Identity and Access Management (IAM) is a set of policies and technologies used to manage entities and their access levels to resources. It aims to make resources available only after proper authorization is assigned and verified. You can use IAM in IT environments like on-premise systems, mobile devices, IoT devices, DevOps environments, physical access controls, and cloud platforms. Every environment has a different IAM implementation. However, the underlying concept is the same—to ensure only authorized users have suitable access to the resources they need to perform their tasks.
By implementing IAM effectively, organizations improve their security posture and compliance with security standards. At the same time, overly stringent or overly permissive IAM standards create security loopholes, incur more costs, increase user frustration, and result in compliance violations.
This article discusses IAM best practices to implement IAM in your environments effectively.
Summary of IAM best practices
Before diving deep into the IAM best practices, the following is the summary of the key practices discussed further in the article:
| Principle of least privilege | Assigning the minimum level of permissions necessary to perform the job responsibilities. |
| Multi-factor authentication (MFA) | Adding an additional layer of authentication on top of password authentication. |
| Review and audit of permissions | Periodically review and evaluate the permissions assigned to users and services. |
| Use of role-based access control | Provides fine-grained access control to resources and data. |
| Strong password policy | Implement a strong password policy to prevent lost or stolen passwords. |
| Monitor user behavior | Monitoring user behaviors for unauthorized/ suspicious activities helps detect and respond to security threats. |
| Limit the use of privileged accounts | Limiting the use of privileged accounts helps reduce the risk of breach. |
Following IAM best practices can provide several advantages, including improved security, compliance, operational efficiency, increased user productivity, and risk management.
#1 Principle of least privilege
The principle of least privilege suggests attaching the minimum level of permissions required by human and software entities to perform authorized tasks. It is based on the idea that having over-permissive access increases the risk of misuse, exploitation, and unauthorized access. For example, an employee designated to maintain specific storage in Amazon S3 should not have full S3 access. Similarly, an employee working as an accountant for a company may only be granted access to financial data relevant to their job description rather than unrestricted access to all company data. Limiting permissions prevent data breaches caused by human error and reduces the scope of attack in case of user credential leakage.
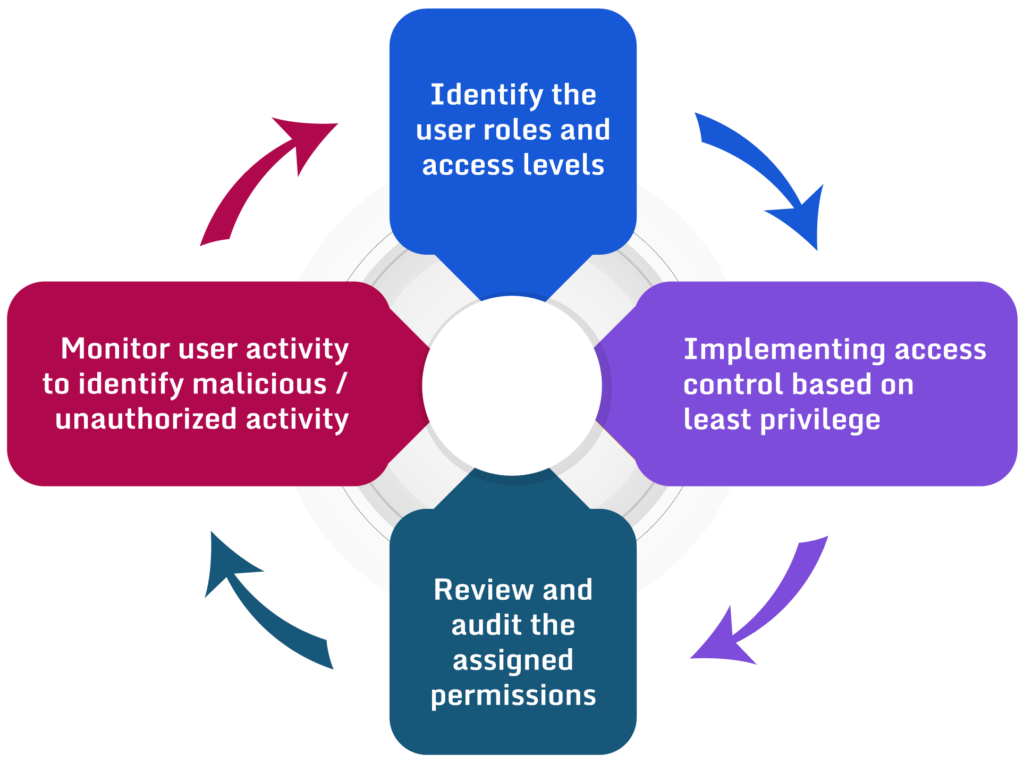
Fig.1 Process of assigning permissions to users
#2 Multi-factor authentication
Multi-factor authentication (MFA) is another IAM best practice that adds an additional layer of security by requiring more identity evidence than just a password. Further evidence typically includes any two or more from
- Something the user knows, like a secret question.
- Something the user has, like a hardware fob or mobile device.
- Something the user is, like a fingerprint or other biometrics.
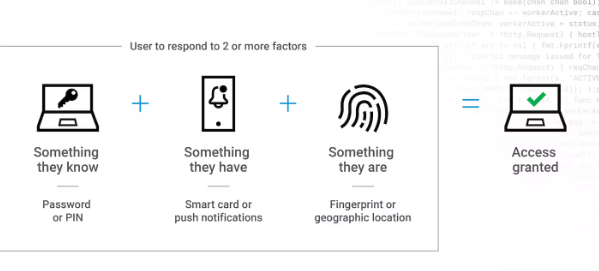
Fig 2. MFA (source)
Using MFA makes it difficult to get unauthorized access to an environment. It’s almost impossible for all layers of credentials to get leaked or stolen.
Cisco Duo is one of the preferred tools to be used for MFA authentication as before allowing users to access your applications, Duo verifies both their identity through two-factor authentication and the security health of their devices. Duo’s product is built on the zero trust model, as it verifies the trust in multiple ways before providing access. Read more here.
#3 Strong password policy
Password policies define the rules and guidelines for creating passwords and managing them. IAM best practices recommend you define rules that enforce password complexity. For example, the system insists that users create passwords with the following:
- Special characters and numbers
- Lowercase and uppercase letters
- Minimum password length
Additionally, the system enforces periodic password changes, rejects password reuse, and enforces MFA usage. Password policies ensure the security of user accounts and access to sensitive data and systems.

Fig 3. Strong Password Policy
#4 Review and audit permissions
Periodically reviewing and accessing permissions assigned to users ensures:
- Every user has the necessary IAM permissions to complete their job.
- Permissions are revoked and updated once the job is done.
You can use automation to revoke and assign permissions as and when required. For example, during a change freeze in an organization, no new developments should be pushed to production. The automation denies any users or processes that do not meet the requirement of a change freeze. Similarly, in case an employee leaves the company, automation revokes access in a timely manner.
#5 Limit the use of privileged accounts
Using privileged accounts is convenient as it allows you to perform tasks that require elevated permissions. However, compromised privileged account credentials can be a huge security risk due to the account’s ability to modify and view critical resources. Key IAM best practices for privileged accounts include:
- Limit the use of privileged accounts.
- Give access to limited users.
- Create separate accounts for different responsibilities.
- Grant access to privileged accounts on a temporary basis.
- Monitor the activity of privileged accounts.
#6 Use of role-based access control
Role-based access control is one of the critical IAM best practices that allows organizations to manage permissions based on the roles or job responsibilities rather than managing permissions for individual users. It improves permission management at scale and reduces the risk of errors and misconfigurations. In addition, you can adapt role management as your organization grows and changes.
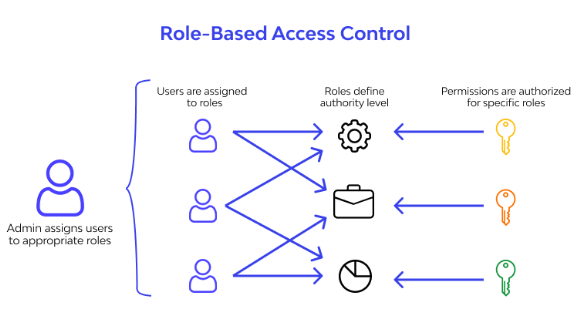
Fig 4. Role-based access control (source)
#7 Monitor user behavior
Monitoring your IT infrastructure for unusual and suspicious activities, such as login from unusual IP addresses or suspicious API access, assists in detecting security threats. Also, you can use the logged data to identify regular access patterns and redefine the permissions based on frequent user access patterns. For example, AWS GuardDuty is a cloud-based service that constantly monitors user activity and identifies deviations from expected user behavior. Monitoring your IT infrastructure can also be helpful in meeting compliance requirements and regulations, such as HIPAA or PCI DSS. It does so by keeping a record of the activities being performed in the infrastructure and demonstrating it for auditing. Moreover, monitoring user behaviors can also help in identifying operational issues.
#8 Automate IAM processes
Automating IAM processes ensures consistency and reduces the risk of misconfigurations or errors in managing access permissions. Automating IAM processes can be helpful in streamlining workflows and reducing the time and resources needed to manage access permissions. By automating routine IAM tasks, IT staff can focus on more complex issues and strategic initiatives. Examples of automation in IAM best practices include:
- Denying authentication into critical systems outside of work hours.
- Denying authentication without MFA.
- Assigning permissions automatically based on job role changes.
- Preventing allocation of Administrator access to a user without specific approval.
How to implement IAM best practices
We give some additional recommendations that facilitate the implementation of IAM best practices in your organization.
Use of a centralized IAM system
Centralized IAM management gives access control to all applications and environments in a single IAM system. You can manage permissions to all applications at a central level instead of having a separate authentication mechanism for all applications. For example, a university’s access portal gives access to all applications by using a single sign-in.
Federation of identities
Identity federation provides a uniform approach to manage access across multiple applications and platforms. Identity federation allows users to authenticate with a single set of credentials to access multiple applications. The key benefit of using identity federation is user experience, users only need to manage a single set of credentials. For example, you can use Cisco Duo’s SSO solution to manage single sign-on to multiple platforms (cloud-based and on-premises). Having one set of credentials to manage improves the posture with lesser chances of breaches. You can further strengthen the security by customizing access policies in the Cisco Duo SSO.
User education and awareness
User awareness and education regarding access management and security threats are important in implementing IAM best practices. Human error, negligence, or lack of awareness often cause data breaches. Therefore, periodically planning user training on security best practices improves IAM effectiveness.
Use of password managers
Password managers are an essential tool for managing the growing number of credentials that users and organizations have to remember. With a password manager, users can securely store and manage their passwords, reducing the risk of security breaches and simplifying the process of accessing different applications and services. Password managers can also help in setting complex passwords. For example, they suggest complex passwords that meet password policy requirements. Most importantly, they can be used to set strong password policies that help to improve the security posture of the organizations. Some password managers also provide the ability to share the password securely with other stakeholders via the password manager.
Privileged access management
Privileged access management (PAM) provides additional layers of security and accountability. It grants privileged account access to authorized users only. PAM solutions also help with the following:
- Privileged accounts discovery
- Privileged accounts session management
- Password management
- Audit and logging
Conclusion
Identity and access management (IAM) support authentication and authorization of users by providing access to resources required to perform their tasks. It improves security posture, compliance with security standards, operational efficiency, and user productivity. However, poorly configured IAM systems result in security breaches and user frustration. Following the principle of least privilege while assigning the permissions and use of MFA can significantly reduce the risk of breaches. Also, setting a strong password policy and reviewing the permissions can reduce the likelihood of a security breach. You must also complement IAM with user awareness and education for comprehensive security. Following the IAM best practices and the third part tools that support IAM processes can make IAM management efficient and practical.
Best practice organizations continuously monitor their IAM resources with third party tools, such as Paladin Cloud’s enterprise platform, to ensure IAM configurations meet industry standards and benchmarks. Updating IAM credentials on a regular basis significantly lowers the probability of unauthorized and undetected access to your cyber assets.