Cloud-native services are particularly susceptible to cyber threats because they often operate in public clouds with shared hosting environments and multiple users sharing the same resources. When a hacker manages to gain control of just one of those resources, orchestrating a deeper attack by exploiting the vulnerable resource is a common pattern. Fortunately, there are cloud security practices, tools, and services that help enterprises mitigate risks.
For organizations running their infrastructure in the AWS cloud, understanding AWS security solutions is essential to maintaining a strong security posture. This article will explore two core AWS security services: AWS web application firewall (WAF) — a.k.a “AWS firewall” — and security groups. We’ll also explore key AWS firewall vs. security group differences and typical use cases for each service.
AWS Firewall vs. Security Group: An Overview
Maintaining a robust security posture often begins with assessing the differences between security services and tools. While there is a lot of technical nuance involved, comparisons typically focus on security scope, ease of administration, and reusability.
Amazon Web Services (AWS) enforces a shared security model in which the platform operates, manages, and controls security services (a.k.a. “security of the cloud”). On the other hand, the client assumes responsibility for securely configuring these services based on their workload’s usability patterns and threat models (a.k.a. “security in the cloud”).
The table below compares how AWS web application firewall and security groups enforce security controls differently.
AWS Firewall vs. Security Group
| Aspect | AWS Firewall (WAF) | Security Group |
|---|---|---|
| Type of traffic blocked | Ingress Traffic (Inbound only) | Both Ingress and Egress (inbound and outbound) |
| Protocols and ports supported | HTTP and HTTPS (Port 80 and 443) | TCP (all ports), UDP (all ports) and ICMP types |
| State | Stateless | Stateful |
| Scope | Endpoint level (API Gateway, Application Load Balancing, CloudFront, etc.) | Instance level (EC2, Elastic Load Balancing, AWS RDS, etc.) |
| OSI layer | Layer 7 | Layer 3 and 4 |
AWS Firewall vs. Security Group: How do they differ?
An AWS security group is a set of rules to protect an instance or instance stack using port or protocol-based filtering. A security group sits in front of elastic instances to apply inbound and outbound traffic rules. As a result, security groups provide a simple and effective intrusion prevention mechanism.
A web application firewall (WAF) helps secure web application resources by monitoring and blocking HTTP(S) requests that are forwarded to cloud resources. In contrast to security groups, a WAF helps define a more sophisticated set of security rules for fine-grained access control. With a WAF, cloud administrators can specify rules that define an application or API’s behavior based on defined criteria, subsequently securing the application/API layer by mitigating known attack patterns.
Type of traffic blocked
Security groups apply access rules to inbound and outbound traffic at the instance level. This service helps control access of internal network resources by defining basic ALLOW rules for different networking protocols and ports.
WAFs only control inbound traffic. A WAF checks incoming request headers and compares them with a database of known attack signatures to determine whether the request should be allowed.
Ports supported
Security group rules can be applied to all types of traffic, and can be used on any communication protocol. The most common protocols specified in security rules include 6 (TCP), 17 (UDP), and 1 (ICMP).
AWS firewall enables intrusion prevention by monitoring HTTP and HTTPS requests forwarded to the application they protect. The firewall filters requests by scanning ports 80 (HTTP) and 443 (HTTPS) and ensuring that the secured resource either responds with the requested content, a custom response, or the forbidden status code (HTTP 403).
State
Security groups are stateful and contain rules that allow all return traffic by default. Being stateful implies that for any outbound request sent from an instance or vice versa, a follow-up response is allowed regardless of the defined outbound security rules.
WAF rules are stateless where the firewall inspects each incoming request in isolation. The WAF performs the inspection regardless of whether the incoming traffic is part of an existing, approved connection.
Scope
Security groups apply rules at the instance level but cannot inspect content type. When an instance or stack of instances is launched, it is associated with at least one security group. The service is used to secure both incoming and outgoing traffic by preceding elastic instances such as the Elastic Load Balancer (ELB), Elastic Cloud Compute (EC2), or the AWS Relational Database System (RDS).
The web application firewall performs packet inspection at the endpoint level by applying access rules to ingress traffic. As the service is capable of inspecting content within incoming requests, WAF can filter out malicious payloads. To implement a WAF for AWS services, it is associated with an Application Load Balancer (ALB) sitting in front of the stack of instances under its protection. Additional service integrations supported by WAF include:
- API Gateway – for REST APIs
- AppSync – for GraphQL APIs
- CloudFront CDN – for serverless workloads or any HTTP webserver
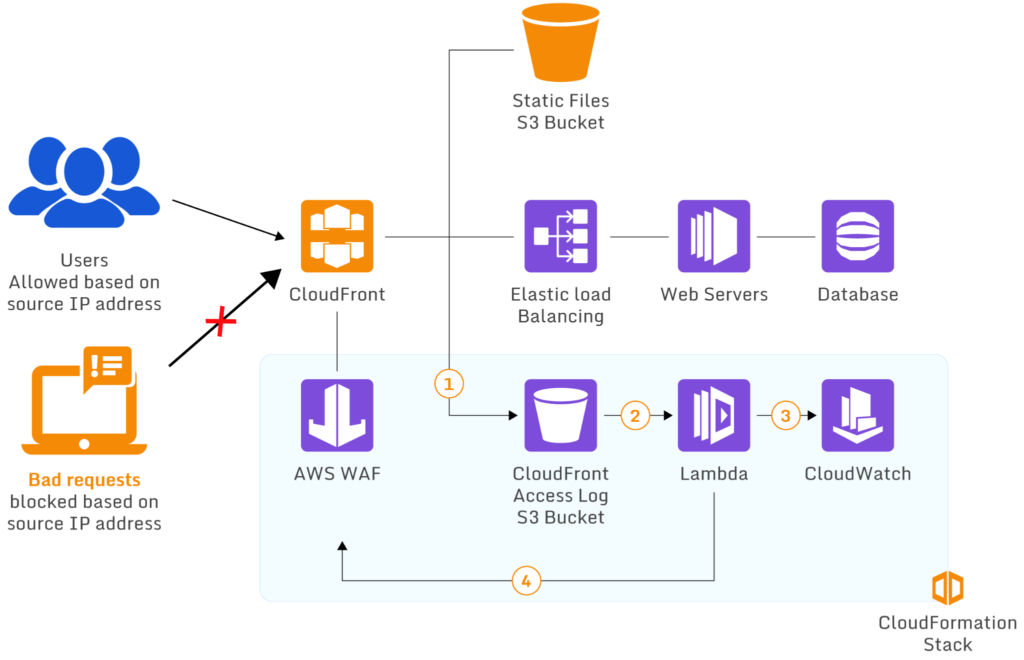
Ideal scenario of AWS WAF using Lambda to block requests from specific IP addresses (source)
OSI layer
Security groups operate on layers 3 & 4 (Network and Transport layer) of the OSI model. As the service helps filter network/transport protocols and determine access permissions based on source ports and IP addresses, they are commonly preferred to secure against network and transport layer exploits, including unauthorized SSH connections, IP spoofing, and routing table poisoning.
The web application firewall operates on layer 7 (Application layer), filtering traffic based on HTTP request headers. The service protects web servers and applications against common web attacks, such as SQL injection, cross-site scripting, and insecure direct object reference.
AWS Firewall vs. Security Group: Recommendations
Both AWS web application firewall and security groups play a vital role in AWS security. AWS firewall vs. security group isn’t typically an “either or” choice. They complement each other when it comes to comprehensive cloud-native workload protection. In this section, we’ll look at recommendations and typical use cases for both AWS firewall and security groups.
When to use AWS web application firewall
The AWS WAF enables cloud administrators to control access of content based on incoming request attributes. The WAF can be used to protect web resources, including:
- Amazon API Gateway REST API
- Application Load balancer
- AWS CloudFront Distribution
- AWS Cognito user pool
- AWS AppSync GraphQL API
The AWS WAF operates on defined rule groups to control ingress HTTP(S) traffic while restricting malicious requests from reaching the application/API layer. Rule groups are typically defined using ALLOW/DENY conditions over a wide range of traffic characteristics, including:
- Strings values within requests
- Country of origin
- Request size/length
- Request header values
- Content of the request body, including SQL code and programming scripts
These behavior filters allow administrators to protect web applications from attack patterns that can’t be typically forbidden by blocking static ports/IP addresses. WAF is also a powerful tool for detecting attacks like HTTP floods, SQL injection, UDP floods and bot attacks.
A WAF offers an extensive rule set to protect against web attacks, it requires extensive knowledge of HTTP requests and attack patterns to establish effective rules. As a result, while it is relatively inexpensive to set up, administering WAF requires a significant investment and upskilling of security teams.
When to use AWS security groups
A security group acts like a virtual firewall that protects AWS instances by allowing or blocking network protocols based on ports and IP addresses. Although security groups are primarily associated with EC2 instances, they can also be applied to other elastic services that are attached to instances via a virtual private cloud (VPC), including:
- Elastic File System (EFS)
- Elastic Load Balancer (ELB)
- AWS RDS
Compared to WAF, security groups offer a straightforward administration of intrusion defense, because access authorization only requires specifying an instance’s IP as a rule. As a result, security groups are preferred as an affordable access control solution.
Because of their simplicity, security groups are highly effective for vanilla environments without customizations made to their original state. However, as security groups do not inspect the content of requests and responses, they are ineffective against most modern attack vectors and don’t provide comprehensive protection of complex cluster setups.
When AWS firewall and security groups complement each other
AWS firewall and security groups are not mutually exclusive. They can be used together to provide flexibility in managing access controls for instances, subnets, and virtual private clouds (VPCs).
For instance, in a large deployment, administrators may allow all inbound connections of a specific type into the VPC, then use security groups to deny some of these connections to access specific resource instances. A hybrid environment can also be used to run staging and production subnets separately. In this case, both subnets can receive requests from external networks through the WAF, but cannot communicate directly with each other since they are in different security groups.
In spite of its benefits, leveraging a multi-service approach introduces multiple operational complexities which requires a lot of manual labor to resolve. Nowadays, companies lack the manpower and resources to maintain the integrity of their clouds – increasing risk of failures and breaches. Hence, for most, protecting their cloud assets and performing continuous monitoring of their security groups is a high priority. To alleviate efforts of tracking every asset or disparate systems, consider using Paladin Cloud’s open-source Cloud Security Posture Management (CSPM) platform which solves these challenges by enforcing continuous monitoring, unified visibility, and proactive threat detection of a distributed ecosystem.
Conclusion
Nearly 33% of the cloud infrastructure market relies on AWS for its agility, scalability and, most importantly, security. security groups and web application firewalls are key AWS security services since these ensure secure access to content and resources without impacting application performance.
Web application firewalls are a cloud workload’s first line of defense – ensuring only eligible traffic makes it to an operating instance. Security groups extend this further by bringing together related resource stacks for centralized access control. While the AWS firewall and Security Group have their individual strengths and differences, they are often used together for an augmented defense-in-depth model that protects different layers of an application stack.

