM represents the **next generation of vulnerability management** by integrating cloud security, endpoint protection, DevSecOps, and compliance monitoring into a single, cohesive framework. Its proactive, continuous, and automated approach ensures that security becomes a business enabler rather than a bottleneck.
Industry analysts predict that UVM will become a key component of cybersecurity strategies as enterprises continue to grapple with digital transformation and hybrid working models. In the coming years, the demand for UVM solutions will grow, with organizations prioritizing platforms that offer holistic visibility and seamless integration across their IT environments.
Conclusion
The cybersecurity industry is shifting towards Unified Vulnerability Management (UVM) as a critical framework to address emerging challenges. UVM provides organizations with a unified, continuous, and automated way to manage vulnerabilities across diverse environments. By integrating with DevSecOps processes, automating remediation, and offering real-time insights, UVM reduces the risk of breaches while ensuring compliance with regulatory standards.
As cyber threats become more sophisticated, organizations need more than just periodic vulnerability scans. UVM offers the necessary agility and coverage to keep pace with modern cybersecurity challenges. Implementing UVM may involve initial complexities, but the long-term benefits make it a vital investment for organizations that prioritize security and operational resilience.
The future of cybersecurity lies in proactive and unified management—and UVM is poised to become the gold standard for organizations aiming to safeguard their assets in an increasingly complex digital world.