Both multi-cloud and hybrid cloud strategies offer benefits such as flexibility, resilience, and cost-efficiency. Multi-cloud enables selecting the best services from a variety of cloud providers, while hybrid cloud combines on-premises infrastructure with cloud scalability. Both approaches have redundancy, disaster recovery, and regulatory compliance advantages while optimizing costs based on the specific workload needs of modern businesses. To get the most out of them, using a set of services that provides a unified platform to manage and secure cloud-native workloads seamlessly across diverse environments is crucial.
Google Cloud Anthos is a hybrid multi-cloud platform offered by Google Cloud that enables you to run cloud-native workloads in a consistent and controlled manner, whether on a public cloud, on-premises, or at the edge. Although Anthos provides a VM runtime, its primary use case is with container-based workloads, which makes it an ideal choice for modern applications. With Anthos, you can manage and control your workloads, whether they run on AWS, Azure, VMware, bare metal, or any other platform. The platform can be accessed through the Google Cloud console, providing a single glass pane for all your workloads.
Summary of GCP Anthos Security features and best practices
| Key concept | Description |
|---|---|
| Use case | Google Cloud Anthos enables organizations to modernize and manage their applications across on-premises, multi-cloud, and hybrid cloud environments. |
| Shared responsibility | Google Cloud and the customer share the responsibility for securing Anthos workloads. |
| GCP Anthos Config Management Policy Controller | The Policy Controller can be used to implement best practices, security, and compliance management of clusters. It regularly monitors the cluster resource and ensures that it is compliant with the defined constraints and policies. |
| Service hardening using CIS Benchmarks | Use third-party applications to check whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes Benchmark. |
| Network security | Utilize authorized networks and private nodes to ensure access to the control plane is restricted to specific CIDRs in authorized networks, nodes within your cluster’s VPC, and Google’s internal production job managing the control plane. |
| Enable binary authorization | Enforcing binary authorization is critical to only deploying trusted container images with the required signatures from allowed repositories. |
| Anthos Service Mesh | This managed service by Google Cloud based on Istio streamlines traffic management, observability, and security while eliminating the need for application code changes, simplifying operations, and enhancing service delivery. |
| Security patching | Google scans containers for vulnerabilities, automatically patches when possible, and classifies issues as critical or high. Regularly upgrading to the latest Anthos or GKE versions is crucial to addressing security vulnerabilities. |
| Monitoring application security | The Anthos Security dashboard helps enhance application security. It provides a clear overview of areas that need improvement, making it easier for platform and application operators to identify and address security concerns. The dashboard includes a policy audit view with detailed analysis for Google Cloud, VMware, and bare metal clusters. |
GCP Anthos Use Case
Google Kubernetes Engine (GKE) is a managed Kubernetes service that runs on Google Cloud’s infrastructure. Although GKE is a popular managed Kubernetes service with a large customer base, it cannot fit every customer’s use case. Customers with an existing on-premises infrastructure or those who don’t want to host their data on the cloud will use on-premises (VMware or bare metal) or private cloud solutions to gain more control over their workloads. Anthos is a solution that brings Google Kubernetes solutions to on-premises infrastructure.
Similarly, the customer may choose multi-cloud for high availability, fault tolerance, disaster recovery, and implementation of security policies and compliance measures across diverse workloads. In that case, they can still use their existing Kubernetes services, such as Amazon EKS or Microsoft AKS, and manage things from Google Cloud Anthos.
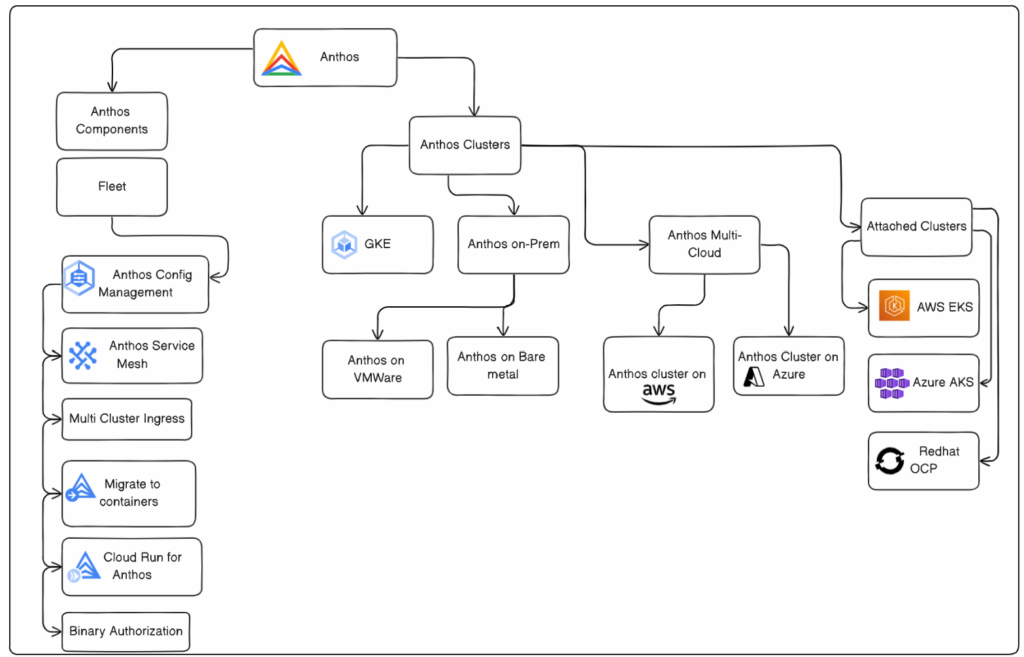
GCP Anthos architecture with different components and offerings
Shared Responsibility Model
Running a business-critical application on Anthos demands that multiple parties carry out their responsibilities diligently. This topic highlights the roles and responsibilities of Anthos clusters for both Google and the customer.
Anthos cluster management is more complex than GKE cluster management due to the added responsibility of handling on-premises infrastructure, network connectivity, and multi-cloud environments. Customers must have a comprehensive understanding of a broad set of components to manage Anthos clusters effectively.
The table below highlights the shared responsibility model for Anthos on-premises (VMware) for Google and the customer.
| Responsibility | Google’s Responsibilities | Customer’s Responsibilities |
|---|---|---|
| Infrastructure management | Maintain Anthos software and components on VMware | Administer the on-premises clusters |
| Image and software maintenance | Keep Ubuntu admin workstation and images up to date | Manage applications, data, and access policies |
| Security and patching | Scan and fix known vulnerabilities in components | Handle infrastructure, like networks, servers, storage, and connectivity to Google Cloud |
| Upgrades and support | Notify users and provide upgrade scripts for Anthos | Maintain and update vSphere and network equipment |
| Google Cloud integration and support | Offer Google Cloud integrations and support | Maintain contracts with VMware and F5 (if used) |
| Issue resolution | Troubleshoot and resolve issues with Google components | Regularly upgrade Anthos clusters to supported versions |
Anthos Config Management Policy Controller
Anthos Config Management Policy Controller is built on an open-source policy engine called Gatekeeper that enforces policies each time a resource is created, updated, or deleted. These policies are defined using constraints from the policy controller template library or Gatekeeper constraint templates.
For example, you may want to enforce having pods be restricted from running privileged containers that can modify the underlying node, including changing the kubelet. This level of access could worsen the impact of a pod security breach. For this, you can apply the K8sPSPPrivilegedContainer constraint.
cat <<EOF>
~/tutorial/anthos-sample-deployment-config-repo/cluster/constraint.yaml
apiVersion: constraints.gatekeeper.sh/v1beta1
kind: K8sPSPPrivilegedContainer
metadata:
name: psp-privileged-container
spec:
match:
kinds:
- apiGroups: [""]
kinds: ["Pod"]
excludedNamespaces: ["kube-system"]
EOF
Service hardening using CIS Benchmarks
Ensure that kube-bench security is integrated as part of the build pipeline to harden the default configuration of Kubernetes. Kube-bench is a Go application that checks whether Kubernetes is deployed securely by running the checks documented in CIS Kubernetes Benchmark. Additionally, a third-party security product such as Paladin Cloud can monitor your CIS compliance across individual or multi-cloud environments and implement additional Google Cloud security policies. Security policies are also available for AWS and Azure.
Anthos Network Security
Implement firewall rules on your on-premises network to restrict access to the control plane. Access to cluster master nodes should be restricted to trusted IP ranges.
It is recommended to use authorized networks and private nodes to ensure that the control plane is reachable by:
- The allowed CIDRs in authorized networks
- Nodes within your cluster’s VPC
- Google’s internal production job that manages your control plane
To ensure that your GCP Anthos cluster’s control plane nodes are only accessible through authorized networks and trusted IP ranges, you can leverage security tools such as Paladin Cloud. These tools can help you catch any misconfigured settings and ensure that your resources remain compliant. For instance, if someone accidentally creates a public Google Cloud Anthos cluster with a control plane accessible outside the authorized network, Paladin Cloud’s security policy will flag it as noncompliant and provide remediation steps.
Enable Binary Authorization
By default, Kubernetes/Anthos allows authorized users to run container workloads from any valid public or private container image registry. Binary authorization ensures that only trusted container images are deployed on Kubernetes.
To protect your cluster, it is essential only to download approved images with required signatures from whitelisted repositories, which reduces the risk of deploying harmful code. You can enforce binary authorization with a well-defined CI/CD process in which the customer defines the signature requirements. Based on that, images are signed throughout the CI/CD process, and image deployments are blocked/allowed at the GKE control plane based on policy.
When a container image initially passes vulnerability scans, that doesn’t necessarily mean that it will always meet security standards since new vulnerabilities or CVEs can be discovered later. It is crucial to scan images both initially and regularly over time to ensure that the security posture meets the desired standards.
It is necessary to ensure that all images comply with relevant security standards, including reviewing, updating, and rebuilding them regularly to obtain new security fixes. You can use Google Cloud container analysis or a third-party tool to scan container images. Aquasec and Red Hat ACS are popular tools for container vulnerability scanning, and their findings can be integrated with Paladin Cloud to notify teams when containers no longer meet their desired security profile.
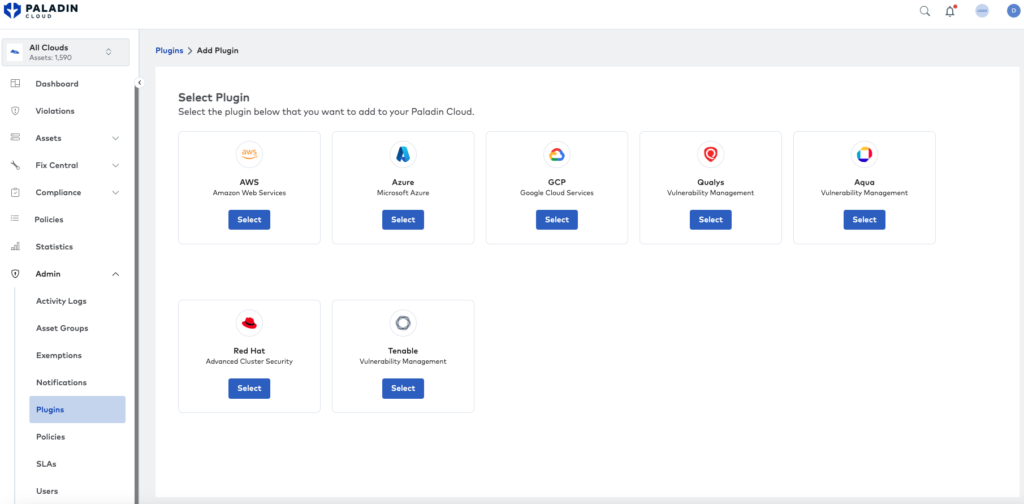
Paladin Cloud third-party plugins; integration with Aquasec and Red Hat ACS enables container security scanning
Anthos Service Mesh
Anthos Service Mesh is a managed platform empowered by Istio that offers a flexible and powerful set of tools and features. Anthos Service Mesh makes it effortless to implement industry-leading practices. This platform works across your entire infrastructure, allowing developers to use extra features without changing your application code.
A service mesh is a robust architecture comprising one or more control and data planes. The service mesh monitors all traffic by deploying a proxy using a sidecar pattern to the microservices within the mesh. This pattern effectively works as a traffic monitor that watches everything, allowing developers to concentrate on building critical business features. Service meshes also enable independent work between development and operations teams, simplifying the process to achieve the desired results.
The following are some of the security benefits of Anthos Service Mesh:
- Mitigates authentication risks: Anthos Service Mesh uses mutual TLS (mTLS) certificates instead of bearer tokens, reducing the risk of replay or impersonation attacks with compromised credentials.
- Encryption in transit: Leveraging mTLS for authentication ensures that all TCP communications are encrypted, enhancing data security during transit.
- Controlled access to sensitive data: Anthos Service Mesh only allows authorized clients, regardless of their network location and application-level credentials, to access services with sensitive data.
- Insider threat mitigation: Anthos Service Mesh reduces the risk of user data breaches within the production network by allowing access to sensitive data only through authorized clients, mitigating insider threats.
- Client identification for sensitive data access: Anthos Service Mesh provides detailed access logging, capturing the mTLS identity of the client along with the IP address and assisting in identifying clients that accessed services with sensitive data.
Anthos Security Patching
Both Google and the customer are responsible for ensuring that patching is done efficiently; it is a shared responsibility.
Using Container Registry Artifact Analysis, Google scans containers to discover vulnerabilities and missing patches in Kubernetes and Google-managed containers. If fixes are available, the scanner automatically begins the patching and release process. In addition to automated scanning, Google discovers and patches vulnerabilities by performing audits, penetration testing, and vulnerability discovery across all Anthos platforms.
Once Google identifies a vulnerability, the Anthos security team classifies vulnerabilities into critical, high, medium, and low categories according to the Kubernetes vulnerability scoring system. They publish security bulletins for high- and critical-severity vulnerabilities and notify customers about them via email.
It is important to upgrade to the latest version of Anthos or GKE because the latest GKE/Anthos versions will fix any security vulnerabilities in the operating system, Kubernetes components, and containers that make up the platform. Some vulnerabilities can be fixed by upgrading the control plane automatically by Google on GKE. However, control plane and node upgrades are required to be upgraded by the customer for some vulnerabilities. Google recommends upgrading your Anthos components at least monthly.
Monitoring Application Security
The Anthos Security dashboard provides a clear and concise view of your applications’ latest security features, letting you quickly identify areas that require improvement. The dashboard’s policy audit view provides a detailed analysis, so you can make informed decisions on modifying security configurations to enhance your security posture.
This Anthos Security dashboard is a must-read for platform and application operators who want to avoid potential security threats by better understanding Anthos application security monitoring. Note that Anthos Security dashboard monitors clusters exclusively on Google Cloud, VMware, and bare metal.
The image below was copied from the official Google Cloud document and shows the status of Anthos application security features in a sample project.

To enhance your ability to view and audit application security through Anthos Security Dashboard, ask your administrator to grant you the following important IAM roles on the project:
- roles/monitoring.viewer (Monitoring Viewer)
- roles/logging.viewer (Logs Viewer)
- roles/serviceusage.serviceUsageViewer (Service Usage Viewer)
- roles/servicesecurityinsights.securityInsightsViewer (Security Insights Viewer)
Additionally, with Paladin Cloud’s advanced prioritization engine, you can effortlessly monitor, prioritize, and mitigate risks across multiple cloud providers. For example, the Paladin Cloud GCP Security Policies, Deny Access to GKE Cluster and Encrypt Application Layer Secrets for GKE Cluster will help you identify environments that are not following security best practices.
Conclusion
To ensure a secure and resilient cloud-native environment, implement Anthos security best practices using secure communication channels, robust identity and access management, comprehensive monitoring, and regular system patching. Anthos provides a scalable platform for modernizing applications along with robust security features. Effectively utilizing these features enhances your security posture, maintains regulatory compliance, and builds trust.
As businesses adopt containerized solutions, there’s a clear need to secure both containers and their supporting infrastructure. Third-party security products, such as Paladin Cloud with its Cloud Security Posture Management (CSPM) module, can safeguard the security of your Anthos environment.
Regular training, Kubernetes-based certifications such as Certified Kubernetes Administrator (CKA) and Certified Kubernetes Security Specialist (CKSS), and collaboration among your team members are crucial elements in maintaining a proactive and adaptive security stance within your Anthos environment. By incorporating security in every aspect of your Anthos deployment, you’ll be equipped to navigate the ever-changing cybersecurity landscape.

