Microsoft Azure is a leading public cloud provider. It offers a broad range of services, including compute, analytics, storage, and networking. These services tightly integrate with the Microsoft ecosystem making Azure a popular choice for enterprise workflows.
Just like with any other technology, security is a top priority for Azure. While data breaches and cyber threats are rising, protecting sensitive and business data is becoming more critical. Microsoft employs a multi-layered approach to enforce strict security controls and mitigate these risks.
This article will explore Azure security tools in detail, including their capabilities and limitations. Additionally, we’ll review where third-party tools can help address use cases native Azure security tools cannot.
Summary of key Azure security tools concepts
The table below summarizes five popular native Azure security tools and their capabilities. We’ll take a closer look at each tool later in this article.
| Concept | Description |
|---|---|
| Microsoft Defender for Cloud | Comprehensive security solution to protect cloud workloads from advanced threats |
| Azure Information Protection | Classify, label, and protect sensitive data to ensure confidentiality and compliance. |
| Azure Sentinel | Cloud-native security information and event management (SIEM) tool that provides deep insights into an organization’s security posture. |
| Azure Policy | Governance service to enforce and automate rules and compliance requirements across Azure resources. |
| Azure Web App Firewall (WAF) | Security solution to protect web applications from common vulnerabilities and malicious attacks. |
In-depth analysis of Azure security tools
The sections below take a deep dive into five of the most popular native Azure security tools that can help organizations improve their cloud security posture,
Microsoft Defender for Cloud
Securing user and resource data in the cloud is hard, and the risk of vulnerabilities increases as the organization grows. A best practice is to leverage a tool that can grow with your organization. Defender for Cloud leverages the latest threat intelligence from various data sources to analyze the data and produce strong detection patterns to mitigate the risk. While trying to scale with the demand, Defender for Cloud enables organizations to centrally manage the resources and integrate with third-party vendors.
Core features of Defender for Cloud include:
- Cloud Security Posture Management (CSPM)– The ability to maintain a robust security posture for the cloud resources based on best practices. See our security posture webinar for more information.
- Threat protection- Provides a detailed threat protection platform with advanced intelligence and machine learning algorithm to detect and remediate security attacks.
- Security and risk visibility- Insights about the latest vulnerabilities and construct surveillance of cloud systems to mitigate the risk and reduce the overall threat exposure.
Microsoft Defender for Cloud
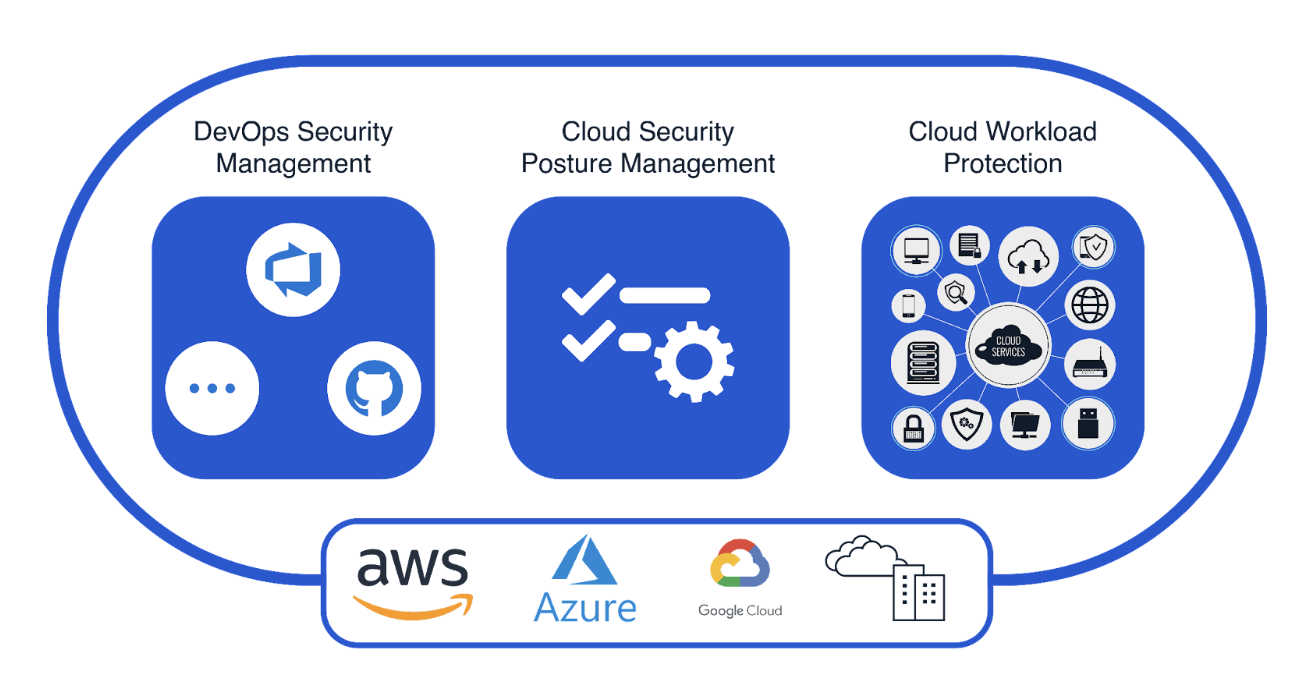
Microsoft Defender for Cloud with three primary offerings including DevOps Security Management, Cloud Security Posture Management and Cloud Workload Protection. (Source)
Azure Information Protection
Data security and labeling are the first steps toward building a secure work environment. Organizations need to understand the kind of data flowing across the organization and require a method to categorize the data into different groups to govern data leakage. Unfortunately, the out of box tools do not provide enough exposure and flexibility to classify and label the resources and the content within those resources.
To deal with this ongoing need for data labeling, Microsoft offers Azure Information Protection (AIP). AIP specializes in data classification and labeling, allowing you to secure and regulate data sharing within and outside the organization. One of the key remarks of this service is that it seamlessly integrates with other Microsoft products such as Word, Excel, and PowerPoint, allowing users the comfort of working within a familiar environment.
Azure Sentinel
Organizations have increasingly started shifting their workloads to the cloud from the on-premises environment, increasing the resources they have to manage and deal with daily. The growing number of resources in the cloud also calls for complexity and a struggle to keep up with the tools to secure the environment. As with any traditional security information and event management (SIEM) tool, managing the cloud environment gets expensive and complex, often resulting in false positives and challenging to identify threats.
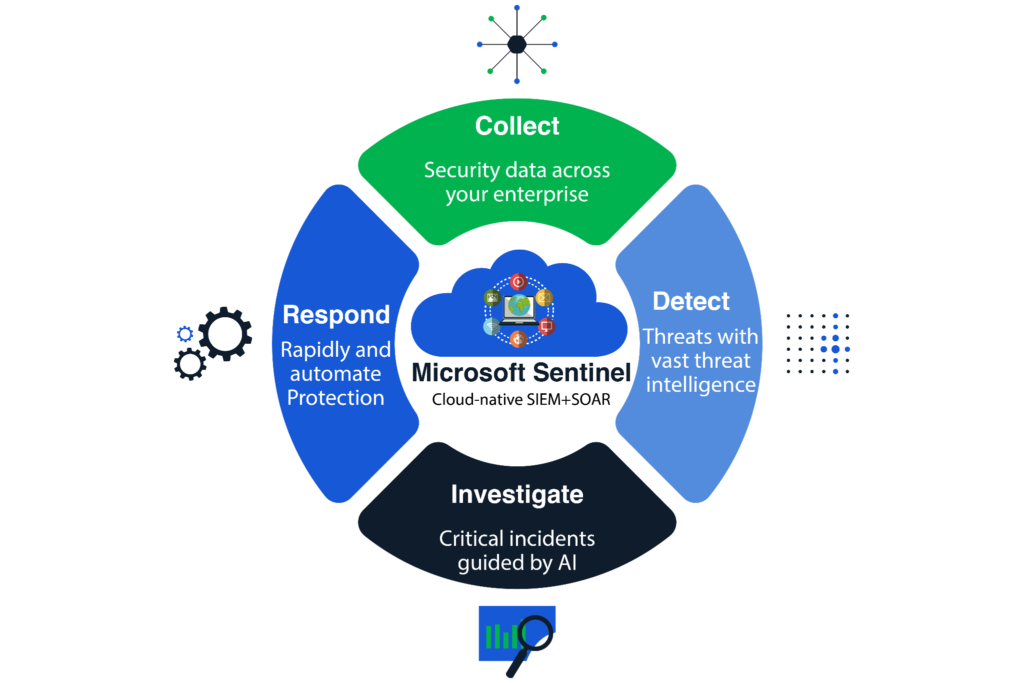
The four primary pillars for Azure Sentinel service in Azure. (Source)
Azure Sentinel provides a bird’s-eye view of all cloud resources while extending its capabilities to secure and protect all assets from potential threats and sophisticated vulnerabilities using Artificial Intelligence (AI) and Machine Learning (ML) models. Sentinel is scalable and can grow with your organization.
Along with threat identification based on rich data collected from various sources, it provides actionable insights using interactive dashboards and automated response playbooks to reduce the burden on the security team. The tool uses large trained datasets to detect patterns and behaviors to match known malicious activities, allowing the system to quickly flag and prioritize the incidents. It also involves analyzing user behavior, network traffic, and system activity to compare against the normal baseline behavior.
Azure Policy
Moving the workloads to the cloud becomes increasingly complex when resource management and monitoring are not configured properly. Organizations often look for ways to enforce compliance, governance, and standardization across Azure resources.
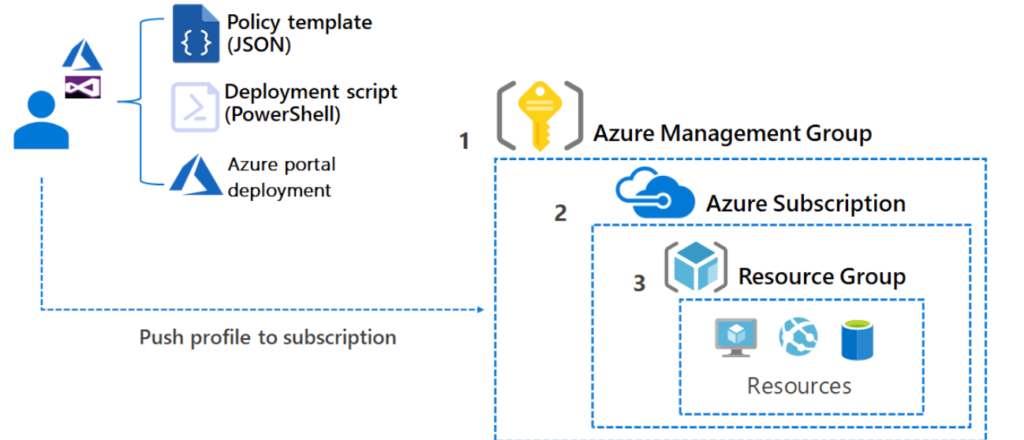
An Azure Policy overview along with deployment scope and process. (Source)
Azure Policy brings the capabilities to manage Azure resources with policies to create, delete, enforce, and audit the cloud systems over time to find mismatched configurations and drifts in the infrastructure. One of the most powerful aspects of Azure Policy is its ability to remediate and prevent resource misconfiguration from being deployed in the first place.
Azure Web Application Firewall (WAF)
Cloud applications hosted on the public cloud are becoming the target of cyber attacks daily. Web applications are the prime target for attackers due to their public accessibility, and they often link to valuable data hosted in the organization’s account. Azure WAF protects these web applications from malicious attackers and common vulnerabilities.
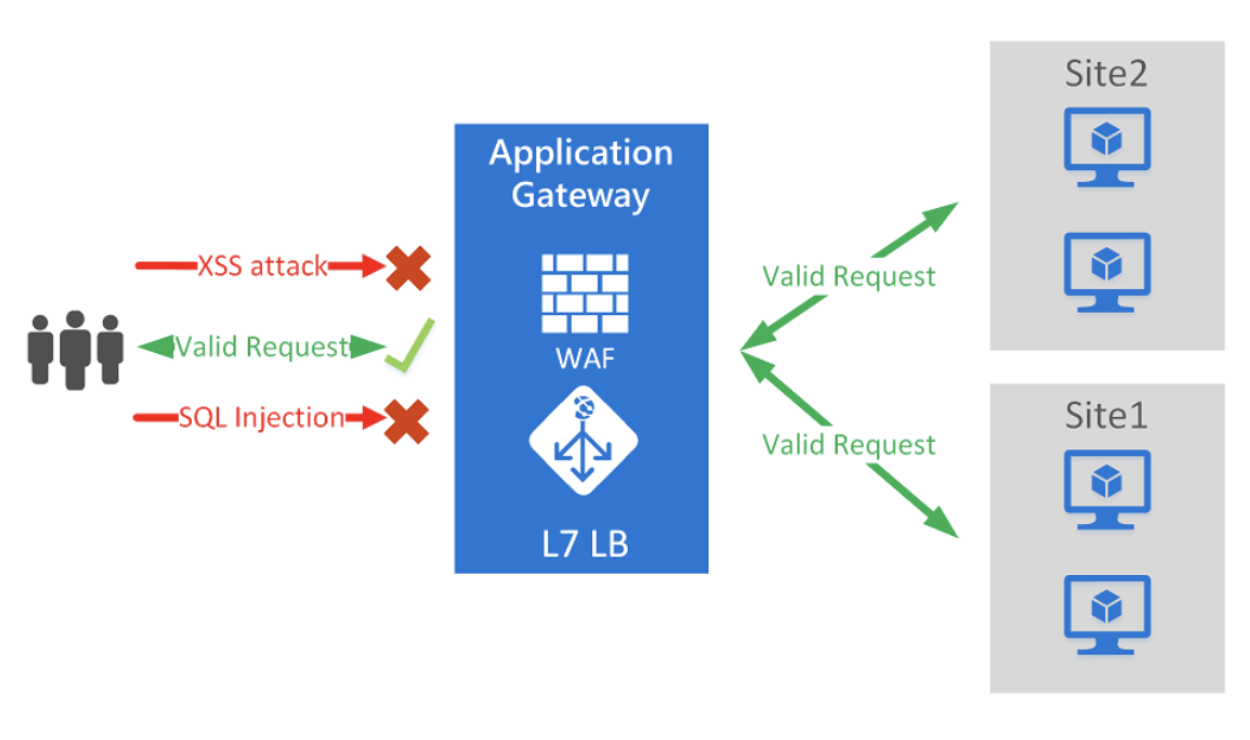
An Azure WAF implementation and traffic flow indicating blocked and allowed requests. (Source)
The key component of Azure WAF is its integration with native monitoring tools such as Azure Log Analytics and Azure Monitor to collect data and store the logs centrally. It also operates on public security frameworks such as OWASP Top 10 to classify security incidents and attacks.
Limitations of native Azure security tools
Every organization’s security requirements are unique, and it is safe to say that no single tool can provide comprehensive protection against security threats. However, each tool has its unique purpose for solving security challenges.
Microsoft Defender for Cloud
Despite the robust and comprehensive security offering of Defender for Cloud, its functionality for non-Azure environments is less developed. Additionally, the high cost of service, such as tier enforcement to use certain features, makes it inaccessible for organizations on a tighter budget.
Open-source security tools such as Paladin Cloud provide multi and hybrid cloud support, including Azure and other cloud service providers, to address many of Defender for Cloud’s shortcomings. Paladin Cloud serves as an enterprise security efficacy platform with a prioritization engine to detect threats and vulnerabilities, while driving remediation for the most important security risks across an organization’s cyber assets.
Azure Information Protection (AIP)
Some security tools require extensive initial effort to set up along with the learning curve to understand the basics of the service. AIP is no different. Moreover, the labeling and classification of documents are not always correct and may cause miscategorization in certain events as its pattern detection algorithm can lead to false positives. The process calls for manual verification and revision of the applied label to identify potential gaps.
Azure Sentinel
SIEM tools often get expensive as more data is ingested into the logging database. A similar case is for Azure Sentinel, as collecting data from various sources adds up the total storage capacity, significantly increasing expenses. Besides the cost, the integration with third-party applications and other cloud vendors is available with limited functionality. The integration feature is important to allow cross platform support and expand the native capabilities of Sentinel. Considering these factors, there may be better solutions for business use cases.
Azure Policy
While the Azure Policy excels at enforcing the policies and governance rules, security measures become easy to bypass as the infrastructure demands increase. Azure Policy cannot manage multi-cloud or hybrid-cloud environments.
Paladin Cloud can help address these gaps. With Paladin Cloud, organizations gain continuous compliance monitoring and multi-cloud support, making it ideal for covering the security gaps of Azure Policy.
Further, Paladin Cloud continuously assesses and monitors the environment to address misconfigurations in real time to reduce the risk of configuration drift. This not only helps with configuration management and streamlines compliance with standards and regulations such as HIPAA, PCI DSS, GDPR, and ISO.
Azure Web Application Firewall (WAF)
While Azure WAF has numerous benefits to protect the web application from common and sophisticated exploits, Azure WAF only focuses on the HTTP/HTTPS protocol and leaves the other protocols unprotected. The rules in the WAF also may only be able to cover some of the edge cases and require a high degree of expertise to configure and maintain the ongoing changes to the system. It is also important to mention that Azure WAF may not provide the defense to secure against zero-day exploits or advanced threats. This often encourages organizations to implement additional or alternative security solutions that suit their purpose.
5 Azure security best practices
Creating a secure and compliant Azure environment requires a comprehensive approach to security rules. Here are some tips to strengthen your cloud security posture:
- Use a landing zone to help develop your environment in line with Cloud Adoption Framework (CAF)’s best practices. This ensures secure cloud adoption, scalability, and consistency of security controls across the Azure environment.
- Automate With Azure PowerShell and CLI. Azure PowerShell and Azure CLI are powerful automation tools that can automate repetitive and complex tasks to avoid human error. This lifts off the manual work and brings consistency and accuracy to common tasks.
- Leverage third-party tools to fill gaps. Third-party tools like Paladin Cloud can amplify security posture management by implementing an additional layer of governance on top of the existing tools and across multi-cloud environments.
 Paladin allowing the onboarding of multiple cloud environments to aggregate security monitoring output into one security tool
Paladin allowing the onboarding of multiple cloud environments to aggregate security monitoring output into one security tool - Automate threat response and remediation. Automating the threat response and remediation using Azure Logic Apps and Azure Function is another option to achieve a fully automated and secure environment while leaving time for the engineers to improve the system rather than maintain it.
- Continuously monitor assets. Continuous monitoring and asset management are critical to infrastructure security and visibility. Tools like Paladin Cloud allow you to categorize and group assets based on business units, users, applications, and cloud services to implement data-driven decisions for the management of the environment.
Conclusion
Securing the cloud infrastructure is a process that requires continuous assessment, adaptation, and improvement. While Azure provides advanced tools to protect the data and resources in the cloud, these tools must be supplemented with third-party solutions like Paladin Cloud to enhance the security measures further and address the limitations of the native tools. A secure and compliant Azure environment comprises many parts, from leveraging native tools, implementing robust security policies, integration with the third-party solution, and ongoing monitoring to stay on top of a rapidly evolving cloud landscape.

