As organizations embrace a digital transformation journey to adopt cloud-native technologies, a comprehensive cybersecurity strategy that includes people, processes, and technology is existential to enabling a secure digital transformation. The Cyber Asset Security and Management (CAASM) philosophy embraces this holistic approach, emphasizing the importance of managing IT assets and ensuring their security in modern cloud-native ecosystems.
Cyber asset management (CAM) extends CAASM. CAM focuses on achieving visibility into an organization’s assets, enabling risk assessments, and proactively identifying potential threats.
In a typical cloud environment, assets commonly refer to:
- Compute/network resources
- Storage
- Databases
- Security & identity services
- Monitoring tools
- Content delivery networks
- Serverless platform services
A comprehensive cyber asset management program ensures that such assets are deployed with a security-first mindset, all assets remain secure throughout their operational life, vulnerable assets are rapidly detected, and end-of-life assets are decommissioned safely to prevent data leakage.
This article will explore five cyber asset management implementation techniques, their implementation stages, and best practices for secure implementation.
Summary of key cyber asset management strategies
Traditional perimeter-based security models are insufficient for protection against modern threats. This is often because managing cyber assets in a cloud-native ecosystem goes beyond conventional asset discovery, classification, and vulnerability management.
Managing assets at scale also introduces operational complexities, especially as environments and network perimeters rapidly change. The complexity is compounded by organizations’ continued reliance on legacy solutions for manifesting cloud resource inventory.
These challenges necessitate adopting modern implementation strategies for cloud-based asset management. The five cyber asset management strategies in the table below address this challenge and enable organizations to implement more granular security controls, improve visibility into asset behavior, and streamline compliance with industry regulations.
| Cyber asset management implementation strategy | Use case |
|---|---|
| Micro-segmentation | Isolating and protecting critical assets |
| Open Standards | Ensuring interoperability and reducing the risk of vendor lock-in |
| Policy-based vulnerability monitoring | Employing a defined policy framework to identify, classify, prioritize, and remediate security vulnerabilities |
| File Integrity Monitoring (FIM) | Monitoring changes to critical system files and detecting unauthorized modifications |
| Zero Trust Architecture | Improving endpoint security with additional authentication and authorization for all network traffic |
| Endpoint Privilege Management | Controlling and limiting the use of privileged accounts on endpoints |
Cyber asset management implementation strategy #1: Micro-segmentation
Micro-segmentation involves segmenting a network into smaller, isolated segments with their own security policies and access controls. It is a highly scalable and adaptable approach to protecting cloud assets that enables organizations to easily adjust their security posture as environments change.
Besides preventing unauthorized access and minimizing data exfiltration risks, segregating critical assets and services into separate network segments also helps organizations restrict an attacker’s lateral movement in the event of a successful breach.
Implementation stages
| Stage | Objective |
|---|---|
| Assess current network and asset landscape | Examine the existing cloud network infrastructure, including services, workloads and their dependencies to gain insight into its segmentation and security posture. |
| Create segmentation policies and rules | Formulate granular rules considering factors like asset sensitivity, user access requirements, and regulatory compliance to create logical network segments. |
| Design micro-segmentation architecture | Develop a comprehensive blueprint for micro-segmentation implementation, including network segmentation, firewall placement, and routing configuration. |
| Implement and configure micro-segmentation | Deploy the micro-segmentation architecture using cloud-native security tools such as virtual firewalls or software-defined networking (SDN) solutions; apply defined policies and rules to corresponding segments. |
| Evaluate and improve | Regularly assess the segmentation by monitoring its efficiency. Make necessary adjustments to policies and rules in response to emerging threats, changes in the cloud setup, or new compliance requirements. |
Best practices for implementing micro-segmentation as part of a cyber asset management strategy
- Map dependencies and data flows before implementation. Before implementing micro-segmentation, thoroughly map application dependencies, inter-service communications, and data flows within your cloud environment to minimize unintended disruptions and identify potential vulnerabilities.
- Leverage flow monitoring. Utilize network flow monitoring or automated dependency mapping to identify critical connections and undertake segmentation decisions.
- Use software-defined policies to improve flexibility and security. Utilize software-defined perimeter solutions to create dynamic, context-aware access policies for a more flexible and secure micro-segmentation implementation.
- Inspect east-west traffic. Deploy virtual firewalls or other network security solutions to inspect and control east-west traffic between micro-segments for enhanced visibility of intra-segment communications.
Cyber asset management implementation strategy #2: Open standards
Open standards are publicly available specifications that enable interoperability, accessibility, and flexibility among complex IT environments. Aligning open standards with asset management ensures that organizations can effectively manage and protect their cloud-based assets while leveraging the benefits of a diverse and evolving technology landscape.
Besides allowing for efficient management and monitoring of cloud assets, open standards ensure that all distributed cloud infrastructure assets are secured uniformly by leveraging a consistent framework for implementing security controls.
Key open standards for cloud assets include:
- OAuth and OpenID Connect for identity and access management federation
- Security Content Automation Protocol (SCAP) for automating vulnerability management and policy compliance
- Cloud Security Alliance’s Cloud Controls Matrix (CCM) for security control mapping and assessment
Implementation stages
| Stage | Objective |
|---|---|
| Assess current infrastructure and standards | Analyze existing cloud asset management practices, tools, and systems to identify scope of optimization. |
| Identify relevant standards | Select open standards relevant to your organization’s cloud cyber asset management needs, such as security, data exchange, monitoring, or identity and access management. Also, evaluate their technical specifications, community support, and adoption by industry peers. |
| Develop adoption strategy | Plan the adoption of chosen standards while considering required architectural changes, API integrations, and migration processes. |
| Integrating standards with existing systems | Modify existing tools, processes, and systems, including APIs, data models, and communication protocols for seamless integration of chosen standards with various cloud infrastructure components. |
| Monitor and refine | Continuously monitor the effectiveness of the implemented standards using metrics and performance indicators. Refine the strategy over time to address potential gaps, challenges, or emerging trends in the threat landscape. |
Best practices for implementing open standards as part of a cyber asset management strategy
- Automate deployment, configuration, and management of assets. Always start with automating cloud asset deployment, configuration, and management using open-standard tools and frameworks. This can help streamline the implementation of open standards and reduce human errors.
- Have a governance structure to oversee the implementation. To ensure alignment with your overall asset management strategy and business objectives, create a governance structure that oversees implementing, maintaining, and gradually refining open standards.
- Monitor compliance. Implement processes to monitor compliance with open standards and address deviations or exceptions.
Cyber asset management implementation strategy #3: Policy-based vulnerability monitoring
Policy-based vulnerability monitoring involves a continuous detection and assessment of security flaws of your cyber assets by leveraging a policy framework of security and compliance controls. The framework outlines policies that set the parameters for routine scanning of cloud assets for known and emerging security risks within a cloud environment.
Once vulnerabilities are detected, the subsequent step involves sorting and prioritizing identified vulnerabilities. Factors considered typically include severity, exploitability, and potential business impact. Guided by policy, remediation efforts then target the highest priority vulnerabilities first, ensuring the prioritization process drives a systematic and strategic response.
Implementation stages
| Stage | Objective |
|---|---|
| Policy development | Develop a comprehensive policy framework that outlines how vulnerabilities and compliance factors are identified, classified, and addressed. |
| Configuring automated scanning tools | Choose appropriate automated scanning tools that can align with the policy parameters, and set them up accordingly. |
| Regular vulnerability scanning | In accordance with the defined policies, execute periodic policy-guided scans of cloud assets for known and emerging security risks. |
| Strategize remediation | Post-detection and classification, develop and implement a policy-guided remediation plan that targets high-risk vulnerabilities first. |
| Policy compliance verification | Regularly verify to ensure policies are in-line with security best practices and adhere to relevant regulatory standards. |
Best practices of implementing policy-based vulnerability management as part of a cyber asset management strategy
- Develop strategic, policy-aligned remediation plans. These might include patch management, configuration changes, or compensating control implementation.
- Use standardized risk scoring models. Configure scanning tools to cross-reference detected vulnerabilities against authority databases such as CVE and CWE.
- Construct Comprehensive Policies. Customize policies that specifically detail identification, classification, prioritization, and remediation procedures.
Utilizing automated scanning tools, such as Paladin Cloud for policy based monitoring can help serve a dual purpose: discovering cyber assets and simultaneously detecting any gaps in security controls.
As an extensible policy management plane, the platform employs hundreds of pre-built/custom policies based on security best practices. This not only helps identify gaps in security controls but also assists in monitoring multi-cloud environments for compliance and governance. With its auto-fix framework, Paladin Cloud also streamlines the remediation process by allowing predefined actions to be taken automatically in response to policy violations.
Cyber asset management implementation strategy #4: File Integrity Monitoring (FIM)
File Integrity Monitoring (FIM) is another advanced security strategy that tracks modifications of critical files, configurations, and access control lists; detecting potential security incidents such as unauthorized access, alterations, or deletions in real time. Integrating FIM with other cloud security tools and practices helps organizations achieve improved visibility into the state of cloud assets and strengthen a multi-layered defense against cyber threats and unauthorized access.
File changes are typically monitored using cryptographic hashes. When a file is created or modified, the FIM solution calculates a cryptographic hash of the updated file version and compares it against an established baseline hash. An alert is triggered indicating malicious activity when hashes do not match.
Implementation stages
| Stage | Objective |
|---|---|
| Define objectives and scope | Identify goals, such as compliance, sensitive data protection, or unauthorized access detection. Determine which cloud components to monitor, such as files, directories, configurations, and what changes to track. |
| Select a FIM solution | Choose a FIM platform considering factors such as integration capabilities with existing systems and support for various hashing algorithms (e.g., MD5, SHA-1, SHA-256). |
| Develop a monitoring strategy | Determine whether to use agent-based monitoring (for more detailed information and real-time visibility) or agentless monitoring (for less overhead but slower visibility rates). |
| Establish a baseline | Baseline each monitored asset by generating a hash of the file or configuration to detect changes accurately. Define a strategy for managing false positives and setting up notifications and alerts. |
| Configure and deploy the FIM solution | Configure the FIM tool according to your monitoring strategy, specifying monitored resources, change types, hashing algorithms, and notification settings. Deploy the FIM solution across your cloud environment, ensuring appropriate coverage and integration with existing systems. |
| Test and validate | Verify FIM implementation to ensure it’s working as expected by simulating changes to monitored components and confirming that the FIM system detects and alerts based on the generated hashes. Also, test incident response and escalation procedures for overall effectiveness. |
Best practices of implementing FIM as part of a cyber asset management strategy
- Combine multiple FIM techniques. To improve FIM accuracy, combine multiple methods and parameters, including hashing algorithms (such as SHA-256), file attributes (such as file size and modification time), and access control lists (ACLs).
- Choose the right solution for your environment. Consider unique characteristics of cloud environments, such as multi-tenancy, shared responsibility model, and distributed architecture to assess compatibility with an FIM solution.
- Update baselines regularly. Periodically update baselines of monitored assets to reduce false positives and maintain accuracy of the FIM system.
- Implement tight security controls for your FIM tooling. Implement strict access controls to protect the FIM system’s configuration files, log files, and agents from unauthorized access and tampering.
Cyber asset management implementation strategy #5: Zero Trust Architecture
Zero Trust Architecture (ZTA) is a security framework that helps implement comprehensive security of cloud-based assets by enforcing continuous authentication and verification for all access requests. The framework relies on granular access controls based on a user’s identity, device posture, and network location.
How does Zero Trust Architecture align with cloud-based cyber asset management?
ZTA aligns with cyber asset management because ZTA:
- Secures cloud resources by enforcing continuous authentication and verification for all access requests, ultimately reducing the risk of data breaches and other security incidents.
- Assumes all users, devices, and applications are potentially malicious, zero trust helps organizations proactively safeguard their cloud assets.
- Implements granular access controls based on a user’s identity, device posture, and network location. As a result, ZTA helps organizations administer fine-grained access permissions to resources based on the user’s specific needs.
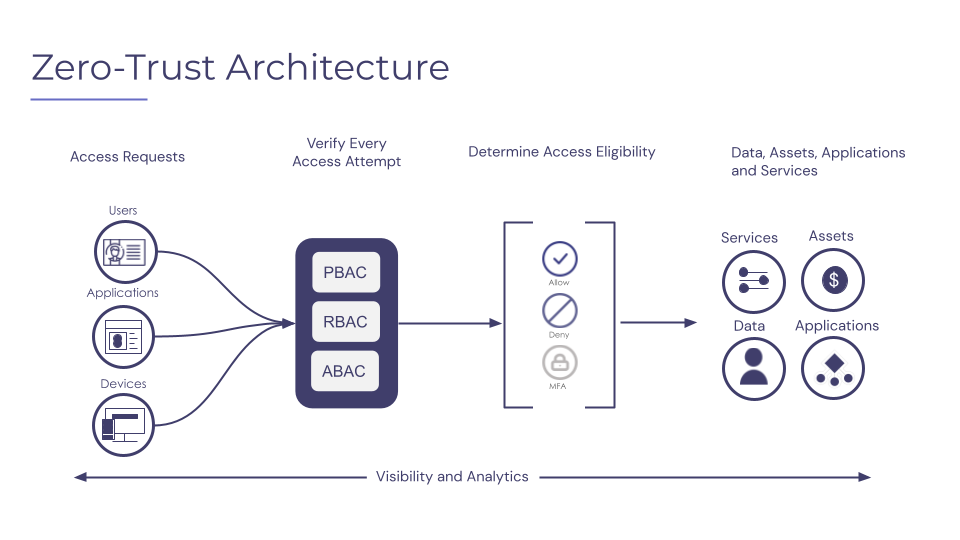
An overview of the Zero Trust Architecture process flow (source).
Implementation stages
| Stage | Objective |
|---|---|
| Define scope | Establish your ZTA deployment’s scope, including all cloud assets, applications, and data. |
| Map data flows | Utilizing data flow mapping to identify where data is stored, processed and transmitted as well as how users and devices interact with that information. |
| Implement authentication and authorization | Administering multi-factor authentication and authorization controls to guarantee that only authorized individuals can access cloud assets. |
| Segment networks | Segmenting networks help protect sensitive resources by blocking unauthorized access and minimize the impacts of lateral movement by attackers. |
| Monitoring & analytics | Utilizing monitoring and analytics capabilities to proactively detect and respond to potential security threats in real-time. |
| Automation | Automating as much of the ZTA deployment and management process as possible to reduce human error. |
Best practices for implementing Zero Trust Architecture as part of a cyber asset management strategy
- Use micro-segmentation for granular security. Implement micro-segmentation to isolate and secure individual workloads and applications within the cloud environment to enforce granular access controls.
- Adopt Software-Defined Perimeter (SDP) to harden the network perimeter. Use SDP to create a secure, isolated network perimeter for sensitive cloud resources.
- Protect endpoints with Endpoint Detection and Response (EDR). Deploy EDR solutions to monitor and analyze endpoint activity, detect malicious behavior, and respond to security incidents.
Cyber asset management implementation strategy #6: Endpoint Privilege Management
Endpoint Privilege Management (EPM) is a key security strategy to safeguard cloud endpoints by restricting access and privileges at the user and application level. The strategy helps reduce the risk of insider threats and external attacks that exploit uncontrolled access to cloud assets, including virtual machines, containers, and other cloud resources.
With an EPM strategy, organizations can:
- Assign the principle of least privilege to grant users and applications only the minimum necessary privileges to perform their intended functions
- Implement controls to enforce access policies, including application whitelisting, privilege escalation management, and access control lists
Implementation stages
| Stage | Objective |
|---|---|
| Asset identification | Identify all assets within an organization’s cloud infrastructure, including virtual machines, containers, services, and other cloud resources. |
| Privilege assessment | Assess privileges required by each user and application to access identified cloud asset endpoints. |
| Policy definition | Define access policies based on the principle of least privilege. |
| Implementation | Implement policy enforcement controls using application whitelisting, privilege escalation management, and access control lists. |
| Monitoring & analysis | Monitor cloud asset activity and analyze logs to identify potential security threats proactively. |
| Policy review & update | Regularly review and update access policies and controls to ensure they remain effective and up-to-date with evolving threats. |
Best practices for implementing Endpoint Privilege Management
- Adopt a secure configuration management strategy. Leverage tools such as Paladin Cloud for comprehensive asset discovery and tracking. Implement secure configuration management practices to ensure endpoint assets are configured with secure settings and are regularly updated.
- Automate as much as practical. Automate EPM processes wherever possible to reduce the risk of human error and increase efficiency.
- Leverage threat intelligence. Use threat intelligence to identify potential security threats and proactively adjust EPM policies and controls to mitigate those threats.
Conclusion
With the continuous adoption of cloud-native architectures, the importance of managing IT assets is more relevant than it used to be in legacy setups. As enterprise IT becomes more dispersed with the expansion of public-facing digital assets and increased use of cloud infrastructure, implementing novel approaches for safeguarding an organization’s attack surface continues to be a challenge.
Adopting advanced cyber asset management strategies can help modern organizations address the challenges and securely adopt cloud-native strategies. Many companies turn to third-party security providers as a cost-effective solution. For example, Paladin Cloud is a cloud security platform that provides continuous compliance over your cloud assets to enhance an organization’s security posture. The platform provides a full asset inventory, while verifying security controls are providing intended protection. Prebuilt and custom security policies provide automated compliance checks to identify vulnerabilities and misconfigurations of cloud resources.


