Attack surface monitoring (ASM) focuses on identifying the entry points into a infrastructure that could be vulnerable to attack. The goal of ASM is to detect and respond to threats by reducing the attack surface, thereby lowering the risk of a successful attack. This is typically achieved through continuous monitoring, real-time threat intelligence, and automated remediation.
In this article, we’ll look at how to apply attack surface monitoring to an AWS cloud environment, although the principles are transferable to similar tools on other cloud platforms. We’ll also examine the limitations of using only first-party security tools and what you can do to overcome these limits.
Key attack surface monitoring concepts
Before we show you practical strategies for implementing attack surface monitoring in a cloud environment, let’s briefly review some of the core principles we want to uphold in using these technologies.
| Asset inventory | Knowing the assets in your cloud environment and keeping track of changes to them. |
| Configuration management | Monitoring the configuration of cloud assets for deviations from secure baselines. |
| Vulnerability assessment | Regularly identifying and assessing vulnerabilities in digital assets. |
| Threat detection | Detecting and alerting on suspicious activity or malicious behavior within the cloud environment. |
| Incident response | Having a plan in place for responding to and mitigating security incidents in the cloud. |
| Compliance monitoring | Ensuring that the cloud environment complies with security and regulatory standards. |
Setting up attack surface monitoring on AWS
In this tutorial, we will briefly walk through the steps to set up a basic attack surface monitoring system in AWS, which requires the use of various AWS services and tools.
1. Create an Amazon Elastic Compute Cloud (EC2) instance
This will act as the primary node for monitoring your attack surface. To create an AWS EC2 instance, log into the AWS Management Console, select EC2, and follow the instructions to launch an instance.
Having an EC2 instance will be helpful when setting up and configuring other services for monitoring your attack surface.
2. Install and configure Amazon CloudWatch
Amazon CloudWatch is a monitoring service that can be used to keep an eye on various components of your AWS infrastructure. To install and configure CloudWatch, log into the EC2 instance created earlier.
You can find thorough instructions for setting up CloudWatch using Amazon’s guide to installing and running the CloudWatch agent on your servers.
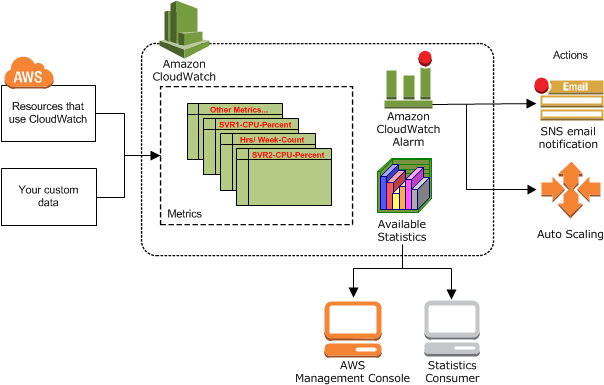
CloudWatch gives you statistics and alarms related to cybersecurity (source).
Amazon CloudWatch Alarms can be used to trigger alerts when certain conditions are met. To create CloudWatch Alarms, log in to the AWS Management Console, select CloudWatch, and follow the instructions to create alarms.
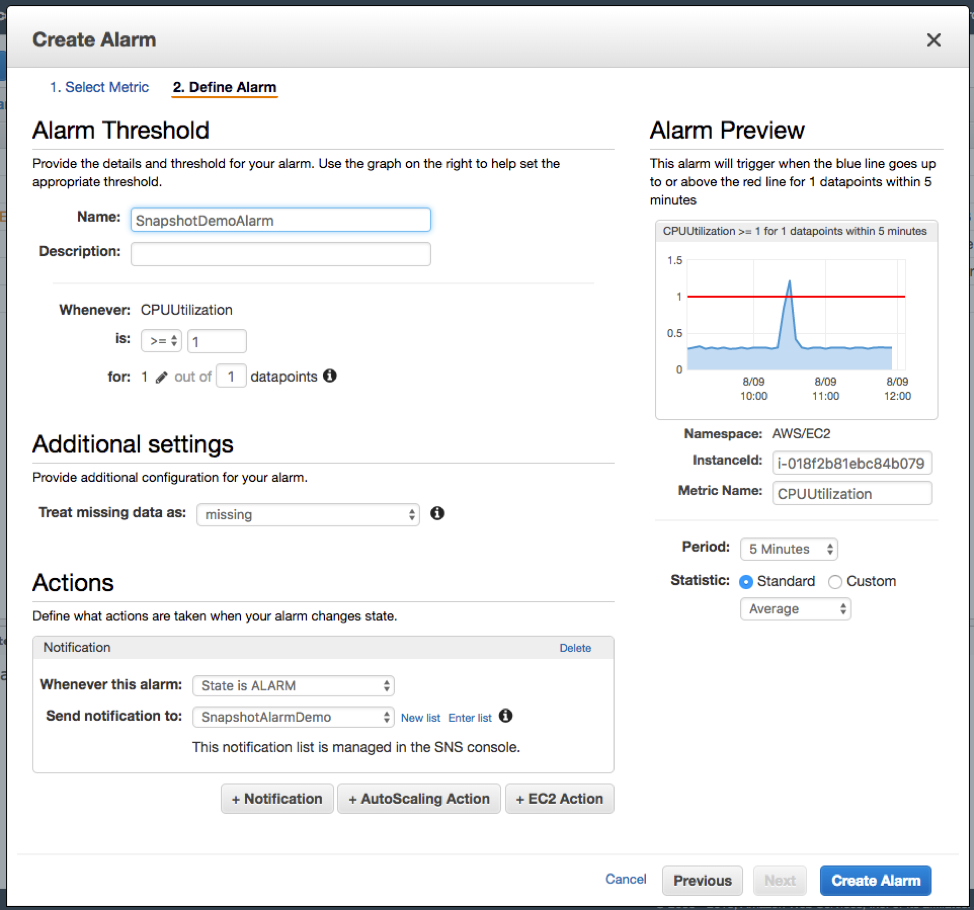
CloudWatch Alarms are highly customizable (source).
CloudWatch Alarms are great for detecting anomalies that indicate security issues, but they’re useful for much more than that. Site reliability and DevOps engineers also benefit immensely from receiving alerts about system performance.
By following these steps, you should have a basic attack surface monitoring system up and running in your AWS environment.
3. Install and configure Amazon GuardDuty
Amazon GuardDuty is a threat detection service that uses machine learning algorithms to detect potential security threats in your AWS environment. To install and configure GuardDuty, log into the EC2 instance created in the first step and run the following commands:
$ aws guardduty create-detector --enable $ aws guardduty list-detectors
Threat detection is a fundamental part of monitoring your attack surface. You want visibility into attacks as they are happening rather than only responding after the fact, and that’s exactly what GuardDuty makes possible.
To get the most out of GuardDuty, you’ll want to integrate it with ElasticSearch or other security information and event management (SIEM) solutions. CloudWatch, for example, might send alerts based on data that GuardDuty provides to your SIEM.
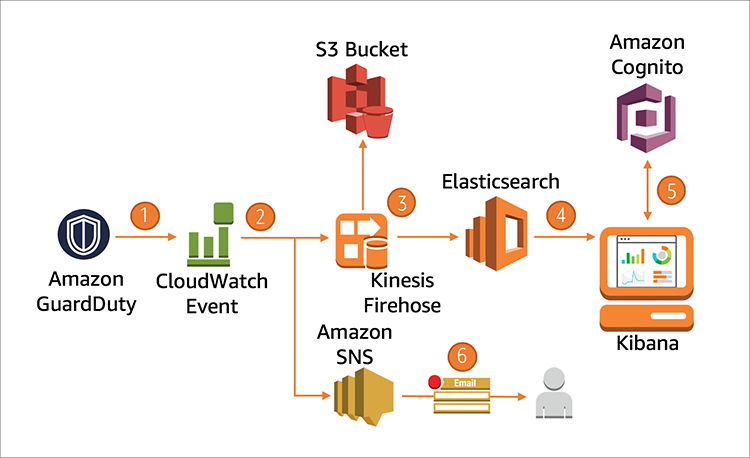
GuardDuty produces notices that you can feed into your monitoring infrastructure (source).
4. Install and configure Amazon Inspector
Amazon Inspector is a security assessment service that can be used to analyze the security of your AWS infrastructure. The basic commands for configuring Inspector look like this:
$ aws inspector create-assessment-target --assessment-target-name my-target $ aws inspector create-assessment-template --assessment-target-arn --assessment-template-name my-template $ aws inspector start-assessment-run --assessment-template-arn
Essentially, Amazon Inspector is a vulnerability management service that helps you continuously and automatically scan your systems for known vulnerabilities. It performs an automated, comprehensive, in-depth security assessment of a workload and provides a detailed report of security findings and recommended remediation steps.
5. Enable and configure Amazon Macie
Amazon Macie is a security service that uses machine learning algorithms to detect sensitive data in your S3 buckets. To configure Macie, you can use the macie2 AWS CLI command:
$ aws macie2 create-classification-job --job-type "ONE_TIME" --s3-job-definition "macie-poc" --name "Macie Example" ’{"bucketDefinitions":[{"accountId":"254378651398", "buckets":["macie-poc"]}]}’
Note that this command requires you to have an S3 bucket setup with a bucket called macie-poc.
What’s great about Amazon Macie is that it can scan through massive amounts of data looking for sensitive data and secrets that you don’t want getting out (such as credentials, private keys, and backups). Obviously, protecting sensitive data is fundamental for security, but it’s also important for meeting data compliance standards.
6. Configure AWS Security Hub
Security Hub provides a comprehensive view of security alerts and compliance status across an AWS environment. With AWS Security Hub, users can centrally manage and monitor security posture, making it easier to detect and respond to potential security threats.
In terms of attack surface monitoring, AWS Security Hub helps users identify potential vulnerabilities and misconfigurations in their AWS infrastructures that could be exploited by attackers. It provides continuous monitoring of resources and generates alerts when it detects any security-related issues.
Users can also customize the alerts they receive and use Security Hub’s integration with other AWS services to automate response actions, such as quarantining compromised resources or revoking access keys. By providing a unified view of security information, AWS Security Hub helps users stay on top of potential attack vectors and proactively improve security posture.
Limitations
While AWS provides several built-in tools for attack surface monitoring, it’s not a panacea. The AWS built-in tools provide a good starting point for attack surface monitoring, but they may have limitations that must be considered when planning a comprehensive security strategy. Here are some to look at before you build your attack surface monitoring infrastructure using these services:
- Limited customization: The built-in tools may not provide the level of customization needed for complex use cases.
- Issues involving integration with third-party tools: Integrating the built-in tools with third-party security tools can be challenging and may require additional development work.
- False positives: These tools may generate many false positives, requiring manual investigation and reducing efficiency.
- Limited coverage: The built-in tools may not cover all aspects of an organization’s attack surface, so additional tools and services may be required.
- Cost: The cost of using the built-in tools may become excessive for larger organizations with complex attack surfaces.
- Complex configuration: Configuring the built-in tools can be complex and time-consuming, requiring a deep understanding of the underlying technologies.
- Limited support for legacy systems: The tools may not support older legacy systems, requiring the use of additional tools and services.
- Limited visibility: The built-in tools may not provide complete visibility into all aspects of an organization’s attack surface, leaving potential vulnerabilities undetected.
Managing your cloud security architecture
Given the limitations we’ve outlined above, cloud security engineers often look for more sophisticated methods for managing their security architecture. One key issue is maintainability.
The key to solving this problem is to manage your cloud deployments by integrating with a multi-cloud cyber asset attack surface management platform with security-as-code (SaC) monitoring capabilities. A multi-cloud platform helps you identify and visualize your cloud asset inventory while verifying security controls are providing the intended protection. Furthermore, SaC monitoring makes it easier to detect potential vulnerabilities and misconfigurations of cloud services while extending your overall security posture.
Ultimately, manually maintaining and documenting security configurations is a recipe for disaster. Luckily, monitoring threats on your attack surface is much more scalable and friendly for engineers when you take advantage of services that let you apply modern engineering practices like security as code.
Summary of key concepts
Attack surface monitoring is a critical component of modern cybersecurity, enabling organizations to identify, monitor, and manage potential security threats to infrastructure. The AWS cloud environment provides several built-in tools for attack surface monitoring, including Amazon CloudWatch, Amazon GuardDuty, Amazon Inspector, and Amazon Macie. However, these built-in tools have limitations, such as limited customization, complex configuration, and limited visibility into all aspects of an organization’s attack surface.
In recent years, security-as-code solutions have emerged as a promising alternative to traditional security tools. Solutions like Paladin Cloud offer an automated, scalable, and cost-effective way to manage and monitor attack surfaces, providing organizations with the necessary visibility to prevent security incidents. By leveraging security-as-code benefits, organizations can improve their attack surface monitoring, ensuring the security and resilience of their critical systems and data.


