Cloud providers are responsible for protecting their infrastructure. However, the customer is also responsible for ensuring the services they run on the platform are as secure as possible. Spending time and money manually managing security configurations, threat detection, and the myriad other crucial components of modern security infrastructure is time-consuming and expensive.
This is where security automation comes in. It helps the customer introduce security patches and features as quickly as possible.
AWS security automation integrates automatic management, creation, detection, and response solutions to your AWS infrastructure. You can implement security automation with native AWS services and external options like Cloud Security Posture Management (CSPM) tools.
This article will review AWS security automation benefits and tools in detail.
Summary of AWS security automation key benefits
Before we get into the underlying technology explaining how security automation works, let’s briefly overview why engineers recommend this approach.
| Benefit | Description |
|---|---|
| Efficiency | Quickly, consistently apply security controls across an environment. |
| Accuracy | Less prone to human error, created with code instead of knowledge. |
| Scalability | Scales up with infrastructure without needing to hire anyone extra. |
| Response time | Automation can help you quickly detect and respond to security threats and incidents, minimizing impact of potential breaches. |
| Consistent Compliance | Reliably audit Infrastructure as Code for compliance and use integrations to achieve compliance easily. |
| External integrations | AWS allows you to integrate more sophisticated, external CSPM (Cloud Security Posture Management) frameworks like Paladin Cloud. |
AWS security and automation
AWS takes measures to protect you, but they do not do everything. Security is the responsibility of both you and AWS. These shared measures of security are also known as the Shared Responsibility Model.
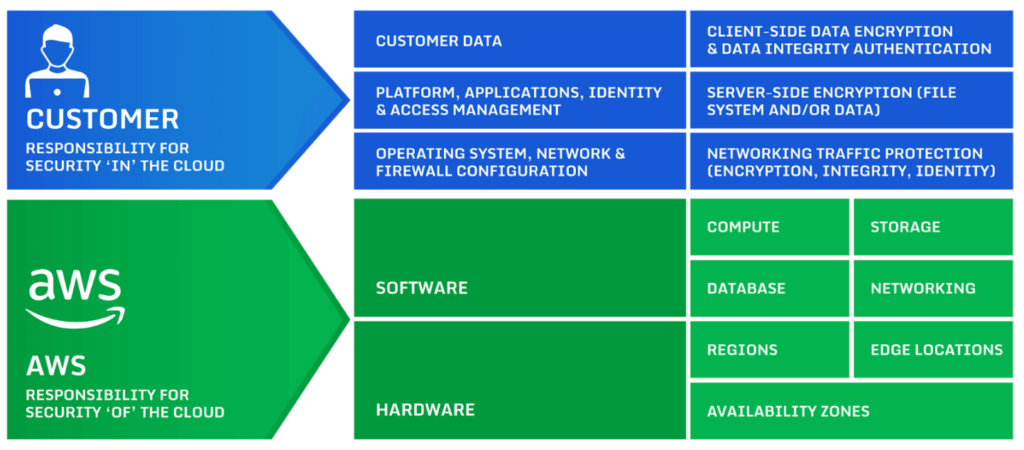
AWS clearly defines what parts of security are their responsibility and what the customer is expected to handle independently. (Source).
Services provided by AWS to help you protect your infrastructure and data include :
- IAM
- VPC
- KMS
- AWS Config
- Web application firewall (WAF) and AWS Shield
Integrating services requires work and knowledge of how they work and interact. Manually provisioning AWS security resources is time-consuming, especially if you have complex infrastructure. Manual security integration is also prone to human error. It could introduce difficulties in maintaining consistent security. Finally, manual security work is less likely to receive constant, regular updates, leading it to drift into outdated versions that are exploitable.
AWS provides various automation tools that can help you streamline and automate security tasks, including:
- Applying security patches
- Rotating access keys
- Detecting threats
- Incident response
Here’s an example architecture using AWS tooling to detect, ingest, remediate and log threats on a cloud infrastructure.
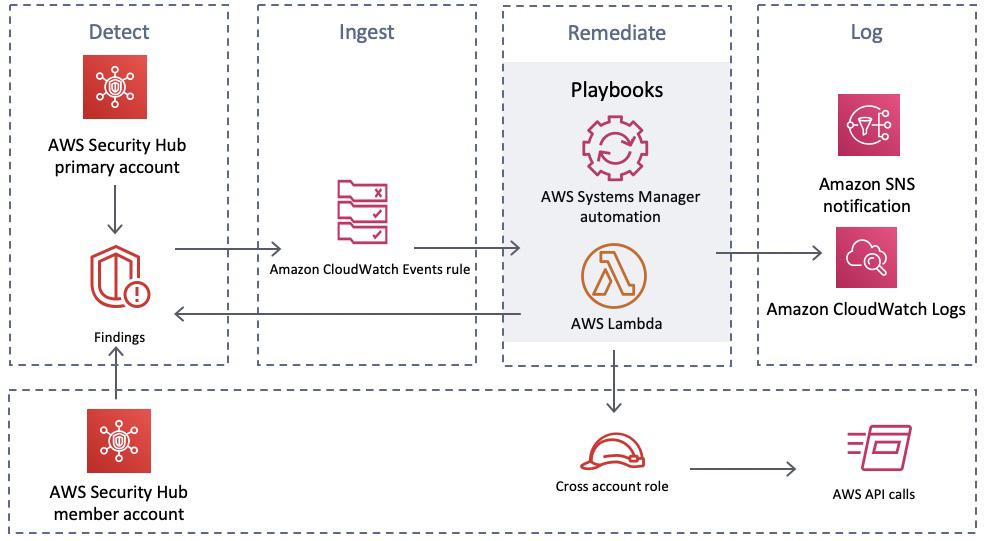
AWS tooling works together to build a secure infrastructure. (Source)
AWS security automation
There are numerous ways to integrate automation into your AWS infrastructure security. Below we will go through some of the most popular AWS integrations to give you a crash course on what’s available and how it works.
AWS Config and automatic remediation of noncompliant rules
AWS Config is used to assess, audit, and evaluate the configuration of your AWS Resources. By setting AWS Config managed rules, you will enable your team to oversee operations and changes in your infrastructure. Some scenarios in which AWS Config helps are:
- Resource Administration: Evaluate configuration settings using AWS Config rules. If one of your resources violates any of the conditions from your rules, AWS Config will flag the resource as noncompliant and send a notification.
- Auditing and Compliance: Demonstrate compliance by using AWS Config to access historical configurations of your resources.
- Managing and Troubleshooting Configuration Changes: AWS Config helps you view changes you have made to your infrastructure configuration by showing you how a given change would impact other AWS resources.
- Security Analysis: You can analyze potential security weaknesses in your infrastructure by using the detailed historical information provided by AWS Config regarding your resources.
The good news is all of the above scenarios can be automated. AWS Config supports automatic remediation by using AWS Systems Manager. This tool automatically helps you resolve noncompliant AWS Config rules using Systems Manager Automation Documents (runbooks).
According to the scenarios above, you should already have a few standard compliance rules set. When an AWS resource is found to be noncompliant, you can specify a remediation action through an AWS Systems Manager automation document. Using a Systems Manager Automation document, you can define custom automatic remediation for every rule.
AWS Security Hub
AWS Security Hub helps you manage security across all of your AWS services including SOAR (Security Orchestration, Automation and Response) and SIEM (Security Information and Event Management). However, AWS Security Hub is limited in that it does not support multicloud nor hybrid cloud environments.
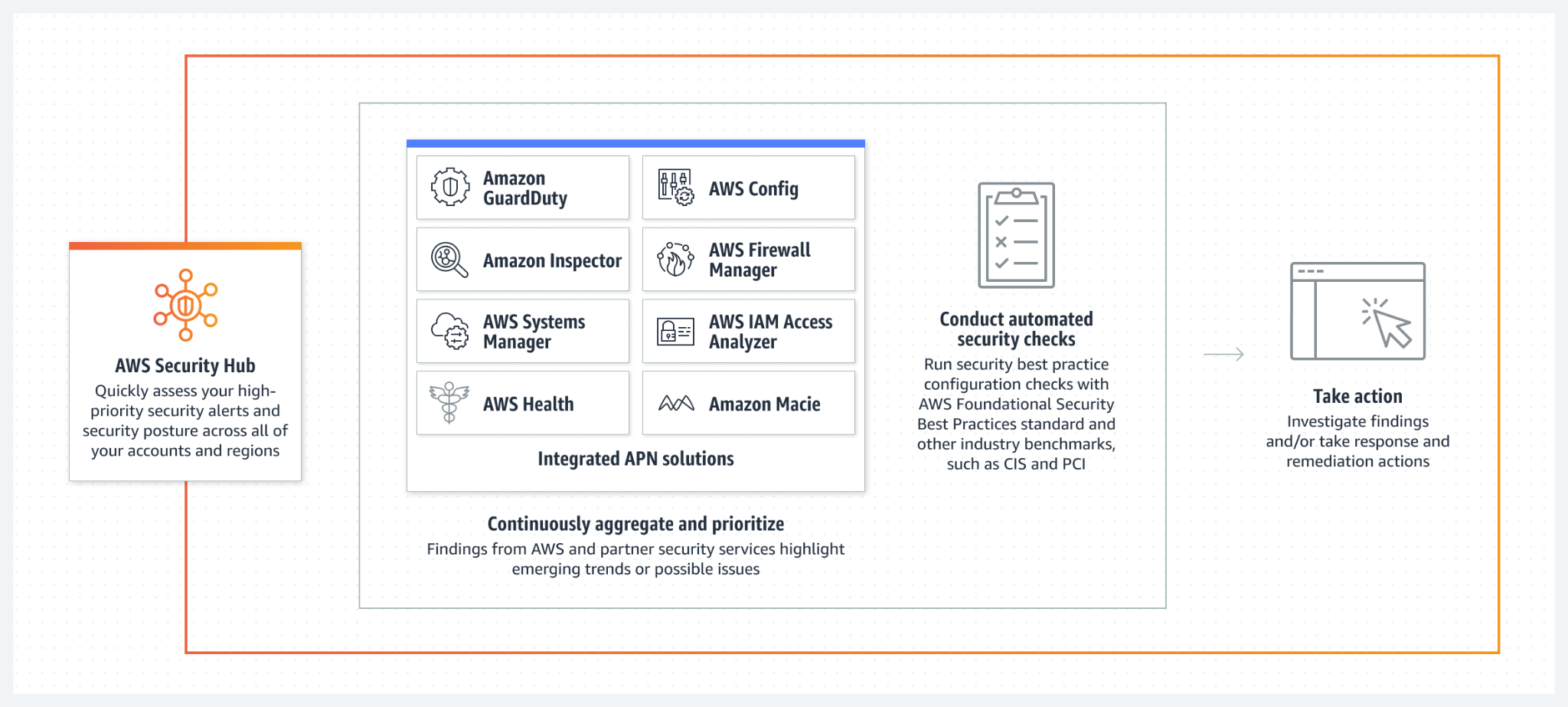
An overview of AWS Security Hub integrations and automation. (source)
SOAR is designed to help teams by incorporating automated responses to various events. It combines three software capabilities: managing threats and vulnerabilities, responding to security incidents, and automating security operations. With SOAR, threats are first identified, and then the response strategy is implemented. This process is then automated to make it run more efficiently. A SOAR integration’s main objective is to increase the effectiveness of security operations. Security Hub integrates with various AWS Services for you to implement SOAR effectively in many different AWS environments.
A security information and event management (SIEM) tool combines data from different sources and uses analytics to detect the most likely threats. A SIEM tool also integrates with Security Hub to help you maximize your cloud security. It combines the management of security information and security events. This is done through real-time monitoring and notification of system administrators. A solution for using SIEM with Security Hub to aggregate findings across multiple accounts, store findings in S3 buckets indefinitely, and correlate multiple AWS and non-AWS services in one place for visualization is integrating your Security Hub with a SIEM solution on AWS Services like S3, Lambda, Kinesis, SNS and OpenSearch.
The picture below shows the architecture of such a solution when using your Security Hub. You can aggregate your findings, send them to an S3 Bucket, have an ETL process in place through AWS Lambda, and analyze/visualize your data through OpenSearch. You can also send notifications to your administrators/users through SNS.
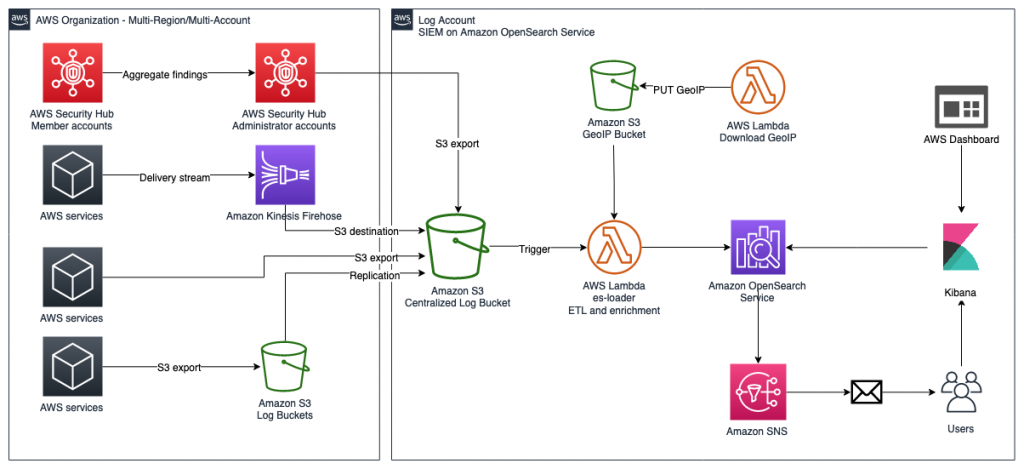
AWS Security Hub powers a variety of security services (source).
You enable Security Hub through the AWS Console or AWS CLI. On the AWS console, you can enable it on the AWS Security Hub console, and when enabled, you can then check or uncheck whichever standards you want your infrastructure to follow.
Automatically block suspicious traffic with AWS Network Firewall and Amazon GuardDuty
Another solution for implementing security response automation is by using AWS Network Firewall to automatically respond to security events in your AWS infrastructure that GuardDuty detects.
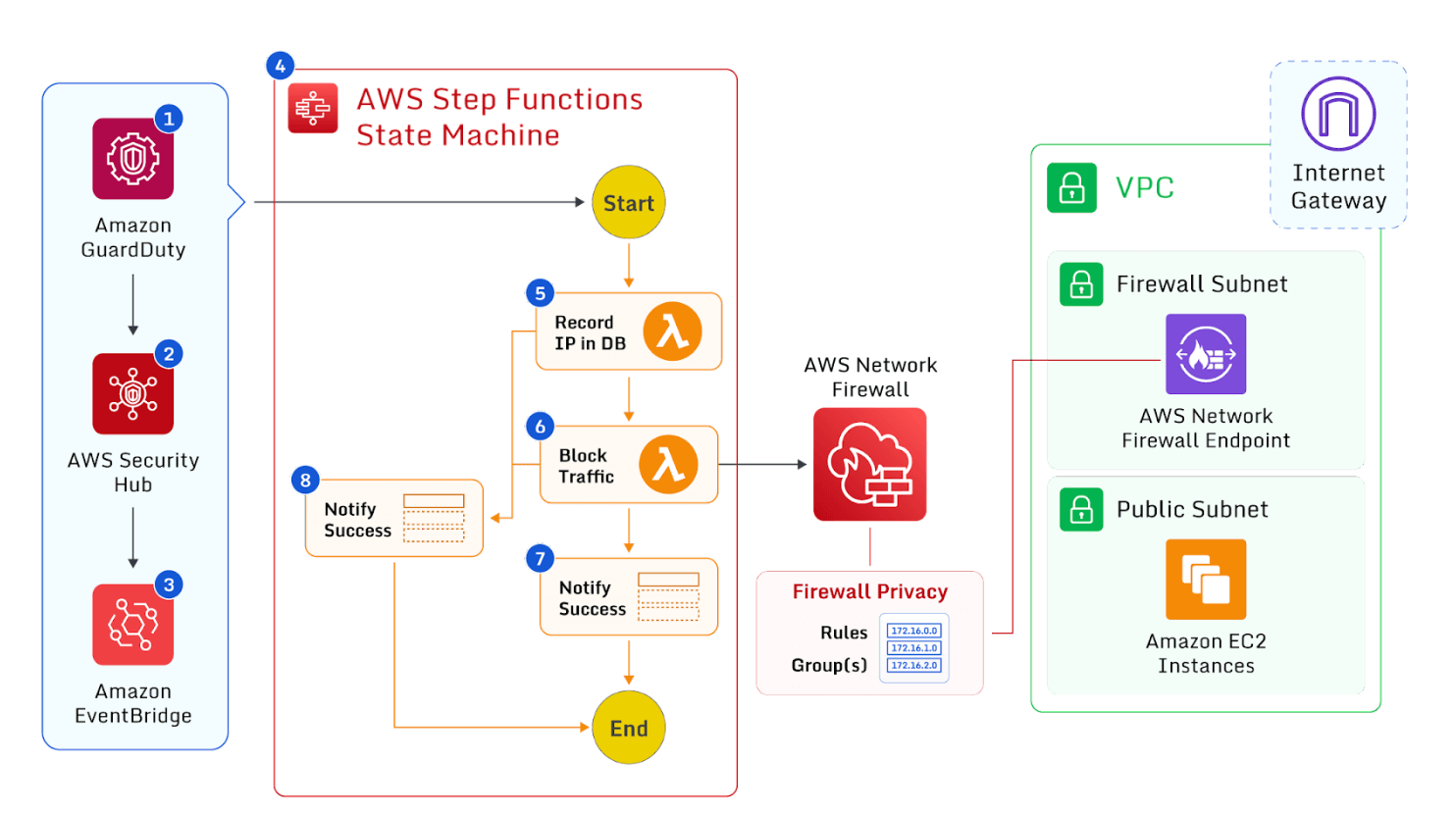
AWS security automation workflow with Amazon GaurdDuty, AWS Security Hub, and Amazon EventBridge.
The diagram above shows a detailed overview of the solution where GuardDuty detects unexpected behavior and generates a finding in JSON format which includes metadata such as account information, type of attack and remote IP. Security Hub then ingests the findings generated by GuardDuty and publishes its contents to Amazon EventBridge. EventBridge routes the event to the designated target which, in our case, is a Step Functions State Machine.
The Step Functions state machine ingests the details of the security hub findings and orchestrates the remediation depending on your action. For example, if the remote IP from the results is a record of our DB, make no changes to the AWS Network Firewall, otherwise, if it’s a new IP, Block Traffic. For more information on this solution provided by AWS, check out the AWS Security blog on the topic.
Automating creation and rotation of IAM Credentials
Automating the creation and rotation of AWS IAM user credentials is one of the solutions you can implement to improve your security automation further. You can do so by having a Lambda, which can check for keys older than 90 days. Then, either notify the users that their keys have expired or you can rotate them and send them to your AWS users through a secure channel. The complete infrastructure will involve AWS Lambda, where your code will reside, Amazon EventBridge, which will trigger the Lambda, and SNS, which will email your end users. Here’s what the infrastructure will look like:
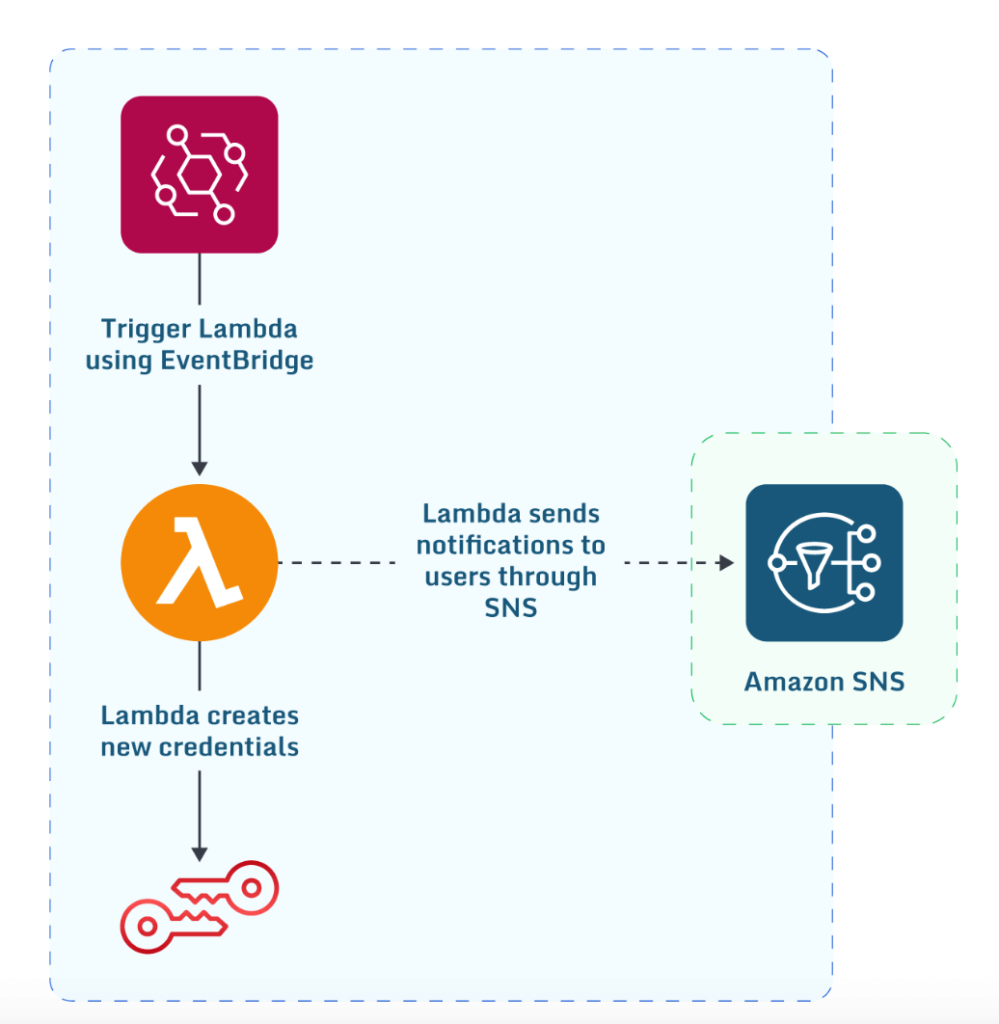
A Lambda trigger using EventBridge that can create new credentials and send an SNS notification.
Automating the creation and management of AWS resources
Integrating automation in your AWS infrastructure provisioning is one of the best ways to automate your security implementations and tighten your security. Resources like VPC, Subnets, and Security Groups can all be automatically provisioned and managed using IaC (Infrastructure as Code). Automating the process of creating and managing resources like VPCs can help you ensure your infrastructure is protected from unauthorized access.
A streamlined deployment process using Infrastructure as Code (IaC) and CI/CD helps you by allowing your organization to define and enforce security policies as code, which can be automatically checked and enforced during the deployment process. This can help to prevent misconfigurations and reduce the risk of security vulnerabilities. IaC can also make it easier to audit and verify the security of your infrastructure since the configuration can be easily reviewed. For example, you could use IaC to define security policies such as “all public facing servers must have firewall rules in place to block all incoming traffic except on port 80” or “all data stored in cloud storage must be encrypted at rest”. You can have these policies automatically checked and enforced during the deployment process, helping you to ensure that the infrastructure is securely configured.
You can also incorporate security automation into your CI/CD process. Your CI/CD pipeline can automatically run testing tools whenever code is committed to a repository. This can help you catch issues early in the development process. Your CI/CD pipeline can also have manual code reviews by providing a way to stage code changes and make them available for review by other team members before deployment to production. This can help ensure that code changes are reviewed and approved by appropriate team members before release. This implementation can also be done by using the AWS Code services (CodePipeline, CodeDeploy, and CodeBuild).
AWS Key Management Service is another service used to configure and manage your cryptographic keys across your environment and other AWS services. KMS can be automated directly on the service itself, which you can use to create, rotate and destroy keys.
All the implementations we have gone through will work if you exclusively use AWS. But what if you’re running a cloud-hybrid infrastructure with multiple cloud providers?
That’s where open-source Cloud Security Posture Management (CSPM) solutions like Paladin Cloud come in. Integrating an external CSPM comes with a bundle of benefits. Using Paladin Cloud as an example, you get:
- Continuous Asset Discovery
- Continuous security policy evaluation
- Detailed Reporting
- Easy to use Self-Service portal
- Custom policies and custom auto-fix actions
- Ability to create multiple compliance domains
- Unlimited AWS, Azure, and GCP Accounts
And many more, which you can find in this GitHub repository.
Summary
In this article, we have gone through what AWS Security is, what automation means in the scope of AWS Security, how you can achieve it, and multiple implementations you can integrate into your infrastructure quickly. You can use the integrations provided by the cloud providers themselves, which are very easy to set up, and you can have security automation in minutes.
However, only relying on the cloud providers means you won’t have full control over the rules and scenarios you have set up. If you want more control over your security automation, consider a CSPM like Paladin Cloud.

