Threat and vulnerability management is vital to maintaining an organization’s security. Security Magazine reported in 2021 that 76% of IT security executives suggested that one or more security vulnerabilities impacted business within that year. An increase in people and assets, as well as a larger footprint, will inevitably increase the number of people who, maliciously or not, may expose data or resources to the public. It also means more to manage and a higher likelihood of introducing misconfigurations, insecure code, or stale software into the environment. This all leads to a larger attack surface.
Before we dive into the details, let’s clarify the differences between threat and vulnerability management. Threats are potential dangers that might exploit a weakness within a system, while vulnerabilities are what would be exploited by those threats. For example, threats would be things like malicious actors or uneducated users, where the corresponding vulnerabilities might be outdated software on public-facing resources or excessive user access to resources where it is not needed. Similarly, malware is an example of a threat that seeks to exploit one or more vulnerabilities.
This article provides a detailed discussion of key considerations for your organization’s threat and vulnerability management capabilities. Starting with a quick briefing on threat and vulnerability management principles, it then discusses the different components of successful threat and vulnerability management. The article focuses more on vulnerability management because a threat generally takes advantage of an existing vulnerability. Avoiding vulnerabilities is an important defense against threats and includes using zero-trust architecture, integrating third-party tools, and using AI and machine learning to automate specific workflows.
Summary of key threat and vulnerability management concepts
| Concept | Description |
|---|---|
| Threat and vulnerability management | Threat and vulnerability management are two slightly different but equally important components of a cybersecurity program. Threat management involves detecting and protecting against threats that might seek to exploit weaknesses within a network. Vulnerability management seeks to remove those weaknesses from the environment altogether. |
| Frameworks for threat and vulnerability management | There are multiple frameworks and guides available to aid in your threat and vulnerability management processes, including the NIST Cybersecurity Framework (CSF) and the MITRE ATT&CK framework. scoring systems like CVSS, SSVC, and EPSS are used to help assess the risk of a given vulnerability being exploited. |
| Components of threat and vulnerability management | A solid threat and vulnerability management program consists of tools, policies and standards, and personnel.
Considerations for vulnerability management include accounting for backward compatibility and planning for downtime. Cloud environments come with additional considerations, such as resources being publicly accessible when they shouldn’t and calculating the true risk associated with non-persistent virtual resources. Your network’s architecture itself is a component of your vulnerability management program. Many organizations are moving to or planning a move to a zero-trust architecture. |
| Best practices for threat and vulnerability Management | Whether you’re just starting or are looking to improve your threat and vulnerability management capabilities, it’s highly recommended that you start with asset discovery. Once you know which assets are on your network, enumerate their vulnerabilities and prioritize your efforts based on severity, topology, and function. Finally, determine the best strategies for your organization. |
What are the differences between threat and vulnerability management?
Threat and vulnerability management both exist to protect an organization’s network, keeping its users and resources secure from compromises of confidentiality, integrity, and availability, but the two accomplish their goals differently.
Threat management
Essentially, threat management is looking for signs of an attempted breach or signs of a successful breach in the process of pivoting or exfiltrating data. When we discuss threat management, we often think of security operations centers (SOCs), threat hunting, and incident response (IR). These are all relatively reactive approaches involving querying log files for activities like failed login attempts, attempted downloads, and attempts to establish connections to suspicious IPs or outright known malicious IPs.
Vulnerability management
In contrast to reactive measures, vulnerability management is more proactive, involving reducing your network’s attack surface by removing the opportunities that attackers (or unwitting users) might exploit. These activities involve actions like securing any code that might expose data or provide access to internal systems, reviewing permissions and fixing any overly permissive accounts or roles, and upgrading vulnerable software. Depending on your organization and industry, vulnerability management may even include physical security.
Example of threat and vulnerability management
Consider this example of how threat and vulnerability management work together. Suppose that someone observes that your public-facing website provides server information when displaying an HTTP status code. Displaying server information is a vulnerability management issue because it lets would-be attackers know more about your environment and gives them a starting point to begin searching for applicable exploits. Threat management would be having your SOC review logs for that particular web server, looking for some of the more applicable exploits related to that server’s operating system (OS) and version information.
How would we even go about detecting a vulnerability like the one in this example? There are steps to both threat and vulnerability management, which we will discuss in detail.
Steps in threat management
Threat management, often in the form of incident response, includes the following steps:
- Detection: First, to be able to respond to an incident, you need to know that one is occurring.
- Containment: Once an incident has been detected, it needs to be contained to minimize damage. This usually involves quarantining the impacted assets from the network or locking compromised accounts.
- Eradication: After the incident has been contained, the initial cause needs to be removed from the environment. This usually involves deleting malicious software from any infected devices and possibly removing any newly provisioned user or service accounts.
- Recovery: Once the issue has been resolved, it’s time to get back to business as usual. The recovery phase often includes activities like restoring systems from a secure backup image or deploying a new image that is known to be safe for use.
- Review: Once the business is back to normal and the initial IR process has been completed, it’s important to review the whole process. This is where you will often find and discuss improvements in your security posture and IR process. Some things to consider are how long the issue existed in your network before detection as well as how long the process took from first detection to full recovery.
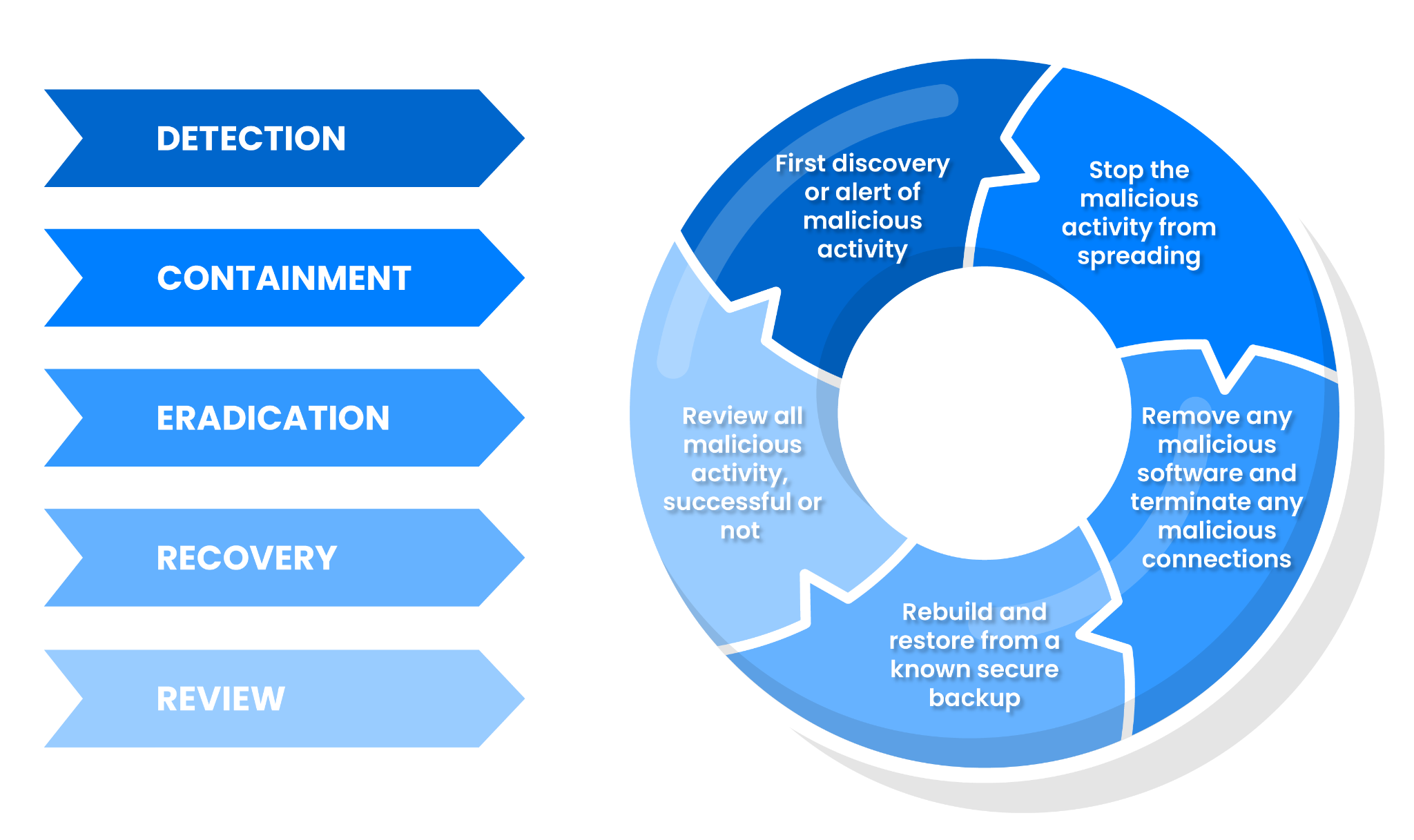
Overview of the threat management process
Steps in vulnerability management
The vulnerability management process can be broken down into the following steps:
- Identify: Similar to the IR process, the first step to vulnerability management is knowing which vulnerabilities are in your environment and on which systems.
- Assess: Once you know which vulnerabilities exist in your network, you need to determine the risk each vulnerability poses. Vulnerabilities are often reported based on severity, ranging from critical to low.
- Prioritize: After determining the risk that these vulnerabilities pose, you need to prioritize your reaction. Organizations often prioritize remediating critical vulnerabilities more quickly than low or moderate vulnerabilities, and they often further prioritize remediating vulnerabilities on critical infrastructure and customer-facing systems over other devices. Generative AI is playing a crucial role in risk scoring to prioritize vulnerabilities, and Paladin Cloud is a leading example of a Unified Vulnerability Management platform that is using generative AI to prioritize the most important risks.
- Remediate: After prioritizing, it’s time to take action. While full remediation is the goal, there may be factors that hinder your ability to accomplish this, such as budgetary constraints and technical debt through multiple outdated applications or operating systems. Some alternatives to full remediation include alternative risk mitigation and risk acceptance.
- Monitor and report: The final step of the vulnerability management process involves tracking your progress. You’ll want to take note of how quickly your organization responds to vulnerabilities, how many new vulnerabilities are identified over weeks and months, and whether any vulnerabilities are being reidentified after having been remediated.
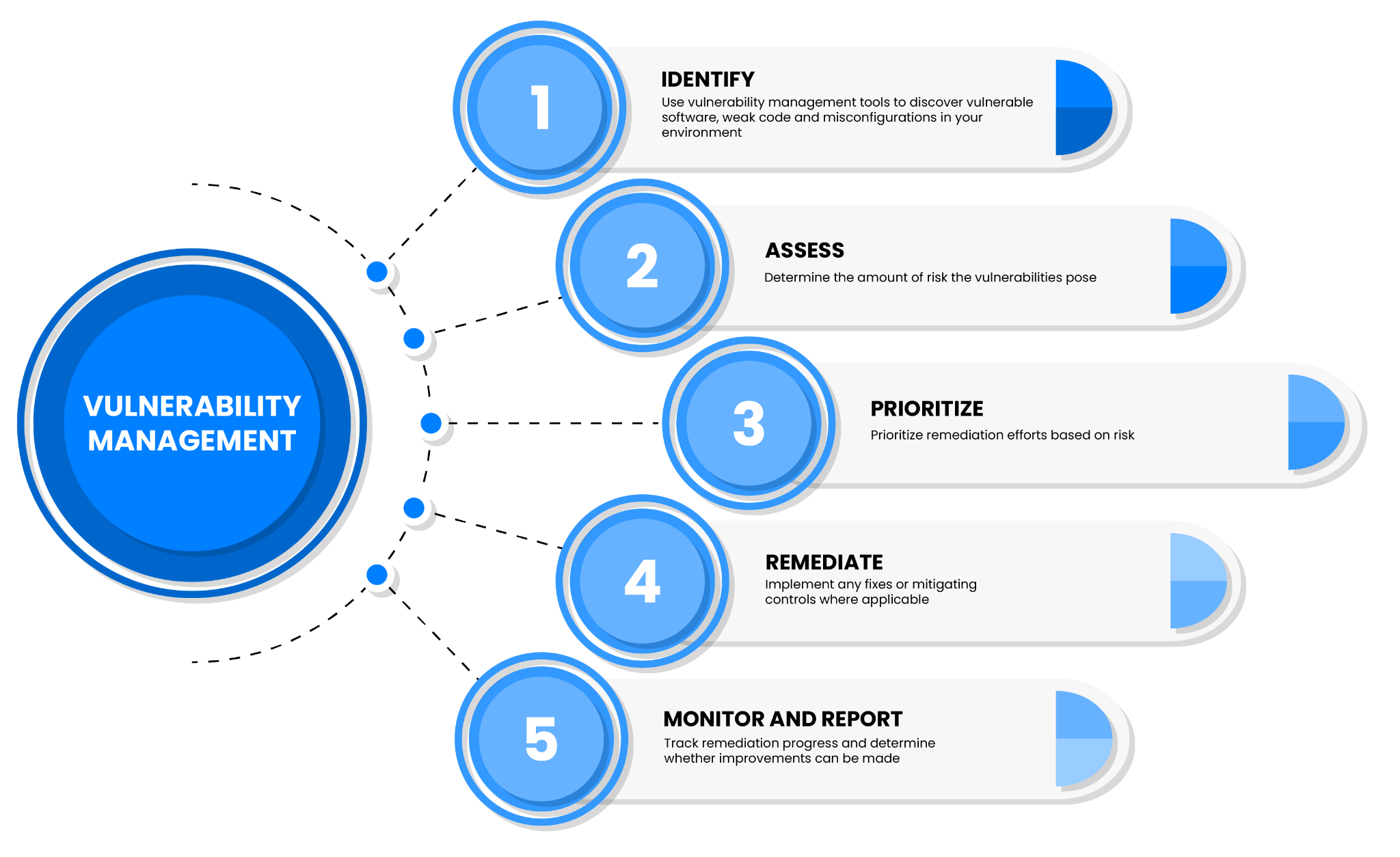
Overview of the vulnerability management process
Frameworks for threat and vulnerability management
There are multiple frameworks and guides available to aid in your threat and vulnerability management processes:
- The National Institute of Standards and Technology (NIST) offers the Cybersecurity Framework (CSF), which guides the management of cybersecurity risk.
- The MITRE ATT&CK framework offers a list of common adversarial tactics and techniques, broken down by category, to help guide you in your efforts to improve your organization’s threat and vulnerability management process.
- When it comes to assessing risk and prioritizing remediation efforts, you may find the Common Vulnerability Scoring System (CVSS), Stakeholder Specific Vulnerability Categorization (SSVC), and Exploit Prediction Scoring System (EPSS) useful. They offer insight into which vulnerabilities pose the most risk to your environment based on capability, your network, and the likelihood of exploitation, respectively.
Threat and vulnerability management in practice
Now that we’ve elaborated a bit on the differences between threat and vulnerability management, the processes involved in each, and the frameworks available, let’s learn more about what your organization needs to be able to get started.
When starting or improving your threat and vulnerability management program, you will want to consider what tools might make the process more efficient and what standards and policies you want your organization to adhere to. You’ll also want to consider what your organization might do if the ideal course of action is infeasible.
Asset inventory for detection and identification
The first step involves detecting and identifying an issue. Whether you’re identifying a potential threat or a vulnerability, you’ll need some form of an asset inventory to keep track of what systems are on your network.
Ideally, this asset inventory will allow for tagging, so your organization can maintain detailed information about which systems are public-facing, which assets are your “crown jewels,” and any other information that might help you assess true threat risk and prioritize response efforts. For example, your asset inventory tagging will help you determine whether a vulnerability affects a production environment that a threat could exploit. This would have a higher risk than a vulnerability affecting a development environment that processes test data.
A Data Security Posture Management (DSPM) tool can be vital to helping your organization better understand which applications and systems are using your data, how they’re using your data, and which users have access. DSPM differs slightly from Data Loss Prevention (DLP) tools in that it safeguards data by identifying and encrypting both at rest and in transit, where DLP’s primary goal is to restrict movement of sensitive data.
Threat hunting
You must decide how proactive your organization will be with threat management. You can conduct threat-hunting activities, which involve looking through logs for suspicious activity that may not have been suspicious enough to alert your SOC. Threat-hunting usually searches for specific indicators of compromise (IOCs) based on previous internal knowledge or through recent threat intelligence.
Vulnerability remediation strategy
With vulnerability management, your proactive activities include regular patching cycles. Your organization must decide whether to conduct patching at regularly scheduled intervals or only patch as findings are reported. If you decide to patch periodically, establishing a schedule benefits all stakeholders involved. It lets your IT team, security team, and application owners know when to expect to take action, and it enables executives to know when to expect vulnerabilities to be remediated.
Zero-day and critical vulnerabilities often require more immediate action than your prescribed patching cycle, so consider your organization’s reaction plan for unplanned patches. Document formal policies and standards detailing what is acceptable to your organization. These policies and standards should address acceptable remediation timelines for the severity levels your vulnerability tools will report and how many versions behind the current version that you will allow different software and operating systems to be.
There may be vulnerabilities you cannot remediate within your stated timelines or at all for the foreseeable future. Your organization needs to determine its risk tolerance and a formal process through which it will allow specific vulnerabilities to remain on the network due to remediation constraints. For example, if your environment is running end-of-life (EOL) servers and an SSH vulnerability is found on those EOL servers, the vendor may not release an update. This means your only options are to either upgrade your servers or accept the risk associated with the SSH vulnerability. Your organization’s risk tolerance will determine whether you decide to upgrade servers more quickly than you may have already been planning or stay the course and accept the risk.
The key to effective and efficient vulnerability management is prioritization. Your organization will only have so many engineering hours to spend on identifying, testing, and remediating vulnerabilities. Determining which vulnerabilities are most exploitable and would cause the most harm is paramount to protecting your organization as efficiently as possible.
Configuration management
A primary consideration that applies to both your threat and vulnerability management capabilities is your network’s architecture. Be sure to maintain an accurate configuration management database (CMDB) to track information such as asset types, version information, software dependencies, and license information. CMDB differs from maintaining an asset inventory: An asset inventory tells you what you have within your cloud environment, whereas the CMDB tells you how assets are configured and the impact of changes to any configuration. A DSPM tool will also help your team identify and track a lot of valuable information such as where your sensitive data rests within the environment and who has access.
Many organizations are moving toward a zero-trust architecture. Zero-trust reduces a threat’s ability to pivot laterally within your network through various security features such as network segmentation, granular access controls, and strong authentication every step of the way.
Best practices for threat and vulnerability management
Starting or improving your organization’s threat and vulnerability management program can seem overwhelming. Let’s discuss a few best practices to help you focus on key concerns.
Perform asset discovery
Even if you think you have an accurate understanding of your network, an up-to-date asset inventory will help you discover potential vulnerabilities that could be exploited. Understanding your attack surface is critical to successful vulnerability management.
Regarding threat management, this is an excellent time to confirm which teams or departments are responsible for which assets and revisit any service-level agreements (SLA) you may have with third-party vendors. Confirm that assets are adequately tagged by attributes such as their location on the network and the type of data they process or store. Doing this will help prioritize response efforts later and provide context to threats.
Use behavioral analytics to identify threats
User entity behavior analytics (UEBA) gives your organization an advantage when detecting anomalous behaviors. UEBA results in faster detection than traditional alerting methods by linking activity to user accounts rather than attributes like hostnames or IP addresses. User entity behavior analytics ties into automation, highlighting the importance of implementing at least some level of automation in your environment.
Consider the role of automation
Your organization must decide what balance of manual and automated response is appropriate, broken down by response efforts. Establishing alert criteria in your SIEM will help automatically raise alerts when specific conditions are met, saving your analysts the headache of monitoring every failed login attempt or dropped connection. This will help identify the most critical threats.
In terms of vulnerabilities, the key is finding a balance. Fully automated vulnerability patching exposes your organization to the risk of a software upgrade that may not be compatible with some of your environment, causing outages and other errors. Vulnerability patching often requires some planning to ensure backward compatibility and interoperability. Patching also requires planning for reboots and other temporary disruptions.
Your organization must discuss which systems can and can’t risk specific automated tasks. You may find that automatically upgrading browsers on user workstations is not an issue, but automatically upgrading Java on production servers would cause serious harm. You also don’t want automated vulnerability remediation to occur during some of your busiest times or during times when teams may not be immediately available to troubleshoot issues that may arise.
Look at unified vulnerability management
Viewing data from multiple tools can be overwhelming. Instead of trying to replace your preferred security tools a Unified Vulnerability Management platform can provide concise, actionable data from your existing security tools via a streamlined view. Paladin Cloud is a leading example of a Unified Vulnerability Management platform providing pre-built plugins that help teams connect their existing security tools effortlessly. This functionality eliminates the need for teams to build complex API integrations.
In addition to centralizing alerts, Unified Vulnerability Management platforms can correlate information across tools to provide enhanced insights. Paladin Cloud’s generative AI risk scores alerts and assets based on the contexual findings across security tools. By unifying your vulnerability management, you can view your overall security posture based on various risk scores and vulnerability metrics.
Always look ahead
Cybersecurity is an ever-evolving industry. Attackers are constantly becoming smarter and more capable while organizations work to get ahead of emerging threats. For example, as quantum computing becomes more advanced and accessible, attacks will happen with increasing frequency and intensity. Your organization should start looking at security measures and tools you can implement to increase resistance to the potential onslaught of attacks quantum computing will bring.
Last thoughts on threat and vulnerability management
Threat and vulnerability management are the cornerstone of an effective cybersecurity program. Although the two differ slightly in terms of day-to-day activities, both aim to secure your network through continuous monitoring and risk remediation. Regardless of your organization’s current threat and vulnerability management capabilities, consider conducting a fresh asset discovery process to understand what’s in your environment. Asset discovery is a great way to assess whether any devices were added without working through your organization’s change management process, which is a risk in itself. It also lets you reevaluate which assets are more likely to be targeted for attacks. After asset discovery occurs, consider tagging assets within your various tools to streamline future threat and vulnerability management efforts.
When selecting which tools will best meet your needs, consider which features are essential to your organization, how easily one tool will integrate with others, and how much impact each tool will have on your CPU and network. Finally, determine whether these tools will allow you to balance manual and automated work. The cybersecurity industry offers many tools to identify and act on threats and vulnerabilities, which can often be overwhelming and leave you with analysis paralysis. Be mindful of how invested in a single ecosystem your organization becomes.
While using a single solution or provider for most of your threat and vulnerability management tools may make interoperability easier, it may make leaving more difficult if you need to evaluate alternatives in the future due to factors like budget or functionality. Paladin Cloud can help your organization consolidate data from all your tools into a single viewpoint and then use generative AI to assess the true risk each vulnerability poses to your environment, helping your team prioritize and take action faster.