Cloud security configuration management (SCM) is the process of managing the security settings of cloud-based resources to ensure they are secure and compliant. The process includes identifying misconfigurations, assessing risk, and remediating vulnerabilities. Misconfigurations can lead to a variety of security risks, including:
- Unauthorized access to sensitive data
- Denial-of-service (DoS) attacks
- Data breaches
There are many different ways to approach cloud security configuration management. Some organizations use manual processes, while others use automated tools. There are also several different cloud security configuration management frameworks available.
This article will discuss the importance of cloud security configuration management, how to implement it, its benefits, and six essential cloud security configuration management best practices.
Summary of key cloud security configuration management concepts
The table below summarizes four essential cloud security configuration management concepts this article will explore in more detail.
| Concept | Summary |
|---|---|
| What is cloud security configuration management (SCM)? | A set of processes, procedures, and tools to eliminate misconfigurations of cloud resources and increase security, such as Paladin Cloud’s automated security policies. |
| How to implement cloud security configuration management | The six high-level steps for cloud security configuration management implementation are:
|
| Cloud security configuration management
benefits |
Key benefits of cloud security configuration management are:
|
| Cloud security configuration management best practices | Six cloud SCM best practices are:
|
Why do we need cloud security configuration management (SCM)?
Configuration management has always been an essential component of IT and cybersecurity. In the legacy world of physical hardware in data centers, configuration management practices include:
- Changing the default passwords on hardware appliances such as routers and switches
- Updating default application configurations
- Hardening operating systems
- Performing firmware updates
- Implementing encryption
Since the shift to cloud computing, configuration management has become increasingly complex. The public nature of the cloud means network configuration is far more critical than it is for resources running on an internal network. Misconfigurations in cloud-based resources can accidentally allow public access to private data. In addition to cloud SCM, Identity and Access Management (IAM) controls are also important for addressing this risk and ensuring only people who need access to resources have it.
Additionally, new cloud technology concepts such as containers, serverless applications, microservices architecture, and SaaS integrations create new security challenges. These services are often easy to deploy but may require expert knowledge to avoid misconfigurations and security vulnerabilities.
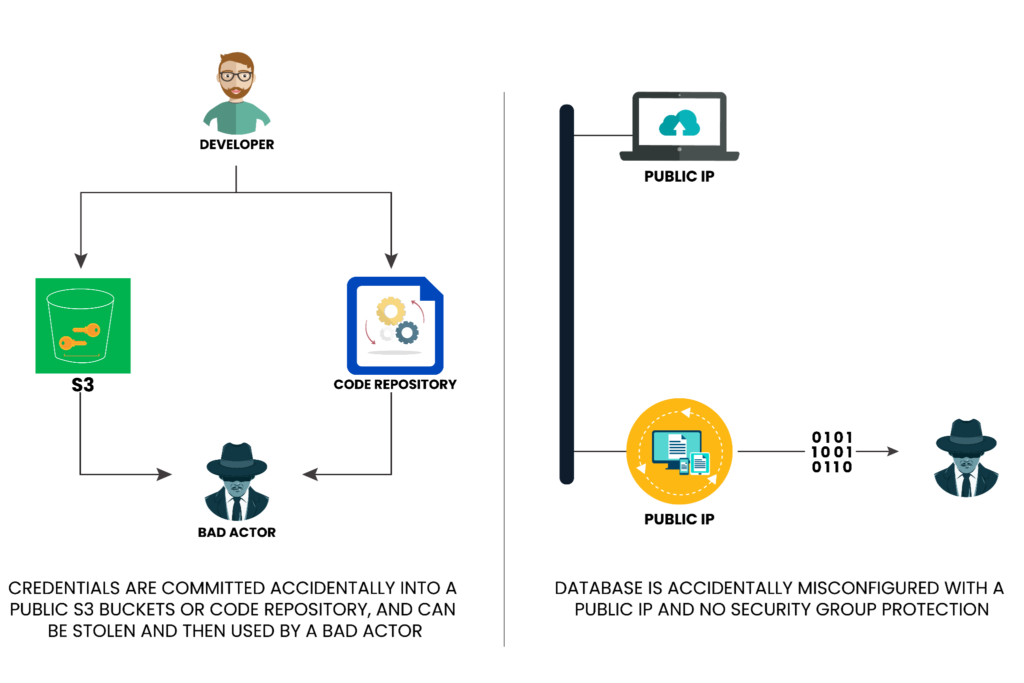
An overview of common cloud misconfigurations that can lead to unauthorized access to credentials and data.
You can solve these issues with the right cloud security configuration management tools. Cloud SCM platforms have best practices built into them and will scan your cloud environment, looking for, alerting on, and potentially auto-correcting misconfigurations as they go. They will also check role-based access controls and identify where excess permissions are granted.
Cloud security configuration management also helps new deployments follow best practices and align with enterprise security strategy. Securely deploying solutions lessens the risk of an exploit and is a crucial aspect of shifting security left.
How to implement effective cloud security configuration management
An organization can take several different approaches to cloud security configuration management. Some choose to use a manual process, while others use automated tools. There are also many different cloud security configuration management frameworks available. For example, Paladin Cloud is a cloud security platform that provides continuous compliance over your cloud assets to enhance an organization’s security posture. The platform provides a full asset inventory, while verifying security controls are providing intended protection. Prebuilt and custom security policies provide automated compliance checks to identify vulnerabilities and misconfigurations of cloud resources.
A company’s approach will depend on a few factors, such as the size and complexity of the organization’s cloud environment, the level of security required, and the budget. Here are six steps to help determine the correct approach for your organization:
- Define strategy upfront– Strategic policies and procedures must be defined to guide the implementation. A governance group or committee, including relevant senior management and technical and security specialists, will agree and formalize these. Policies may include guidance from relevant recognized organizations such as CIS, NIST (US), and the NCSC (UK).
- Compile an asset inventory– This step involves the identification of all cloud-based resources. This could be a manual inventory of all systems, but such an approach is prone to oversight and human error. A more efficient solution is a Cloud Asset Attack Surface Management (CAASM) tool, which automatically scans the cloud landscape, providing a unified view of all cloud resources.
- Evaluate tools– The next step is agreement on the toolchains and platforms . This will likely involve a period of assessment and perhaps a series of technical “spikes” to determine the correct platform for your organization. Relevant tools include infrastructure as code (IaC), configuration management scripts and automation, and cloud security posture management (CPSM) tools.
- Implement tools– This step involves the implementation of the selected tools and running tests to ensure they operate correctly.
- Follow change control processes– Change control processes ensure that proposed changes are investigated and researched for security implications. Access control and auditing are vital to ensuring adherence to change control processes. However, change control shouldn’t be too demanding as it can stifle innovation and business agility. Ideally, tools should help organizations streamline change control to balance oversight with agility.
- Ensure compliance– Continuous monitoring must be in place to reduce the potential of missing accidental misconfigurations, flag poorly implemented change controls, or identify new vulnerabilities.
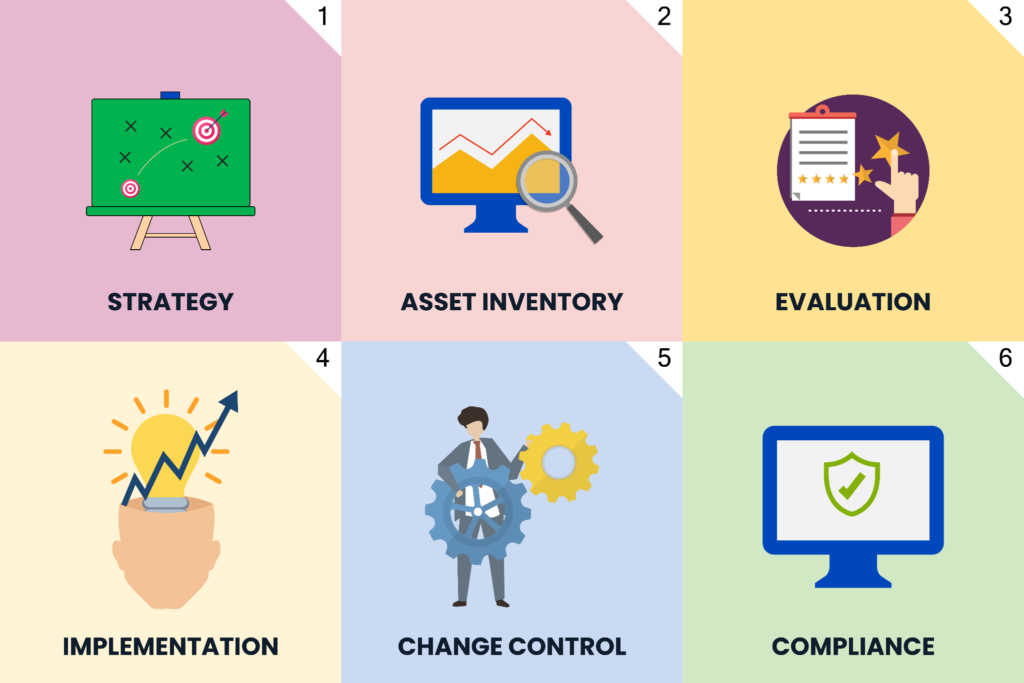
The six stages of cloud security configuration implementation.
Cloud security configuration management tools
The sections below explore three essential cloud security configuration management tools.
Infrastructure as Code (IaC)
Infrastructure as Code (IaC) is a process for managing and provisioning cloud infrastructure using code. It involves writing scripts or templates that define the configuration of cloud resources, such as virtual machines, storage accounts, plus serverless and networking components. These scripts or templates can be version-controlled, tested, and deployed like any other software code.
IaC helps ensure that cloud resources are configured consistently and can be easily audited and rolled back in case of issues. It also identifies any drift in the configuration, indicating changes in the cloud resources outside of the code. The administrator can either revert these uncontrolled changes or seek approval retrospectively and then update the code to reflect them. An example of a commonly used IaC tool is Hashicorp’s Terraform.
Configuration management tools
Configuration management tools help automate the process of managing and configuring cloud resources. These tools can help organizations enforce policies and procedures, automate repetitive tasks, and ensure the consistent configuration of cloud resources. Examples of configuration management tools include RedHat Ansible, Perforce Puppet, and Salt.
Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) is a process of assessing and managing the security posture of cloud resources. CSPM tools help organizations monitor and assess the security configuration of cloud resources, identify risks and vulnerabilities, and provide recommendations for remediation. CSPM tools can also help enforce compliance with industry standards and regulatory requirements.
A tool such as Paladin Cloud’s Open Source Community Edition is a pre-configured cloud security solution that monitors common vulnerabilities across multiple cloud providers and data center infrastructure. It provides a modern user interface that visualizes security data and takes predefined remedial actions when security exposures are detected.
Cloud security configuration management benefits
From a business perspective, cloud security configuration management offers two key benefits:
- Improved security posture. Cloud SCM helps organizations identify and remediate misconfigurations, reducing the exposure of cloud assets to security vulnerabilities, denial of service attacks, and the risk of data breaches.
- Increased compliance. Cloud SCM helps organizations monitor and audit their cloud environments for compliance with company security standards. Many regulations require organizations to have a process in place for managing and controlling the configurations of their IT systems (e.g, Sarbanes-Oxley Act (SOX), General Data Protection Regulation (GDPR), and ISO27001). Cloud SCM can help organizations meet these requirements and provide evidence of this during audits.
Six cloud security configuration management best practices
Effective cloud security configuration management requires tools, strategy, and continuous improvement. Here are six best practices that can help enterprises get it right.
- Start with a strategy– Start with a strategy that meets business requirements, considering any compulsory regulations, or if there is a business goal to obtain security certifications (e.g., SOC 2). Regular reviews of the strategy will ensure it continues to meet the current recommendations and business demands.
- Create cloud-specific policies. Implement a security policy specifically for cloud-based resources. Many organizations fail to do this, and this is a mistake. Cloud security needs to address different challenges than on-premises security. While achieving greater IT security within the cloud is arguably easier, it requires knowledge and effort.
- Leverage purpose-built tooling. Implementing a cloud security configuration management tool could be part of a more comprehensive toolset, such as a CAASM/CPSM all-in-one solution, such as Paladin Cloud.
- Follow the principle of least privilege. Enforce access control mechanisms based on least privilege and audit all cloud activity.
- Automate as much as practical. Ideally, use an agentless tool to scan for misconfigurations regularly, apply security policies, and patch or remediate other security vulnerabilities.
- Train and upskill staff. Train and upskill the relevant employees on cloud security best practices. Include security awareness training for all employees, including phishing simulation attacks.
Conclusion
Cloud computing has changed how many organizations operate their IT infrastructure, providing flexibility and helping to increase innovation. However, the shift to cloud computing has also brought new challenges related to security. New technologies such as serverless computing, containers, and digital identities can’t be effectively managed using legacy operational management and security toolsets.
Implementing effective cloud security configuration management requires a combination of tools, processes, and policies. Best practices include using concepts such as IaC for consistent deployments, configuration management tools to enforce access controls and implement security policies, and then CSPM to regularly scan, monitor and audit cloud resources, with automated remediation wherever possible.
By following these best practices, organizations can maintain a secure and compliant cloud environment, reduce the risk of data breaches and other security incidents, and ensure their data and applications’ confidentiality, integrity, and availability.


