Cybersecurity risk assessment tools that provide feedback on an organization’s cyber security posture, risk, and exposure are essential in any security team’s arsenal. When these tools are used effectively with frameworks such as the National Institute of Standards and Technology’s Cybersecurity Framework, an organization can be sure they have a firm grasp of its cybersecurity posture.
To effectively implement cybersecurity risk assessment tools, organizations must understand the different categories of tools, their use cases, and the key business outcomes these tools generate. Security is best approached proactively and must be implemented across various categories since your cybersecurity defenses are only as strong as its weakest link.
This article will explore six categories of cybersecurity risk assessment tools in detail, including required features, real-world examples of tools in each category, and a solution for centralizing and prioritizing insights from multiple tools in a single platform.
Summary of key cybersecurity risk assessment tool concepts
The table below provides a list and a quick overview of each tool category that will be discussed in this article. Remember that, although some categories might be more applicable to your organization than others, the constant change in any organization, its cloud infrastructure, and the cybersecurity landscape requires that all of these categories and the various guidelines and best practices provided by the frameworks above are reviewed regularly.
| Category | Description |
|---|---|
| Application security scanners | Application security scanners do static checks against applications to identify vulnerabilities and risks introduced by changes to the application. Using code analysis and dependency checks, SAST tools generally identify issues before the application is deployed. After deployment, Dynamic application security testing (DAST) tools are used to assess the running application. |
| Vulnerability scanners | Vulnerability scanners can scan multiple types of cloud infrastructure, across multiple providers, for known vulnerabilities and exploits. They go beyond the functionality of traditional infrastructure scanners in that they understand virtual and cloud-based architectures. |
| Container security scanners | Containerization has created a whole new way to run and manage infrastructure. It’s also introduced its own set of unique vulnerabilities and security issues. Container security scanners assist in identifying security issues in virtualized containers and images. |
| Cloud provider tools | The big cloud providers, like AWS and Azure, provide you with tools to assess the security posture of your cloud infrastructure. Since these are vendor-specific tools, they can provide unique insights into your cloud architecture for that specific vendor but must be integrated with the rest of your assessment tools. |
| CSPM | Cloud security posture management tools give an organization a holistic view of the state and scope of its cybersecurity readiness within the cloud. CSPM tools automatically and continuously check for misconfigured cloud infrastructure assets and provide remediation recommondations. |
| DSPM | Data security posture management tools give an organization a holistic view of its data security posture. These tools track and manage your data-related cybersecurity risks and actions. |
Understanding the business value of cybersecurity risk assessments
Cybersecurity risk assessments enable effective prioritization of resources and intelligent risk management. There is an almost endless list of security mitigations and hardening activities an organization can apply to prevent a cyber attack against its assets. Realistically, though, no organization has the funds or the time to apply every action, so a cybersecurity risk assessment is used to determine where the organization is most at risk.
Organizations can use frameworks such as the NIST Cybersecurity Framework and ISO27001 to structure the assessments and prioritize actions to manage risk appropriately. The only thing worse than doing no assessments and remediations is doing it badly. The various frameworks give guidance on how to do it properly.
In a world where many organizations choose to effectively outsource their infrastructure through cloud providers, continuously assessing the cybersecurity risk is a must. Cloud providers constantly update their services. Even when these updates are communicated to the customer, it’s easy to miss or incorrectly assess the impact of the change on the organization’s cybersecurity posture. Continuous assessments ensure no new vulnerabilities are exposed due to changes made outside of the organization’s control.
Six cybersecurity risk assessment tool categories
The sections below thoroughly explore the six cybersecurity risk assessment tool categories. For each category, we provide a summary, a list of required features and functionality, and popular example tools.
Application security scanners
Application Security Scanners find design and implementation vulnerabilities in various types of applications. Attackers can use these vulnerabilities to compromise the application or its underlying infrastructure. These scans can be performed statically (SAST) by scanning changes to the application code and associated libraries for common vulnerabilities. There are also dynamic application security testing (DAST) tools that assess the application from the outside by probing the user interface and public APIs for vulnerabilities.
Required features and functionality
- Identification of possible vulnerabilities introduced by
- Bad coding practices, such as duplicating code or overly complex functions
- The use of outdated or vulnerable libraries
- The hardcoding of credentials or endpoints
- Integration with CI/CD tools to provide continuous feedback on changes made to the application
- Integration with IDE’s to provide real-time feedback to developers to reduce the turnaround time on security feedback
Example tools
Snyk and Veracode provide security scans and feedback on applications, written in various languages using various frameworks, and the libraries and third-party code they reference. Integrations into CI/CD tools such as Github and integrations with various IDEs are also available. For dynamic scanning, you can look at tools like Contrast Security and Checkmarx, and if your systems are API-heavy, consider a product like Cequence.

The Contrast Security Dashboard shows various security metrics for an application. (Source)
Vulnerability scanners
The breadth of features provided by cloud infrastructure providers and the ease of access to these features make a cloud environment a potentially high-risk environment. Features might provide functionality but can create security holes that the untrained administrator might not recognize. As a result, someone may inadvertently create a gaping security hole with the click of a button. Cloud infrastructure scanners are built to quickly and accurately detect these cybersecurity issues.
Required features and functionality
- Integration into deployment and DevOps toolsets to allow continuous feedback as part of CI/CD pipelines
- Ability to scan across various cloud providers so that an organization isn’t locked into a specific provider.
- Real-time reporting on vulnerabilities and issues for specific assets to ensure rapid issue detection and remediation.
- Automated or guided discovery of cloud assets to reduce manual work and improve coverage.
Example tools
Qualys and Tenable provide various tools for an organization to perform vulnerability scans of its cloud infrastructure. They cover the major cloud providers and provide multiple automations and integrations to streamline their use and feedback. For example, these tools can scan AWS EC2 for known vulnerabilities in the operating system, running services and open ports.

The Qualys dashboard shows discovered assets across a company’s infrastructure. (Source)
Container security scanners
Containers and container orchestration tools like Kubernetes are fundamental to modern software infrastructure. This architecture brings its own set of security challenges and mitigation opportunities. Container and cluster security scanners allow organizations to determine and mitigate the risks introduced by these technologies.
Required features and functionality
- Integration with DevOps and security tools to provide continuous and immediate feedback to operators and developers.
- The identification of vulnerabilities and risks on base images as well as custom-built images
- Detection of malware, embedded secrets, and security configuration issues in build images to improve security posture.
Example tools
Depending on the profile and systems deployed within an organization, it can look at Container Security Scanners like Redhat ACS that focus on security for Kubernetes, or cloud-native application protection platforms like Aqua and Sysdig.
Cloud provider specific tools
Public cloud providers provide basic tools tailored to their specific architectures and toolsets to enable their users to effectively fulfill their share of the shared responsibility model. Various features and functions discussed in this article are covered by the cloud providers themselves. Features & functionality of example tools
- AWS Detective – Use Machine Learning and other advanced analytics techniques to investigate and triage security related data within AWS.
- Azure Network Watcher – Monitor your virtual networks on Azure to diagnose and identify security vulnerabilities and issues.
- GCP Cloud Asset Inventory – Gain visibility into the assets in use in your Google cloud environment.
CSPM
Security posture management is an important topic in any cybersecurity discussion. When deploying systems on cloud-provided infrastructure, a cloud-focused SPM — known as cloud security posture management (CSPM) — must be available.
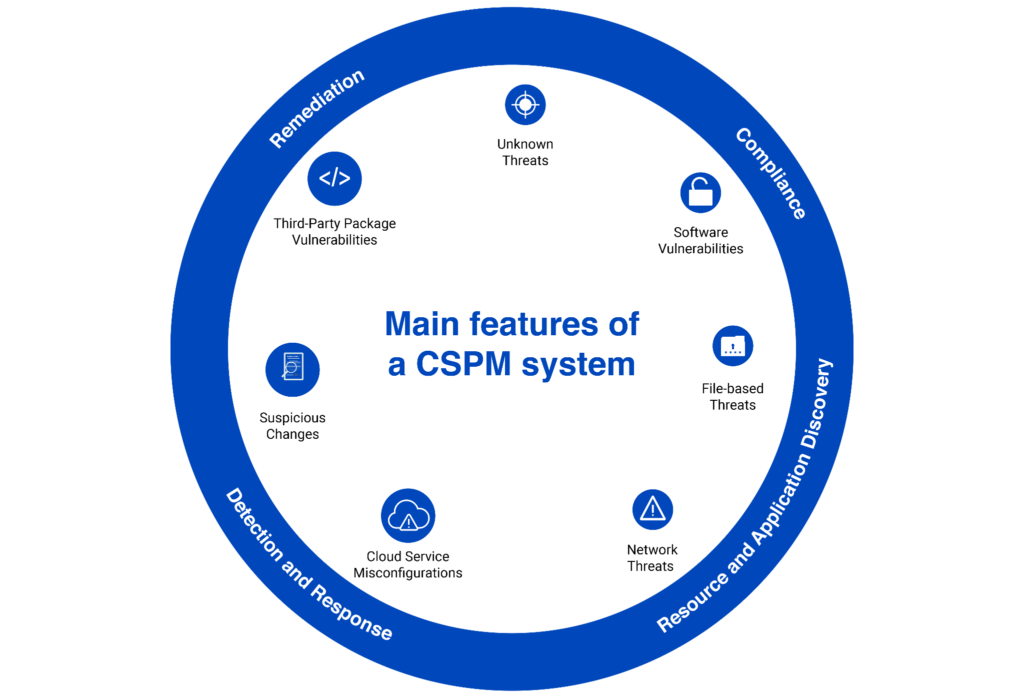
The main features required from a CSPM system. (Source)
Required features and functionality
- Continuous discovery and identification of resources and their associated risks.
- The early detection of threats and misconfigurations on the identified resources.
- Effective and efficient remediation of identified threats.
- Infrastructure compliance monitoring for internal and external policies. Look for tools that include CIS Benchmarks. CIS Benchmarks provides security configuration recommendations developed with the help of security professionals.
Example tools
AWS Security Hub and GCP Security Command Center provide basic CSPM features specific to the respective cloud providers. Paladin Cloud provides multi-cloud security (CSPM) as an optional module within its AI-powered prioritization product.
DSPM
DSPM focuses on the data security aspects of an organization’s security posture management.
Required features and functionality
-
- Data discovery, classification, and access analysis to enhance visibility
- Risk assessment, including static risk analysis.
- Implementation of data security controls to reduce data risk
- Monitoring and auditing of data access, activity, and exposure to improve compliance and response times.
Example tools
BigID provides DSPM capabilities and a range of other data related security tools. Cyera covers the major cloud providers and various popular platforms.
Unified Vulnerability Management
Within your organization, you may already have implemented best-in-class security tools to monitor your cloud environments, like vulnerability scanners, CSPM, DSPM, and application code scanners. Unfortunately, these tools may be being used in isolation, where prioritizing and correlating results from these tools is a manually intensive activity.
Duplicate, redundant, and out-of-context alert notifications lead to alert fatigue within security operation teams, and they can miss critical issues. To address these challenges, organizations have been taking a holistic approach to vulnerability management that includes unifying alerts across best-in-class tools. Risk based vulnerability management allows enterprises to leverage risk scores to aggregate and correlate risks across various tools to identify the most critical issues to remediate.
Required features and functionality
The challenge is in continuously identifying and prioritizing the most important risks to drive remediation of these issues, including:
- Differentiating between vulnerability vs. exploitability of a risk
- Collating results from various tools and processes
- Understanding the real risk of a threat to an organization
Example tools
Tools like Paladin Cloud can significantly reduce the burden of manually reviewing individual alerts from various tools, while increasing the effectiveness and turnaround time for security teams.. Furthermore, the latest security tools aggregate findings from different security tools and use generative AI to apply a risk score and prioritize findings. Critical business context is added by correlating these findings across the different tools. An example of context-based prioritization is correlating the findings of a misconfigured cloud storage account with public access enabled (from your CSPM) and known to contain sensitive data (from your DSPM).
Last thoughts on cybersecurity risk assessment tools
The range of cybersecurity risk assessment tools available to cloud administrators and security specialists is daunting. The sourcing and analysis of these tools can easily overwhelm the boldest of security administrators. And that’s only the beginning. You still need to implement the tools and go into the long-term cycle of assessing and remediating the outcomes of the various assessments.
Although tools are available to perform cybersecurity risk assessments, they still involve a lot of manual effort. The last thing you want is for a known but forgotten or deprioritized vulnerability to be the cause of a cyber attack. Organizations can reduce risk and increase infrastructure resilience by taking a strategic approach to risk management that considers all these variables holistically.
The latest security tools are using generative AI models that can correlate findings to prioritize the top security risks affecting your cloud environments. Paladin Cloud is a leading example of a Unified Vulnerability Management platform that is using generative AI to prioritize security alerts.