Unified vulnerability management (UVM) enables organizations to create a data fabric by combining their security data into a single, cohesive holistic view. Advanced UVMs often include other vulnerability management-influencing information, such as organizational policy directives, legal requirements, and external data feeds, such as threat intelligence.
The resulting integrated view allows organizations to enhance the effectiveness and efficiency of their vulnerability management. Many organizations find a UVM helps improve their security posture by enabling risk-based prioritization decisions while reducing alert fatigue and tool sprawl.
This article explains the need for unified vulnerability management (UVM), how UVMs work, six best practices all UVMs need, and four benefits a UVM provides for an organization’s vulnerability management.
Summary of key unified vulnerability management benefits for organizations
The table below summarizes the four key benefits of unified vulnerability management that this article will explore in more detail.
| Benefit | Description |
|---|---|
| Consistency | UVM normalizes data and analyzes existing security tools in a consistent, unified format. This format provides clear insights, reduces alert fatigue, and reduces tool sprawl. |
| Risk-based prioritization | UVMs provide risk-based prioritization to vulnerability events. By combining organizational policy, previous lessons learned, external data sources (such as threat intelligence), and security findings, UVMs ensure all factors influencing a vulnerability are considered. |
| Continuous deployment | UVMs reduce an organization’s vulnerability window by being constantly on and working. New findings, policies, and alerts are incorporated immediately into the vulnerability management process. |
| Corporate memory | UVMs continuously capture and analyze an organization’s knowledge base. As lessons are captured and policies updated, UVMs immediately incorporate them into vulnerability management. |
The need for unified vulnerability management
Organizations face a four-sided challenge when managing vulnerabilities across multiple domains, including application, cloud, and data security. Let’s take a look at each of these challenges.
Tool sprawl
Organizations must incorporate a myriad of cybersecurity tools to secure multiple environments. Even though each tool may be the best-of-breed in a specific area of expertise, each tool typically uses a custom data format, often incompatible with other tools. The resulting tool sprawl means organizations must either support multiple overlapping tools and their associated training/integration requirements or choose a less effective but more compatible option.
Asset discovery
Effective vulnerability management requires effective cyber asset management and a complete understanding of an environment and the technical and contextual changes that impact it. However, capturing and linking this information can be a significant technical challenge in and of itself. As a result, many organizations defer to methods such as network scanning, human assessment, or extra tools to attempt to understand their network. Each of these methods creates additional risk or resource usage to the organization.
Organizations using multi-cloud or on-premises environments can find asset discovery even more challenging. Not only is the scale of the monitoring often increased, but organizations can also find themselves tracking and contextualizing ephemeral workloads such as Kubernetes clusters. Along with this, each cloud vendor often has different ways of tracking and monitoring the workloads the organization is using.
Systematic vulnerability reduction
Organizations must balance the need to respond to existing and emerging vulnerabilities while continuing to reduce the environment’s overall risk profile. While the now vs. future tension is typical in business, tool sprawl makes this balance significantly more complex. As a result, organizations expend extensive resources to understand the current state before improving it.
Integration of organizational imperatives
Vulnerability management does not operate in isolation. Various policies, legislative requirements, external data feeds, and past lessons learned inform remediation activities; however, each element burdens the existing system. As a result, organizations can either not prioritize vulnerability activity effectively or expend precious resources considering all these factors before beginning the remediation process. Regardless of the choice, organizations need help effectively prioritizing remediation efforts based on risk.
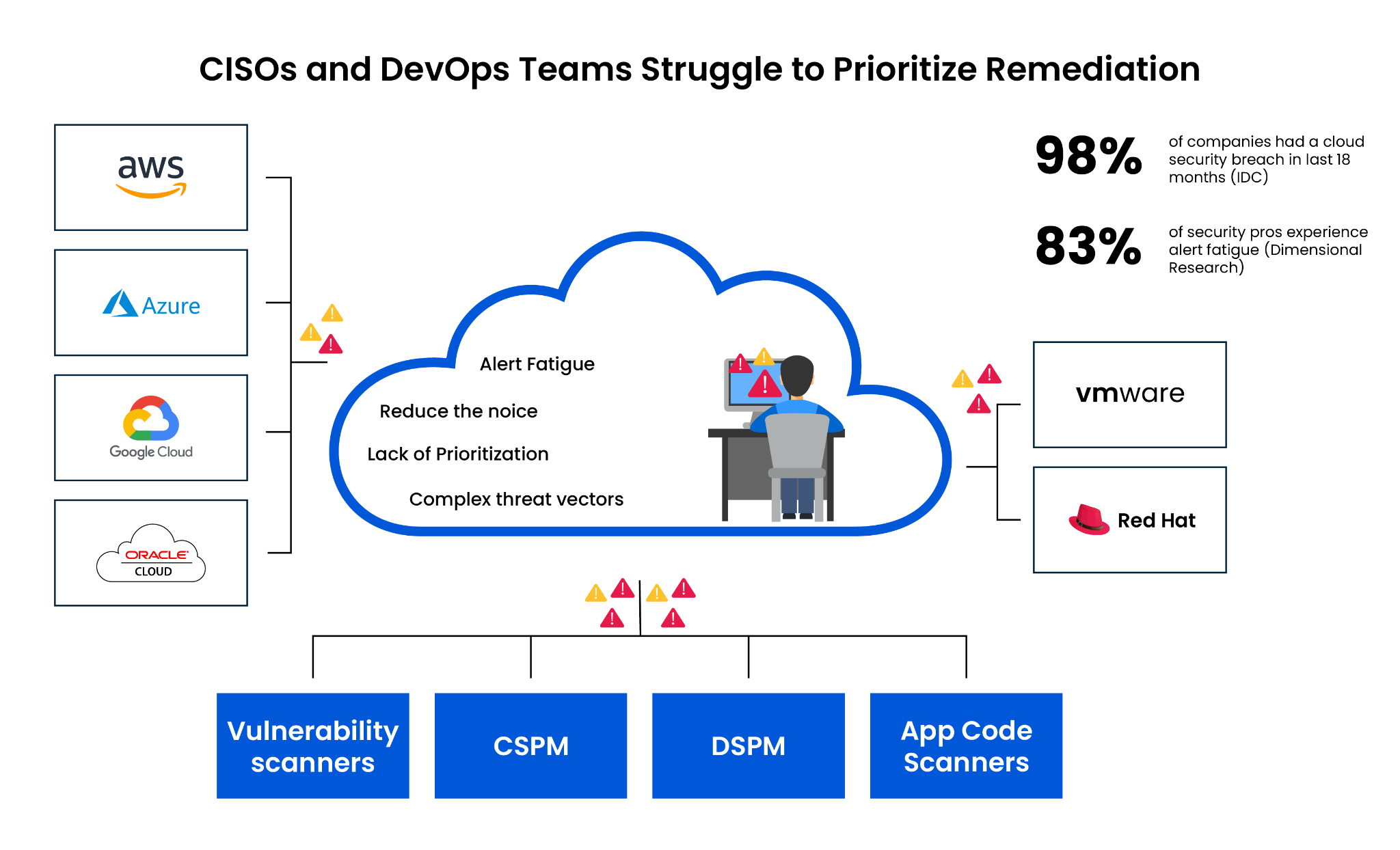
CISOs and DevOps teams struggle to prioritize remediation efforts from ‘code to cloud’ across numerous tools spanning application, cloud and data security.
When unresolved, this four-sided challenge results in one or more negative outcomes:
- Resource exhaustion – Organizations find themselves exhausting computing resources (or budget) on the collection and analysis of data, with each new tool further adding to this burden.
- Alert fatigue – As people and systems repetitively analyze incoming alerts and data, often duplicated across multiple tools, the ability to apply the required focus and attention decreases. As a result, essential events can ‘fall through the cracks’, especially when security teams become overwhelmed by the volume of alerts. Excessive alerts, noise, and false positives cause security teams to struggle to prioritize and respond in a meaningful and timely manner.
- Incomplete understanding of the environment – The multiple incongruent data formats mean organizations often find they ‘do not fully understand the environment.’ For example, organizations may find they do not understand how their critical business processes interact with the enterprise. Lacking this contextual, business-specific information, the organization may disregard a security alert related to excessive data extraction from this area – only to find that they have lost their ‘crown jewels’.
- Crisis-driven management – Organizations can find themselves so busy dealing with the latest crisis that they cannot systematically and intelligently reduce the overall vulnerability of the environment. In effect, they become stuck in a constant cycle of crisis-driven resource allocation.
How unified vulnerability management works
UVM systems operate on a four-stage, continuously repeating cycle to deliver their core outcomes. The four-stage cycle is below:
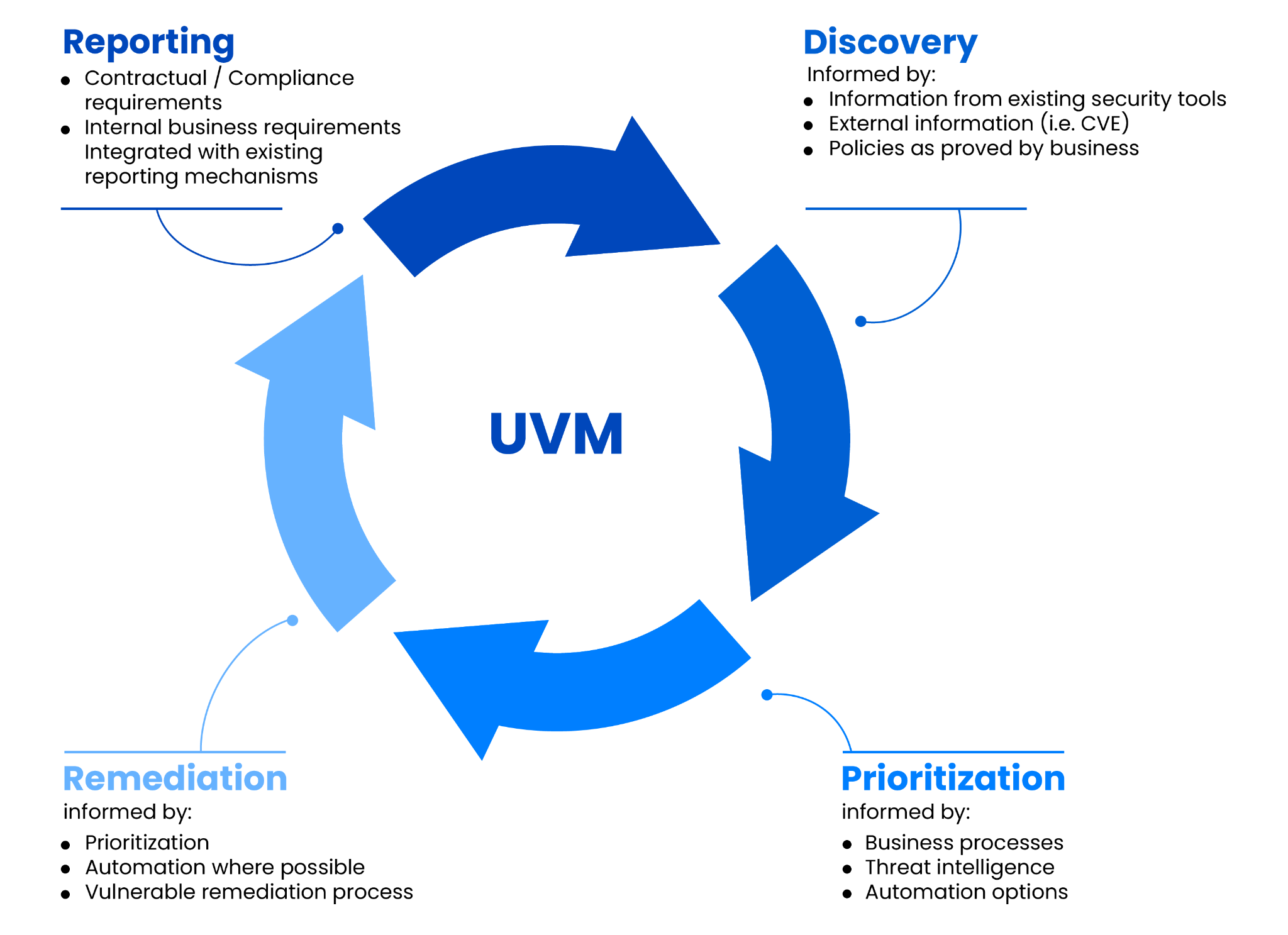
The four-stage UVM cycle of Discovery, Prioritization, Remediation, and Reporting
1. Discovery
Constant assessment of incoming data. This might include information from existing tools, business processes, and external vulnerability information such as new Common Vulnerabilities and Exposures (CVE).
2. Prioritization
Once a vulnerability is discovered, the UVM applies contextual information to determine remediation priority. This might include specific processes based on legislated remediation timeframes or other priorities specified in organizational policy.
Generative AI plays a crucial role in risk scoring to prioritize vulnerabilities, and Paladin Cloud is a leading example of a Unified Vulnerability Management platform that uses generative AI to prioritize the most important risks.
3. Remediation
Once a prioritization is assigned, vulnerabilities move through the vulnerability mitigation/remediation process. This includes any considerations for automated actions vs. human-driven processes and the inclusion of the UVM to confirm effective remediation. This stage may also include integration with any required ticketing systems. Workflow automation is critical at this stage to ensure that tickets are automatically distributed to the relevant teams to begin the remediation process.
4. Reporting
As vulnerabilities are remediated, the UVM generates the reporting required to meet business and compliance needs. This stage may include integration with any required reporting systems.
Four benefits a UVM provides to an organization’s vulnerability management
A UVM system enables organizations to improve their vulnerability management outcomes by delivering four core benefits.
Consistency
UVM normalizes the data and analysis from each tool to create a consistent and cohesive picture for an organization. There are several benefits from this approach:
- Best-of-breed tools. Organizations can select the best tool to address a specific need while relying on the UVM to integrate the tool output into a unified format.
- Reduced tool sprawl. Organizations can identify and address specific environmental coverage gaps. Instead of supporting multiple tools with overlapping functionality, organizations can focus on solving identified coverage gaps. This reduces the overall tool sprawl (and associated costs) without negatively impacting the organizations’ cybersecurity posture.
- Less alert fatigue. Providing a standardized data format improves the quality and decreases the quantity of alerts (all other things being equal). When combined with risk-based prioritization, this reduction reduces alert overload, which reduces alert fatigue.
Risk-based prioritization
Risk-based prioritization of vulnerabilities combines organizational policy, external drivers (such as threat intelligence), and the environmental data generated by cybersecurity tools. UVMs incorporate these data sources when prioritizing vulnerability events, with advanced UVMs, such as Paladin Cloud using generative AI to risk score individual findings and to derive context-based asset scores.. The resulting risk-based prioritization more effectively allocates scarce resources to the most important vulnerability events.
Continuous deployment
UVMs use continuous deployment to be always on, constantly analyzing, and consistently available. This contrasts with many approaches, where a network gets scanned regularly, a report is compiled, and remediation begins. As a result, an effective UVM significantly reduces the time from vulnerability discovery/creation to mitigation/remediation.
Corporate memory
UVMs continuously incorporate organizational data into the vulnerability management lifecycle, creating a continuous learning system. In effect, a UVM can act as a corporate memory system, reducing the reliance on people to remember the lessons learned.
The UVM halo effect
On top of the individual outcomes, combining the four outcomes creates a powerful halo effect for UVMs.
For instance, consider implementing vulnerability remediation automation. An engineering or vulnerability team can easily and rapidly build an automation script using the normalized data. The automation can be immediately deployed using UVM’s continuous deployment characteristics (after appropriate testing). Immediately after automation deployment, UVM updates the vulnerability event prioritization approach to leverage the automation while simultaneously capturing this in the organizational memory.
Each stage benefits the organization; however, the overall halo effect further bolsters an organization’s security posture.
Six Unified Vulnerability Management Best Practices
Simply having a UVM isn’t enough. Properly leveraging the system to maximize security benefits is essential. These six unified vulnerability management practices will help you do just that.
Before we jump into the details, a summary of these six UVM best practices and their benefits is shown in the table below.
| Best Practice | Benefit |
|---|---|
| Start with asset discovery and management | All assets in the business are accounted for. This includes capturing the addition and removal of assets and the associated business process that caused it. |
| Conduct continuous vulnerability assessment | Monitor incoming data sources constantly for the emergence of vulnerability events. Some examples are alerts, CVEs, and incidents. |
| Prioritize based on risk | Dynamically assign a prioritization to a vulnerability event based on the event and the context supplied by organizational policy and data feeds |
| Remediate and mitigate strategically | Assign and monitor mitigation/remediation activity, including reprioritizing as required. |
| Leverage reports to improve security posture and compliance | Provide measurement and insight into vulnerability management within the organization. |
| Understand the role of AI | Undertake complex analysis of vulnerability management within the organization to identify hidden trends and analyze unstructured data |
Start with asset discovery and management
Unified vulnerability management starts with an accurate and up-to-date understanding of an organization’s asset inventory. Note that this stage should also include data normalization as required.
Some examples of the types of data are:
- The current configuration of all of an organization’s assets
- Association of a configuration change to an organizational event (i.e. an update occurring)
- Identification of the addition or removal of assets from the inventory
- Association of identification and removal events to organizational events (i.e. a new employee starting, new asset assigned)
- Capture of data streaming from existing assets, tools, and security tools (i.e. logs from events, technical support tools, cybersecurity tools)
Conduct continuous vulnerability assessment
The UVM continuously monitors internal and external data sources for vulnerabilities.
Typical data sources include:
- Common Vulnerabilities and Exposures (CVE) feeds
- Threat Intelligence
- Incident Response systems (for when an incident is determined to be due to a vulnerability)
- Existing tools from asset discovery and management
Prioritize based on risk
As vulnerability events occur, the UVM dynamically prioritizes mitigation and remediation efforts based on various risk factors.
Typical inputs include:
- Legislative requirements
- Organizational policy (policy-as-code)
- Threat intelligence feeds
- Existing events
- Existing automation approaches
- Advanced analysis using generative AI
Remediate and mitigate strategically
As vulnerability events occur, UVMs assign and track mitigation/remediation activity.
This includes aspects such as:
- Confirming successful remediation, especially if remediation activity was performed using automation
- Tracking timeframes
- Monitoring workload
- Updating prioritization if new events change existing activity
- Assigning events to appropriate teams or tools
Leverage reports to improve security posture and compliance
Throughout the vulnerability lifecycle, UVM’s provide comprehensive reporting options.
This includes measurements like:
- Time-to-remediation
- Detailed breakdowns of each stage of an organization’s vulnerability lifecycle steps (i.e. the time from identification to first action)
- Comparison of activity against compliance frameworks
- Identification of patterns of activity
Understand the role of AI
Advanced UVMs such as Paladin Cloud incorporate generative AI to power risk-based prioritization and remediation. UVM generative AI focuses on analyzing normalized data from diverse toolsets and integrating organizational policy and external feeds into the overall vulnerability picture.
Some applications of generative AI include:
-
- Trend analysis to identify critical, recurring areas of vulnerability
- Large Language Model (LLM)-based AI that effectively analyzes complex, unstructured business processes such as previously learned lessons or policy documents.
- Analysis of previous events to learn from historical context
For example, the latest security tools aggregate findings from different security tools and use generative AI to apply a risk score and prioritize findings. Correlating these findings across the different tools adds critical business context. An example of context-based prioritization is correlating the findings of a misconfigured cloud storage account with public access enabled (from your CSPM) and known to contain sensitive data (from your DSPM).
Last thoughts on unified vulnerability management
Unified vulnerability management solutions enable organizations to improve and scale their vulnerability management capabilities.
Ultimately, UVMs strengthen an organization’s security posture. The constant normalizing and combining of data gives organizations a more insightful, digestible understanding of their vulnerability management lifecycle. Combined with the continuously deployed nature of UVMs, organizations become more effective at risk-based prioritization, more efficient in managing their environment, and reduce their vulnerability window. A UVM also helps organizations address the problems of tool sprawl and alert fatigue. By consolidating the findings from multiple security tools into a UVM, the noise can be reduced, and the top security issues prioritized. Paladin Cloud is a leading example of a Unified Vulnerability Management platform using generative AI to prioritize security alerts.