Cyber Asset Attack Surface Management (CAASM) platforms are critical for managing cyber-attack surfaces and protecting digital assets. They provide a comprehensive view of an organization’s digital assets and the attack surfaces of these assets. A properly configured CAASM platform enables proactive risk detection, verification of security controls, and automated remediation to improve an organization’s security posture and reduce cyber-attack risks.
This article will explore CAASM in more detail, explain six essential attack surface management best practices, and provide recommendations to help organizations effectively deploy CAASM as part of an attack surface management strategy.
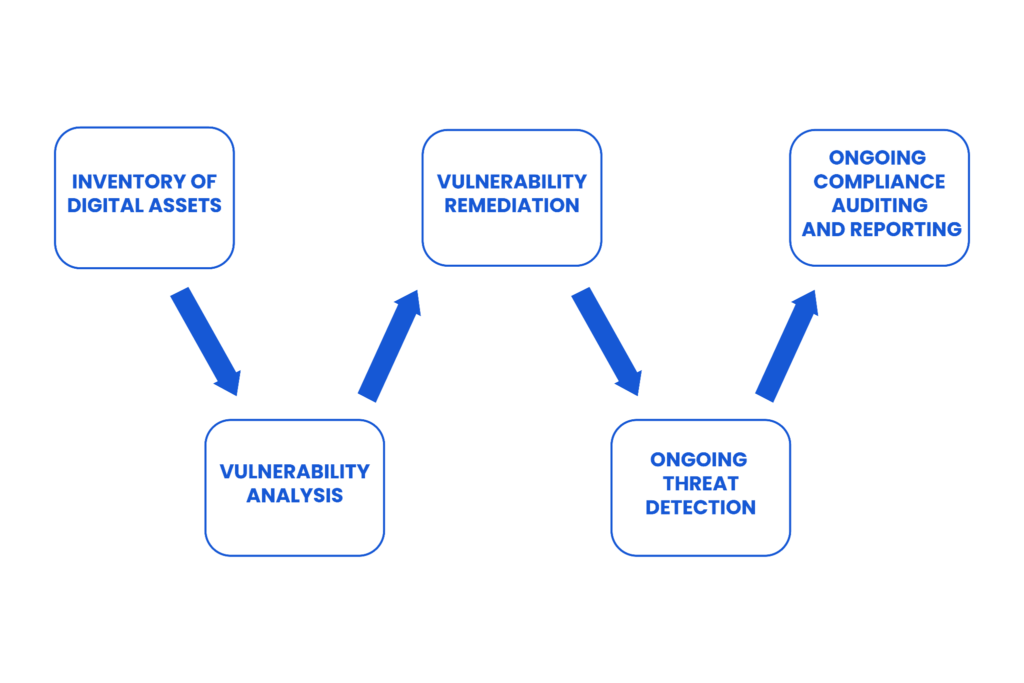
An overview of the steps involved in attack surface management.
Summary of attack surface management best practices
The table below summarizes the six attack surface management best practices this article will explore in more detail.
| Best practice | Description |
| Establish a comprehensive inventory of digital assets | This process involves identifying and cataloging all IT assets within an organization’s environment using network scanning tools, active discovery techniques, and other methods to locate and document all devices, software, and network components. |
| Conduct a vulnerability analysis | Vulnerability analysis involves scanning IT assets to identify attack surfaces and testing these vectors for exploitable vulnerabilities. |
| Implement a vulnerability remediation plan | Once vulnerabilities are identified, vulnerability management tools can apply security updates and patches to mitigate or remediate them. |
| Leverage continuous threat detection | Threat detection tools should be configured to generate alerts when suspicious activity is detected so incident response teams can quickly investigate and respond to potential attacks. |
| Perform ongoing compliance auditing and reporting | Organizations should use compliance reporting tools to meet regulatory requirements and industry standards, such as CIS, HIPAA, PCI, CSA, NIST, and SOC2. |
| Integrate CAASM tools with other security systems | CAASM platforms should be integrated into an organization’s broader security platform to enable comprehensive monitoring and proactive threat management. |
Six essential attack surface management best practices
Attack surface management best practices help organizations effectively manage infrastructure security and minimize the risk of cyber-attacks. The sections below detail six essential attack surface management best practices to help enterprises create or improve an attack surface management strategy.
Establish a comprehensive inventory of digital assets
The first step in protecting your attack surface is identifying and inventorying all digital assets that a threat actor may try to exploit. This best practice consists of two primary steps:
- Asset discovery for all Internet-facing digital assets
- Asset classification
Discovery is performed using network scanning tools, web crawling tools, and manual input of asset addresses. One of the most important objectives in this process is the discovery of shadow assets and orphan assets.
Shadow assets are hardware or software deployed on the network without official administrative approval or oversight. Common shadow assets include cloud applications used via the organization’s network and unmanaged personal mobile devices used to access company information.
Orphaned assets include old software, websites, servers, and devices that are no longer in use and need to be properly retired and disposed of.
Asset classification drills down further and helps describe and group digital assets. It includes four key attributes:
- Asset ownership/responsibility: Defines the person, organization, or business unit responsible for the asset. This attribute can include unknown “shadow IT” assets being used without the IT or security team’s approval.
- Asset type: This attribute classifies the technical or business purpose of the asset. Examples of asset types include:
- Web applications, services, and APIs
- Mobile applications and their backends
- Cloud storage
- Network devices
- Domain names
- SSL certificates
- IP addresses
- IoT and connected devices
- Code repositories such as GitHub, BitBucket, and Gitlab
- Email servers
- Data sensitivity: This attribute categorizes the sensitivity of data the assets contain. Assets with sensitive data should be classified and labeled appropriately. Examples of sensitive data include PII, PCI, PHI, and secrets (such as passwords and API keys).
- Asset location: A location details an asset’s physical or logical location. Third-party or vendor assets are assets that the organization doesn’t own but are part of its IT infrastructure or digital supply chain. These include SaaS applications, APIs, public cloud assets, or third-party services used within the organization’s website.
Conduct a vulnerability analysis
Vulnerability analysis is also known as penetration testing. Vulnerability analysis tools scan attack surfaces for vulnerabilities in software, configuration errors, and other issues that attackers can exploit.
After an asset inventory has been established, organizations should scan their assets to identify potential vulnerabilities and unprotected attack vectors. Then, the second step in vulnerability analysis involves testing and probing these vulnerabilities to determine if an attacker can exploit them.
Implement a vulnerability remediation plan
Once vulnerabilities are identified, vulnerability management tools can apply security updates and patches to remediate vulnerabilities. Patching ensures that systems and applications are up-to-date and protected against known security threats.
Remediation tactics include patching software vulnerabilities, removing malware, reconfiguring systems, or implementing additional security controls to prevent the threat from occurring again. Remediation can also involve broader measures, like implementing a network firewall, SSL, or multi-factor authentication (MFA).
Leverage continuous threat detection
A threat detection system is essential for proactive threat detection, notification, and sometimes even automated remediation.
These tools continuously scan your existing assets and your network to identify new ones. They scan to detect suspicious activity and can be configured to alert incident response teams when new assets or vulnerabilities are discovered. This enables incident response teams to respond to potential attacks quickly.
In some cases, these tools can automatically implement remediation of certain security vulnerabilities. This greatly reduces risk exposure, and threat detection time previously performed manually by humans.
Perform ongoing compliance auditing and reporting
Compliance reporting tools help organizations reduce risk by ensuring they meet regulatory requirements and industry standards, such as CIS, HIPAA, PCI, CSA, NIST, and SOC2.
Maintaining compliance is essential for protecting sensitive information, reducing the risk of data breaches and cyber-attacks, and ultimately avoiding potential financial penalties and legal actions. Continuous compliance, an ongoing systematic approach to ensuring compliance, helps organizations implement tighter control and improve visibility for compliance-related risks.
Compliance reporting tools provide visibility into an organization’s information security posture, including vulnerabilities and potential threats. This visibility can help monitor risks and identify areas for improvement. These tools can also help organizations report compliance to regulators and internal and external stakeholders, such as auditors, customers, and partners.
Integrate CAASM tools with other security systems
CAASM platforms should be integrated into an organization’s broader security platform to enable comprehensive monitoring and proactive threat management.
Effective cybersecurity requires comprehensive knowledge of your infrastructure and cyber assets. By understanding what exists, where it exists, and all relevant meta-data about each asset, it is possible to establish a robust security program that builds on this knowledge.
Integration of security tools enables security teams to collaborate on threat investigations or incident response by combining information about threat intelligence on analyst results. This integration also allows teams to gain complete visibility over all assets and ensure they are managed and protected.
Recommendations for a successful attack surface management strategy
The following tips and recommendations can help organizations effectively implement the best practices and apply CAASM to attack surface management in a modern cloud-based setting to reduce cyber-attack risk.
- Automate as much as possible. When establishing your inventory of digital assets, use automated tools, such as asset discovery tools, to help identify and track assets.
- Prioritize risk. Develop a risk management plan that includes a process for identifying and prioritizing risks. Consider using threat modeling techniques to identify potential attack vectors and prioritize risks.
- Create and enforce standards-driven policies. Develop and enforce security policies and standards for cloud-based assets. Leverage security automation tools to enforce compliance with security policies and standards.
- Continuously monitor for threats. Establish a continuous monitoring process that includes automated detection and response capabilities. Train security personnel on threat detection and response best practices.
- Adopt Shift Left practices. Consider implementing shift left practices to automate security processes throughout the software development lifecycle.
- Understand and adapt to regulatory changes. Monitor changes to regulatory requirements and adjust security policies and controls accordingly. Conduct regular compliance audits and reports to ensure that cloud-based assets meet regulatory requirements.
Summary
Though deploying a cyber asset attack surface management solution may be challenging and expensive, following the recommended best practices highlighted in this article can help. These best practices can help organizations detect risks proactively, validate the efficacy of your security controls in safeguarding their cyber assets, and automate the remediation of identified violations.
A free, open-source tool like Paladin Cloud provides a powerful yet simple solution to this challenge. It can be rapidly deployed and immediately start scanning for and protecting against common cloud vulnerabilities with its built-in, pre-configured policies based on the cloud provider’s best practices. It also provides an auto-fix capability to remediate some of these issues where appropriate.


