Cloud-native services are highly vulnerable to cyber threats due to their operation in public clouds and multiple users sharing the same resources. In such scenarios, a hacker can orchestrate a deeper attack by exploiting a vulnerable resource they manage to control.
Perimeter security alone isn’t enough, but it still functions as the first line of defense. For organizations operating their infrastructure in the cloud, it is imperative to understand how a web application firewall (WAF) and security groups contribute to maintaining a robust security posture. So, what are the key differences between using a firewall and a security group, and what are typical use cases for each service?
Key differences
A security group is a set of rules that protect an instance or instance stack by filtering ports or protocols. It’s like a bouncer for elastic instances, ensuring that only the right traffic gets in. This helps prevent unwanted intrusions in a simple and effective way.
A web application firewall (WAF) helps protect web application resources by blocking HTTPS requests sent to cloud resources. Unlike security groups, a WAF can set up more complex security rules for more precise control over access. With a WAF, cloud administrators can set rules that dictate how an application or API should work based on specific criteria, which can then be used to protect the said application by preventing known attack patterns
The table below compares how web application firewalls and security groups enforce security controls differently.
AWS Firewall vs. Security Group
| Aspect | AWS Firewall (WAF) | Security Group |
|---|---|---|
| Type of traffic blocked | Ingress Traffic (Inbound only) | Both Ingress and Egress (inbound and outbound) |
| Protocols and ports supported | HTTP and HTTPS (Port 80 and 443) | TCP (all ports), UDP (all ports) and ICMP types |
| State | Stateless | Stateful |
| Scope | Endpoint level (API Gateway, Application Load Balancing, CloudFront, etc.) | Instance level (EC2, Elastic Load Balancing, AWS RDS, etc.) |
| OSI layer | Layer 7 | Layer 3 and 4 |
Implementing WAF and Security Groups
Both WAF and Security Groups are essential for security. The choice isn’t between a firewall and security groups but how to use them to work together to protect cloud-native workloads. Let’s explore common use cases for both firewalls and security groups.
Web Application Firewalls use rule groups to control incoming HTTPS traffic and block harmful requests from reaching the application or API layer. Rule groups are created by setting ALLOW or DENY conditions for various traffic characteristics, such as:
- String values within requests
- Country of origin
- Request size/length
- Request header values
- Content of the request body, including SQL code and programming scripts
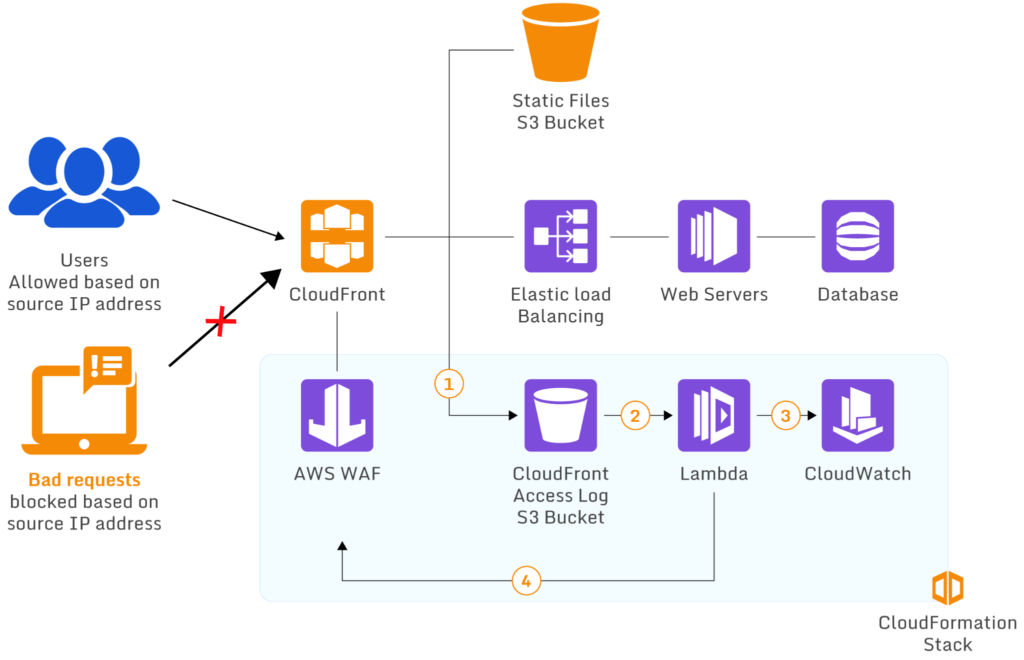
A WAF using Lambda to block requests from specific IP addresses (source)
Behavior filters help administrators defend web applications from attack patterns that are difficult to block using only static ports/IP addresses. A WAF is also useful in detecting attacks like HTTP floods, SQL injection, UDP floods, and bot attacks.
To protect against web attacks, a WAF has a comprehensive set of rules. However, extensive knowledge of HTTP requests and attack patterns is required to create effective rules. Therefore, while it is not costly to set up, administering a WAF can require significant investment in specialized training.
When it comes to blocking hackers, using security groups is easier than using WAF. To do it, you just need to say which IPs can or cannot access your data. That’s why security groups are a good choice if you want to save money.
Security groups are best for simple application environments that haven’t been changed much. However, security groups can’t inspect the content of requests and responses, so they can’t protect against more advanced attacks.
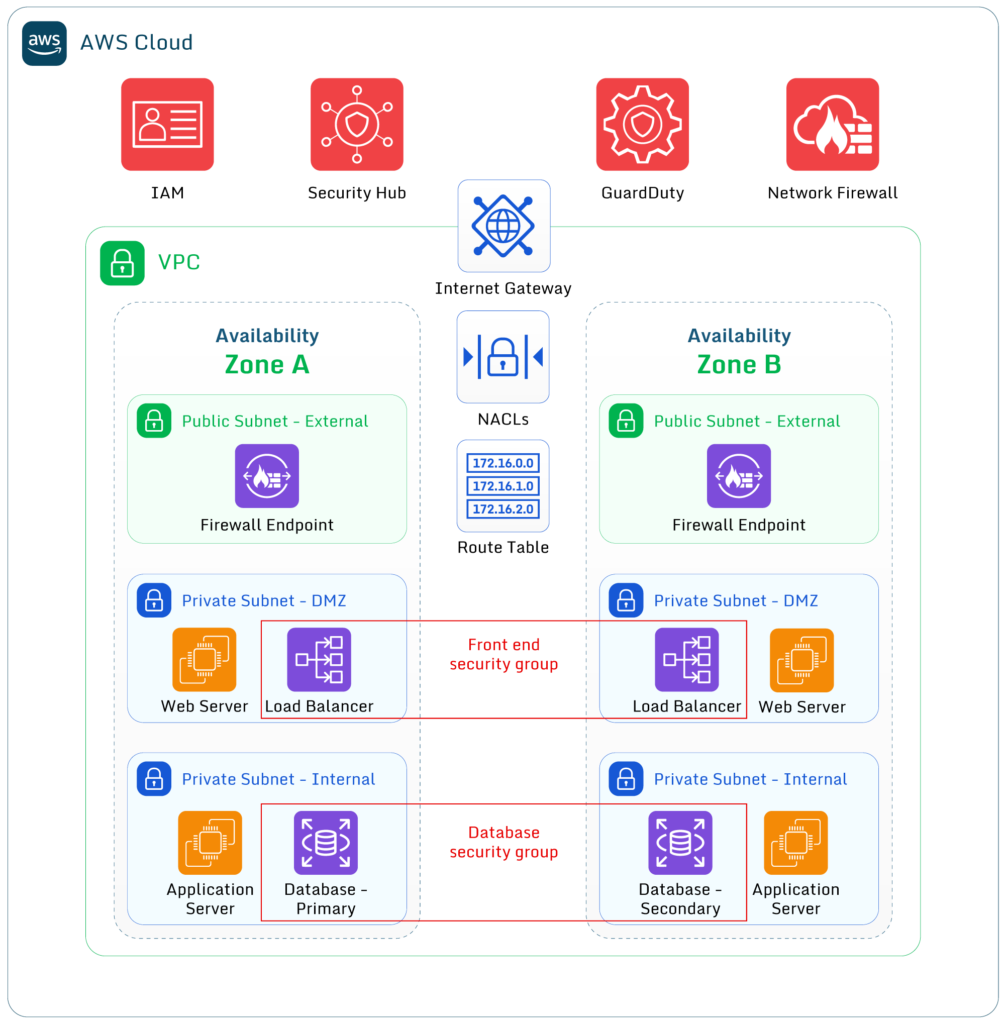
Firewall and security groups can be used together to manage access controls for instances, subnets, and virtual private clouds (VPCs). In a large deployment, administrators may allow all inbound connections of a specific type into the VPC, then use security groups to deny some of these connections to accessing particular resource instances.
Managing security posture
Protecting cloud assets and continuously monitoring security groups is a high priority for most companies. However, managing an organization’s security posture while using a multi-service approach introduces multiple operational complexities that require a lot of manual labor. To alleviate the effort of tracking every asset over disparate systems, consider using a free open-source security-as-code tool like Paladin Cloud, which enforces continuous monitoring, unified visibility, and proactive threat detection of a distributed ecosystem.
Web application firewalls are like the first line of defense for cloud workloads. They make sure that only the right traffic gets to the operating instance. Security groups help by allowing you to extend common restrictions across different resource stacks. Firewall and Security Group should be used together to create a more complete defense protecting your application’s different parts.
Further reading: AWS Firewall vs. Security Group: Use Cases & Recommendations
