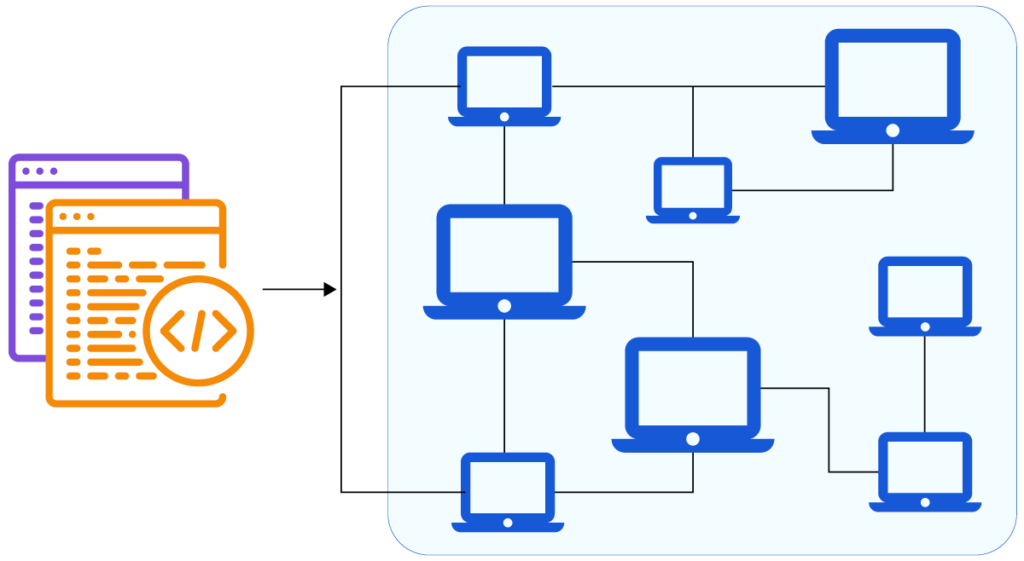
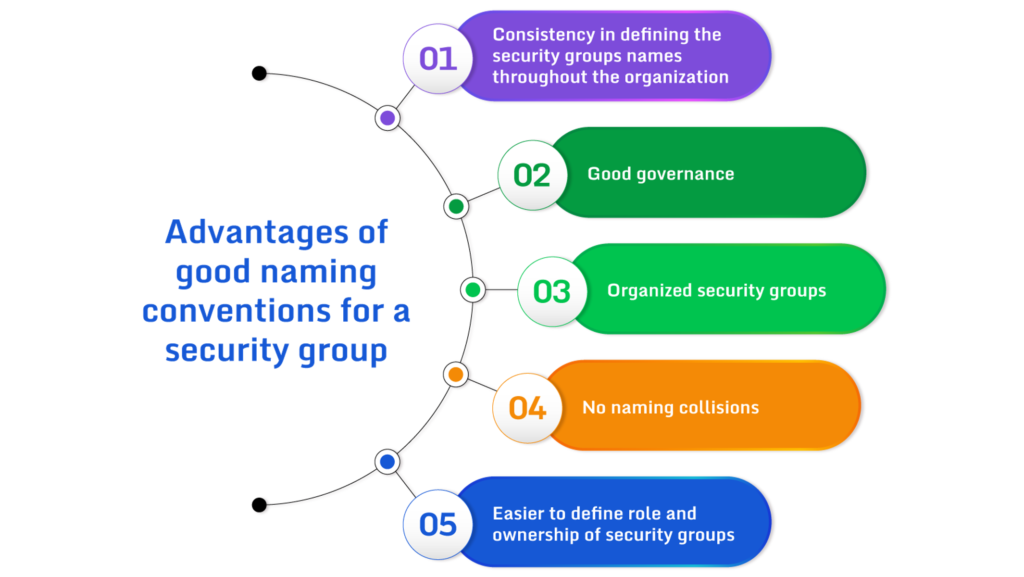
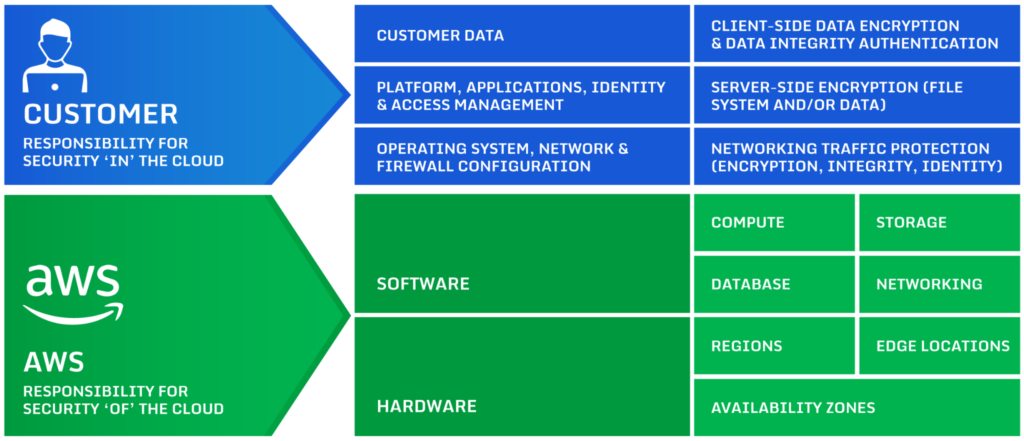
Cloud-native services are highly vulnerable to cyber threats due to their operation in public clouds and multiple users sharing the same resources. In such scenarios, a hacker can orchestrate a deeper attack by exploiting a vulnerable resource they manage to control. Perimeter security alone isn’t enough, but it still functions as the first line of… Read more »