Open source is important to the world
This line from Security in the Open was followed by “It’s the underpinning of everything we do on the web.” Since open source is so important to the web, it’s no surprise that open source security is also essential to the web. Here AWS shared its three pillars for increasing open source security.
1. Work upstream
- Release security libraries & tools as open source
- Provide financial support
The session shared specifics on how they worked towards these, for example, donating to fund developers to work full-time on projects like OSSF. They challenged the audience to consider how to work upstream, share our code, and support the OSS projects we care about.
AWS re:Inforce 2023 – Security in the Open: OSS and AWS (SEC201-L)
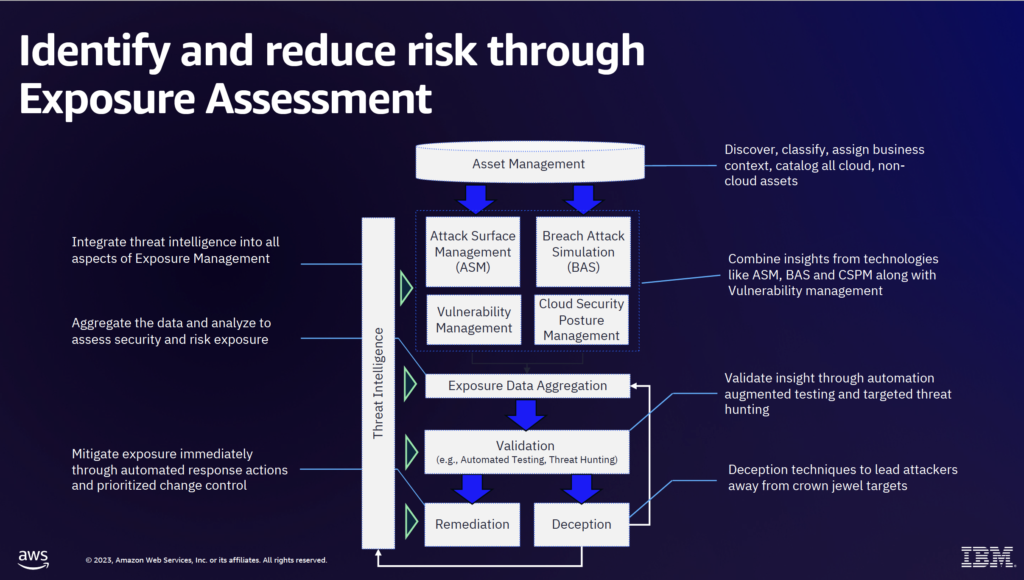
Here at Paladin Cloud, open source is at the center of everything we do. Our core product is always free and open source to use. It also gives visibility into our security practices so organizations know how we handle their data.
Threats evolve but don’t go away
Misconfigurations, Vulnerabilities, Malware, and Identity Management are top organizational concerns, with ransomware being one of the most feared outcomes. Every year thousands of folks learn from the FBI, for the first time, that they were breached and their data was found exposed. The reason security conferences and tooling are continuing to grow despite the challenging economic conditions is that breaches prove to be far more costly.
Conclusion
Some of the best learnings I had at re:Inforce weren’t from a session but over lunch or breakfast with fellow practitioners. The session speakers were knowledgeable, but AWS had tight control over who spoke, and there was a prevailing sentiment of wishing for more speaking slots for customers.
The AWS keynote made me feel they had things under control as they talked about tackling challenges at a scale I couldn’t even grasp, like the 350 billion WAF rules they process daily. I was impressed as they shared the new cryptology algorithms built to thwart quantum supercomputers that don’t even exist yet but, hypothetically, may exist in the future. And then, a few sessions later, the AWS US-East-1 Lamda outage hit, causing my, and everyone else’s, workshops to fail. It was a vivid reminder that nothing is 100% reliable and why redundancies and defense in depth are our profession’s watchwords.
Still, I would put this event in the success column as I learned a ton and met some fantastic people. I’d encourage you to check out the sessions on demand.