Cyber asset attack surface management (CAASM) tools and platforms are an emerging type of cybersecurity solution that enables organizations to identify, manage, and secure their digital assets. They provide visibility into modern IT assets, such as people, data, proprietary code, cloud infrastructure, and online applications and services, especially in terms of the organizational attack surface. Knowledge of these assets and the relationships among them is the first step in ensuring their integrity.
The IT landscape of many companies has drastically changed over the last ten years. Traditional asset management tools are not equipped to deal with new concepts such as cloud infrastructure, digital identities, and software-as-a-service (SaaS) solutions.
In this article, we’ll discuss CAASM in more detail. We’ll examine the new challenges presented by technologies such as cloud assets and show how a CAASM solution can help resolve them.
Executive summary of key CAASM concepts
The following is a summary of the key concepts discussed in this article.
| IT infrastructure evolution | The uptake of more modern technologies like cloud computing and digital identities means traditional approaches to asset management are no longer sufficient or relevant. There has been exponential growth of IT “digital” or “virtual” assets, which are vulnerable to unauthorized access and attack, and also a need for increased connectivity with other organizations and customers. |
| What is CAASM? | CAASM tools give centralized visibility of new IT asset types, such as cloud assets, especially when it comes to the overall attack surface. |
| How are cloud assets categorized? | Cloud assets can be placed into four categories:
Cloud asset configurations can include firewall/ACL rules, auto-scaling groups, security policies, load balancer configurations, etc. |
| Attack surface | An organization’s attack surface consists of all the various points where an unauthorized user can enter or extract data. Examples include an open network port giving access to a virtual server or database, unencrypted disks, or storage buckets; permissive security policies giving more access than needed; credentials posted in a public code repository; or a lack of audit trails for the detection of suspicious activity. |
| CAASM as a solution | By adopting a CAASM solution, security teams can obtain detailed contextual insights and a unified view of their cyber assets, leading to a more effective security posture. The use of a CAASM platform gives organizations visibility of their internal and external cyber assets and the ability to examine them and consistently rectify security control and vulnerability gaps. |
| CAASM challenges | CAASM can involve complexity and high costs both for setup and ongoing operational management, especially without using automation. Another potential challenge involves the required integration into other solutions, such as SIEM/SOAR tools for analysis and remediation. |
Why you need CAASM
In the past, asset management was a critical function of most businesses. IT asset management systems provided the means to classify hardware and software license ownership and track the asset lifecycle to ensure financial overview and regulatory compliance. However, the adoption of more modern technologies and operational trends—including cloud computing, digital identities, increased connectivity, and hybrid working—have made the traditional approach to asset management no longer sufficient or relevant.
Many organizations have a cloud-first strategy for new infrastructure. These virtual resources have no asset values or depreciation requirements, and the required software licensing is normally included within a pay-as-you-go subscription model. Alongside this, the COVID-19 pandemic shifted many workers to a home or hybrid approach. The rapid shift to this style of working created a need for “anywhere” access to company applications and data, often through online portals and involving the use of employees’ own personal IT equipment.
The security implications of these new directions are significant and have made the visibility of these assets critical for ensuring the integrity of corporate information and access to company services. Rather than just compiling a database of hardware and software, asset management should be more concerned with people, data, proprietary code and cloud infrastructure, and online applications and services. More important still is the vulnerability of these essential resources to being exploited by unauthorized individuals. Cyber asset attack surface management (CAASM) tools and platforms are emerging to provide the necessary capabilities in this area.
What is CAASM?
CAASM solutions are cybersecurity products that enable organizations to identify, manage, and secure their digital assets. They provide security teams with a comprehensive view of their attack surfaces, which includes all of the digital assets that an organization owns, uses, or manages. CAASM also provides features to help organizations assess and manage the risks associated with their attack surfaces.
A CAASM solution works by gathering information about an organization’s digital assets through various methods, such as API integrations, network scans, existing asset inventory systems, and other tools like security information and event management (SIEM) systems. Once this information is collected, CAASM provides security teams with a unified view of the organization’s attack surface, including details such as the types of assets found, the location of the assets, and the risks associated with them.
CAASM platforms also help organizations identify security gaps and vulnerabilities in their attack surfaces. These vulnerabilities could be caused by outdated software, misconfigured settings, or other issues. CAASM platforms provide automated remediation workflows to help organizations address these vulnerabilities and reduce the risk of a cyber attack.
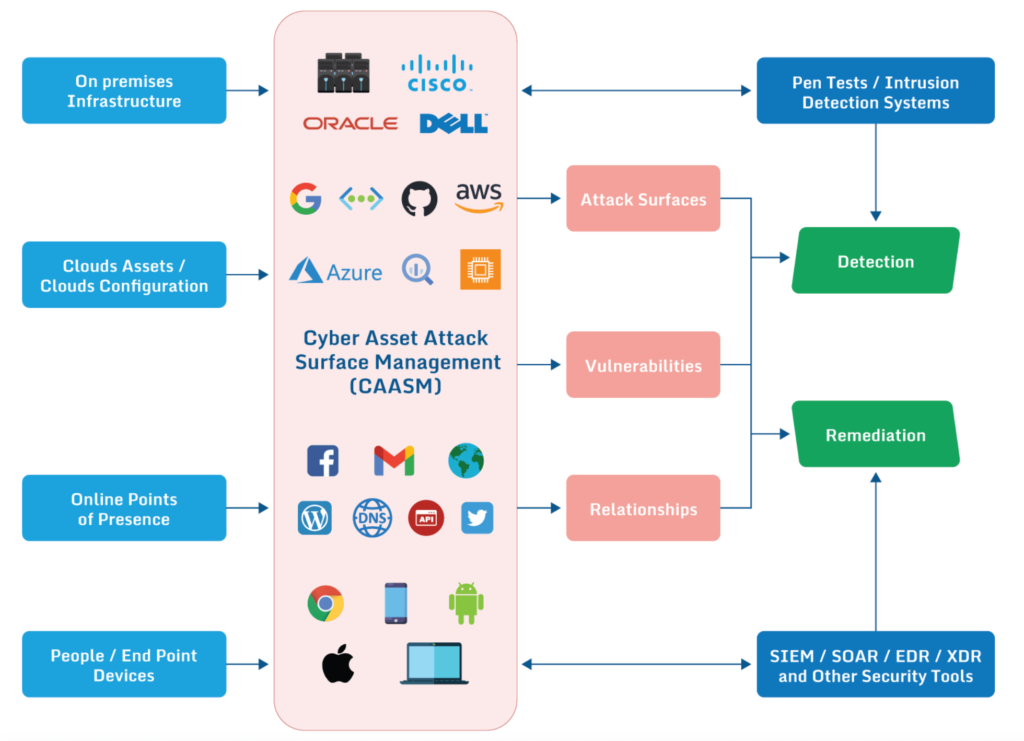
A logical architecture overview of a CAASM solution integrated into other security toolsets
Cloud assets
Cloud assets are any resources that are stored or managed in the cloud. They can include anything from data and applications to infrastructure and services.
Cloud assets are an area where traditional asset management systems struggle to have relevance because these are not physical assets: They are more often temporary or ephemeral and have no “value” in conventional financial models.
These assets can generally be divided into four categories:
- Compute: This includes all cloud assets that process data in some way, including virtual servers, containers, functions as a service, and some data analytics services.
- Network: This category includes any cloud asset involved in the transmission of data. Examples are virtual networks, virtual private clouds (VPCs), virtual private networks (VPNs), and security groups or virtual firewalls.
- Storage: This group includes cloud assets or services that hold data at rest, as opposed to those that process or transform data. Storage buckets and containers, databases, and virtual hard disks go here.
- Services: This category includes any asset that doesn’t fit into the ones above. Examples include identity services, such as IAM solutions, or services that use common authentication protocols (e.g., SAML, OIDC, or OAuth) like Azure Active Directory and Google’s G Suite.
Cloud configurations
These are the configuration profiles of cloud assets. Cloud configurations are important because they ensure that cloud resources are used securely and efficiently and that cloud resources are compliant with regulations and standards. Common examples of such configurations are the following:
- Virtual server or container compute specifications (e.g., assigned CPUs and RAM)
- Virtual firewall rules / access control lists (ACLs)
- Load balancer configurations
- Encryption policies and ciphers for storage buckets and virtual hard disks
- Roles, groups, and the permissions assigned to these in IAM solutions
- Password policies and MFA protection guard rails for authentication services
Online points of presence
Online points of presence are typically used to reach an organization’s customers or potential customers, ultimately to build better relationships and generate revenue. In terms of categorization into assets, they could be identified as shown below:
- Websites / online portals: A company’s website is its online home, typically the first place that potential customers will visit to learn more about the company and its products or services. However, it is very common now for companies to host multiple websites for different purposes. Examples might be a customer-only support portal, a retail website, an informational site, and an online portal for employee services.
- Application programming interfaces (APIs): Increasingly common are API gateways to allow customers, suppliers or employees to access or ingress data through programmatic means.
- Mobile applications: These applications are generally made up of code similar to that used in websites and API gateways. However, they are often developed separately and thus offer another route into a company’s networks or data.
- Social media channels: Generally linked to marketing and customer relationship building, social media accounts are an essential part of a modern business.
- Domain Name System (DNS) hosting providers: DNS names and hosts are used to allow connections into the firm’s online resources. External providers host DNS domains, so these should be considered part of the online assets to manage and monitor.
- Autonomous system numbers (ASNs): Larger companies may have blocks of public IP addresses assigned to them for routing. If this is the case, these are assets that should be identified within the CAASM.
People
People create, use, and manage IT systems, and they are generally the parts of the system most vulnerable to cyber attacks. CAASM can help to protect people by providing them with the information and tools they need to stay safe online. A CAASM solution can also help protect cyber assets by identifying and remediating vulnerabilities in client devices. Two examples of routes through which people interact with cyber assets are end-user devices (e.g., personal laptops and phones) and digital identities (e.g., an employee’s Azure AD or G Suite account).
Attack surfaces
A cyber attack surface is the sum of all the ways that an attacker can try to gain access to a system or data. It includes all the entry points into a system, such as websites, network devices, API endpoints, and authentication systems. It also includes all the vulnerabilities that an attacker can exploit, such as unpatched software and misconfigured systems.
The size of a cyber attack surface can vary depending on the size and complexity of the system. For example, a large enterprise with a complex IT infrastructure will have a larger attack surface than a small business with a small online presence. The attack surface can also vary depending on the type of system; for example, a company’s website will have a different attack surface than its mobile application. The important thing to note is that the traditional network “perimeter” does not control modern attack surfaces.
The attack surface is an important concept in cybersecurity because it helps identify the areas that are most vulnerable to attack. By understanding the attack surface, organizations can take steps to mitigate the risks.
The following are some examples of common attack surface entry points:
- Any open networks or firewalls attached to compute infrastructure may allow traffic inbound or outbound from the internet.
- Data stored in a cloud bucket or virtual hard disk without encryption, or with weak encryption, is far more vulnerable to being used for malicious purposes if stolen or extracted.
- Permissive security policies can allow either direct or indirect elevated control over cloud assets to be used for unintended purposes.
- Confidential or sensitive data stored within public code repositories or storage containers is at risk of accidental exposure (e.g., an API key or secret access key credentials)
- Email phishing or other social engineering attacks can trick employees into providing sensitive data or installing malware such as keyloggers to capture their digital identity information. An attacker can use this information to access the company’s network, services, and data.
- Although not directly part of an attack surface, a lack of logs and auditing of cloud systems would allow a malicious user’s activity to go undetected.
CAASM as a solution
What the list above shows is the complexity of not only identifying all cyber assets but also ensuring the correct configuration to reduce attack surfaces. This, combined with the increased sophistication of modern cyber attacks, means that corporations should have an all-inclusive view of both internal and external assets, many of which are often overlooked by traditional security solutions.
Fortunately, there are manageable ways to get started. Cloud providers have tools and APIs that deliver accessible routes to create an inventory of cloud assets and their configurations. In conjunction with commercial or open-source tools, it is relatively straightforward to build this inventory, identify attack surface entry points, and scan for current vulnerabilities and misconfigurations. By taking this step, organizations can go a long way toward protecting themselves and these potentially vulnerable assets.
A CAASM solution based on the above principle can solve most of these challenges through these methods:
- Providing an improved security posture by utilizing multiple routes to detect cloud-based assets, such as:
- Using network scans and API queries to scan cloud platforms and identify services.
- Employing web crawling and Internet scanning of public endpoints, known domain names, and public IP blocks / ASNs.
- Detection of security vulnerabilities and the relationships of these vulnerabilities to other assets. For example:
- A vulnerable container could be exploited to access a sensitive backend secure database (lateral movement).
- A phishing attack on vulnerable employees can result in stolen credentials (credential dumping). Bad actors install malware using these credentials to elevate their access and exfiltrate sensitive data or cause malicious damage such as a ransomware attack.
- Alerting of these issues and, ideally, using automation to remediate them:
- Patching the vulnerability in the container and updating the container image so that subsequent deployments are protected.
- Conducting phishing awareness training, including simulated attacks for all employees, to educate staff about risk and prevent the initial credentials from being obtained.
- Continuous monitoring to maintain compliance and prevent configuration drift.
Challenges of using CAASM
Implementing a cyber asset attack surface management solution can be complex and expensive, especially for small and medium-sized businesses that don’t have full-time security teams. Even if an outside consultancy is engaged to do this work, there is then the cost of ongoing operational management and the remediation of any uncovered risks.
A free, open-source tool like Paladin Cloud provides a powerful yet simple solution to this challenge. It can be rapidly deployed and immediately start scanning for and protecting against common cloud vulnerabilities with its built-in, pre-configured policies based on the cloud provider’s best practices. It also provides an auto-fix capability to remediate some of these issues where appropriate.

A cloud-centric CAASM solution like Paladin Cloud provides effective protection
It is also important to note that CAASM is not a silver bullet but just one part of a comprehensive security strategy. In the longer term, more effective protection can be provided via integration into other tools, such as security information and event management (SIEM) or security, orchestration, automation, and response (SOAR) solutions, as well as endpoint, extended, and managed detection and response (EDR, XDR, and MDR) systems.
Organizations should also implement other traditional cloud-based security measures, such as virtual firewalls, intrusion detection systems, and malware scanning tools, and carry out security awareness training for all their employees.
Conclusion
Modern cyber asset attack surface management (CAASM) platforms provide organizations with up-to-date and comprehensive views of their digital assets, including cloud-based ones, and the attack surfaces they collectively present. These platforms facilitate the identification, management, and protection of these assets and help minimize the risks of cyber attacks.
CAASM tools bring benefits such as improved security, increased visibility, and enhanced compliance. However, there are also challenges to adopting a CAASM solution, such as complexity and the requirements for integration with other security toolsets.
Despite these challenges, CAASM is increasingly becoming an essential tool in today’s cybersecurity landscape. Security experts now recommend that corporations of all sizes begin implementation to ensure the safety of their digital assets, data, and reputation. Using a tool such as Paladin Cloud gives a unified view of cloud assets, configurations, and attack surfaces. It also delivers proactive risk detection, verification that security controls are protecting your cyber assets and automated remediation of identified violations to improve the organization’s security posture and dramatically reduce the chances of a cyber attack.


