Safeguarding an organization’s sensitive data and critical systems is paramount as the digital landscape changes. Cyber threats loom large, ranging from malware and data breaches to sophisticated hacking attempts. The threat remediation concept emerges as a crucial defense mechanism within this context.
Threat remediation involves identifying, assessing, and mitigating security threats to protect an organization’s assets. This multifaceted approach bolsters your defenses against potential attacks and helps ensure the uninterrupted flow of business operations. On average, teams spend nearly 140 hours per week monitoring systems for threats and vulnerabilities. This article delves into the best practices for implementing effective threat remediation strategies.
As you embark on this journey through threat remediation, this article will offer practical advice and guidance. We will help fortify your organization’s cybersecurity posture. Expect to gain a comprehensive understanding of the strategies and techniques necessary to identify, assess, and mitigate security threats.
Summary of key threat remediation concepts
| Concept | Description |
|---|---|
| Rapid threat identification: prevention and detection | Swiftly detect and respond to security threats to minimize potential damage.
Prevention systems include firewalls, Intrusion Prevention Systems (IPSes), and Endpoint Detection and Response (EDR). Detection systems include Intrusion Detection Systems (IDSes), Cloud Security Posture Management (CSPM), and Dynamic Application Security Testing (DAST). |
| Threat prioritization | You can optimize resource allocation by ranking security threats by severity, likelihood, and impact. Several risk assessment frameworks, including NIST CSF and CVSS metrics, can guide your threat prioritization. |
| Incident triage and escalation | Incident triage involves assessing the severity and potential impact. Knowing when and how to escalate incidents is essential to avoid delays. The NIST SP 800-61 Rev. 2 Computer Security Incident Handling Guide is a good foundation for developing your incident response process. |
| Threat remediation techniques and post-incident analysis and documentation. | Remediation focuses on fixing identified misconfigurations or patching vulnerabilities. On the other hand, mitigation aims to reduce the likelihood of a threat exploiting a vulnerability.
Explore practical strategies and security controls to mitigate threats, bolster defenses, and conduct thorough post-incident analysis and documentation for continuous improvement. |
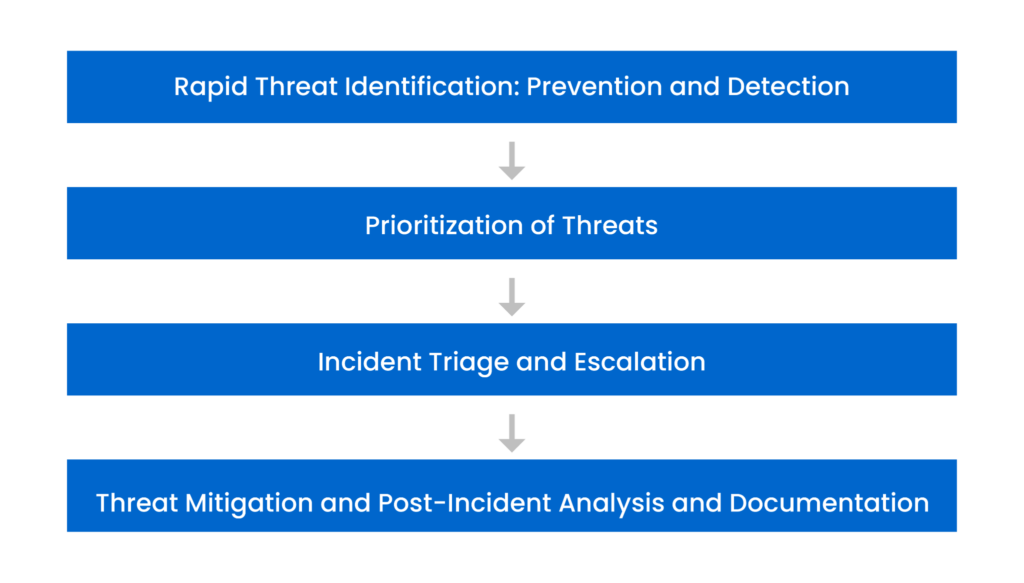
This article covers four stages of threat remediation
Rapid threat identification: prevention and detection
Real-time threat identification is the linchpin of effective cybersecurity. In today’s fast-paced digital landscape, threats can emerge anytime, and an effective defense strategy hinges on prevention and detection. Each is pivotal in identifying and responding to threats in real-time to minimize potential damage.
Prevention takes a proactive approach to security and involves several key components:
- Firewalls act as a barrier, blocking unauthorized access and ensuring that only legitimate traffic enters your network.
- Intrusion prevention systems (IPSes) monitor network traffic for suspicious patterns and proactively prevent potential threats from exploiting vulnerabilities.
- Endpoint detection and response (EDR) platforms safeguard endpoint devices and IT assets against cyber threats that can bypass traditional antivirus software and other endpoint security tools.
In contrast, detection measures like intrusion detection systems (IDSes) focus on live monitoring for suspicious activities and highlighting potential threats across your network. Organizations can enhance threat identification by integrating cloud security posture management (CSPM) and dynamic application security testing (DAST) tools. CSPM tools identify misconfigured cloud resources and unsecured infrastructure, while DAST tools examine vulnerable code in runtime environments, adding an extra layer of vigilance against breaches. Combining these tools can let organizations bolster their threat identification capabilities and address the primary drivers of alert fatigue, ultimately improving their security programs.
Monitoring your network, systems, and applications is essential to spot vulnerabilities, insecure configurations, and possible threats as they occur. This timely response thwarts attackers and reduces the attack surface.
An essential part of the threat identification process is vigilant log management, which includes log collection and storage processes from various sets of devices (networking gear, systems, databases, servers, endpoints, etc.) in your company network. This data can then be fed into a security information and event management (SIEM) system. SIEM solutions offer advanced analytics, centralization, aggregation, and security data correlation across your IT infrastructure. This comprehensive approach enables advanced security analytics to generate reports and alerts.
Understanding the dangers of vulnerabilities and misconfigurations is essential. Consider a misconfigured Amazon S3 bucket where public access is unrestricted; sensitive information could be accessed in such a scenario. The images below show turning on public access to an S3 bucket. A sudden increase in exposed data may indicate that this threat is present. You might notice this by looking at the access logs or seeing suspicious data egress trends.
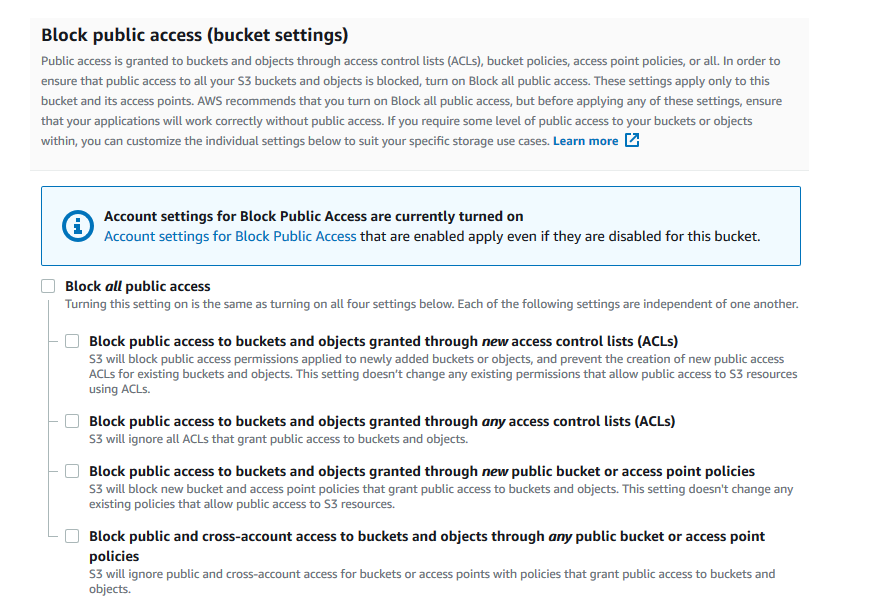
AWS permissions for website access: block public access turned on (Source)
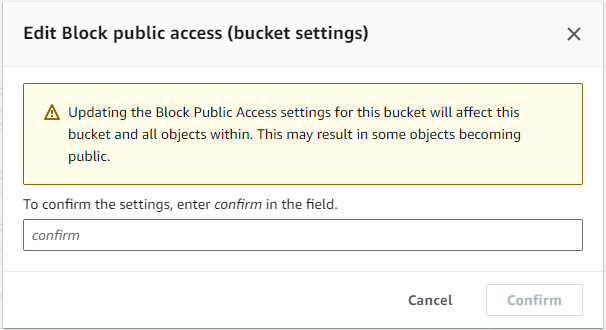
AWS permissions for website access: confirming the changes
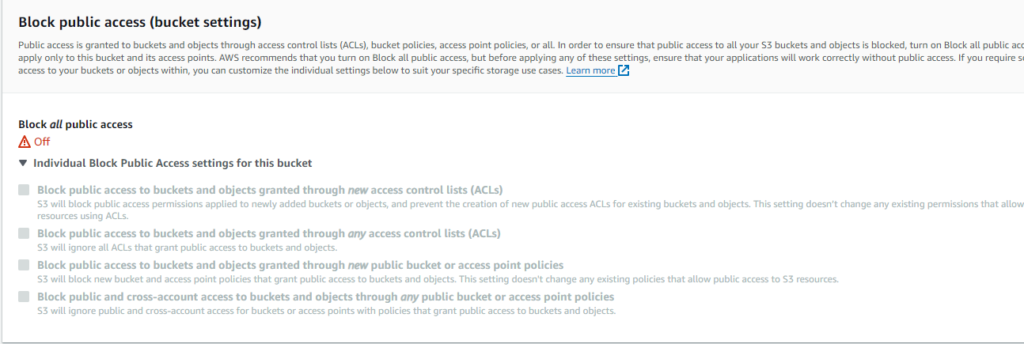
AWS permissions for website access: block public access turned off
Misconfigured AWS identity and access management (IAM) policies can lead to unauthorized access attempts. Unusual IAM role usage patterns (due to unused IAM roles) or an influx of authentication failures could indicate this threat. The following diagram showcases the integration of AWS Config rules, Lambda functions, and CloudWatch alarms to provide real-time insights into your IAM role usage. This robust setup allows organizations to proactively detect and remediate unused IAM roles, reducing the risk of unauthorized access and ensuring that IAM resources remain secure and optimized for operational efficiency.
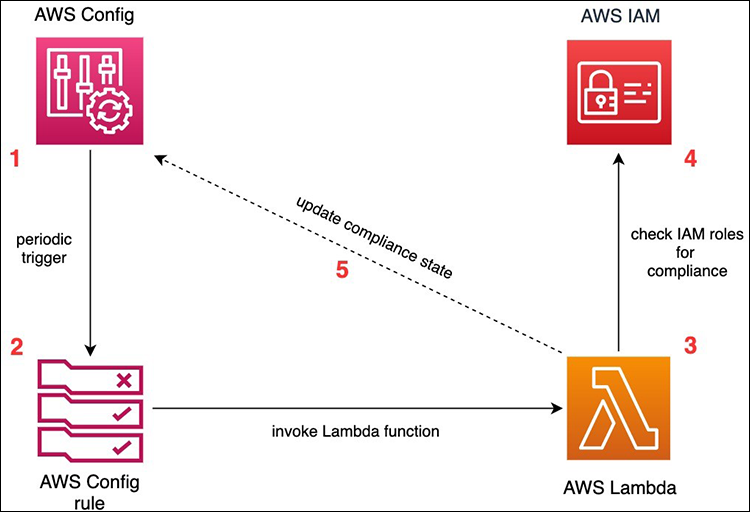
Architecture for continuous monitoring of unused IAM roles with AWS Config (Source)
For further details on this solution AWS provides, check out the AWS Security blog.
Prioritization of threats
The spectrum of threats, vulnerabilities, and even misconfigurations is vast and ever-evolving, and employing a one-size-fits-all approach to prioritize threats is often impractical. Threat remediation requires prioritization; therefore, many organizations have adopted a multi-pronged strategy to address this challenge, leveraging various security tools and practices. These best-in-class tools encompass a range of security solutions, including vulnerability management, cloud security posture management (CSPM), Data Security Posture Management (DSPM), application code scanners, and endpoint detection systems, among others. Integrating these tools is vital to identifying and addressing security risks effectively, mitigating the issue of alert fatigue that often plagues security teams.
Additionally, organizations use risk scoring to streamline the prioritization of cybersecurity threats and correlate these threats across various security tools. This approach provides valuable business insights and allows security and developer teams to focus on remedying the most critical risks. By doing so, organizations can improve their security resilience in the face of diverse and ever-present threats.
Furthermore, using a cybersecurity or risk assessment framework like NIST’s Cybersecurity, MITRE ATT&CK, or ISO 27001 risk management, it is strongly recommended to guide your threat prioritization efforts and understand the Common Vulnerability Scoring System (CVSS). CVSS is an open industry standard for assessing the severity of vulnerabilities and provides a numerical representation of the severity. It can be turned into a qualitative representation (low, medium, high, and critical) to help prioritize vulnerabilities.
These frameworks provide structured methodologies for evaluating and ranking risks, helping you make informed decisions about which threats require the most urgent action. The frameworks have different scopes, structures, and approaches and can be used to create a comprehensive cybersecurity strategy. Organizations should determine which portions of these frameworks to use and customize them based on their business needs. Working with experienced cybersecurity professionals to develop and implement an effective cybersecurity plan is essential.
A practical approach to threat ranking can further refine your prioritization strategy. Creating a risk analysis matrix is valuable, as illustrated in the following image. The matrix considers both the likelihood of the risk and the impact it would have. This scenario-based ranks threats on a scale that considers likelihood (from “Rare” to “Highly Probable”) and impact (from “Insignificant” to “Severe”). The resulting ratings are low (L), medium (M), high (H), and extreme (E). Actions for these risks could range from.
- immediate actions like shutting down a resource
- regular patching and triggering your incident processes
- management notifications and involvement
- developing a mitigation strategy
Regularly revisit and update the matrix as your threat landscape evolves.
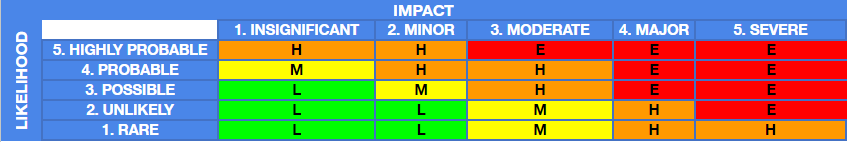
Example risk analysis matrix
Businesses can enhance their risk analysis efforts by incorporating the OWASP Threat and Safeguard Matrix (TaSM) to build a more robust defense-in-depth security plan. This specialized matrix, designed by the Open Worldwide Application Security Project (OWASP), complements traditional risk analysis matrices by focusing on significant information security industry threats and corresponding safeguards.
By integrating TaSM into their security strategies, organizations can better identify and address the most significant threats, ultimately bolstering their overall security programs in an increasingly digital world.
Role of AI
With security operations teams facing a barrage of alerts, artificial intelligence is a key technology to correlate and contextualize findings. Threat detection is one of the top use cases for generative AI in cybersecurity. Threat activity often follows repetitive patterns, which can be hidden within the vast amounts of data produced by different security tools. Generative AI can learn from historical security data and then be applied to detect subtle changes in network behavior, user activity, or cloud resource configurations.
Organizations may have implemented best-in-class tools within a given security tool category, for example, a CSPM, a DSPM, and an application code vulnerability scanner. But using these tools in isolation can miss critical business context. Generative AI models can ingest findings from multiple security tools to provide security response recommendations based on what tactics were successful in the past. These models can learn from incidents and adapt response strategies over time.
For example, Paladin Cloud’s AI-Powered risk-scoring Prioritization Engine harnesses the power of generative AI. It identifies, prioritizes, and offers remediation guidance to prioritize the most critical security risks. This advanced engine considers the severity of threats and their likelihood and impact on your organization—high-severity threats with a significant potential impact demand immediate attention.
Incident triage and escalation
The incident handling process starts with incident triage. During triage, the team assesses the incident’s severity and impact to develop an initial response plan and allocate resources effectively.
Knowing when and how to escalate incidents is also essential. When an incident is beyond your response team’s capabilities, you need to escalate it. This can involve notifying higher-level personnel, third-party experts, or specialized response teams to prevent delays in resolving the incident.
Additionally, incident response capabilities can be automated by integrating it with security orchestration, automation, and response (SOAR) systems, which integrate and coordinate several tools into threat response sequences or playbooks for detection, investigation, and response.
Having a well-documented incident response workflow is crucial. This workflow includes preparation, detection and analysis, containment eradication and recovery, and post-incident activity, as shown below.
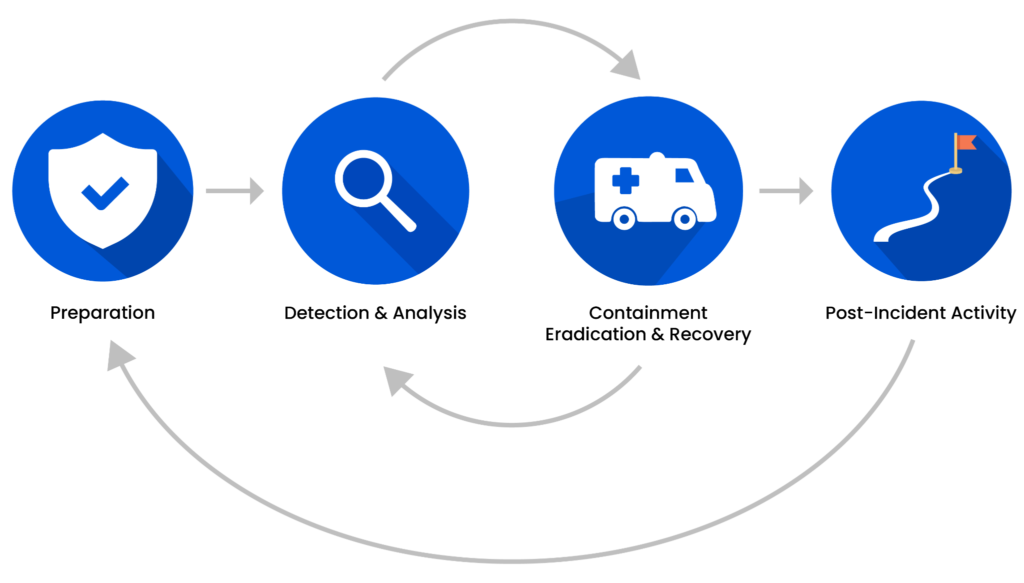
Incident response lifecycle (Source)
Organizations can use the NIST SP 800-61 Rev. 2 Computer Security Incident Handling Guide to streamline the process. This well-established resource is a foundation for creating security incident response capabilities. It allows organizations to handle incidents efficiently and effectively while adapting them to their technical and business needs without building response protocols from scratch.
This structured approach ensures that everyone involved in incident response follows a consistent and proven process that reduces the risk of errors during high-stress situations. Organizations can effectively manage security incidents, minimize their impact, and improve cybersecurity by aligning their incident handling with this guideline.
Threat mitigation and post-incident analysis and documentation
Threat remediation constitutes a critical phase in an organization’s cybersecurity strategy, primarily focusing on eliminating identified vulnerabilities and misconfigurations to fortify its defenses. Remediation seeks to address the root causes of security weaknesses, providing a lasting solution to potential threats. This phase involves meticulous efforts to patch vulnerabilities, fix misconfigurations, and rectify security flaws across an organization’s infrastructure. The goal is to render vulnerabilities non-exploitable, minimizing the potential harm cyber threats pose.
Here are two common examples of remediation constraints that companies might face in their operations:
- Resource and budget limitations: These can significantly impact a company’s ability to remediate security threats promptly. Remediation efforts often require dedicated resources, including highly skilled personnel, time, and financial investments. In cases where a company operates with constrained resources or budgetary constraints, promptly addressing all vulnerabilities and misconfigurations may be challenging. This can lead to prioritization issues, forcing companies to allocate resources to the most critical threats first. In such situations, mitigation measures, such as implementing risk-based prioritization or compensating controls, may be necessary to temporarily reduce the exposure to threats until sufficient resources become available for remediation.
- Legacy systems and dependencies: Legacy systems and their dependencies within a company’s infrastructure often do not support security patches or updates, making it challenging to remediate vulnerabilities effectively. Sometimes, these systems are critical for the company’s operations and cannot be easily replaced or upgraded. As a result, companies may have limited remediation options for vulnerabilities within these legacy systems. In such scenarios, mitigation measures—such as network segmentation and stringent access controls—become essential to reduce the risk of exploitation while the company works on a long-term solution.
Threat remediation techniques emphasize the importance of swift and comprehensive actions. Imagine having the power to centralize health notifications that provide a comprehensive view of security recommendations, as shown in the image below. You can map a strategic plan to take corrective action to optimize your security response. Automated remediation management ensures that critical security updates and corrective actions are applied promptly to your system resources, reducing response times and minimizing the impact of security incidents while saving valuable time to enhance your organization’s defenses.
The Paladin Cloud centralized health notification center
After the initial incident response phases, you need thorough post-incident analysis and documentation. Post-incident analysis is fundamental as it helps your organization learn from past events. It identifies the leading causes of issues and improves security measures by helping team members learn to prevent repeating the same mistakes.
Conducting a root cause analysis is a substantive component of the post-incident analysis process. It involves a deep dive into the incident that will uncover the underlying issues. This meticulous examination may include scrutinizing system logs, interviewing relevant parties, and reviewing security policies and procedures. By identifying the root causes, your organization can implement long-term fixes to address vulnerabilities.
Comprehensive documentation of incidents is a must for regulatory compliance and is also essential for continuous improvement. This documentation should include detailed timelines, actions taken, and outcomes; it will serve as a valuable resource for incident response teams. Future security strategies should incorporate lessons learned from these documented incidents to ensure that your organization evolves with a proactive and adaptive cybersecurity approach. As mentioned above, organizations can strengthen their incident response capabilities by aligning with the NIST SP 800-61 Rev. 2 Guide to bolster their security posture.
Paladin Cloud offers a unified platform to navigate this complex landscape. The platform seamlessly connects vulnerability scanners to CSPM tools and application code scanners. Organizations can use its AI-Powered prioritization engine to efficiently correlate risks across their cloud environments to identify and prioritize security threats.
Conclusion
The path to a robust and resilient security posture begins with proactive measures. This article has explored various vital facets of safeguarding your organization’s digital assets, covering rapid threat identification encompassing prevention and detection, effective threat prioritization, the significance of incident triage and escalation protocols, and emphasized the importance of threat remediation techniques and post-incident analysis and documentation.
By implementing these best practices, organizations can prevent and reduce the potential damage caused by cyber-attacks and ensure the uninterrupted flow of business operations. Prioritizing threats based on likelihood and impact while leveraging advanced tools and techniques for identification is paramount. Efficiently allocating resources to address high-priority risks can substantially mitigate alert fatigue, elevating your organization’s information security to new heights.
Establishing streamlined incident response procedures and continuous adaptation to evolving threats lets you stay ahead of potential attacks and safeguard your valuable assets. It’s vital to recognize that cybersecurity is an ongoing journey that requires unwavering attention and investment to ensure long-term resilience in the face of dynamic and persistent threats.
Learn more about the Prioritization Engine of Paladin Cloud and its benefits and advantages at Paladin Cloud. You can also explore the free, open-source product on GitHub.