AWS GuardDuty is a service that continuously monitors an AWS account’s security and detects threats using data from multiple sources. GuardDuty plays an active role in near real-time monitoring of your account security. Organizations can monitor multiple accounts in a consolidated way with GuardDuty.
Threat detection features in GuardDuty analyze Indicators of Compromise (IOCs) from threat intelligence feeds and flag behaviors that deviate from the normal access patterns for an AWS account.
After processing the data, AWS GuardDuty generates security findings for administrators to review and act upon. You can set up an S3 bucket to export the findings for later consumption or compliance reasons. You can also set up Amazon Simple Notification Service (SNS) alerts to notify you of new findings.
Findings is the term that describes the anomalies GuardDuty highlights. Security professionals can review GuardDuty to investigate further and filter out false positives.
This article will take a deep dive into AWS GuardDuty data sources, the protections it provides, findings types, and remediation actions.
AWS GuardDuty Concepts: Executive Summary
Below is an executive summary of the key areas covered in this article.
AWS GuardDuty Key Concepts
| Key Concept | Description |
|---|---|
| Data sources | Used by GuardDuty for detecting various deviations.
|
| Protection using GuardDuty | Protections provided by GuardDuty against S3 loopholes, malware, and Kubernetes Protection.
|
| Understanding the findings | Various findings types and how they can be filtered, suppressed, etc., for investigation. |
| Investigating and remediating findings | Process of investigating each finding further and remediating it in case of True positives. |
AWS GuardDuty Data Sources
GuardDuty uses the data sources to analyze and detect unauthorized activities in your AWS account. GuardDuty used the data from the following log sources to identify the anomalies.
- CloudTrail logs, including management events and data events
- DNS logs
- VPC flow logs
- Kubernetes audit logs
- Elastic Block Storage volume
GuardDuty extracts specific data from these logs for analysis and discards the remaining logs. GuardDuty encrypts data-in-transit when communicating with other services and discards data post-analysis (i.e., GuardDuty does not retain log data). We’ll look at each log type GuardDuty uses in the sections below.
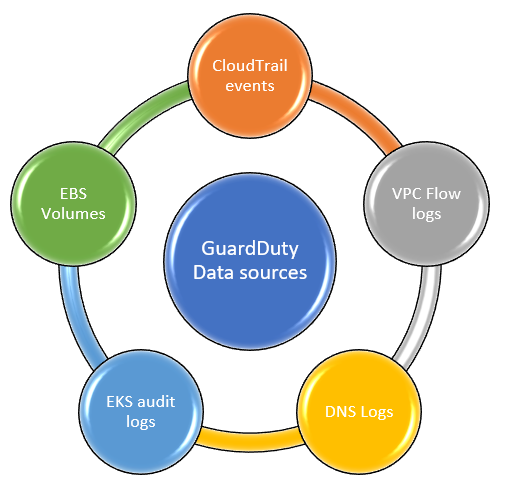
Fig GuardDuty Data sources
CloudTrail logs
CloudTrail provides the history of AWS API calls executed by IAM users, roles, or services in your account. The APIs can be executed using the management console, command line tools, or AWS SDKs. CloudTrail logs help identify the Source IP address from where API calls were made, the error code in case of unsuccessful execution of API, or user/role/AWS services that executed the API.
As soon as you enable GuardDuty, it starts analyzing the CloudTrail logs. GuardDuty also analyzes the global events published on a trail. You can also analyze S3 data events (an optional data source) with GuardDuty.
Kubernetes audit logs
In GuardDuty, Kubernetes audit logs are an optional data source. Kubernetes audit logs contain the sequential activities performed by users or applications using the Kubernetes API.
GuardDuty can monitor Kubernetes audit logs to identify suspicious activities. It ingests logs using an independent and duplicate stream of flow logs originating directly from the Amazon EKS control plane logging feature.
VPC Flow logs
VPC flow logs can be enabled at a VPC, subnet, or interface level. Once enabled, they capture the logs for inbound and outbound traffic for network interfaces in an environment. These logs help GuardDuty analyze traffic from unauthorized IP addresses and destination ports.
DNS logs
If you use the AWS DNS resolver (Amazon Route 53) for EC2 instances, GuardDuty can analyze DNS queries from its logs. GuardDuty does not support consuming logs from other resolvers (e.g., OpenDNS).
GuardDuty uses DNS logs for monitoring DNS queries to known malicious domains. DNS queries to known malicious domains can be a potential indication of compromise and a botnet activity.
Elastic Block Storage Volumes
GuardDuty Malware Protection uses these data sources to scan for malware. It creates a snapshot of the EBS volume and creates an encrypted replica from it to scan for malware. If nothing is detected, GuardDuty deletes the snapshot and the replica. If malware is detected and you have retention of EBS volumes enabled, it deletes the replica but retains the snapshots for further actions.
Protection using AWS GuardDuty
AWS GuardDuty analyzes underlying data sources to identify suspicious activity. For example, if an IAM user makes an unusual API call, GuardDuty highlights it as a finding for further analysis.
Protection based on the CloudTrail management events is enabled as soon as you enable GuardDuty. In the sections below, we’ll take a closer look at the different additional and optional protections GuardDuty offers.
S3 Protection using AWS GuardDuty
Using the S3 protection feature of GuardDuty, you can monitor object-level API operations to detect potential risks to the data in your S3 buckets. GuardDuty generates findings based on the access patterns using the S3 data events. This feature is optional and needs to be enabled to monitor the S3 data events. You can enable GuardDuty S3 protection for a standalone account or for all/any member account of the Organization using the Administrator account.
Malware Protection using AWS GuardDuty
Malware Protection analyzes the resources in your account to identify resources that are compromised or at risk of compromise. After you enable Malware Protection, when GuardDuty detects suspicious activity from an EC2 instance or a container workload it starts a scan on attached EBS volumes.
The scan doesn’t require the installation of an agent or additional configuration at the instance level. You can choose to scan or skip resources. Based on your selections, GuardDuty will include or exclude resources from scans.
If a scan detects malware, you can view a detailed finding for it in the GuardDuty console. Malware Protection is an optional feature and needs to be enabled.
Two important notes about Malware Protection:
- GuardDuty does not analyze EBS volumes encrypted with Amazon EBS encryption.
- Malware Protection is designed to run without any performance impact on instances.
Kubernetes Protection using AWS GuardDuty
Kubernetes Protection is an optional feature that helps detect malicious activity in EKS workloads using the additional data sources. When Kubernetes protection is enabled, GuardDuty ingests Kubernetes audit logs to detect suspicious activities. These logs capture chronological API activity from user, application, and control planes and are ingested in GuardDuty for detecting any suspicious or malicious activity.
AWS GuardDuty Findings
Findings are potential security issues AWS GuardDuty detects in your account. They need to be reviewed to validate security issues. Each GuardDuty finding has a security level that indicates its severity. The available security levels are high, medium, and low.
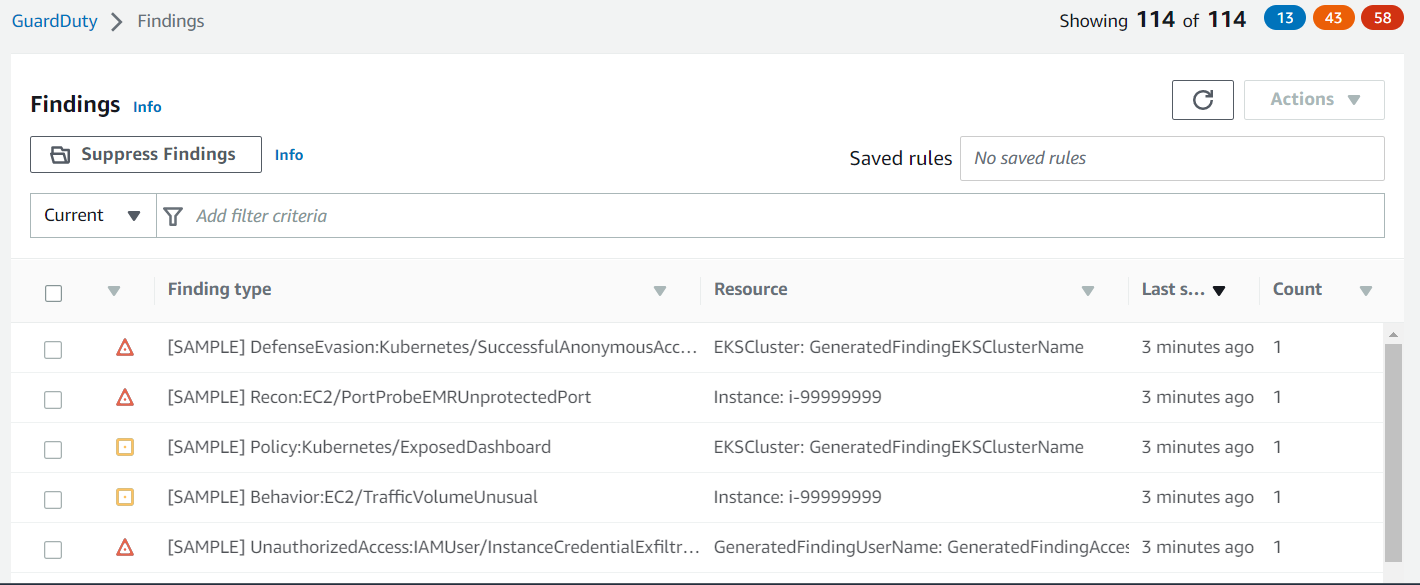
Sample GuardDuty findings with severity level and finding types.
GuardDuty aggregates information into a single finding instead of creating new findings for similar suspicious activity. When related activity is detected, GuardDuty updates the existing finding with the new information.
There are numerous finding types related to multiple AWS services. You can read more about the finding types here. For example, finding type CryptoCurrency:EC2/BitcoinTool.B is related to identifying an EC2 instance querying a bitcoin/crytpocurrency IP address. It utilizes the VPC flow logs and threat intel feeds from various sources to correlate and identify suspicious requests from an instance.
GuardDuty findings require further investigation in light of the context associated with the environment to identify the finding as a true positive. A true positive indicates an EC2 instance is compromised and requires further host-level investigation.
Filter findings
To investigate a finding or to identify and display the findings that meet certain criteria, you can utilize the option to filter. You can create the filter using API or console based on the selected criteria. You can view all the filtering attributes here.
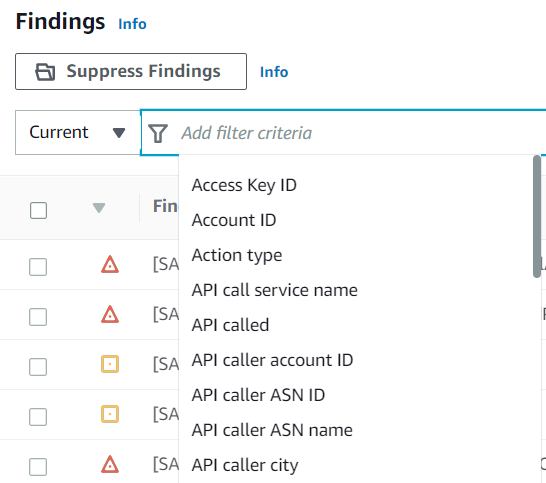
Add filters to GuardDuty findings using the console.
Suppress findings
Based on the investigation of the findings, you can opt to suppress findings related to legitimate activities. For this, use suppression rules to archive findings that meet your defined criteria. The suppressed findings are automatically archived and do not generate CloudWatch events.
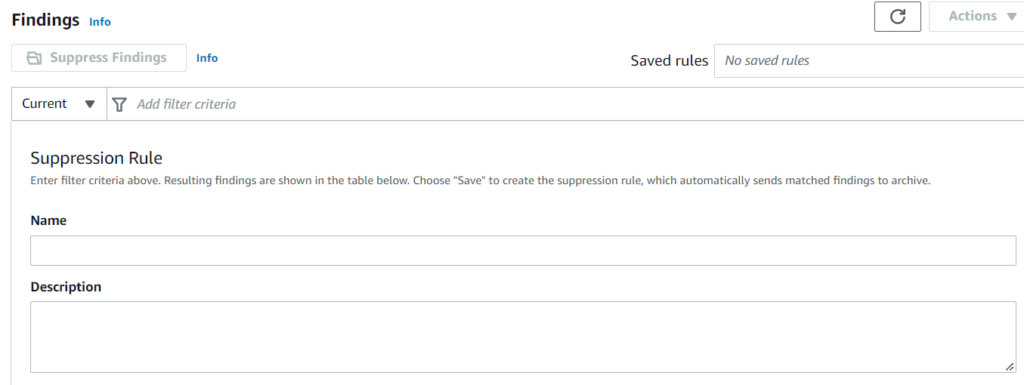
Fig. Creating suppression rule using the console
Trusted IPs list
You can identify and list the trusted IPs for your environment in GuardDuty. The GuardDuty Trusted IPs excludes IP addresses from being analyzed or flagged.
You can also maintain a list of known bad actors for your environment or the industry in general and add it to the managed lists in GuardDuty. Activities from these IPs are flagged as findings by GuardDuty.
Trusted IPs and Threat IPs can be added to GuardDuty from the console.
Customize responses to findings with CloudWatch events
To respond quickly, you can configure a CloudWatch event rule to notify you of new findings. You can configure it by following the steps mentioned here. Also, optionally to meet your compliance requirements, you can configure the export of GuardDuty findings to S3. You can use the remediating recommendations by Amazon to investigate and respond to the findings, shared here.
AWS GuardDuty Best Practices
There is no one-size-fits-all GuardDuty configuration that will work for every organization. However, there are some guiding principles and AWS GuardDuty best practices that can help you make informed decisions.
Below are seven key GuardDuty best practices to that can help you improve your AWS security posture.
- Use AWS GuardDuty in all your regions– Organizations should enable GuardDuty in all regions to identify malicious activities wherever they occur. This best practice includes enabling GuardDuty for unauthorized regions and regions that are not utilized by your applications.
- Link all your AWS accounts– Linking all AWS accounts to a single GuardDuty account provides you with a holistic view of your organization’s cloud assets.
- Enable Malware Protection– GuardDuty Malware Protection helps you take a proactive approach to security. You should configure Malware Protection to actively scan all of your environments (and at least production environments).
- Record known trusted IPs– Context matters in security. To get the most out of this popular AWS security solution, maintain a list of trusted IPs (e.g, your VPN IPs, Enterprise network IPs, etc.) in GuardDuty.
- Track potentially malicious IPs– Certain IP addresses may be particularly concerning. You should track these IP addresses in the GuardDuty threat IP list. To keep the list current, consider scanning threat intel feeds every week to identify relevant threat actors and add their IPs to the threat IPs list.
- Act on findings quickly– Fast response times can minimize the damage a threat actor can cause. To investigate and remediate the findings quickly, enable CloudWatch event notifications to notify you of new findings.
- Address false positives proactively– False positive alerts waste your time and resources. After you identify a false positive, suppress it with descriptive criteria to suppress similar nuisance alerts (i.e, fine-tune your environment).
Conclusion
AWS GuardDuty is a tool that can identify potential security issues in an environment. A fine-tuned GuardDuty configuration can help you actively identify security issues in near real-time. Understanding how GuardDuty works and using the best practices we reviewed here can help you get the most out of the platform.
Monitoring enterprise systems can become complex. The manpower needed to track and remediate every misconfigured cloud asset and security risk is scarce. Nowadays, cloud security is of high priority. Though GuardDuty can help identify security issues, it doesn’t resolve them. Such is a daunting feat for an IT team who cannot possibly surveillance countless assets and disparate systems. Consider using a free and open-source tool such as Paladin Cloud‘s open-source Cloud Security Posture Management (CSPM) platform, which can improve your clouds’ situational awareness through its continuous monitoring, unified visibility, proactive threat detection of risks (i.e misconfigurations of assets), and automated remediation of security violations.

