Microsoft Azure, like other cloud providers, operates under the shared responsibility model to maintain a secure environment for all users. While Azure focuses on securing the infrastructure, the user retains responsibility for several critical aspects, such as data protection, endpoints, account management, and access controls – vital aspects that you must proactively manage to prevent potential breaches.
This article focuses on the core aspects of the Azure shared responsibility model in the context of security, privacy, and compliance. We outline your responsibilities and the best practices and tools you can use to meet your security obligations when using Azure.
Summary of key concepts
Below is an example responsibility matrix to provide a view into the Azure shared responsibility model.
| Architecture element | Azure responsibility | Customer responsibility |
|---|---|---|
| Data storage | Azure manages the physical security and infrastructure of the data storage. | Customers manage data security, including classification, access control, and encryption settings. |
| Access to virtual machines | Azure ensures the availability and resilience of the VM service. | Customers manage access controls, network controls, and the operating system of the VMs. |
| Security monitoring | Azure provides the tools and services for security monitoring. | Customers must set up and manage the use of these tools to monitor their specific resources. |
| User accounts & identity management | Azure provides identity and access management services (like Azure Active Directory). | Customers manage their user accounts, including assigning appropriate roles, supervising permissions, and monitoring account activity. |
| Payment gateway integration | Azure provides secure and compliant services for integrating payment gateways. | The customer is responsible for secure integration with the payment gateway and compliance with PCI-DSS and other applicable regulations. |
| Website Content & Updates | Azure provides hosting services like Azure Web Apps, with built-in security features. | The customer must ensure that website content is secure, updated regularly, and not in violation of any laws or policies. |
What is the Azure shared responsibility model?
When using Azure for your application environment, you, as the user, and Microsoft as the cloud provider, are both responsible for the security of your cloud resources. The division of responsibilities, however, varies across the different cloud deployment models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Under an IaaS model, Azure only secures the fundamental infrastructure like Azure VMs or Blob Storage. Users are responsible for managing the security of all other infrastructure components, including the operating system, middleware, applications, and data.
In the PaaS model, Azure is also responsible for the security of runtime and middleware layers. Users are responsible for their application and data security.
It’s only in the SaaS model that Azure takes responsibility for the infrastructure and application security. Users still retain responsibility for data and application access management.
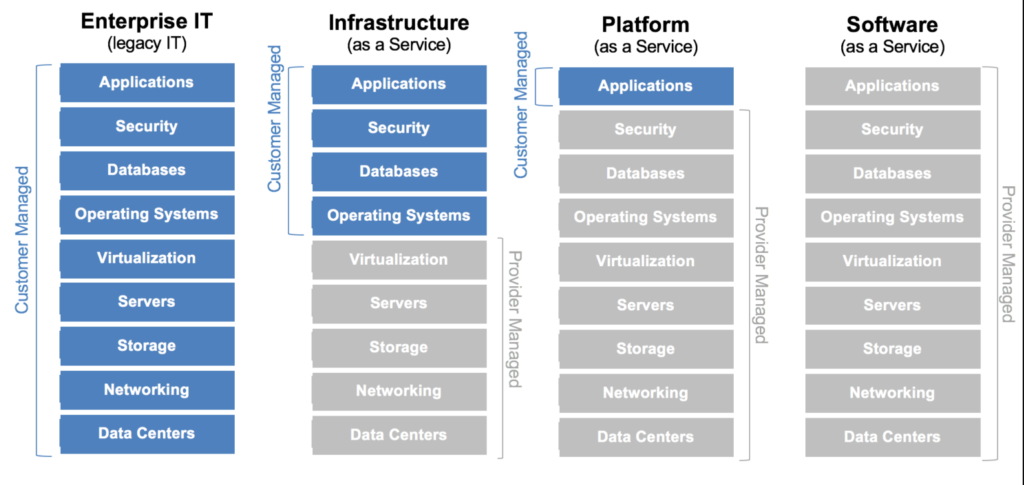
The image shows what a customer is responsible for vs. a cloud provider for the different cloud deployment models (Source)
Azure services and features
Azure provides a host of services tailored to various business needs. However, every service has different features and limitations. Azure’s Service Level Agreements (SLAs) ensure you know the service availability you can expect and the compensations in case of breaches. SLAs also provide insights into Azure’s commitments regarding incident response times and resolution procedures.
You must understand the complexities of the services you plan to utilize and how it aligns with your operational objectives. Doing so ensures you can leverage the full potential of Azure and enhance productivity while minimizing risks.
Azure Role-Based Access Control (RBAC)
Azure RBAC is vital in managing access to resources in your Azure environment. You can use Azure RBAC to grant only the necessary permissions to users, groups, and applications based on their roles and responsibilities. Both built-in and custom roles are available to meet your operational security requirements. You can also use Azure Privileged Identity Management (PIM) for additional controls and oversight over privileged access.
Best practices in the Azure shared responsibility model
We give below some best practices you can use to make sure you do your part in securing your Azure cloud applications. We summarize the best practices below.
| Concept | Description |
|---|---|
| Risk assessment | Draft a risk assessment outlining security, privacy, and compliance requirements. |
| Network security | Protect your data center and applications with stringent network security measures. |
| Application & data security | Understand ownership of application vulnerability management and data security efforts. |
| Leverage Azure Security Center and Azure Policy | Azure services for unified security management and policy-driven governance. |
| Regular security monitoring | Ensures consistent environmental surveillance for any anomalies or risks. |
| Incident response process | Maintain a transparent and efficient method for handling security incidents. |
#1 Create a risk assessment
Understand your system’s vulnerabilities and customize your security strategy to mitigate risks before they escalate to threats. Your risk assessment should be dynamic and evolving alongside your cloud environment. Outline and track all security, privacy, and compliance requirements. Be sure to regularly review and update RBAC permissions as roles or needs change.
#2 Implement network security measures
Network security includes configuring firewall settings, setting up Virtual Private Networks (VPNs), and ensuring secure data transit. Such measures help safeguard your operations from potential cyber threats. Further, use Azure’s encryption capabilities to secure your data at rest and in transit.
#3 Implement application and data security
Ensuring the security of your applications and data within Azure is a crucial aspect of your responsibilities. Understand the sensitivity of your data, classify it accordingly, and apply appropriate controls. Always adopt a least privilege approach for data access to mitigate the risk of unauthorized access.
#4 Maximize use of Azure Security Center and Azure Policy
Microsoft Azure Security Center is a set of security tools for managing and monitoring the security of virtual machines and other Azure cloud computing resources. Similarly, Azure Policy is a free Azure service that permits you to make security policies, assign them to resources, and receive alerts or take action in cases of non-compliance with the guidelines. Use Azure Security Center for unified security management and Azure Policy for policy-driven governance. Both tools help maintain a secure and compliant Azure environment.
#5 Monitor security regularly
You can use various third-party tools for frequent security monitoring. Regular monitoring ensures a reactive response to threats and a proactive approach to preventing them. You will need an efficient incident response process in place that minimizes the damage from security incidents. The process should include detection, analysis, containment, eradication, and recovery stages, with lessons learned being fed back into the system for continuous improvement.
Best tool for enhanced Azure security
Paladin Cloud is an enterprise cloud security platform that offers various key features to fulfill your obligations as part of the Azure shared responsibility model. For example, with Paladin Cloud, you can:
- Monitor your Azure environment 24/7 to detect and remediate cloud vulnerabilities and misconfigurations of your Azure services.
- Automate compliance checks and ensure you meet organizational and regulatory standards consistently.
- Track and manage resources across your Azure environment.
Paladin Cloud’s asset discovery feature gives a consolidated view of your Azure assets, helping identify misconfigurations and unused or non-compliant resources. Regarding security risks, Paladin Cloud helps prioritize the most critical issues in order to drive efficient workflow and remediation. Overall, Paladin Cloud reduces manual workload and increases accuracy in your Azure compliance processes.
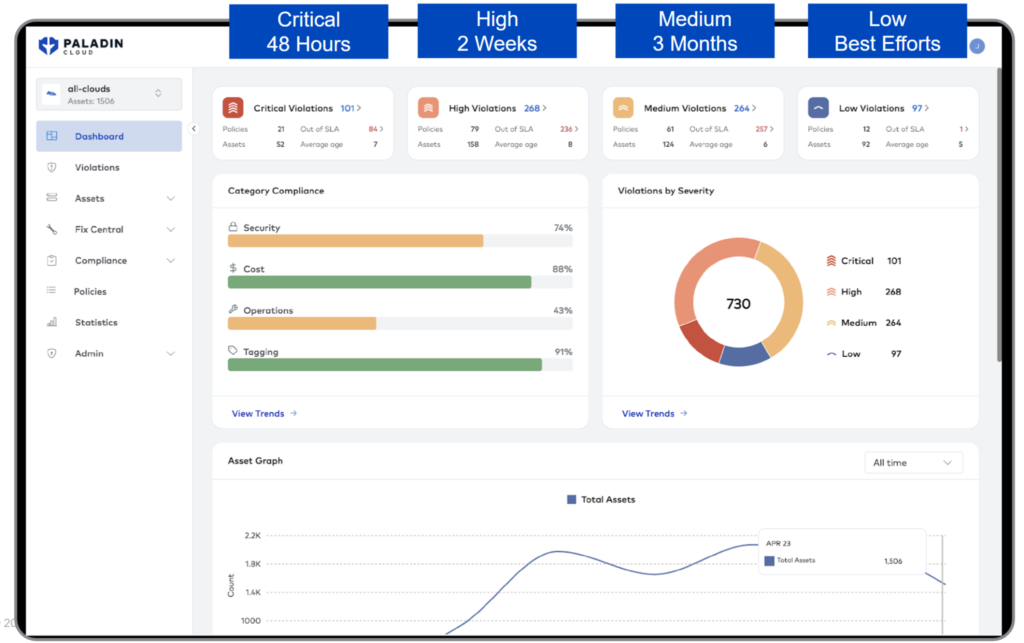
The image shows SLA Management within Paladin Cloud to improve security compliance, a customer’s responsibility within Azure.
By using Paladin Cloud alongside Azure’s built-in security and management tools, you can ensure robust protection for your resources, remain continuously compliant, and effectively manage your responsibilities within the Azure shared responsibility model.
Conclusion
The Azure shared responsibility model is a clear framework that describes both Azure’s commitment towards security and your responsibilities as a customer. Risk assessments, Azure’s security tools, regular monitoring, and a straightforward incident response process are all essential. In addition, integrating third-party tools, like Paladin Cloud, can significantly augment your security and compliance posture.

