Resource Groups are a critical component of Azure management. Simply put, an Azure Resource Group is a container for resources deployed on Azure, that enhances their management and security. But to leverage the full potential of a Resource Group, sound understanding and strategic application are essential.
This article serves as a comprehensive guide to utilizing Azure Resource Groups effectively. We’ll explore various best practices, from effectively structuring resources and implementing Infrastructure-as-Code to ensuring robust security measures and more.
What is a Resource Group in Azure?
A resource group is more than a simple container; think of it as a logical unit serving a specific function. It is a well-structured organization of resources based on lifecycle, application, or environment. It streamlines management, simplifies cost tracking, and enhances security.
Let’s consider a scenario in which you’re deploying a web application in Azure. You create a resource group named “WebApp1-Prod”. It is a logical unit that contains all resources related to your production web application, such as the web app service, the database, and the storage account.
You can manage and monitor these resources as a single unit. For instance, you can apply consistent policies across the resource group, simplify cost tracking, and manage access control efficiently. If the application needs to be removed or replicated, you can delete or clone the whole resource group, making management tasks easier and more efficient.
Reasons for organizing resources into multiple groups
While Azure Resource Groups allow you to manage related resources as a single unit, there are several scenarios where you may want to divide your resources across multiple resource groups. While separating resources is beneficial, it’s also important not to over-complicate your Azure resource structure. The key is balancing management ease, security, cost tracking, and operational efficiency. We give some example scenarios for multiple resource groups below.
Environment separation
You might have separate resource groups for different environments like Development, Testing, Staging, and Production. It provides clear isolation between environments and ensures that actions (like deployments or tests) in one environment don’t impact others.
Lifecycle and management
Resources with different lifecycles or managed by different teams should be in separate resource groups. For example, you might have an application that’s updated frequently and a database that rarely changes. Putting them in different resource groups allows you to manage and version them independently.
Access control
If you have different teams or individuals that need specific access to certain resources but not others, use separate resource groups to provide a more granular level of access control.
Geographical distribution
If you have resources deployed across different geographical regions, it may make sense to group them by their location for easier management, cost tracking, and compliance with data sovereignty requirements.
Billing purposes
You can group resources based on the cost center or department they belong to, enabling more precise cost allocation and tracking.
Resource organization strategies
A common pitfall when starting with Azure Resource Groups is overlooking the importance of a well-planned structure. Without careful planning, resource groups can quickly become cluttered, leading to inefficiencies and potential security issues.
To avoid future complexity, you must:
- Define a structure based on your operational needs, such as environment (Dev, Test, Prod), project, or department.
- Establish clear naming conventions for resources.
- Consider lifecycle similarities when grouping resources, as deleting a resource group will delete all resources within it.
Lastly, remember that although you can move resources across groups, some services experience downtime during the move. You can establish a robust foundation for Azure cloud adoption by focusing on these areas from the start.
Best practices for using Azure Resource Groups
A brief rundown of essential best practices for optimizing Azure Resource Groups are given below
| Best practice | Description |
|---|---|
| Strategic use of management groups and subscriptions | Leverage the relationship between Azure Resource Groups, Management Groups, Subscriptions, and Resources for effective resource governance. |
| Infrastructure-as-Code adoption | Implement automation with Infrastructure-as-Code tools like ARM, Terraform, and Ansible to streamline the management and provisioning of Azure Resource Groups. |
| Efficient tagging practices | Utilize resource tagging for improved tracking, management, and cost allocation within Azure Resource Groups. |
| Awareness of known limitations | Stay informed about the known limitations of Azure Resource Groups to plan and manage resources effectively. |
| Adherence to naming standards | Follow well-defined naming standards to maintain consistency across Azure Resource Groups. |
Let’s dive deeper into each of the best practices presented in our summary, providing a clearer understanding and practical guidance for effective Azure Resource Group management.
Leverage management groups and subscriptions
Management Groups and Subscriptions are your allies in the effective governance of resource groups. Use Management Groups to apply policies at a high level, with Subscriptions providing an extra layer of administration. This layered governance model promotes consistency and control.
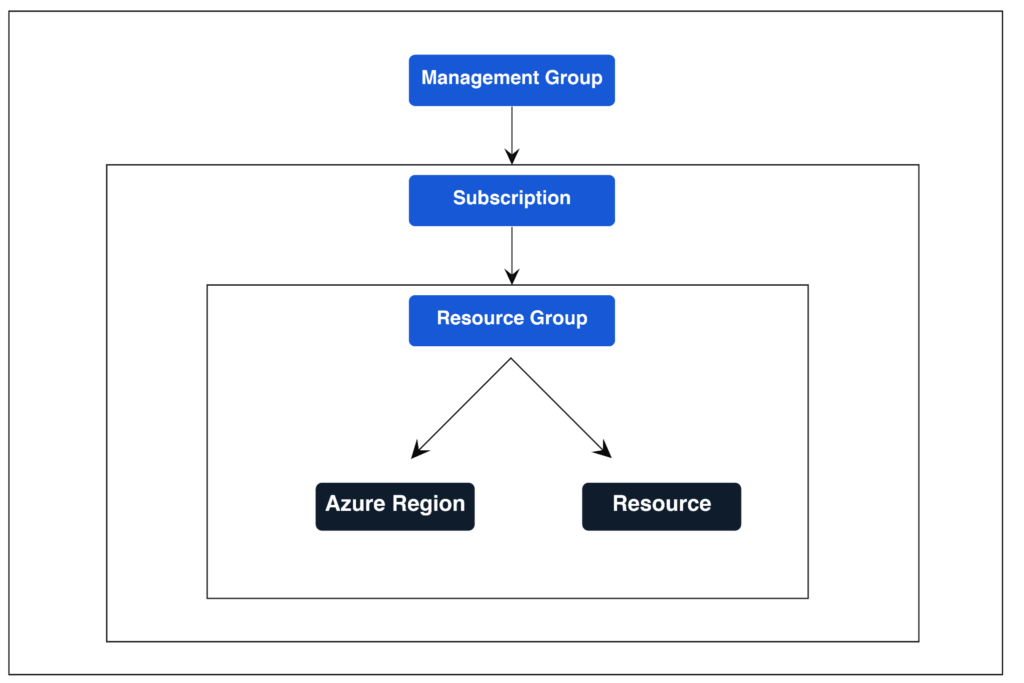
The diagram shows the relationship between a Resource Group and an Azure Subscription and Management Group. The Resource Group is associated with an Azure Region and has Resources under it.
Adopt Infrastructure-as-Code
As Azure Resource Groups grow in number and complexity, management becomes more challenging. Infrastructure-as-Code (IaC) allows you to define and manage your Azure infrastructure using code. You can provision, update and delete Resources consistently and reliably through scripts. It reduces the scope of manual errors and makes infrastructure more predictable and secure.
You can use tools like Azure Resource Manager (ARM) templates, Terraform, or Ansible to implement IaC. Below is an example of an ARM template to create a resource group.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"resourceGroupName": {
"type": "string",
"metadata": {
"description": "The name of the resource group"
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "Location for the resource group"
}
}
},
"resources": [
{
"type": "Microsoft.Resources/resourceGroups",
"apiVersion": "2020-06-01",
"location": "[parameters('location')]",
"name": "[parameters('resourceGroupName')]"
}
]
}
Use efficient tagging practices
Tags are key-value pairs you apply to your Azure resources as metadata elements. A well-defined tagging strategy with consistent tags across your organization can revolutionize resource management. For instance, tagging is helpful for:
- Quick resource identification
- Simplified cost management
- Facilitating automation
Our preferred tagging approach involves establishing a consistent strategy centered around mandatory tags like ‘Project,’ ‘Owner,’ and ‘Environment.’ Optional tags can cater to specific needs. The key is to ensure simplicity and clarity and promote easy resource management.
Be aware of Resource Group (Azure) limitations
As you architect your resource organization, be aware of the cap on the number of resource groups within one subscription and the total resources a single group can contain. Although Azure permits shifting resources between groups, some services might momentarily pause during the transition. Understanding these constraints lets you seamlessly adapt your resource grouping strategy and scale operations.
Adhere to naming standards
Naming conventions are an often-underestimated facet of effective cloud management. A thoughtful, consistent naming convention simplifies identification, aids in automation, and enhances overall clarity.
Adopt a hierarchical, meaningful structure when naming your Azure resources. You could follow a structure like <environment>-<application>-<objectType>-<region>. Here, each naming component contains information about the environment (Prod, Dev, Test), the application it’s part of, the object type (VM, Storage, DB), and the Azure region.
Security measures for the Resource Group (Azure)
Security in resource groups relies on good practices like ‘least privilege’ access. Assign only necessary rights to users or processes. For instance, avoid assigning the ‘Owner’ role when ‘Storage Blob Data Contributor’ would suffice. This reduces the potential impact of a breach.
Here are examples of Azure Resource Manager (ARM) templates that contrast poor practice against best practice regarding role assignments.
Poor practice
The below template assigns the ‘Owner’ role to the user at the resource group level. The ‘Owner’ role provides full access, including the ability to assign roles to other users, which can pose a security risk if the user’s credentials are compromised.
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Authorization/roleAssignments",
"apiVersion": "2018-01-01-preview",
"name": "[guid(resourceGroup().id, 'Owner')]",
"properties": {
"roleDefinitionId": "/subscriptions/{subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635",
"principalId": "{user-object-id}",
"scope": "[resourceGroup().id]"
}
}
]
}
Best practice
The below template assigns the ‘Storage Blob Data Contributor’ role to the user at the resource group level. This role allows users to read/write data in Blob storage but does not give them control over the account or access keys. It demonstrates the principle of least privilege, limiting potential damage if a security breach occurs.
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Authorization/roleAssignments",
"apiVersion": "2018-01-01-preview",
"name": "[guid(resourceGroup().id, 'Storage Blob Data Contributor')]",
"properties": {
"roleDefinitionId": "/subscriptions/{subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/ba92f5b4-2d11-453d-a403-e96b0029c9fe",
"principalId": "{user-object-id}",
"scope": "[resourceGroup().id]"
}
}
]
}
Tools that improve Azure Resource Group management
Integrating Paladin Cloud into your Azure Resource Group management strategy can significantly improve visibility and control over your cloud environment. One of Paladin Cloud’s standout features is its ability to conduct in-depth security analysis. It provides actionable insights into your Azure infrastructure’s security status, helping you identify and mitigate potential risks before they escalate.
In addition, Paladin Cloud excels in asset discovery, a crucial aspect when dealing with multiple resource groups across different subscriptions. It lets you maintain an up-to-date inventory of your Azure resources, helping you manage and track their status effectively.
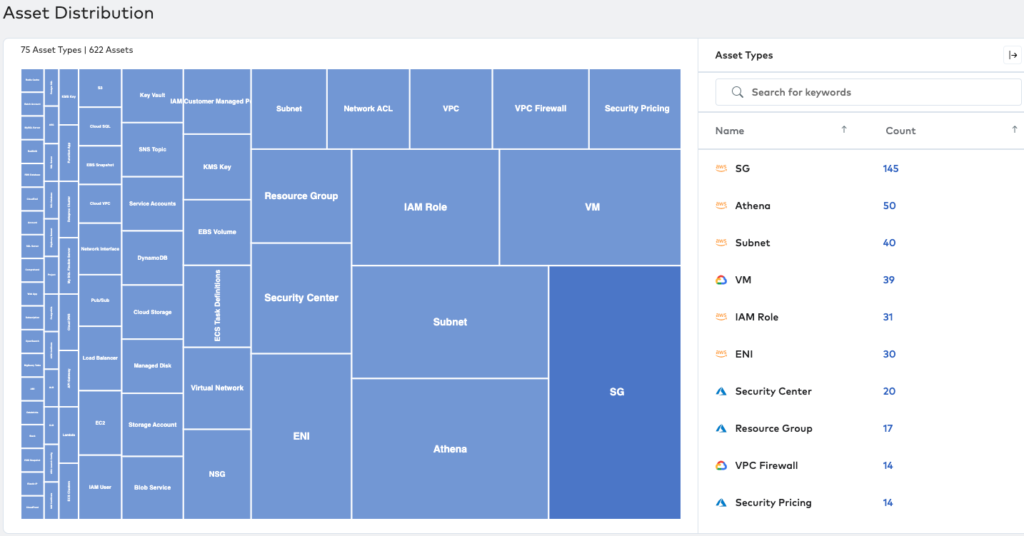
The image shows an example of an asset discovery heat map from Paladin Cloud to visualize Azure resources, and multi-cloud assets, from a single pane.
Conclusion
Effective Azure Resource Group management requires thoughtful organization, efficient practices, and the strategic use of tools like Paladin Cloud. The best practices like efficient tagging and IaC help you maximize the utility of your resources, streamline operations, and bolster security. Remember, a well-managed cloud is the cornerstone of a successful digital transformation journey. Embrace these practices and enhance your Azure adventure, achieving operational efficiency and robust security in the cloud.

