In today’s interconnected world, companies of all sizes are using the cloud, leveraging its scalability, cost-effectiveness, and flexibility. However, as organizations migrate their critical data and applications to cloud platforms, they must grapple with a new set of challenges: cloud vulnerabilities. These digital chinks in the organizational armor expose sensitive information, jeopardizing data integrity, customer trust, and business continuity.
Cloud vulnerability management is the process of assessing cloud resources to address misconfigurations and security flaws that cybercriminals might exploit. The Equifax Data Breach in 2017 was an example of how poor cloud vulnerability management can have serious consequences. The breach was attributed to a known vulnerability in a web application that Equifax had failed to patch despite receiving alerts from the US Department of Homeland Security about the flaw.
As companies are inundated with a backlog of alerts, it can be challenging to prioritize what they need to investigate and remediate in a timely manner. This article delves into the intricacies of cloud vulnerability management and alert fatigue in cybersecurity. We explore the shared responsibility model, how to manage cloud vulnerabilities, critical problems, the most common vulnerabilities, their remediation, and best practices.
Summary of key cloud vulnerability management concepts
| Concept | Description |
|---|---|
| The shared responsibility model | The cloud service provider (CSP) and customer have a shared responsibility for security. CSPs secure the core infrastructure, while customers are responsible for configuration, access control, encryption, patch management, and vulnerability mitigation. |
| How to manage cloud vulnerabilities | Six steps an analyst can take to address problems in cloud vulnerability management are listing assets, assessing vulnerabilities and misconfigurations, prioritizing, remediating, monitoring and reporting, and repeating the process. |
| Critical problems in cloud vulnerability management | Critical problems in cloud vulnerability management include high volume, false positives, repetitive tasks, a lack of skilled analysts, and having too many buried tools. |
| The most common cloud vulnerabilities and their remediation | The Cloud Security Alliance identified unpatched web services, secrets in Git, AWS keys stored in the file system, and overprivileged IAM roles as the most common cloud vulnerabilities in 2023. Remediation requires taking proactive action to discover and correct these issues, with the specifics tailored to each specific vulnerability. |
| Best practices for cloud vulnerability management | Effective prioritization, automation, hiring skilled analysts, maintaining an up-to-date asset inventory, consolidating tools, and using a tool such as the Paladin Cloud Prioritization Engine are best practices for cloud vulnerability management. |
The shared responsibility model
The shared responsibility model describes the division of responsibilities between cloud service providers (CSPs) and their customers. In general, CSPs are responsible for securing core infrastructure, while cloud users are responsible for configuration, access control, encryption, patch management, and vulnerability mitigation.
The shared responsibility model requires collaboration. Both customers and CSPs must actively create security policies and procedures to minimize gaps in vulnerability management.
How to manage cloud vulnerabilities
The table below provides a step-by-step guide to managing vulnerabilities in the cloud.
| Step | Description |
|---|---|
| 1. Get the “lay of the land” | List all assets that are part of the cloud environment. |
| 2. Assess vulnerabilities and misconfigurations in the environment | Teams can do this through vulnerability scanning and assessments |
| 3. Prioritize | Prioritize findings based on criticality and business needs. |
| 4. Remediate | Remediate the prioritized vulnerabilities. |
| 5. Monitor and report | These steps are essential because if you can’t measure it, you can’t manage it. |
| 6. Repeat | Vulnerability management should become part of your everyday operations—a proactive rather than reactive approach. |
1. Get the “lay of the land”
One of the significant challenges many companies face is a need for more visibility into their cloud assets. This means ensuring the ability to see resources, configurations, policies, and activities. Effective cloud asset management is crucial for organizations to maintain security, compliance, and cost optimization. Without proper visibility, companies risk overspending, misconfigurations, and an increased attack surface with potential security vulnerabilities.
2. Assess vulnerabilities and misconfigurations in the environment
Some of the methods of assessing vulnerabilities and misconfiguration include:
- Conducting regular audits, using cloud security posture management (CSPM) and cyber asset attack surface management (CAASM) to remediate cloud misconfigurations
- Practicing the principle of least privilege
- Using infrastructure as code (IaC) to maintain consistency
- Performing vulnerability scanning and penetration testing
3. Prioritize findings based on criticality and business needs
To effectively prioritize findings, security teams must align their efforts with the organization’s business goals. Here’s why this alignment matters:
- Contextual Relevance:
- Not all risks are equal. Some directly impact critical business processes, while others may be less significant.
- By understanding business goals, security analysts can tailor their risk assessments. For instance:
- If an application hosts sensitive customer data (e.g., financial records, personal information), any high-risk findings related to it become paramount. The potential damage to customer trust and legal repercussions necessitates swift action.
- Conversely, a critical finding in a web app containing only public data (e.g., marketing content) may not have the same urgency. While it still requires attention, the business impact is likely lower.
- Resource Allocation:
- Organizations have finite resources—time, budget, and personnel. Prioritization ensures efficient resource allocation.
- By considering business goals, security teams can allocate resources where they matter most. For example:
- Protecting customer data aligns with business continuity and regulatory compliance.
- Addressing public-facing web apps contributes to brand reputation and user experience.
Security professionals should view risk assessment as a strategic endeavor. By assessing criticality, understanding likelihood, and aligning with business objectives, they can make informed decisions that safeguard the organization’s interests. Remember, risk management isn’t just about fixing vulnerabilities; it’s about protecting what matters most to the business.
Paladin Cloud’s AI-powered prioritization engine plugs into existing security tools and clouds to prioritize and correlate findings across application, data and cloud security.
4. Remediate the prioritized findings
Security teams must take a “shift-left approach” to remediate vulnerabilities in the same sprints where they are building. Security checks should be integrated as early and often as possible in the software development lifecycle rather than waiting until deployment. Leadership must agree on what percentage of the sprints to focus on remediating active vulnerabilities based on severity and the business impact of active threats.
Jira is a ticketing system that has the power of automation of workflows. A scrum master or product owner can build out epics, user stories, and tasks that assign a designated amount of work per sprint to security tasks.
5. Monitor and report
Visualize and manage your application and cloud security risks in a single platform. Monitoring and reporting on cloud vulnerabilities are essential for protecting cloud data and applications from cyber-attacks. Monitoring and reporting involves documenting and communicating identified risks, their impacts, and the recommended mitigations to relevant stakeholders.
6. Repeat
To uphold security standards throughout regular work activities, repeat the first five steps of managing vulnerabilities in the cloud repeatedly.
Critical problems in cloud vulnerability management
Many organizations suffer from alert fatigue for a variety of reasons.
| Problem | Description |
|---|---|
| High volume and false positives | Generating alerts alone does not provide value to the organization. It takes skilled analysts to create rules and configurations that are meaningful. |
| Repetitive tasks | Repetitive tasks affect the mental wellbeing of employees. |
| Lack of skilled analysts | There is a need for more skilled cybersecurity analysts who can effectively sort through alerts and pick what is most valuable to address. |
| Too many buried tools | There are over 18,000 tools available on the Azure marketplace, and many companies need a comprehensive asset inventory. |
High volume and false positives
Joint research from the Ponemon Institute and Exabeam revealed that security personnel waste approximately 25% of their time analyzing false positives. This troubling statistic shows how generating alerts alone does not provide value to an organization.
An intrusion detection system (IDS) like Snort has default rules that can make typical Microsoft Outlook behavior look like malware. An analyst who inspects packets thoroughly can refine rules to reduce false positives. Here is an example:
alert tcp any any -> any 25 (msg "IOC! Outlook sending email to external SMTP server";flow:to_server,established; content:"EHLO OUTLOOK"; nocase; classtype:web-application-attack; sid:10000001; rev1;)
This rule will alert a user about TCP traffic sent to any destination port 25 (SMTP) that contains the string “EHLO OUTLOOK” in the payload. The string is usually sent by Outlook clients when initiating an SMTP session. However, if Outlook sends email to an external SMTP server, it could indicate a compromise is being used to send spam or exfiltrate data. It is easy to see why a typical rule can generate a large amount of false positives.
Repetitive tasks
Repetitive tasks can cause fatigue, boredom, job dissatisfaction, and burnout. While some repetition is inevitable in any job, excessive repetition can negatively affect workers and employees.
Lack of skilled analysts
The State of Security 2023 report by Splunk found that 88% of respondents report talent challenges. Analyst positions, whether network, cloud, or cybersecurity, require high technical expertise and experience.
For example, companies like the SANS Institute offer certificates such as GIAC Certified Intrusion Analyst (GCIA) that will train analysts to inspect network packets. This class is one of the most difficult 500-level courses the company offers. Only a few classes dive into such technical specifics, and unless you have already worked a job with a mentor doing such tasks, it is a difficult skill to hire for.
Too many buried tools
According to the official website, over 18,000 apps and services are available in the Azure Marketplace. A large organization can quickly end up with dozens of tools to manage day-to-day activities such as security, performance, cost, and compliance. Tool sprawl can result in too many tools, leading to increased costs, reduced efficiency, and lower visibility.
The most common cloud vulnerabilities and their remediation
In this section, we take a look at the Cloud Security Alliance’s top cloud vulnerabilities in 2023 and how they are best remediated.
Unpatched web services
A report by the cloud security company Orca Security revealed that over one-third of organizations have unpatched web services exposed to the internet in their cloud environments. This finding indicates a severe risk of cyber-attacks. Attackers can easily exploit known vulnerabilities to tamper with the web service’s content or functionality, gain unauthorized access to other cloud resources or data, exfiltrate sensitive information, or launch additional attacks on the network.
Remediation: Companies must discover and correct vulnerabilities in their cloud environments before attackers exploit security weaknesses that cause harm. They can do this by conducting penetration tests, performing vulnerability assessments, and using tools that scan their cloud assets continuously. They should prioritize internet-facing systems that may contain sensitive information.
Secrets in Git
Sensitive information can mistakenly get pushed to a Git repository. In 2022, Toyota revealed that it had accidentally exposed a secret key publicly on GitHub when a subcontractor uploaded source code to a repo that was set to public. This publicly displayed source code resulted in unauthorized access to customers’ email addresses.
Remediation: If the damage has already been done, users can leverage an open source tool such as BFG to remove it from the history. To prevent leaking data in the first place, developers can use a .gitignore file to specify files or directories that they do not want to track in Git. Using tools like GitGuardian to scan the repository for sensitive information is essential before deploying.
AWS keys stored in file systems
Developers often prioritize efficiency and productivity, which may compromise the security of the organization. For example, AWS keys are credentials that grant access to various AWS resources and enable the execution of different operations, such as launching or terminating instances and creating or deleting objects.
Storing AWS keys in the file system of a virtual machine may be convenient, but it is not a secure practice because it can expose keys to misuse by attackers. The worst part is that these keys are stored in the file system by default.
Remediation: AWS advises its users to use tokens rather than AWS keys. Tokens are temporary credentials that developers can use to restrict specific permissions and scopes. In addition, users can leverage tools such as AWS Secrets Manager or Azure Key Vault to securely store, distribute, and rotate secrets using encryption.
Overprivileged IAM roles and lambda functions
Privilege creep is a common cybersecurity issue that affects many organizations and systems. It refers to users or service accounts gradually gaining more access rights or permissions than required to carry out their tasks.
Privilege creep can happen for various reasons, such as users getting promoted, temporary assignments, or providing access to third-party vendors. Users with excessive privileges can view, modify, delete, or exfiltrate information they should not be able to access. It is common for companies to have too many admins or lambda functions with excessive privileges.
Remediation: It is essential to understand and prevent privilege creep by following the principle of least privilege and using a privileged access management (PAM) solution.
Best practices for cloud vulnerability management
Prioritize effectively
The first step to prioritizing vulnerabilities is to understand the business’s priorities and risk tolerance. Which systems have the highest risk associated with them? Given that knowledge, assess the criticality and likelihood of risk for the systems with the highest risk using a standard scoring system such as CVSS.
If this seems like a lot of manual labor, that’s because it is. Luckily, a new product category is emerging to unify vulnerability management across tool categories, such as CSPM, application security and vulnerability scanning. An example is Paladin Cloud’s AI-Powered Prioritization Engine that uses Generative AI to risk score findings across tools to prioritize and remediate the most important risks.
Automate repetitive tasks
Cloud analysts can save time, reduce errors, improve productivity, and focus on more strategic work by automating repetitive tasks. For example, activities like patch management of Amazon EC2 instances can be automated to tackle high volumes of vulnerabilities efficiently.
Hire skilled analysts
Companies can address the talent shortage in cybersecurity by doing the following:
- Offering competitive salaries and benefits
- Investing in their current employees with continuous education, certificates, and mentor programs
- Partnering with colleges and other agencies that provide access to incoming talent
- Leveraging tools and automation to replace the need for skilled analysts
Maintain an up-to-date asset inventory
Regularly scanning cloud environments is vital for recording all cloud assets and keeping an inventory up to date.
Consolidate tools
Having too many tools can add complexity to an analyst’s job. By consolidating tools, businesses can reduce the number of data sources, platforms, and vendors they have to deal with, instead using a smaller set of tools that are more productive and efficient. Regardless of the number of tools used, consolidating outputs into a single platform will help security teams focus on what matters most by deduplicating, correlating, and contextualizing findings.
Use Paladin Cloud’s AI-Powered Prioritization Engine
One way to implement all the solutions listed above is to use the right tool. Paladin Cloud’s Prioritization Engine helps identify, prioritize, and remediate security risks. It will significantly reduce alert fatigue and monotonous tasks.
The tool uses generative AI to score cloud vulnerabilities, allowing analysts to correlate cybersecurity risks and misconfigurations with business needs. It also provides a heat map of all cloud assets and has the ability to segment data using asset groups. Using a tool such as the Prioritization Engine will reduce the need for skilled analysts to sort through false positives that cause alert fatigue in cybersecurity.
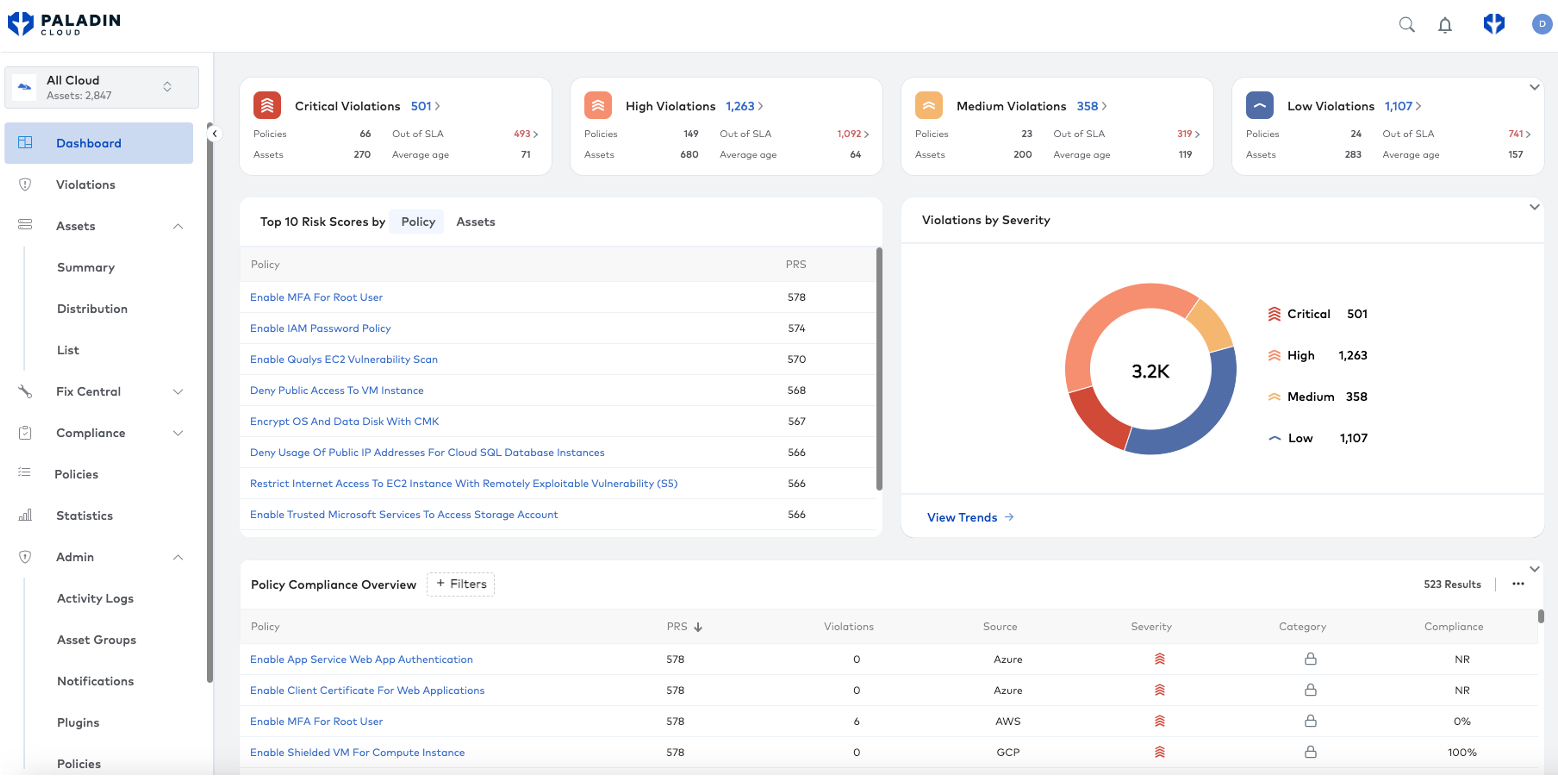
Paladin Cloud’s prioritization dashboard unifies findings from multiple security tools into a single location and uses generative AI to determine the top 10 risk scores.
Last thoughts on cloud vulnerability management
Cloud vulnerability management is vital for ensuring security and compliance in cloud environments. As cloud adoption continues to grow, especially the use of hybrid and multi-cloud models, it is crucial for analysts to adopt best practices and ensure that security integrates into their operations.
Manage cloud vulnerabilities by following a six-step process: list assets, assess vulnerabilities and misconfigurations, prioritize, remediate, monitor and report, and then repeat.
Alert fatigue in cybersecurity is a common problem for analysts who have to deal with many security alerts that are false positives or low in priority. Alert fatigue can lead to reduced efficiency, increased stress, and missed indicators of compromise.
To address this issue, analysts should follow these best practices:
- Automate tasks using tools or scripts to reduce repetitive tasks.
- Prioritize vulnerabilities. Paladin Cloud’s AI-Powered Prioritization Engine scores risks based on policies and can correlate across multiple cloud environments.
- Hire skilled analysts or use tools capable of sorting through a high volume of alerts.
- Maintain an up-to-date asset inventory.
- Consolidate tools to simplify workflows and avoid inconsistency.
- Use continuous adaptive automated security monitoring tools such as Paladin Cloud’s Prioritization Engine that can monitor and analyze an organization’s security posture continuously and adaptively and provide actionable recommendations. Paladin Cloud’s tool that can evaluate and prioritize alerts based on factors such as threat intelligence, asset value, and business context.