Alert fatigue is an increasingly prevalent issue akin to the classic tale of the boy who cried wolf. Just as the boy’s repeated false alarms led the villagers to ignore a genuine threat, cybersecurity professionals inundated with a barrage of alerts may become desensitized to warnings, potentially overlooking critical security threats. Alert fatigue arises when the sheer volume of security alerts overwhelms the organization’s capacity to respond effectively, leading to diminished vigilance against real cyber threats.
In addition to the challenges outlined, a significant driver of alert fatigue in the cybersecurity landscape is the prevalence of numerous best-of-breed security tools. While these tools excel in their specific functions, they often operate in silos, lacking the necessary context or correlation with risks identified by other tools in the security stack. This fragmentation creates an environment where alerts are generated in isolation, making it difficult for cybersecurity teams to create a coherent threat narrative.
Furthermore, the accelerated pace of digital transformation has led enterprises to rapidly adopt multi-cloud environments, introducing a new array of security tools and technologies. These include advanced vulnerability management systems, Cloud Security Posture Management (CSPM), Data Security Posture Management (DSPM), and application security scanners. Each tool contributes to the overall security posture and adds complexity to managing alerts. Integrating these diverse tools, each generating its own set of alerts, exacerbates the challenge of alert fatigue as security teams struggle to prioritize and respond to the multitude of notifications in a meaningful and timely manner.
A striking statistic from the 2022 Orca Security Report reveals that 40% of security alerts are false positives. This not only contributes to alert fatigue but also translates to approximately 20% of a security team’s time being expended on chasing these false alarms. Such a high rate of false positives not only strains resources but also risks the security posture of businesses because critical alerts might be lost in the noise.
This article sheds light on practical strategies to minimize alert fatigue, ensuring that cybersecurity teams can maintain their focus and effectiveness. While the causes and consequences of alert fatigue are likely familiar to our readers, we will touch upon them briefly, focusing primarily on actionable solutions to this pervasive challenge. By the end of this article, you should have a clearer understanding of how to tackle alert fatigue, enhancing your team’s ability to respond to genuine cybersecurity threats efficiently.
Summary of alert fatigue key concepts
This table outlines key concepts for understanding and addressing alert fatigue, providing a concise summary of each major aspect.
| Concept | Description |
|---|---|
| Causes of alert fatigue | Alert fatigue arises from an overwhelming volume of security alerts, a high incidence of duplicates and false positives, ineffective prioritization, tool complexity, limited resources, inadequate contextual information, and inconsistent alert thresholds. |
| Consequences of alert fatigue | The fallout from alert fatigue includes missed critical threats, strained resources, increased organizational risk, and a potential decline in the cybersecurity team’s effectiveness and morale. |
| Mitigating alert fatigue | To effectively reduce risks, you must use a mix of strategies, such as smart risk assessment, centralized management, context-driven prioritization, and seamless tool integration. Proactive vulnerability assessments, ongoing policy reviews, real-time insights, team empowerment, and cooperative ecosystems should support these efforts. |
Summary of strategies for mitigating alert fatigue
Here’s an overview of the specific strategies for mitigating alert fatigue that we’ll discuss in more detail later in the article.
| Strategy | Description |
|---|---|
| Intelligent risk scoring | Intelligent risk scoring leverages advanced algorithms and AI to evaluate and prioritize risks, focusing attention on the most critical threats and enhancing overall security response efficiency. |
| Centralized alert management | Centralized alert management streamlines cybersecurity efforts by aggregating diverse alerts into a unified dashboard, enabling more efficient monitoring and a quicker response to potential threats. |
| Context-driven alert prioritization | Context-driven alert prioritization involves analyzing alerts within their specific operational contexts, enabling more accurate identification of genuine threats and reducing response times to critical incidents. |
| Seamless tool integration | This integration approach focuses on harmonizing various cybersecurity tools to create a cohesive security infrastructure, reducing redundancies, and enhancing overall threat detection capabilities. |
| Proactive vulnerability assessment | Proactive vulnerability assessment entails the continuous scanning and evaluation of systems to identify and address vulnerabilities before they can be exploited, significantly reducing potential security breaches. |
| Continuous policy and threshold review | This effort involves regularly updating and refining alert-generating criteria and security policies to ensure that they remain effective and relevant in the evolving cybersecurity landscape. |
| Collaborative security ecosystem | A collaborative security ecosystem advocates for a unified approach to cybersecurity where IT and security teams work together, leveraging shared insights and strategies for more effective threat management. |
| Empowerment through training | This approach underscores the need for continuous education and awareness programs for cybersecurity teams, enhancing their skills and preparedness to effectively manage and respond to security alerts. |
Causes of alert fatigue
Alert fatigue in cybersecurity results from a relentless stream of alerts, a significant portion of which are false positives. This overwhelming flow of notifications often lacks effective prioritization and correlation, causing crucial alerts to be lost in the noise. The use of intricate and overlapping security tools, which can produce redundant or conflicting alerts, further complicates the situation.
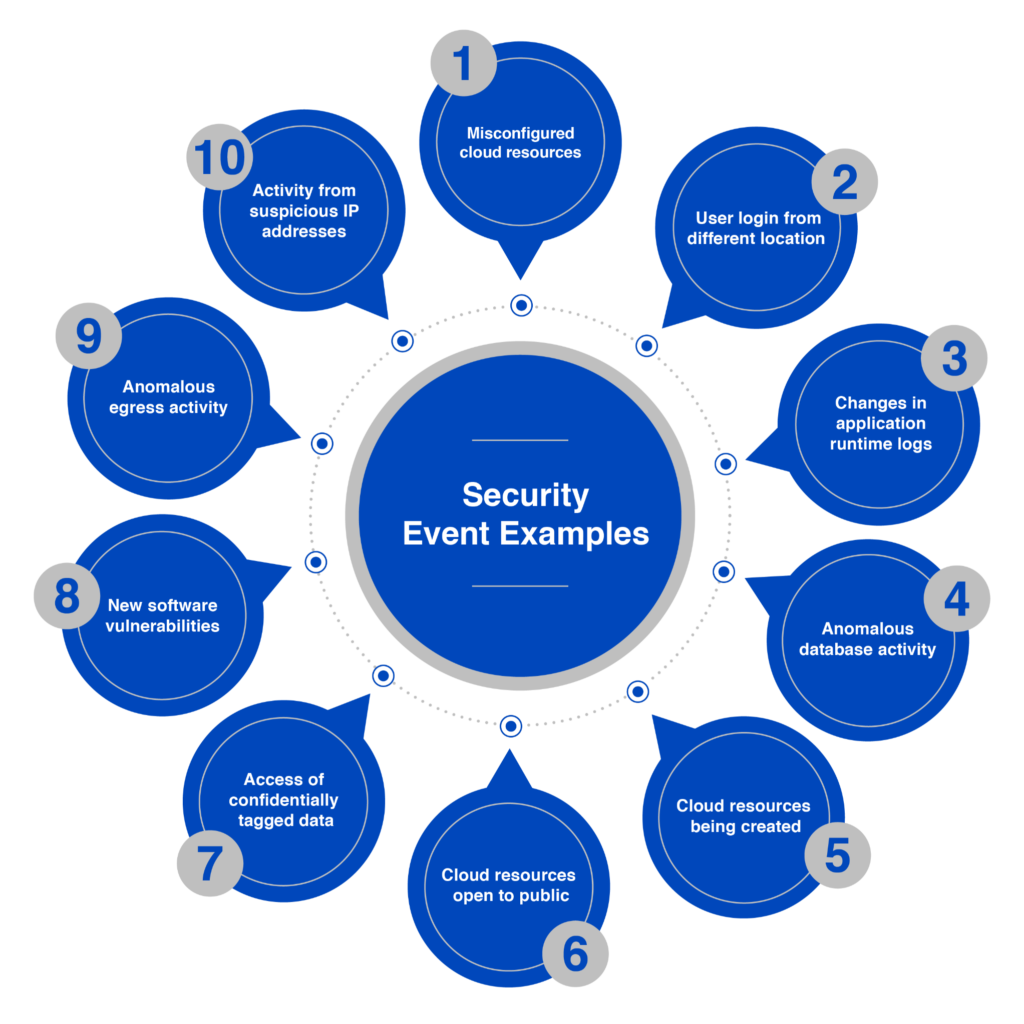
Additionally, teams frequently face challenges due to limited resources and staffing, coupled with inadequate contextual information about the alerts. Inconsistent alert thresholds also contribute to this issue, often triggering unnecessary alerts for minor or irrelevant events.
This combination of factors places immense pressure on IT and cybersecurity teams, leading to inefficient responses and increased overall business risk. The inability to effectively manage and respond to these alerts can compromise an organization’s security posture, leaving it vulnerable to cyber threats.
Real-world use case: We can draw relevant insight about alert fatigue from the SolarWinds cyberattack. This Fortinet article discusses the SolarWinds cyber attack and mentions that in IronNet’s 2021 Cybersecurity Impact Report, 85% of the attack’s impact was related to alert fatigue.
Consequences of alert fatigue
The consequences of poor alert management and alert fatigue extend beyond operational inefficiencies, striking at the very core of a security team’s effectiveness. While alert fatigue refers to the desensitization and subsequent inattention to alerts due to overwhelming volume, poor alert management encompasses broader issues, such as ineffective prioritization and response strategies. This combination can lead to critical oversights, not just because of the sheer number of alerts but also due to suboptimal handling.
The human impact of this phenomenon is profound. Cybersecurity professionals who are constantly bombarded with alerts may experience declines in their ability to discern genuine threats from false positives. This constant high alertness can lead to stress, fatigue, and ultimately burnout, significantly diminishing the team’s vigilance and responsiveness. The psychological toll of managing endless streams of alerts, especially when many are inconsequential, cannot be overstated.
From a business perspective, the risks are equally grave. Missed threats due to alert fatigue and poor management can result in undetected breaches, leading to data loss, financial repercussions, and reputational damage. Moreover, the inefficiency in handling alerts can lead to resource waste as teams expend valuable time and effort on low-priority or false alerts.
Real-world use case: A real-world example of the consequences of alert fatigue was evident in the 2020 Twitter Bitcoin scam. Cybersecurity teams at Twitter were overwhelmed with alerts, and amid this chaos, hackers orchestrated a breach, compromising high-profile accounts. This incident highlights how alert fatigue can lead to significant security oversights, resulting in substantial financial and reputational damage.
Mitigating alert fatigue
In the face of ever-increasing cyber threats, mitigating alert fatigue has become a critical task for cybersecurity teams. The key to effective mitigation lies in a holistic approach that combines advanced technology with human expertise. This involves implementing strategies that not only reduce the volume of alerts but also enhance the quality and relevance of each.
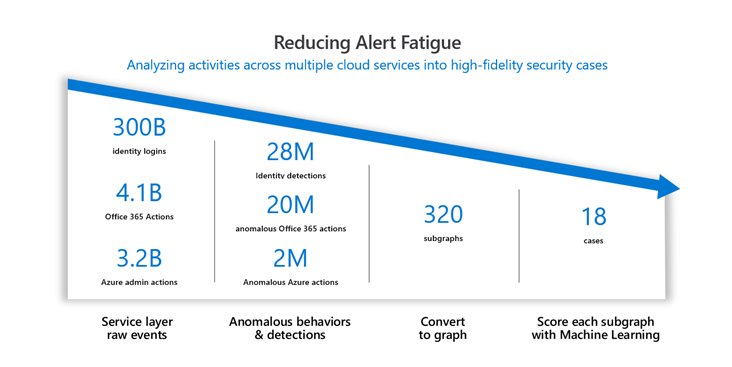
By using machine learning, raw events can be consolidated into fewer high-quality alerts (Source)
Centralized alert management systems play a crucial role in this process, consolidating alerts from various sources into a single, manageable platform. This not only streamlines the monitoring process but also provides a clearer picture of the threat landscape.
Context-driven alert prioritization is another vital aspect. By understanding the context in which alerts occur, teams can make more informed decisions about their severity and required action. Seamless integration of various security tools also contributes to a more cohesive and effective response, reducing redundancies and enhancing overall threat detection.
Proactive vulnerability assessments and continuous policy and threshold reviews ensure the system remains effective and relevant, adapting to new threats and changing environments. Real-time security insights enable quick, data-driven decisions, while empowerment through training ensures that teams are equipped with the latest knowledge and skills. Finally, fostering a collaborative security ecosystem encourages a unified approach to threat management, leveraging shared insights and strategies across different teams.
| Ways to mitigate alert fatigue | |
|---|---|
| Intelligent risk scoring | Centralized alert management |
| Context-driven alert prioritization | Seamless tool integration |
| Proactive vulnerability assessment | Continuous policy and threshold review |
| Collaborative security ecosystem | Empowerment through training |
Intelligent risk scoring
Intelligent risk scoring is a pivotal strategy for mitigating alert fatigue. By leveraging advanced algorithms and generative AI, this approach evaluates and scores each alert based on its potential risk. This method allows cybersecurity teams to focus on the most critical threats, ensuring that their attention and resources are directed efficiently, and critical threats are not lost in the noise.
Real-world use case: The article “Cyber Risk Scoring Algorithms: A Multi-Factor Approach” on LinkedIn discusses the development of a cyber risk scoring algorithm—a form of intelligent risk scoring. The algorithm leverages various factors, such as leaked passwords, attack surface size, and open ports, which indicate an intelligent approach to assessing cybersecurity risks.
Centralized alert management
Centralized alert management consolidates alerts from various security tools into a single, unified dashboard. This approach simplifies the monitoring process and provides a more coherent view of the security landscape, enabling quicker identification and response to genuine threats. By centralizing alert management, organizations can significantly reduce the time and resources spent on sifting through numerous alerts, thereby enhancing the efficiency and effectiveness of their cybersecurity operations.
Real-world use case: The article “Case Study: Centralized Security Management for Major Bank” on Trigyn’s website discusses how a major retail bank implemented a centralized security and facilities management solution. This case study can be a practical example of how centralized alert management is implemented in real-world scenarios, particularly in the banking sector.
Context-driven alert prioritization
Context-driven alert prioritization involves analyzing alerts not just based on their inherent properties but also the broader operational environment in which they occur. Such prioritization ensures that responses are tailored to the most pressing threats, enhancing the efficiency and effectiveness of cybersecurity efforts. By understanding the specific circumstances of each alert, security teams can make more informed decisions, leading to a more targeted and effective response to genuine cybersecurity threats.
Paladin Cloud unifies findings from existing security tools and cloud environments into a single platform. Paladin Cloud’s prioritization engine is AI-Powered to enable findings to be correlated and additional context added to alerts. This approach identifies the most impactful risks, so teams work on what matters most. SOC teams using this approach are more focused on addressing top security risks and reduce their alert fatigue by up to 50%.
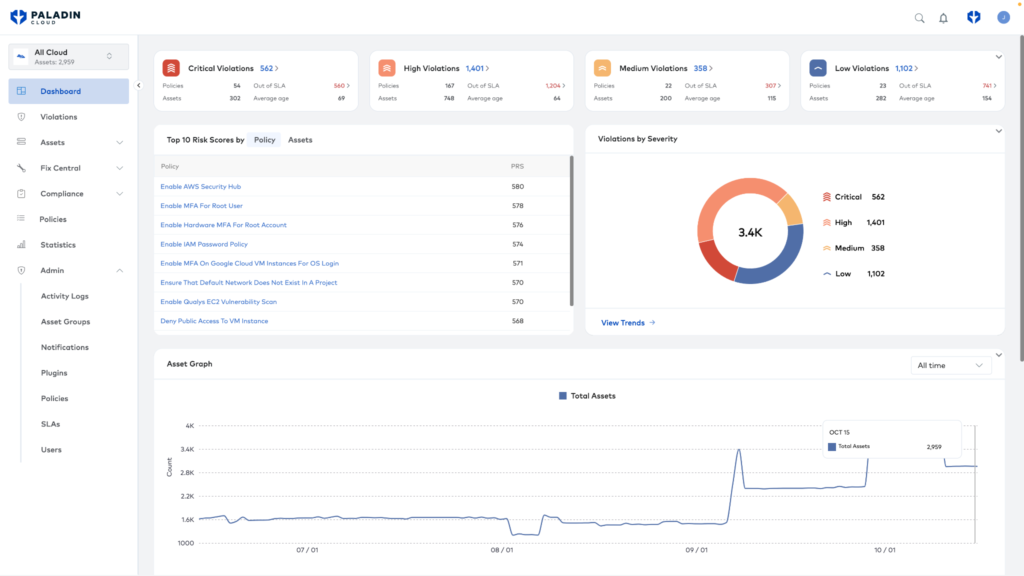
Paladin Cloud’s prioritization engine unifies findings into a single platform, enabling security teams to focus on the top security risks.
Real-world use case: A notable implementation of context-driven alert prioritization was seen in a US-based oil refinery. The system prioritized alerts based on operational technology risk context, enabling the security team to focus on the most critical issues, improving their overall security posture and operational efficiency, and reducing alert fatigue.
Seamless tool integration
Seamless tool Integration ensures that various security solutions work together for optimal protection. This approach streamlines operations while enhancing threat detection and response capabilities. By integrating disparate tools, organizations can create a cohesive security environment, reducing gaps and improving overall efficiency. Solutions like Paladin Cloud exemplify this integration, offering a platform with pre-built integrations with existing security tools to ingest their findings. Once ingested, the findings are correlated and compared against policies and assets to drive risk scoring and prioritize the most important risks.
Real-world use case: A case in point is Morris Crocker Chartered Accountants, which achieved enhanced cybersecurity through seamless integration with IRIS Anywhere. This transition showcases how effective integration can fortify security measures and streamline operations.
Proactive vulnerability assessment
Proactive vulnerability assessment focuses on the early detection and management of vulnerabilities. This approach involves continuously scanning and evaluating systems to identify potential security weaknesses before attackers can exploit them. By proactively assessing vulnerabilities, organizations can significantly reduce exposure to cyber threats and enhance the overall security posture.
Real-world use case: A notable example of proactive vulnerability assessment could be seen in an energy company that implemented Skybox Vulnerability Control. This approach enabled them to detect three times more security vulnerabilities, significantly enhancing their ability to preemptively address potential threats and strengthening their cybersecurity defenses.
Continuous policy and threshold review
Continuous policy and threshold reviews involve regular updates and refinements to security policies and alert thresholds. This process ensures that cybersecurity measures remain effective and aligned with the evolving threat landscape. By continuously reviewing and adjusting policies and thresholds, organizations can maintain a proactive stance against emerging threats, adapt to new technologies and attack vectors, and ensure that their security protocols are always up to date.
Real-world use case: The UK government’s “Cyber Primer 3rd Edition” highlights the significance of continuous policy review in national defense cybersecurity. This approach has been instrumental in adapting to changing cyber threats and maintaining robust security measures.
Collaborative security ecosystem
A collaborative security ecosystem involves various entities, such as organizations, IT teams, and security experts, sharing insights, strategies, and resources. This approach enhances the ability to detect, respond to, and prevent cyber threats more effectively. By pooling knowledge and capabilities, a collaborative ecosystem fosters a more comprehensive and resilient defense against cyber attacks.
Real-world use case: A prime example of a successful collaborative security ecosystem is the joint effort between Meta, Google, and Microsoft. The collaboration has significantly strengthened their cybersecurity measures, showcasing the power of collective action in combating cyber threats.
Empowerment through training
Empowerment through training involves providing comprehensive training and awareness programs to employees, equipping them with the knowledge and skills needed to identify and respond to cyber threats effectively. This approach not only enhances the individual capabilities of team members but also fosters a culture of cybersecurity awareness throughout the organization. Well-trained employees are a vital line of defense, capable of recognizing potential threats and taking appropriate action, thereby significantly reducing the risk of successful cyber attacks.
Real-world use case: A notable example of empowerment through training is highlighted in an article on LinkedIn, where an organization’s commitment to cybersecurity training significantly bolstered its overall security posture. The training programs focused on recognizing and responding to threats like phishing, resulting in a more aware and proactive workforce when dealing with cybersecurity challenges.
Role of SIEM/SOC/SOAR in cybersecurity
Security information and event management (SIEM), security operations center (SOC), and security orchestration, automation, and response (SOAR) systems represent traditional bastions of defense, focusing on comprehensive monitoring, threat detection, and automated response. These systems are designed to aggregate and analyze security data and logs, manage operations, and automate responses to detected threats.
However, as cyber threats evolve, modern enterprises must implement a unified approach to vulnerability management to ingest findings from various security tools and clouds to drive prioritization and remediation. Tools like Paladin Cloud’s prioritization engine contain prebuilt plugins for the enterprise’s existing tools and clouds to provide a holistic view. Using generative AI, Paladin Cloud risk scores individual findings from security tools, and then correlates risk to prioritize the most important issues. This specialization complements the broader scope of SIEM, SOC, and SOAR systems, providing an additional layer of security focused on applications and data residing in cloud environments.
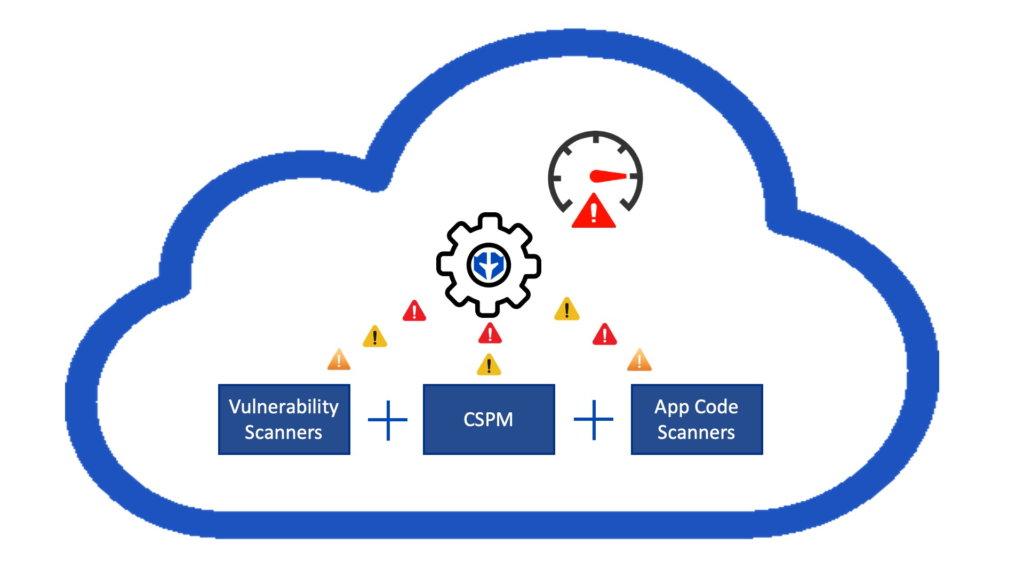
Paladin Cloud connects vulnerability scanners, CSPM, and app code scanners to correlate and prioritize risks across cloud resources.
Real-world use case: The article “AWS Security Automation” on Paladin Cloud’s website discusses the use of SIEM with AWS Security Hub for real-time monitoring and notification, which aligns with the capabilities of SOC and SOAR systems. This article is a practical example of how these technologies can be integrated and utilized effectively in a cybersecurity environment.
Conclusion: addressing alert fatigue in cybersecurity
It is clear that effectively managing alert fatigue is not just about operational efficiency—it is a cornerstone of robust cybersecurity. The above mentioned strategies are crucial in transforming an overwhelming stream of alerts into a manageable and actionable flow of critical information. These approaches not only streamline the process of identifying genuine threats but also ensure that cybersecurity teams can respond swiftly and effectively, safeguarding the organization’s digital assets.
Paladin Cloud emerges as a significant player in this landscape, enhancing these strategies with its specialized focus on prioritizing risks across application, cloud, and data security. Its capabilities in using generative AI to prioritize vulnerabilities and provide actionable insights make it an invaluable tool in the fight against alert fatigue. By integrating solutions like Paladin Cloud into your cybersecurity framework, you can leverage advanced technology to bolster your defense against an ever-evolving array of cyber threats.
The ability to not only detect but also intelligently prioritize and respond to threats is a game-changer in cybersecurity management. It empowers teams to focus their efforts where they are most needed, enhancing the overall security posture of the organization.
The battle against alert fatigue is ongoing and dynamic. It requires a proactive and adaptive approach, combining the strengths of human expertise with the sophistication of AI-Powered tools. As we continue to navigate the complexities of the digital landscape, integrating comprehensive strategies and advanced solutions like Paladin Cloud will be pivotal in ensuring the resilience and effectiveness of cybersecurity defenses.
Furthermore, it’s important to recognize that managing alert fatigue is not just a technical challenge but also a human-centric one. The psychological impact of alert overload on cybersecurity professionals is a critical aspect that often goes unnoticed. Prolonged exposure to high volumes of alerts can lead to decision fatigue, reduced attention to detail, and even burnout among team members. Therefore, an effective strategy against alert fatigue should also encompass elements of human psychology and workplace wellness. By incorporating practices such as regular team rotations, stress management programs, and continuous professional development, organizations can ensure that their cybersecurity teams remain sharp, motivated, and resilient.
This human-focused approach, combined with the technological prowess of tools like Paladin Cloud, creates a more holistic defense mechanism. It not only addresses the technical aspects of cybersecurity but also nurtures the well-being and efficiency of the people behind these systems, ultimately leading to a more sustainable and effective security posture in the face of evolving cyber threats.