With around 76% of organizations using some form of cloud integrations as of 2022 and an Enterprise Strategy Group publication from February 2023 indicating that nearly 88% of organizations see strategic benefits in using more than one public cloud provider, it’s clear that cloud risk management is a must for organizations. In fact, the cloud is now one of the biggest attack surfaces in modern enterprises. IBM reports that 82% of breaches involve data stored in the cloud.
Statistics like these highlight the need for effective cloud risk management. Organizations must play a proactive role in addressing the new threats that come with running workloads in multi-cloud environments.
This article will explore essential cloud risk management practices, challenges, and how to implement viable solutions for modern organizations, ending with a set of recommendations.
Summary of key cloud risk management concepts
The table below summarizes eight essential cloud risk concepts this article will explore in more detail.
| Concept | Description |
|---|---|
| Migration | Migrating from on-premises to cloud resources is the first step toward utilizing the cloud. Still, it is also the first significant risk. There are several factors to consider when planning your migration. |
| Cloud asset management | Just as you would track and manage on-premise resources, your organization needs to understand and manage your cloud assets properly. Whether your organization is new to the cloud or operates in a multi-cloud environment. |
| Risk identification | It’s important to understand risks within your cloud environment:
|
| Risk likelihood | Some risks may be more likely to be exploited than others, and some may be more impactful if exploited. |
| Risk mitigation | Several tools and processes are available to help your organization discover, evaluate, and mitigate security risks within your cloud environment. |
| Threat modeling | Threat modeling can become more complex as your cloud environment grows. |
| Vulnerability management | Cloud resources still require patching, which requires using either third-party vulnerability management tools or internal cloud resources to identify vulnerabilities. |
| Incident response | Integrating your cloud assets with your incident response tools (such as SIEM) is vital to ensure real-time monitoring for threats. |
Migrating to the cloud
While cloud risk management presents many of the same challenges as risk management for on-premises environments, a few are either more cumbersome or unique to cloud environments altogether. Migrating can be broken down into two stages: the planning stage and the execution stage. During the planning stage, you will need to consider what technologies you will use, which cloud service provider(s) you will work with, and plan for any applicable compliance rules or regulations. Also, consider whether you are simply testing a new cloud service provider as part of an evaluation or you’ve already decided to go with one or more providers.
Once your organization has determined which provider(s) to work with, evaluating the chances of being locked in by the vendor and how vendor lock-out is handled is worthwhile. You want to ensure your organization can still move from one provider to another and that you won’t be confined to a vendor due to cost or dependency. You’ll also want to ensure whichever vendor(s) you choose have a record of satisfactory customer service to minimize your organization experiencing issues accessing your new cloud environment.
Let’s look at resource migration as another example. One of the biggest risks your organization will encounter when migrating to the cloud is the risk of data loss, corruption, and leakage. Migrations can become more complicated by factors such as the volume of data being migrated, the sensitivity of the data, the availability requirements throughout the migration, and more. Planning a migration to the cloud is an excellent time for reflection; confirm whether your data is appropriately classified and your assets are correctly tagged, and review your organization’s current state of compliance.
Regardless of the volume and type(s) of data you intend to migrate to the cloud, producing and maintaining at least one backup of everything you need is always a good idea. Backups should be maintained in any environment, but a migration to the cloud introduces the same risk of data loss or corruption as any data transfer. So, take extra care to ensure your backups are as recent as possible before migration. It is also worth discussing a migration strategy with your new cloud provider(s) because many have dedicated migration services to assist in successfully transferring your data.
Cloud configuration is another essential aspect of cloud risk management. Are you migrating entire virtual machines (VMs) and databases (DBs), or are you building new VMs and DBs in your new cloud environment and only migrating the data? If you’re building new, ensure your VMs and DBs are secure by following best practices such as:
- Enabling encryption
- Do not make VMs and DBs publicly available unless necessary for business functions.
- Follow the principle of least privilege to ensure Identity Access Management (IAM) policies are not overly permissive.
- Also, consider how users will authenticate when accessing your cloud environment. Active Directory (AD) may be an option, whether through a new AD tree or via integrating your existing on-premises AD with the cloud.
- Tools like CIS Benchmarks provide security best practices which are developed with the help of security experts. Implementing CIS Benchmarks can help prevent compliance failures due to misconfigured cloud resources.
Finally, be sure to consider security monitoring. Most cloud service providers offer some form of security incident and vulnerability monitoring. Dedicated security monitoring solutions also offer cloud compatibility. Whatever your organization decides, it may take some time to reestablish a baseline once you’ve completed your migration, which means there may be an adjustment period during which alert parameters may need to be fine-tuned and suppressed.
Cloud asset management
Another challenge many organizations face regarding successful cloud risk management is asset management – knowing what resources are being migrated, replicated, and/or created in the cloud. Without knowing what resources are in your cloud environment, what type of data those resources interact with, and who is responsible for maintaining them, your organization’s cloud environment is at risk.
Tying back into ensuring IAM policies are not overly permissive, it’s crucial to ensure that roles able to create, remove, or modify cloud resources are limited to only what is necessary. It’s also essential to ensure cloud resource creation, modification, and removal of cloud resources are tracked through some form of workflow for security and business reasons. Without proper tracking, your organization risks introducing what is commonly referred to as “shadow IT” assets to your environment. Shadow IT is a term used to describe assets unknown to an organization’s IT and security department(s). It often results from a lack of collaboration and coordination between IT/security and other departments within the organization. For example, suppose the development team was to create a new production server and not inform IT/security. In that case, that new server will more than likely be configured insecurely and eventually need software patches, but because IT/security doesn’t know about the existence of this server, no security scanning or patching is occurring.
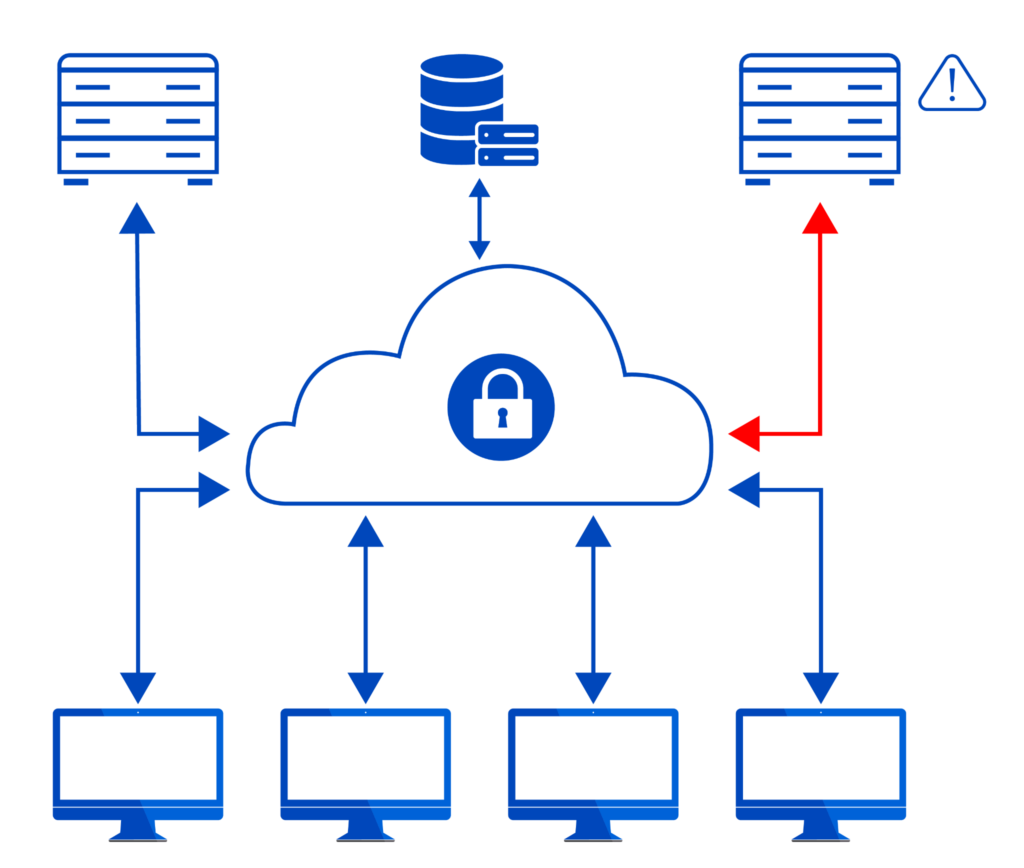
This diagram shows a shadow IT device within the cloud environment. Poor cloud asset management has led to an unknown device being connected to other cloud resources.
Assigning clear responsibilities for your cloud environment is another essential risk step for effective cloud risk management. Unclear assignment of responsibilities can lead to longer response times, which leaves your environment’s attack surface open longer and risks giving attackers more time on your network. Asset owners need to be accountable for their assets, and equally important, those asset owners are known within your organization. The longer it takes to determine ownership, the longer your environment is at risk. Paladin Cloud can help with creating and monitoring asset tagging policies to ensure all cloud assets are accounted for and mapped to their owners, products and environments.
Risk identification
Risk identification is a crucial component of effective cloud risk management. Whether your organization is 100% in the cloud or operating a hybrid environment, several risks need to be identified and addressed.
Examples of relevant risks include:
- Cloud assets may be unknowingly accessible to the public (this exposure could result in increased alert volume as bad actors may try to scan and/or authenticate these assets).
- Cloud assets may be unknowingly unencrypted (this may lead to an increase in vulnerability alerts).
- Identity Access Management (IAM) policies may be too permissive.
- Backups may not be scheduled or retained within legal standards and organizational policy.
- Notifications may not be set up correctly to notify the right people or teams.
- Security tools may not be monitoring cloud assets properly or at all.
The basic principles of security revolve around confidentiality, integrity, and availability. Cloud security is no different, and the first step your organization should take when protecting your cloud environment is to identify risks. Identify the risks which might compromise the confidentiality of your organization’s and your customer’s data. Recognize what may negatively impact the integrity of your data, services, and products.
Finally, determine what risks could threaten the availability of your organization’s network. It would be beneficial to amend your disaster recovery and business continuity plans to include your cloud environment. You may find some areas of improvement around backups, preventative monitoring, and how your organization manages IAM permissions.
It’s also important to note most cloud providers operate on what is known as a shared responsibility model. This shared responsibility model highlights which cloud security components belong to the provider and the customer. In many cases, the cloud provider’s responsibility is to provide all the tools and features necessary for the customer to implement so they can meet the organization’s security policies and applicable legal requirements.
Risk likelihood
Understanding the current attack patterns and how they relate to your environment will help you identify the risks your organization faces beyond what traditional vulnerability scanners or security audits would identify. As the threat landscape grows increasingly complex, new attack vectors have opened up across application, data and cloud security. Once your organization has identified the risks within your cloud environment, it is time to prioritize your response efforts by assessing the likelihood of each risk being exploited and its impact. To be able to accurately calculate risk likelihood, we’ll first need to contextualize the risks your organization has identified. The makeup of your environment will influence the type of risks your organization will face, and will make some risks more likely than others. For example, being a large organization dealing with billions of dollars worth of customer data and payments may increase your risk of being targeted by ransomware attacks instead of intellectual property theft (IP), while being a cutting-edge medical research organization may increase your likelihood of being targeted for IP theft rather than ransomware.
Two tools that may greatly assist in assessing risk likelihood are the Exploit Prediction Scoring System (EPSS) and the National Institute of Standards and Technology’s Risk Management Framework (NIST RMF). The EPSS accounts for several variables before assigning each CVE (Common Vulnerabilities and Exposures) a decimal score from 0 to 1 based on how likely a particular CVE will be exploited within the next 30 days. Less than 10% of vulnerabilities are exploited, so the EPSS can significantly assist your organization’s prioritization of remediation efforts to focus only on the riskiest vulnerabilities. The NIST RMF is a valuable resource for categorizing risks based on what you know about your environment. Once you’ve categorized those risks, you can evaluate that data against NIST RMF controls to help your organization prioritize response efforts.
Risk mitigation
Now that your organization has identified and assessed the risks to your cloud environment, it’s time to mitigate them. Depending on what tools your organization has used to identify the risks in your cloud environment, you may already know exactly what needs to be done to strengthen your security posture. This often involves upgrading software to newer versions to fix security flaws or changing the configuration settings of some operating system or tool, but there can be additional complexities.
The NIST RMF can also help your organization prioritize response and mitigation efforts holistically. Still, your organization will likely also want to implement third-party tools or cloud-native products and services to begin the mitigation. Most cloud service providers offer one or more options to help with risk mitigation. For example, AWS Inspector and Azure Security Center identify vulnerabilities and recommend what action to take and when.
Paladin Cloud’s open source Cloud Security Posture Management (CSPM) can help ensure your organization’s cloud security posture is secure by highlighting existing opportunities for improvement, not just with unpatched software, but with misconfigurations such as overly-permissive IAM policies, missing backups, and more. Paladin Cloud’s CSPM provides a holistic overview of your cloud environment by ingesting data directly from your cloud setup, as well as third-party tools like vulnerability scanners, and aggregating all that information into an actionable report.
Something to consider when assessing your options for risk remediation is the use of compensating controls. Compensating controls can be used if the recommended remediation is not feasible for your organization in the short term. For example, consider an environment that uses an FTP server. FTP is an insecure protocol and should be avoided, but if your organization absolutely needs an FTP server, you could make it more secure by enabling heavily restrictive firewall rules to only allow access to the FTP server via one or two machines specified by IP address. While this solution is less ideal than trading the FTP server for a more secure option, it is better than exposing it to more than just one or two machines.
Threat modeling, vulnerability management, and incident response
As your organization expands its cloud environment, it risks expanding its attack surface. Understanding how your cloud environment works within itself, with your on-premises stack, and how it all interacts with the public internet is imperative. A deep understanding of your architecture will help your organization assess the value of each asset and determine which assets are most likely to be attacked first.
Asset identification is the first step in the threat modeling process. You need to know what each asset is, its business function, who’s responsible for it, and its mission criticality. It helps to label your cloud resources by function and location (public or internal facing). From there, you can identify risks facing each resource or resource group, such as whether a particular group of resources is more valuable because of its function. Paladin Cloud offers asset discovery solutions to help you visualize your attack surface to help better prepare you to defend it.
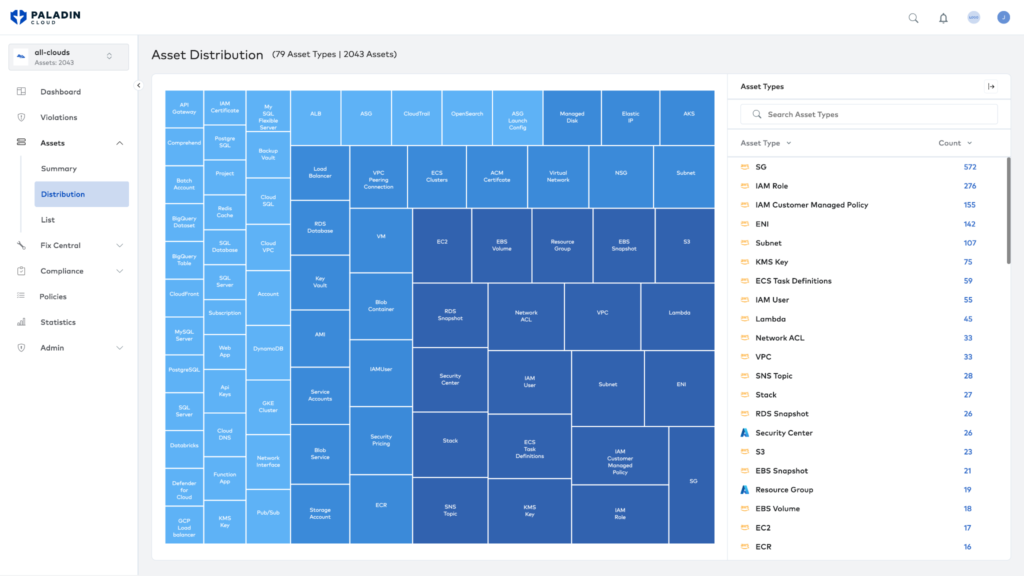
An example of Asset Discovery in Paladin Cloud helps visualize your attack surface and identify any shadow IT resources.
The next step in the threat modeling process is vulnerability analysis. While this ties back into risk identification, it’s important to distinguish that by now, you should have a detailed, holistic understanding of your environment and be able to factor in the criticality of each resource or resource group when prioritizing actions from vulnerability analyses. Once you’ve identified your assets and threats and analyzed any applicable vulnerabilities, your organization needs to implement countermeasures. Often, this will be as simple as patching outdated software or fixing misconfigurations, but countermeasures can include additional IAM restrictions, password complexity improvements, firewall rules, and more.
As we’ve covered, a significant component of cloud risk management is vulnerability management, which includes software patching and fixing misconfigurations. Your organization should use at least one vulnerability scanning tool for your on-premises assets. That same tool may be compatible with your cloud environment, or you may use a more cloud-specific alternative. Either way, your cloud environment should be scanned regularly for vulnerabilities such as outdated software, application vulnerabilities (outdated libraries and insecure code), and misconfigurations.
Many tools are even moving to a 24/7 scanning model to reduce the time a vulnerability lives within your environment undetected. Vulnerability management tools like Tenable, Qualys, and Orca are helping organizations monitor multiple cloud environments from within a single tool. Some of these tools even allow users to take actions such as quarantining or upgrading specific assets right from within the tool. Your organization should aspire to protect your cloud environment with the same level of care (or more) as your on-premises environment. Paladin Cloud can integrate security findings from multiple sources and prioritize the most critical vulnerabilities using an AI-Powered Prioritization Engine. This allows you to see all your vulnerabilities, outdated software, insecure code, and misconfigurations prioritized and ready to act on, in one place.
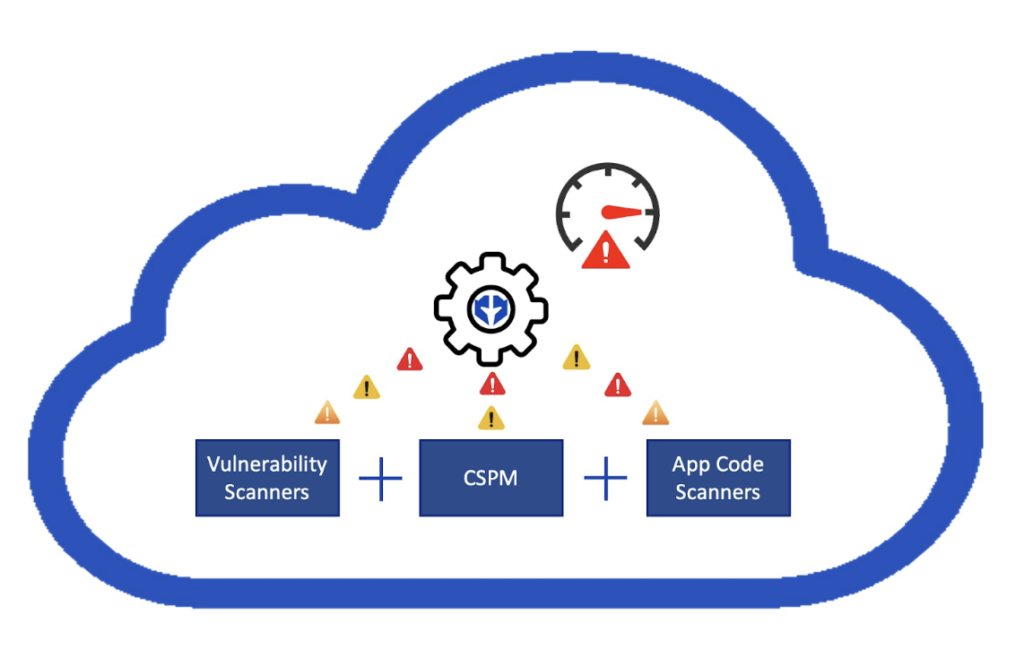
Paladin Cloud offers an AI‑Powered Prioritization Engine that can correlate risks from third-party vulnerability scanners, CSPM, and app code scanners
Summary of cloud risk management best practices
The security aspects of cloud risk management do not have to be overwhelming. Whether you’re looking to start utilizing the cloud or want to expand your existing cloud usage, the following tips will help smooth the transition. The table below summarizes best practices for each aspect of cloud risk management we explored in this article.
| Summary | Best Practice |
|---|---|
| Migration | Account for availability disruptions when planning the migration of on-premise workloads. |
| Cloud asset management | Maintain accurate asset inventories and update them regularly, ideally using tooling that automates the process. |
| Risk identification | Enumerate risks early and often in the planning process. |
| Risk likelihood | Ensure your organization is optimizing its response efforts by considering risk likelihood as you prioritize remediation. |
| Risk mitigation | Leverage tools and processes available to help your organization discover, evaluate, and mitigate security risks within your cloud environment. |
| Threat modeling | Know your environment. Know how your cloud-based assets communicate with the Internet, amongst themselves, and with your on-premises environment. |
| Vulnerability management | Perform regular vulnerability scanning and patching. Your cloud-based assets accumulate vulnerabilities and will become End of Life / End of Support just as your on-premises assets do if you don’t actively patch the underlying software and operating systems. |
| Incident response | Implementing a centralized incident management tool, maintaining an accurate asset inventory, and documenting knowledge of your organization’s overall architecture will help make incident response a smooth process. |
Paladin Cloud can help your organization’s security and developer teams run smoothly by correlating and prioritizing findings across existing security tools and clouds, including CSPM, vulnerability scanners, and application security tools. Discussing factors such as budget, resources, and whether your organization is looking for a single cloud provider or multi-cloud options are the first steps to effective cloud risk management.