Your IT infrastructure’s attack surface is the sum of all methods, vulnerabilities, and backdoors that an attacker could use to gain unauthorized access to your systems. Today’s organizations have ever-expanding attack surfaces that include all devices, cloud, on-premise storage, applications, services, network connections, and other physical and digital assets you can access remotely. Attack surface analysis is the process of identifying, verifying, validating, and mitigating these potential vulnerabilities and security risks.
This article outlines six important steps in attack surface analysis. We discuss each step in detail, explaining what this is and how it can strengthen your organization’s security posture.
Overview of the attack surface analysis process
Attack surface analysis identifies and analyzes the various ways in which potential attackers can target or exploit an organization. It is a complicated and long-term ongoing process because an organization’s attack surface constantly changes due to
- Introduction of new technologies
- Emergence of new threats
- Evolution of business goals and objectives over time.
The process of attack surface analysis typically consists of six main steps, explained below.
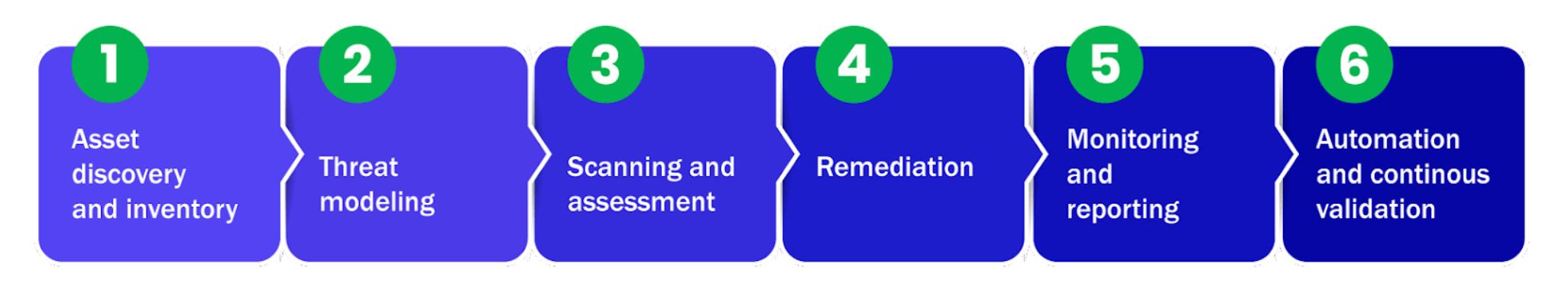
| Step in the process | What it means |
|---|---|
| Asset discovery and inventory | Identifying all assets and their configurations, software, and network connections among your infrastructure. This also includes third-party risk management, external penetration tests of vendor infrastructure, and different compliance certifications. |
| Threat modeling | Analyzing the potential threats to each asset, determining their likelihood and potential impact using standard security frameworks. |
| Scanning and assessment | Scanning assets for vulnerabilities and associated risk evaluation. This includes purple teaming using breach and attack simulation tools, penetration tests, vulnerability scans, and red team activities. |
| Remediation | Implementing measures for vulnerability risk mitigation, such as patching software, configuring firewalls, implementing access controls, network segmentation, privileged access management, and implementing a zero-trust model. |
| Monitoring and reporting | Continuously monitoring the attack surface for new vulnerabilities and threats and reporting on the effectiveness of existing remediation efforts. |
| Automation and continuous validation | Automation of attack surface analysis tasks, so they run on schedule. Includes tracking of progress and modifying the approach as needed. |
Step #1 Asset discovery and inventory
You cannot protect something you don’t know exists, right? Asset discovery involves more than simply making a list of assets. You must identify and document configurations, software versions, and network connections of all assets to ensure they are secure and compliant with organizational policies and industry standards.
Cloud Infrastructure
Attackers scan for known vulnerabilities in your cloud infrastructure and attempt to exploit them. Knowing the configurations and software versions of all assets including software, endpoints and API connections is crucial as it helps you discover the cloud assets running outdated or unpatched software. You can then prioritize patching and updating to minimize the risk of a cyberattack.
Cloud services
Using cloud services nowadays is really a common thing. Also, a common thing is the misconfiguration of those cloud services or bad integration with cloud infrastructure, including compute, networking or storage services, which could lead to data leakage. Understanding all assets’ network connections is critical to identify which assets are publicly accessible or contain sensitive data. You can then create barriers preventing unauthorized access to specific network areas while allowing authorized users to access the necessary resources. From the other side, we need to take care of identity access management to limit the user privileges and provide them the rights and access they really need as well as make sure all unused accounts are revisioned.
Shadow IT resources
The first step in attack surface analysis includes identifying “Shadow IT” resources. Shadow IT refers to the use of technology and software by employees within an organization without the approval of the organization’s IT department. Examples include unauthorized applications, services, devices, or cloud-based services.
Third-party asset inventory
Asset discovery includes the identification of security risks with vendors and third-party providers who have access to your organization’s assets. Third parties like cloud service providers, software vendors, or contractors, can introduce unknown security weaknesses that result in an attack. Hence, for all third-party assets you must:
- Conduct security assessments
- Review contractual agreements
- Ensure that third-party security obligations are clearly defined.
Step #2 Threat modeling
After you complete a detailed asset inventory, it’s time to move to the next stage and prepare a threat model. Threat modeling in attack surface analysis determines attacks’ likelihood and potential impact. You use security frameworks like MITRE ATT&CK or threat intelligence sources to obtain a comprehensive list of attack vectors based on real-world examples from recent attacks.
Modeling strategies
You conduct threat assessments that consider the threat actor’s motivations, capabilities, and opportunities. We give some standard modeling methods below
Attack trees
Attack trees use charts to display potential attack paths in your system. Your attack goal is the root, and possible attack approaches are the branches. You can create multiple trees with different attack goals for a single system.
PASTA
One popular method uses the acronym PASTA for Process for Attack Simulation and Threat Analysis. You first define business objectives and then identify the technical scope of that objective. You then perform risk analysis for the applications and infrastructure related to that objective.
CVSS
Common Vulnerability Scoring System (CVSS) is another method that lets you assign and modify risk scores to different attack surface components like configurations, network connections, and similar.
Step #3 Scanning and assessment:
Now that we have our threat model in place and understand the potential threat to our company, we need to assess current protection levels. Scanning and assessment are critical attack surface analysis processes that help organizations identify vulnerabilities and gaps in security controls that protect their infrastructure. They involve techniques such as penetration testing, vulnerability scans, and red/purple teaming. Let’s talk about each of them.
Vulnerability scanning
Vulnerability scanning is a process that involves automated tools (such as Aquasec and Red Hat ACS). The tools scan the network for software features like open ports, operating system versions, and so on. They check the features against a known database of existing vulnerabilities and raise alerts if they find a match.
Penetration testing
Penetration testing is a technique that simulates an attack on an organization’s network or application. You can choose between black, gray, and white box testing. It usually includes but is not limited to internal applications, infrastructure as well as external pentests of third-party providers infrastructure.
Black box testing
In a black box test, pen testers have no information about the infrastructure they are about to test, only the scope and limitations of their tests and the goals they need to achieve.
White box testing
The pen testers have all the information about the tested environment, usually supported by vulnerability scan reports. They concentrate on testing how easily vulnerabilities found during the vulnerability scans could be exploited and the severity of the potential damage.
Gray box testing
Gray box, as the name states, is between black and white box testing. Pentesters have little information about the environment they are trying to break into.
Red teaming
Red team activities simulate real-world attacks to test an organization’s security posture. Skilled ethical hackers attempt to penetrate an organization’s defenses using various techniques, such as social engineering, phishing attacks, and advanced persistent threats (APTs). By simulating a real-world attack, organizations can take corrective action before an actual attack occurs, reducing security risks and minimizing the attack impact if one occurs. The red team activities are more advanced than penetration tests as they use real-world scenarios which involve every step of the cyber kill chain.
Purple teaming
Purple teaming is a collaborative approach that involves both your internal security team(defenders) and red team (attackers) working together to evaluate the effectiveness of your security controls. This approach typically involves using breach and attack simulation tools. Purple teaming is less adversarial than red teaming. It takes a collaborative approach to assess both existing vulnerabilities and response mechanisms.
Step #4 Remediation
There are several steps that organizations can take to remediate vulnerabilities and improve their security posture effectively.
- Conduct regular audits of infrastructure and configuration
- Regularly review and apply software patches to ensure your systems remain secure and up-to-date.
- Re-configure and update firewall rules regularly based on recent threats.
- Divide your network into segments to control and monitor access to your systems and applications.
- Restrict and strictly control access to privileged accounts with sensitive data access.
- Implement a zero-trust model that requires strict user authentication and access controls.
Also, keep in mind that we only mention generic security controls suitable for attack surface analysis of all types of organizations. You must tweak the list above based on your specific infrastructure and assessment results.
Step #5 Monitoring and reporting
Unfortunately, you cannot remediate every security gap in your organization due to time and budget constraints. Some gaps may also be impossible to overcome due to the specifics of your business. Additionally, the ever-evolving threat landscape may create new challenges you cannot prepare for in advance. That is why we need one extra layer of security: continuous monitoring.
Continuous monitoring
Continuous monitoring involves keeping a close eye on your organization’s attack surface to reduce your response time interval in case of an incident. You can implement security controls like
- Security event log monitoring
- Host and network intrusion detection of threat events
- Antivirus identification of malicious code.
- Security information and event management(SIEM) tools
- Endpoint detection and response (EDR) tools
Comprehensive monitoring helps you detect and respond to all incoming attacks much faster.
Reporting
Monitoring is only half the battle. Reporting on the effectiveness of attack surface analysis efforts is equally important. Reporting involves analyzing the results of the actions taken to address vulnerabilities and threats and determining whether they successfully protected the company’s systems and data. Most of the monitoring tools mentioned above can also generate reports on your existing security efforts.
Of course, monitoring and reporting can be time-consuming and complex, especially for businesses that lack the expertise and resources. Many companies turn to third-party security providers as a cost-effective solution. For example, Paladin Cloud is a cloud security platform that provides continuous compliance over your cloud assets to enhance an organization’s security posture. The platform provides a full asset inventory, while verifying security controls are providing intended protection. Prebuilt and custom security policies provide automated compliance checks to identify vulnerabilities and misconfigurations of cloud resources.
Step #6 Automation and continuous validation
Automation of attack surface analysis requires creating processes that reduce human interaction and perform required tasks on a scheduled, regular basis. Automation saves time and resources on routine tasks and allows security teams to focus on critical work. This is particularly important for large and complex systems where manually performing attack surface analysis can be challenging.
Continuous validation is also a critical component of the attack surface analysis process. It involves monitoring and evaluating the effectiveness of the remediation measures implemented so far. Continuous validation ensures that security measures effectively mitigate the identified risks and helps organizations identify new threats and vulnerabilities that may have emerged since the last attack surface analysis.
Conclusion
Attack surface analysis is a crucial component of the overall cybersecurity strategy. It helps organizations to understand and limit their exposure to potential cyber-attacks. By promptly identifying and mitigating vulnerabilities, organizations can reduce their cyber-attack risk and protect their data, systems, and networks from various attacks and attack groups, from so-called “script kiddies” to APTs or nation-state hackers groups. Automating such a process allows an organization to constantly improve and defend itself from recent and more advanced attacks and track its progress in building a solid security posture.


