Most organizations have more logs than they can keep up with. Similarly, many organizations have many security tools and regularly adopt more, leading to tool sprawl and alert fatigue. Properly analyzing all of those alerts could be overwhelming and inefficient for any security team.
In addition to that, actual security incidents could be drowned among tons of false positive alerts. Incident management automation is using technology and automated processes to streamline and enhance the management of security incidents within an organization to help address such issues. Automation is employed to accelerate incident detection, response, and resolution, ultimately improving the efficiency and effectiveness of an organization’s security operations. Simply put, incident management automation helps teams get more signal and less noise.
This article describes each step in the incident management automation process so you can implement it in your organization and improve the company’s overall cyber security posture.
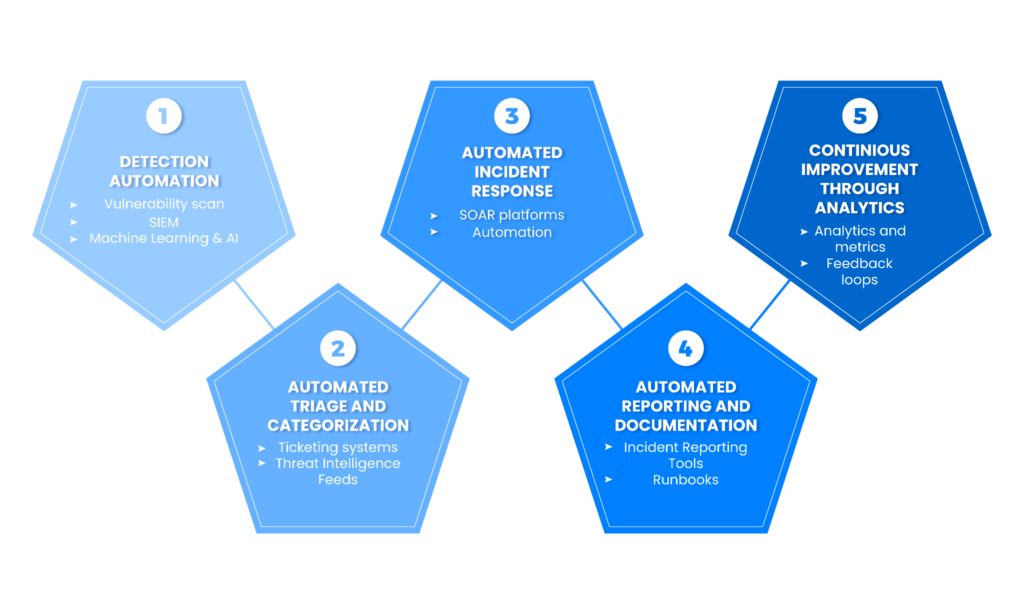
The image shows five Incident Management Automation phases covered in this article.
Summary of incident management automation phases
The table below summarizes the five incident management automation phases this article will explore in more detail.
| Phase | Description |
|---|---|
| Detection automation | Uses technologies like SIEM and AI algorithms to automatically identify and alert on potential security incidents in real-time based on predefined rules and patterns. |
| Automated triage and categorization | Employs automated ticketing systems and integrates with threat intelligence feeds to categorize incidents, assign priority levels, and streamline the initial assessment process. |
| Automated incident response | Implements orchestration and automation platforms to create workflows that automatically execute predefined response actions, such as isolating affected systems or blocking malicious activities. |
| Automated reporting and documentation | Leverages automated tools to generate comprehensive incident reports detailing the incident timeline, response actions, and lessons learned. It also integrates with documentation platforms for streamlined reporting. |
| Continuous improvement through analytics | Provides analytics and metrics on incident response performance, enabling organizations to identify areas for improvement. Implement feedback loops to adapt to the changing threat landscape and improve response effectiveness. |
Incident management automation phase 1: Detection automation
Three main steps will help you to automate your detection capabilities:
1. Implement regular vulnerability scans
Vulnerability scans play a crucial role in identifying and detecting possible security incidents even before they happen. They help to automate detection capabilities through:
- Scheduled and continuous scans: Vulnerability scanning tools automate regular scanning of networks, systems, and applications for potential vulnerabilities. These scans can be scheduled at predetermined intervals or run continuously to ensure ongoing visibility into the security posture.
- Vulnerability detection for networks, systems, and applications: Vulnerability scanners identify weaknesses in various IT environment components, including network devices, servers, and software applications. These weaknesses may include outdated software versions, misconfigurations, or known security vulnerabilities.
Paladin Cloud Unified Vulnerability Management is an excellent example of vulnerability scanner automation. It helps the company connect vulnerability scanners, CSPM, and app code scanners to correlate risks across your tools and clouds using their AI‑Powered Prioritization Engine.
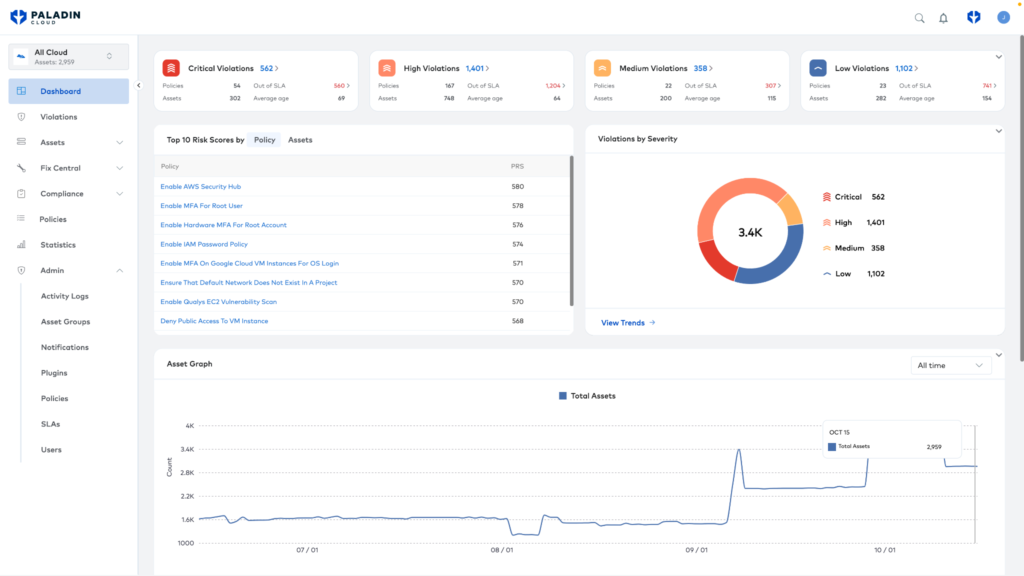
The image shows Paladin Cloud Unified Vulnerability Management console
2. Use a SIEM
SIEM solutions serve as a cornerstone in cybersecurity by providing real-time log analysis, utilizing predefined rules and patterns to identify security threats, and offering automated alerting functionalities like:
- Real-time log analysis: SIEM solutions are crucial in monitoring and analyzing log data generated by different systems and applications within an organization’s IT environment. They provide real-time visibility into security-related events, such as login attempts, access patterns, system changes, and firewall logs.
- Predefined rules and patterns: SIEM systems use predefined correlation rules and patterns to identify known security threats. Security teams can customize these rules based on the organization’s specific security policies and compliance requirements or create a new one based on the current threat landscape. When an event matches a predefined rule, the SIEM system generates alerts for further investigation.
- Automated Alerting: One of the key benefits of SIEM is its ability to detect and alert on potential security incidents automatically. Administrators can configure alerts to notify security teams in real-time when suspicious activities or patterns are identified. This timely notification is crucial for a prompt response to mitigate potential risks. Moreover, some SIEMs can respond appropriately based on predefined scenarios without any human interaction.
- Real-time metrics and dashboards: SIEM solutions often provide real-time metrics and dashboards that visually represent the security landscape. These dashboards enable security professionals to quickly assess the overall security posture, monitor ongoing incidents, and identify trends or anomalies that may require attention.
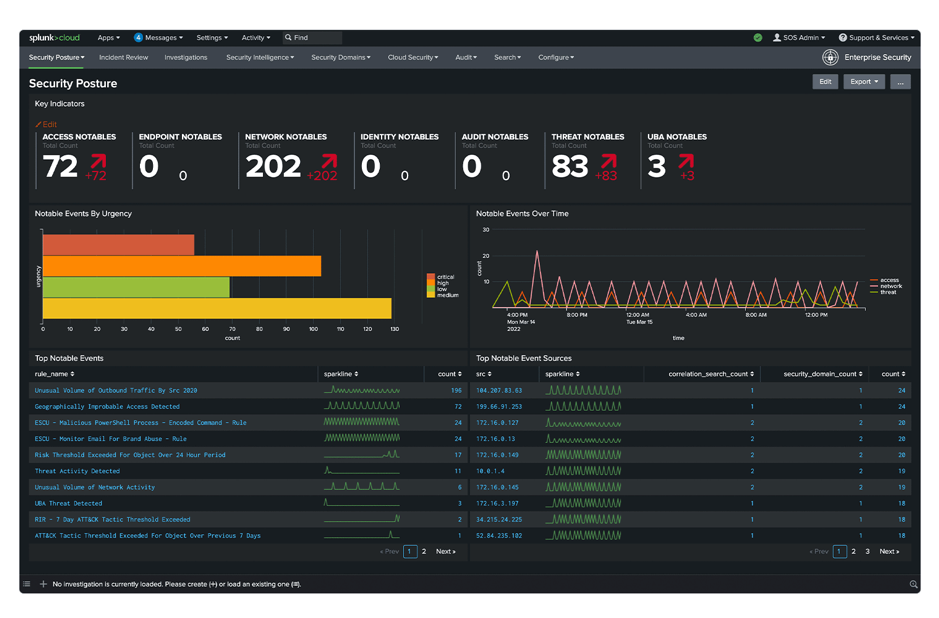
The image shows Splunk Cloud SIEM as an example
3. Leverage machine learning and AI
Continuous learning through ML and AI algorithms is a powerful asset in cybersecurity. It enables automated systems to adapt to emerging threats. These technologies excel at abnormal pattern detection within vast datasets, effectively identifying sophisticated threats that deviate from known attack signatures.
- Continuous learning: Machine learning (ML) and artificial intelligence (AI) algorithms empower automated systems to continuously learn and adapt to new threats. Unlike static rule-based systems, ML and AI can evolve by analyzing large volumes of data and recognizing patterns that may not be apparent through traditional rule sets.
- Abnormal pattern detection: ML and AI algorithms excel at detecting abnormal patterns or behaviors within the vast amount of data they analyze. This is particularly valuable in identifying sophisticated and evolving threats that may not conform to known attack signatures.
- Reducing false positives: ML and AI can contribute to reducing false positives by learning the normal behavior patterns within an organization’s network. This helps in focusing on truly anomalous activities that may indicate a security incident, improving the accuracy of threat detection.
Paladin Cloud’s AI‑Powered Prioritization Engine is an example of a solution that leverages AI to risk score and correlate findings across tools to help teams focus on the security issues that matter most.
Incident management automation phase 2: Automated triage and categorization
Incident ticketing can be automated to ensure the instant generation of tickets upon detecting security incidents. This approach makes incident reporting more efficient by guaranteeing prompt documentation of every security issue identified and ensuring uniformity in how incidents are recorded. Tickets are automatically generated and sorted into categories according to established guidelines, which might include the nature of the incident, impacted systems, and other pertinent information.
Automation
The automation process includes the prioritization of incident tickets. Through predefined criteria, the system evaluates the severity of each incident and assigns a corresponding priority level, allowing teams to concentrate on the most critical issues first. Platforms like ServiceNow, BMC Remedy, and Jira Service Management exemplify ticketing systems that facilitate such prioritization.
Integration
Integration with threat intelligence feeds enhances incident categorization by leveraging information about known threats. Threat intelligence provides up-to-date data on malicious IP addresses, domain names, malware signatures, file hashes, and other indicators of compromise. Threat intelligence feeds can enrich incident data by providing context and additional information about the nature of the threat. This enrichment aids a more comprehensive understanding of the incident and informs effective response strategies.
To connect Threat Intelligence Feeds to SIEM, we can use the TAXII Protocol. Trusted Automated eXchange of Indicator Information (TAXII) is a protocol designed for automated threat intelligence exchange. Connecting Threat Intelligence Feeds to an SIEM solution through TAXII enables real-time updates on emerging threats. With this integration, the SIEM system can dynamically adjust its rules and detection mechanisms based on the latest threat intelligence. It ensures that the organization’s security measures remain aligned with the evolving threat landscape.
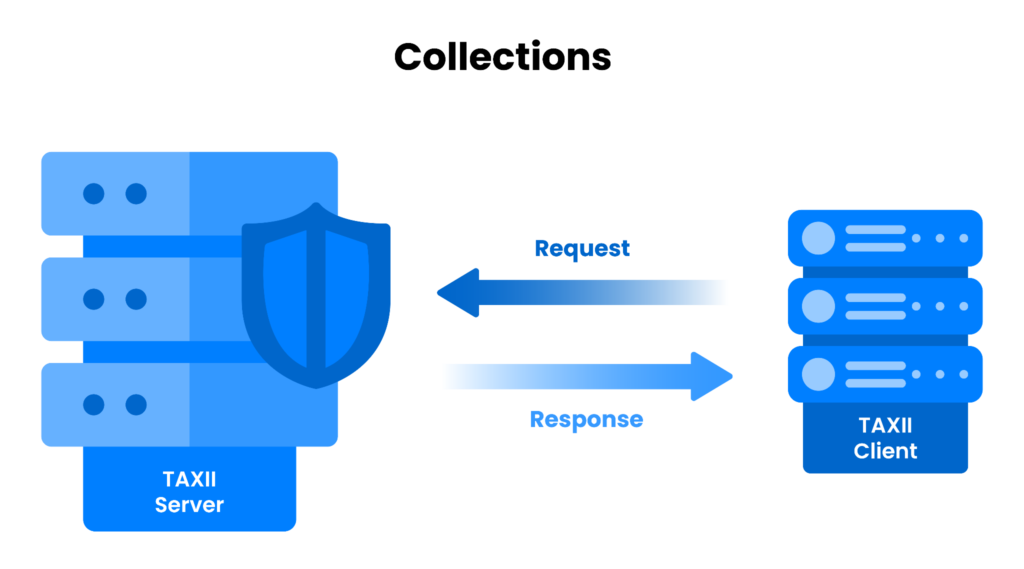
This image shows a simplified visualization of how TAXII works. (Source).
Organizations can achieve a more responsive and adaptive incident management process by combining automation in incident ticketing with integration with threat intelligence feeds. Automation reduces manual effort in incident handling, response, and analysis time, while threat intelligence integration provides the necessary context and information to make informed decisions during incident response. This synergy enhances the overall effectiveness of an organization’s cybersecurity posture.
Incident management automation phase 3: Automated incident response
Security Orchestration and Automation Response (SOAR) Platforms enable the creation of automated workflows that define and execute response actions. These workflows can include a series of predefined steps to be taken in response to specific types of incidents. Teams can automate tasks such as isolating affected systems, blocking malicious IP addresses, and deploying patches with SOAR platforms. This accelerates the incident response process, reduces manual effort, and ensures a consistent and coordinated response. SOAR platforms could also be integrated with SIEM, for example, to provide automated workflows and execute responsive actions based on incidents created by SIEM. Paladin Cloud is a great example that helps to connect and monitor multiple security tools and cloud environments to correlate findings across the stack.
Timely communication
Timely communication is critical in incident response. Automated notification systems inform stakeholders about incident status, progress, and resolution. Timely communication is essential for coordinating efforts and ensuring everyone knows the incident’s current state. Different stakeholders may require different levels of information. Notification systems can be configured to send role-based notifications, providing specific details to IT teams, management, and external parties based on their responsibilities and needs.
Automation
Automation also can be used to integrate incident response processes with communication platforms. This ensures that real-time incident information is updated on collaboration tools, messaging apps, or other communication channels. Integration with communication platforms facilitates cross-team collaboration. Security teams can collaborate with IT teams, management, and external partners seamlessly, sharing updates and coordinating response efforts effectively.
In summary, integrating SOAR, playbooks, notification systems, and communication platforms creates a well-coordinated and automated incident response framework. This framework accelerates response time and enhances incident management’s overall effectiveness by providing guidance, communication, and automation throughout the entire incident lifecycle.
Incident management automation phase 4: Automated reporting and documentation
Incident reporting tools are crucial in summarizing and documenting key aspects of a security incident. These tools generate comprehensive reports that include the incident timeline, initial detection, response actions taken, and the resolution process.
Incident reports
Incident reports provide a platform for capturing lessons learned from each incident. This includes insights into what worked well, what could be improved, and any unexpected challenges faced during the incident response process. Incident reports facilitate retrospective analysis, allowing security teams to review the entire incident lifecycle. By examining the timeline and response actions, teams can identify areas for improvement in detection, response, and recovery processes.
Runbooks
Integration with documentation platforms streamlines the process of recording and automating incident details. This ensures that incident information is consistently and systematically documented for future reference as a short checklist that analysts can follow if the same incident occurs again. Documentation platforms often serve as knowledge management systems where incident-related knowledge, insights, and best practices are stored. Integration allows incident details to be seamlessly incorporated into the organization’s broader knowledge repository and reused to make an analysis and incident response faster and more consistent.
By leveraging incident reporting tools and integrating them with documentation platforms, organizations can establish a structured approach to capturing, analyzing, and learning from security incidents. It ensures that institutional knowledge is preserved and can be shared across teams, leading to more effective incident response in the future.
Incident management automation phase 5: Continuous improvement through analytics
Automated incident management systems generate analytics and metrics that quantify various aspects of incident response performance. Metrics may include:
- Detection time
- Response time
- Resolution time
- Effectiveness of implemented security measures
Organizations can define key performance indicators to assess the efficiency and success of their incident response processes. These KPIs help measure the overall health of the cybersecurity program and identify areas that may require attention. Moreover, analytics help to adapt to the current threat landscape. Continuous monitoring and feedback loops allow organizations to adjust their automated incident response processes to the evolving threat landscape. As new threats emerge, automated systems can dynamically adapt their rules, response actions, and detection mechanisms.
Automated incident management, through continuous monitoring and feedback, allows organizations to learn from experience. Insights from past incidents guide policy, procedure, and technology implementation improvements. Over time, organizations can enhance their incident response maturity and resilience by applying lessons learned from previous incidents. This iterative improvement process strengthens the overall cybersecurity posture and prepares the organization for future challenges.
Last thoughts on incident management automation
Implementing incident management automation can significantly enhance an organization’s ability to respond to security incidents promptly and consistently, ensuring that repetitive and time-consuming tasks are handled automatically and allowing human resources to focus on more complex aspects of incident response.
Organizations can build robust and adaptive automated detection capabilities by combining the strengths of vulnerability management, SIEM solutions, and advanced technologies like ML and AI. These technologies work together to provide a comprehensive approach to identifying and responding to security incidents in a dynamic and evolving threat landscape. It also reduces response time for each incident and generally contributes to a more agile and adaptive cybersecurity posture. Stop incidents before they happen with Paladin Cloud’s Unified Vulnerability Management platform.