Containers are increasingly popular in computing environments because they solve several common problems. They help with dependency management, environment consistency, continuous deployment, resource utilization, and environment isolation.
Amazon Web Services (AWS) provides several services that can help you deploy containerized workloads in the cloud, including Elastic Container Service, AWS Fargate, and Elastic Kubernetes Service. There are several different components related to AWS container security. Some components are common among all AWS container services. Others are specific to a service.
The fundamental AWS container security components are
- Image Security
- Container Users
- Secrets Management
- Networking
- Encryption
With ECS and EKS you are responsible for securing the underlying hosts (ECS and EKS worker nodes). This article will review AWS container security tools, their security benefits, and best practices for implementing them in your AWS environment.
AWS container security executive summary
The table below summarizes the AWS security services we will explore in this article and their benefits.
| Security Benefit | AWS Service | Benefit |
|---|---|---|
| Identity and access | AWS IAM | Control Access to AWS Services |
| Image scanning | Amazon Inspector | Automated continuous vulnerability assurance of container images and EC2 hosts |
| Credential security | Secrets Manager | Deploy containers without secrets in the images |
| Encryption | AWS KMS | Image Encryption at rest in Elastic Container Registry (ECR) |
| Regulatory compliance | AWS Audit Manager | Audit your AWS usage to simplify how you assess risk and compliance with regulations and industry standards |
| Auditing | AWS CloudTrail | Verify on authorized users perform authorized functions |
| Logging and log analysis | AWS Cloudwatch | Collect and visualize logs, metrics, and event data |
| Threat detection | AWS GuardDuty | Analyzes and detects threats within your AWS accounts |
AWS container security tools and their security benefits
Shared responsibility between the customer and AWS is AWS container security. This includes the responsibility for network configuration, customer data storage, data sensitivity, your requirements, and applicable laws and regulations. AWS offers many security tools to help secure containerized workloads running in the cloud. The following sections will review these native security tools and their benefits.
Identity and Access: AWS IAM
AWS IAM (Identity and Access Management) is essential for AWS container services because it provides a central method for managing access to container resources and services. This includes managing and controlling access to container clusters, task definitions, tasks, and services and granting and revoking access for individual users, groups, and applications.
IAM also enables temporary security credentials to access ECS resources, allowing for more flexible and dynamic access control. Overall, IAM helps ensure the security and integrity of ECS environments while providing a scalable and flexible way to manage access and permissions.
Image scanning: Amazon Inspector
Amazon Inspector is a security assessment service that uses automation to continuously scan for vulnerabilities in container workloads, eliminating the need for manual intervention. Inspector will inspect container images stored in AWS Elastic Container Registry (ECR). This allows for faster detection of known vulnerabilities, reducing the average time it takes for an organization to identify and resolve security threats (known as Mean Time to Remediate, or MTTR).
Credential security: Secrets Manager
With AWS Secrets Manager, you can securely store and manage sensitive information, such as database credentials, API keys, and other secrets. Secrets manager can be integrated into your containers workloads which helps to create a zero-trust environment by reducing the number of shared secrets. With AWS Secrets Manager, there is no need to store passwords in applications. Authorized applications can access the secrets, and access can be controlled and monitored using IAM policies and AWS CloudTrail. Additionally, AWS Secrets Manager provides encryption and rotation capabilities to enhance security and prevent potential breaches.
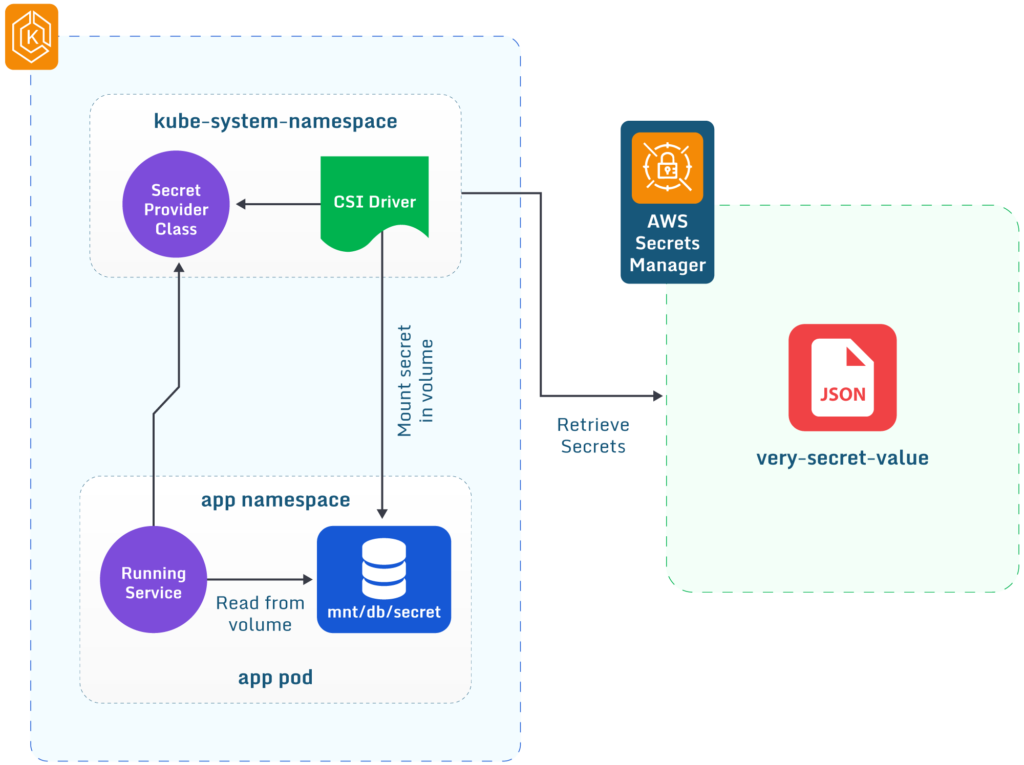
Diagram of Secrets Manager integration with Amazon EKS.
Encryption: AWS KMS
AWS KMS (Key Management Service) has several benefits to container workloads. Its primary utility is providing a central and secure way to manage encryption keys. This is important for container workloads because containers often need to access and store encrypted data, such as personally identifiable information (PII), and other protected data.
With AWS KMS, encryption keys can be centrally managed, accessed, and rotated, making it easier to ensure the security and integrity of containerized data. Additionally, AWS KMS allows hardware security modules (HSMs) to provide additional protection for keys and enables encryption policies and audits to monitor and control access to keys. KMS keys can also encrypt container images stored in AWS ECR.
Regulatory compliance: AWS Audit Manager
AWS Audit Manager is a service that provides a centralized way to automate the compliance of workloads with regulations and industry standards. This is particularly useful to container workloads because these compliance audits can be integrated into container build pipelines, assuring only compliant workloads can be deployed. AWS Audit Manager allows organizations to create custom audit plans and workflows, assign audit tasks to team members, and it provides tools for reviewing and approving evidence, as well as generating reports and assessments.
Auditing: AWS CloudTrail
AWS CloudTrail is a service that provides visibility into AWS activity to verify that authorized users perform specific functions. This is helpful for container security because it enables organizations to track and monitor access to and usage of their containerized applications and services.
For example, CloudTrail logs API calls made to the ECS and EKS APIs, allowing organizations to see who is running containers, what actions they are performing, and when they are taking place. This information can be used to identify and prevent potential security issues, such as unauthorized access or misuse of containers. Additionally, AWS CloudTrail integrates seamlessly with Cloudwatch and AWS SNS to provide alerting and notification, allowing organizations to respond to potential security incidents quickly.
Logging and log analysis: AWS CloudWatch
AWS CloudWatch is a service that provides centralized logging, monitoring, and alerting for AWS workloads which ensures the availability and reliability of applications and services. This is helpful for container workloads because containers are ephemeral and do not retain their state after they are terminated.
CloudWatch enables the centralized and persistent storage of log files, which can be analyzed after the container has been terminated. CloudWatch also helps provide visibility into the performance and health of their containerized applications and services. It has tools for alerting and notification, allowing quick response to potential performance issues or outages.
Threat detection: AWS GuardDuty
AWS GuardDuty analyzes and detects threats within your AWS accounts by extracting specific data from various data sources (e.g., AWS CloudTrail and AWS CloudWatch). In transit, data is encrypted when communicating with other services. Once data is extracted, the remnants of the source are discarded. The extracted data is then used to identify anomalies that pose as suspicious activity. Findings are aggregated into a listing – specifying the severity level and type of threat.
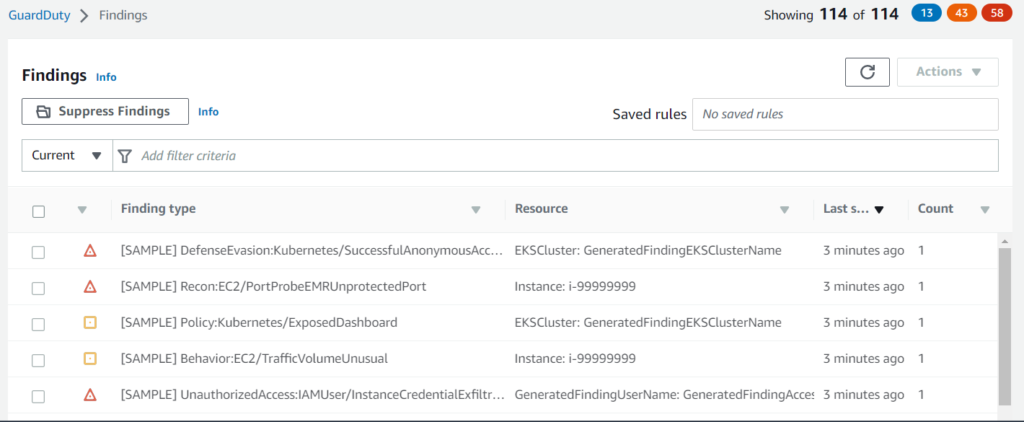
Sample GuardDuty findings with severity level and finding types.
AWS container security best practices
The following section provides several recommendations to help you implement secure container workloads in AWS.
Do not run containers as root
Containers should not run as root because running as root gives the container access to the host system’s root user privileges, which could be used to compromise the security of the underlying host and other containers running on the host. When a container runs as root, it has unrestricted access to the host system’s resources. It can modify or delete critical system files, install malicious software, or access other containers or the host system’s network.
Running containers as non-root users ensures that the container has only the permissions and access it needs to perform its intended function. This helps improve the system’s security and stability and reduce the impact of security vulnerabilities.
Only run official images
It is highly recommended to only run official base images, which are images released by a vendor. Official base images are typically more secure and reliable than unofficial images. Official base images generally are built, maintained, and supported by a vendor that ensures the images are updated with the latest security patches and updates. Unofficial images may include outdated or vulnerable components.
Utilize the AWS Security Maturity Model
The AWS Security Maturity Model is a framework that provides best practices for improving the security of workloads in AWS. The AWS Security Maturity Model includes five levels of security maturity, ranging from “basic” to “innovative,” and provides recommendations and guidance for moving from one level to the next. It helps organizations understand their current security maturity level and provides guidance on improving their security posture over time.
Consider using Third Party Tools
Third-party tools can be used to help secure your AWS Container workloads. They identify and assess potential vulnerabilities – quickly, efficiently, and continuously evaluate the security of their AWS environments. These tools provide recommendations on improving their security posture and help identify and address potential vulnerabilities and compliance issues.
Conclusion
Deploying containerized workloads in AWS can be challenging from a security perspective. Fortunately, with proper implementation of these native tools and recommendations mentioned above, organizations can enhance their security posture.
Tooling is available from AWS and third-party vendors — such as Paladin Cloud’s open-source Cloud Security Posture Management (CSPM) platform — that improve security, compliance, and vulnerability remediation. Paladin Cloud provides best practice security policies and monitoring for EKS, IAM, and KMS services.

