The rapidly changing landscape of cloud security necessitates robust tools and practices. Google’s Security Command Center (SCC) offers a comprehensive suite of features to protect your data and operations. This article will delve into the core concepts of SCC along with its history, functionality, best practices, limitations, and how integration with Paladin Cloud can enhance its capabilities.
Historical context of Google Security Command Center
Google’s Security Command Center began as a response to the increasing need for multifaceted security solutions in the cloud environment. Its evolution has been guided by the ongoing changes and challenges in the field of cybersecurity. By understanding the history of SCC, we can grasp what it currently offers and does not offer, making it easier to align its capabilities with our specific needs.
Summary of key Google Security Command Center concepts
Google Security Command Center (SCC) evaluates your security and data attack surface on Google Cloud by performing threat discovery, Security Health Analytics and data loss prevention. The table below summarizes these core concepts.
| Concept | Description |
|---|---|
| Threat discovery | Identification and analysis of potential security threats. |
| Security Health Analytics (SHA) | Monitoring and analysis of security postures. |
| Data loss prevention (DLP) | Tools for protecting sensitive data. |
The image shows the SCC coverage overview (Source)
Threat discovery: identification and analysis of potential security threats
This critical component of SCC is designed to continually scan the cloud environment, identifying and analyzing potential security threats. By employing advanced algorithms, it not only detects threats in real time but also provides actionable insights to handle them. This continuous vigilance can help organizations pre-emptively address risks before they escalate. Account takeover, business email compromise, and bot abuse are only some of the top threats detectable.
Security Health Analytics: monitoring and analysis of security postures
Security Health Analytics in SCC functions like a vigilant sentinel, constantly monitoring the security postures within the organization’s cloud. By evaluating various metrics, detecting misconfigurations, and analyzing user behaviors, it provides a comprehensive overview of the system’s security health. Regular reports and timely alerts ensure that any anomalies are promptly addressed, maintaining the overall integrity of the system.
Data loss prevention (DLP): tools for protecting sensitive data
Data is often considered the lifeblood of modern businesses, and losing it can have devastating consequences. SCC’s data loss prevention tools protect sensitive data with robust encryption, access controls, and monitoring. They ensure that valuable data stays secure while preventing unauthorized access or accidental loss, allowing businesses to operate with confidence. DLP tools also help both classify and prioritize sensitive data along the way, helping narrow the overall threat landscape for digital assets.
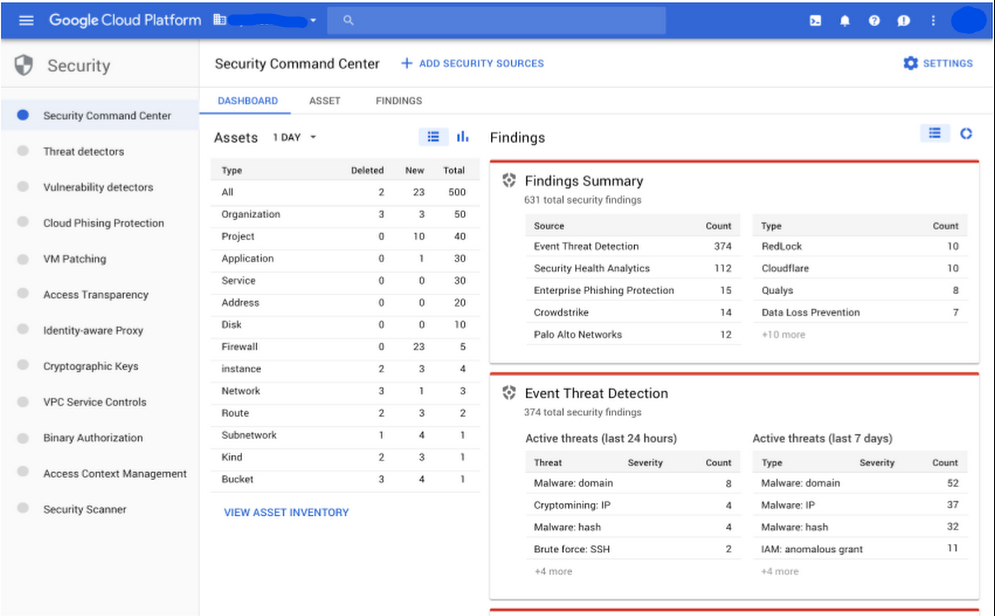
An overview of the SCC interface from Google Cloud Platform (GCP) (Source)
How Google Security Command Center works
Threat discovery
Google Security Command Center’s (SCC) threat discovery is a pivotal component aimed at safeguarding the cloud environment. Using complex algorithms, SCC continuously searches for potential security risks, providing real-time alerts and insights. SCC can detect misconfigured storage buckets that might inadvertently expose sensitive data to the public or trace unusual IAM role assignments that could escalate privileges beyond intended limits. It also identifies potential web application vulnerabilities or traces of data exfiltration. By keeping an eye out for such security risks, SCC plays a pivotal role in ensuring that organizations maintain a robust security posture within the Google Cloud ecosystem.
- Continuous scanning: SCC threat discovery operates around the clock, monitoring your cloud assets and applications for any suspicious activities or vulnerabilities.
- Intelligent analysis: Leveraging machine learning algorithms, it categorizes threats based on severity, helping you prioritize your response.
- Real-time alerts: SCC notifies your security team immediately upon detecting a threat, allowing for swift action.
- Integration with other tools: It can be customized to work in harmony with other security tools (including Paladin Cloud), enhancing its effectiveness.
Security Health Analytics
SCC’s Security Health Analytics (SHA) is a tool for maintaining the health and integrity of your cloud systems. Through comprehensive monitoring and analysis, it ensures that everything is functioning as it should in a variety of ways:
- Monitoring security postures: It continually evaluates security configurations and user behaviors across various cloud services.
- Detecting misconfigurations: Identifying misaligned security settings helps prevent potential vulnerabilities. One vulnerability that SCC can identify is publicly accessible storage buckets. Cloud storage buckets, such as those in Google Cloud Storage, are used by organizations to store a plethora of data, ranging from website assets to sensitive organizational data. By default, these storage buckets are private. However, misconfigurations can sometimes leave them accessible to anyone with the link; they can even become publicly searchable, potentially leading to massive data breaches. In the past, numerous instances have been reported where companies inadvertently left their storage buckets open to the public, leading to the exposure of sensitive data like customer details, internal documents, or even database backups. Cloud storage misconfigurations can be even more difficult to detect in multi-cloud environments. Third-party tools, like Paladin Cloud, provide the ability to detect security misconfigurations from multi-cloud environments like GCP, AWS, and Microsoft Azure. We will consider other limitations of SCC later in the article.
- Providing insightful reports: Through detailed analytics, SCC offers actionable insights into your security landscape. For instance, its ability to autogenerate comprehensive IAM role assignment reports can pinpoint anomalies, such as a marketing team member unexpectedly receiving database admin privileges. Such insights, whether indicating a mere oversight or a potential security breach, highlight SCC’s proficiency in proactively detecting risks and enabling organizations to promptly rectify problems and fortify their security measures.
- Facilitating compliance: SHA helps in ensuring that your cloud environment aligns with regulatory requirements, simplifying compliance management.
Data loss prevention
DLP in SCC is geared to protect the most vital asset in the digital age: data. These tools ensure that valuable data stays secure, preventing unauthorized access or accidental loss. DLP acts as a safeguard, ensuring that sensitive information remains within the secure confines of your organization:
- Robust encryption: It employs strong encryption methods to secure data both at rest and in transit.
- Access controls: By managing who can access what, it adds an extra layer of security.
- Monitoring data movement: DLP keeps a vigilant eye on data, alerting on unauthorized or suspicious access or transfers.
- Compliance alignment: It helps maintain compliance with various data protection regulations, supporting organizational adherence to legal requirements.
- Data classification and data masking/tokenization: It identifies sensitive elements within the data, such as credit card numbers or personally identifiable information (PII), and replaces them with tokens or masks.
Configuring Google Security Command Center
Correctly configuring SCC is crucial. Here are step-by-step instructions to set it up optimally:
- Set up threat detection: Instructions
- Configure Security Health Analytics: Tutorial
- Understanding SCC’s functionality is one thing; implementing it effectively is another. Here are some examples that emphasize best practices:
- Tutorial for data loss prevention: Instructions
- Using Big Query to structure data: Tutorial
Best practices for using Google Security Command Center
This section will provide an in-depth look into Google Security Command Center, offering practical examples, best practices, and known limitations.
Understand Security Needs
Before diving into the configuration, assess and define your organization’s specific security requirements. This understanding allows you to tailor SCC’s functions to align with your unique needs.
Leverage built-in templates
Google SCC comes with predefined security policies and templates. Using these as a starting point can expedite the configuration process while ensuring adherence to best practices.
Set up proper access controls
Access controls are fundamental to security. Within SCC, define user roles and permissions carefully. Limit access to sensitive features and data to only those who absolutely need it by following the principle of least privilege.
Customize threat detection
SCC’s threat discovery tool can be customized. By setting specific parameters that align with your business’s risk profile, you can ensure that the tool looks out for the particular threats most relevant to your organization.
For instance, an ecommerce platform handling daily credit card transactions might be particularly vulnerable to SQL injections or unauthorized data access attempts. To address this, the platform’s team can fine-tune SCC’s parameters to prioritize alerts related to database queries, unusual data transfers, or suspicious script activities. In this way, SCC’s customized threat detection becomes a tailored security shield, ensuring that the platform is safeguarded against the most relevant and potential threats, like unauthorized crypto mining.
Configure Security Health Analytics
Optimize SHA to provide timely and relevant insights. Regularly review and update the configurations to keep up with the ever-changing security landscape.
Enable DLP features
DLP in SCC can be fine-tuned to meet your data protection requirements. Configuration should consider factors like data sensitivity, regulatory compliance, and internal policies.
Test and validate
After configuring, it’s essential to test the system to validate that all settings are functioning as intended. Regular testing helps uncover any unnoticed issues.
Regularly monitor and update
Configuration is not a one-time task. Regularly review and update the configurations to adapt to changes in the security landscape, organizational needs, or regulatory requirements. A few of the features that can be found are as follows:
- Pub/Sub for real-time alerts: SCC can configure real-time alerts using Google Cloud Pub/Sub. Once an alert condition is met, a message is published to a designated Pub/Sub topic, enabling immediate notifications. This allows for the rapid dissemination of critical information to your security team, effectively minimizing the time between threat detection and response.
- Cloud Functions for automated mitigation: Going a step further, SCC can also trigger Google Cloud Functions based on these Pub/Sub messages. For example, if an unauthorized user is detected attempting to access a sensitive area, a Cloud Function could be invoked to automatically revoke their access permissions.
For those interested in setting up real-time notifications, you can refer to Google’s official guide on enabling real-time notifications here.
Document and comply
Document all configurations, changes, and rationales. Proper documentation supports compliance efforts and provides valuable insights for future configuration modifications. These additional features enhance both documentation and compliance adherence, acting as invaluable tools for a comprehensive security strategy.
Here are some specific relevant features:
- Attack path simulation: One of the standout features, attack path simulation models how an attacker might exploit vulnerabilities to move laterally across your network. This not only helps in identifying weak points but also aids in proactive mitigation planning.
- SIEM integration: SCC can be seamlessly integrated with security information and event management (SIEM) solutions. This aids in centralized logging and real-time analysis of security alerts generated by SCC, making it easier to track, document, and react to security events across different platforms.
- SOAR integration: Security orchestration, automation, and response (SOAR) can also be integrated into SCC. This allows for automated playbooks and response actions, like automated patching or alert escalation, to be executed directly through the Security Command Center, making compliance and response more efficient.
- Asset query: SCC offers a feature to perform complex queries on your assets, enabling you to create a comprehensive inventory. This is crucial for identifying unprotected assets and ensuring that all components are included in your security audits for better compliance.
These extended features make Google Security Command Center not just a tool for threat detection but a comprehensive platform for security governance, risk management, and compliance (GRC). They fortify your overall security posture, allowing you to transition from reactive to strategic security planning. As a rule of thumb, it’s best to automate, audit, and perform compliance checks quickly whenever possible.
Utilize configuration management tools
If your organization operates on a larger scale, consider utilizing configuration management tools that can help in maintaining and automating the configurations across different environments within SCC.
Limitations of Google Security Command Center
While SCC is a powerful tool, it has its limitations. Understanding them will help you utilize SCC to its fullest potential.
Limitations in threat discovery
Google SCC has made remarkable strides in threat discovery, enabling organizations to spot and respond to a myriad of vulnerabilities and threats within their Google Cloud environments. However, like any tool, there are complexities and evolving threat landscapes that might pose challenges even to SCC’s comprehensive detection algorithms.
One type of threat that sophisticated attackers employ is a “low and slow” attack strategy. Here, an adversary conducts malicious activities at a pace that’s deliberately designed to avoid detection. These types of attacks often involve:
- Slow scans: Instead of scanning a network for vulnerabilities rapidly, which could trigger alarms, attackers spread out their reconnaissance over days or even weeks.
- Gradual data exfiltration: Instead of quickly extracting large volumes of data, which might get flagged, attackers might siphon off smaller chunks of data over an extended period.
- Intermittent C&C communications: Command and control (C&C) servers, used to control compromised devices, might be contacted infrequently to avoid detection patterns.
SCC, which is designed to recognize malicious behavior patterns, might face challenges detecting such stealthy techniques. While it can spot rapid, abnormal spikes in traffic or unauthorized activities, the subtle and prolonged nature of “low and slow” attacks might sometimes fall below its detection threshold. This underscores the necessity for organizations to have layered security approaches, including behavioral analytics and advanced threat intelligence, to catch such sophisticated strategies.
Limitations in data loss prevention
SCC’s DLP is pivotal in identifying and protecting sensitive data across various GCP services. Designed to detect patterns and flag content that might be of concern, it has been instrumental in preventing many inadvertent data exposures. Nevertheless, like any advanced tool, there are certain intricate scenarios where its scope might not cover every risk.
This example demonstrates the potential shortcomings of DLP when dealing with encrypted or obfuscated sensitive data.
- Setup: Create a sample text file with sensitive information, such as a Social Security Number (SSN). Encrypt or obfuscate this SSN using a custom algorithm or a standard method that isn’t typically recognized by conventional tools.
- Configure DLP in SCC: Set up the DLP tool in SCC to monitor a Google Cloud Storage bucket where you’ll upload the file. Configure the DLP to scan for SSNs within stored files.
- Upload the file: Place the text file with the encrypted or obfuscated SSN into the Cloud Storage bucket.
- Run the scan: Activate the DLP scan and let it process the files within the bucket.
- Observe: Post-scan, you may find that the DLP tool identifies direct text patterns that match the format of SSNs, but it might miss the encrypted or obfuscated SSN in the file.
Additional limitations to consider
The following are some additional limitations that are high-level considerations to take into account:
- Complexity in configuration: SCC’s native tools can sometimes become overwhelming and complex to configure, particularly for small and medium-sized businesses without dedicated security teams.
- Usage and quota limitations: SCC has some caps on usage that you should be aware of; they are described here.
- Gaps in threat intelligence: SCC’s threat intelligence is substantial but can still miss certain specialized or evolving threats.
- Limited to Google Cloud: SCC only works with GCP. A third-party tool like Paladin Cloud offers oversight of multi-cloud environments.
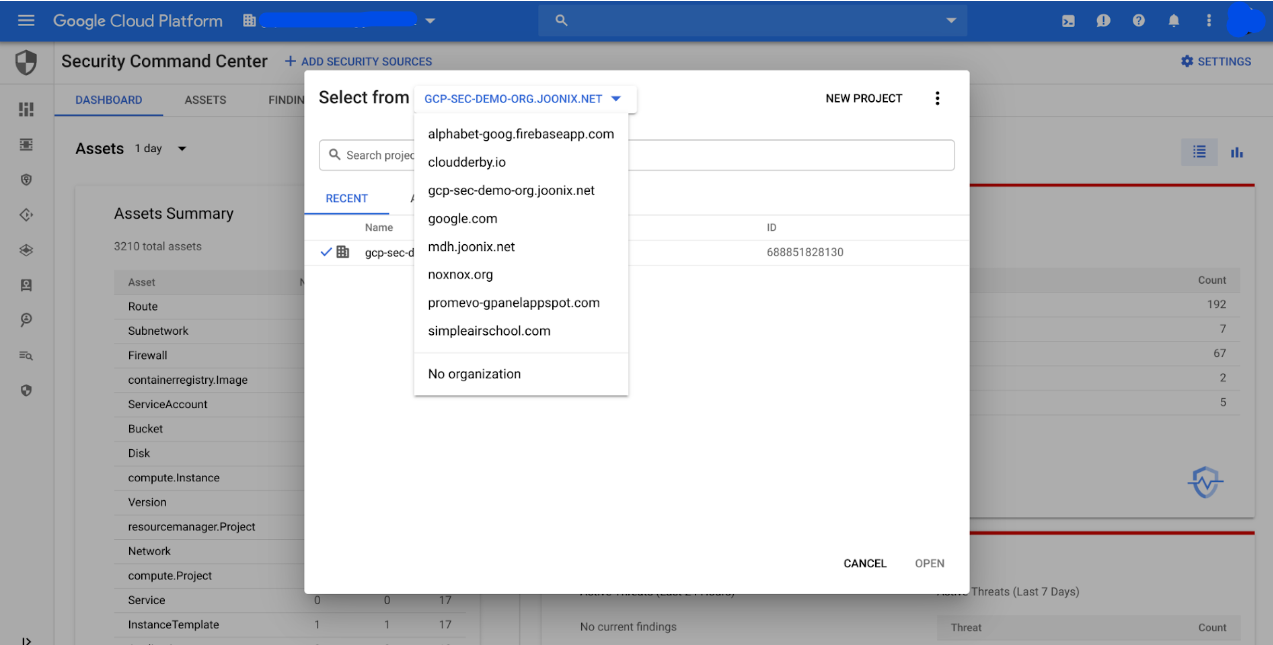
An example of managing multiple organizations or integrations in SCC (Source)
Paladin Cloud integration to overcome SCC limitations
While SCC offers an impressive array of tools and functionalities, it is not without limitations. Integration with Paladin Cloud can enhance its capabilities, filling the gaps and creating a robust security environment that mirrors Paladin Cloud’s strategies with other cloud services. The result can be a robust, flexible, and efficient security environment.
Paladin Cloud’s integration fills these gaps and builds upon SCC’s strengths by:
- Offering preconfigured settings: One common challenge with SCC is the complexity of configuration, particularly for organizations without dedicated security expertise. Paladin Cloud offers preconfigured settings that align with common security needs, simplifying the configuration process.
- Streamlined monitoring and reporting: Combining SCC’s security health analytics with Paladin Cloud’s monitoring tools provides a unified security overview, making reporting and analysis more streamlined.
- Ongoing collaboration: The integrated system works in tandem, continually communicating and sharing information to offer comprehensive security coverage.
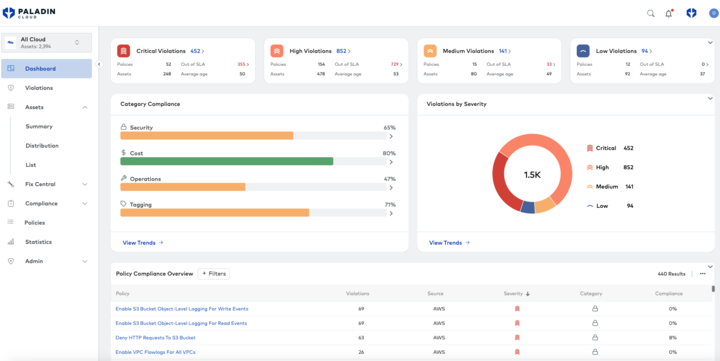
An example of a Paladin Cloud dashboard showing policy violations for Google Cloud (Source)
In essence, while SCC is a valuable tool for threat discovery in Google Cloud, understanding its potential blind spots helps organizations reinforce their security postures even further by integrating SCC with complementary security solutions.
Conclusion
Google Security Command Center (SCC) serves as a comprehensive security management platform, offering features ranging from threat discovery to data loss prevention and real-time alerts. Its customizable nature allows it to align well with various organizational needs, though it’s essential to be aware of its limitations and to consider integrating third-party solutions like Paladin Cloud for a more robust security posture.
The platform continues to evolve, with Google consistently rolling out updates and new features. Therefore, it’s crucial to stay updated with these improvements to maximize your security efforts effectively.

