Effective vulnerability prioritization is a cornerstone of cybersecurity defense, especially in complex environments like public and hybrid clouds and expansive enterprise IT infrastructures. Organizations simply don’t have enough resources to address every vulnerability, so they have to be efficient with their efforts and resolve high-risk issues first.
Of course, understanding how to prioritize vulnerabilities can be challenging with all the complexities of modern applications and cloud infrastructure. Navigating the intricacies of exploit availability, attack vector specificity, and business impact assessments requires the proper tooling, mindset, and strategy.
This article will help seasoned cybersecurity professionals navigate that complexity and provide practical advice to enhance strategic decision-making in vulnerability management, ensuring that vulnerability prioritization is both informed and effective.
Summary of how to prioritize vulnerabilities
Below is a concise summary of key vulnerability prioritization concepts designed to guide cybersecurity professionals in effectively managing and mitigating digital threats:
| Concept | Description |
|---|---|
| Exploit availability analysis | Assess whether an exploit for a vulnerability is actively available in the wild. |
| Attack vector specificity | Evaluate the specific conditions required for an exploit to be successful. For instance, an attack requiring a physical presence in a server room is less risky than remotely exploitable vulnerabilities. |
| Privilege requirement assessment | Determine if a vulnerability can be exploited with or without elevated privileges. Generally speaking, vulnerabilities that an attacker with standard user privileges can exploit are more severe because there is a greater likelihood that they will be. |
| Business Impact Assessment (BIA) Integration with DSPM | Prioritize vulnerabilities based on a thorough business impact assessment. This involves identifying which systems are most critical to your business operations and data integrity. |
| Avoid common vulnerability prioritization pitfalls | Several vulnerability management antipatterns, such as overreliance on automatic scanning tools, can reduce the effectiveness of vulnerability prioritization. |
| Patch availability and viability | Consider the availability and viability of patches for identified vulnerabilities. |
| Compliance and regulatory requirements | Consider any compliance or regulatory requirements that particular vulnerabilities might impact. Prioritizing vulnerabilities that affect compliance can help avoid legal and financial repercussions. |
| Historical data and trend analysis | Utilize historical data and trend analysis to predict which vulnerabilities are more likely to be exploited in your specific environment. |
How to prioritize vulnerabilities: Seven essential practices
Incorporating frameworks such as the Exploit Prediction Scoring System (EPSS) and the Common Vulnerability Scoring System (CVSS) into our insights, the sections below will offer a refined lens through which cybersecurity professionals can evaluate and act on vulnerabilities. These tools are pivotal in moving beyond a one-dimensional approach to security, allowing for a nuanced assessment that considers the potential impact of a vulnerability and its likelihood of exploitation.
With that in mind, let’s explore seven essential practices for vulnerability prioritization that can help organizations take a pragmatic approach to risk prioritization. For each practice, we’ll include strategies, impact, and a real-world example to help cybersecurity professionals take a practical approach to vulnerability prioritization.
Exploit availability analysis
Distinguishing between theoretical vulnerabilities and those with active exploits is critical for prioritizing cybersecurity efforts. Exploit availability analysis identifies vulnerabilities that threat actors have weaponized and can exploit in the real world, highlighting those that pose a realistic risk.
Strategies for monitoring and assessing exploit availability
Cybersecurity teams employ several strategies to monitor exploit availability effectively:
- Subscribing to threat intelligence feeds that provide up-to-date information on new exploits.
- Using vulnerability databases integrated with the KEV system to track exploit developments.
- Leveraging platforms with real-time alerts on newly discovered exploits.
- Utilizing the CISA Known Exploited Vulnerabilities (KEV) Database: As a vendor-neutral resource, the CISA KEV database is invaluable for checking if an exploit has been observed in the wild.
Impact of exploit availability on prioritization decisions
The availability of an exploit significantly impacts prioritization decisions. Vulnerabilities with known exploits are prioritized for immediate remediation, as their exploitation can directly harm an organization’s digital assets and reputation. This approach ensures that resources are allocated efficiently, first focusing on the most pressing threats.
Generative AI significantly enhances risk-based vulnerability prioritization, a method at the core of Paladin Cloud’s product suite. This technology automates the evaluation of security alerts across various tools, scoring and ranking them to spotlight the top 10 vulnerabilities that demand immediate attention. Such precision allows organizations to strategically focus their remediation efforts, optimizing resource allocation and bolstering defense mechanisms against the most critical threats. By correlating and aggregating alerts, Paladin Cloud’s approach exemplifies the practical application of generative AI in streamlining cybersecurity workflows, ensuring that teams can address vulnerabilities with the highest risk impact first.
Real-world example
A notable example of exploit availability influencing prioritization was the WannaCry ransomware attack. WannaCry exploited the EternalBlue vulnerability, for which a patch had been available for two months before the attack. Despite this, many organizations had not applied the patch, leading to widespread damage. This incident underscores the importance of prioritizing vulnerabilities with available exploits, especially when patches are available. Visit WannaCry incident and its implications for exploit prioritization for more information.
Attack vector specificity
Understanding the specific conditions under which a vulnerability can be exploited is essential for refining vulnerability prioritization. Attack vector specificity involves:
- Evaluating how an attacker can exploit a given vulnerability
- Considering physical access
- Network access
- Social engineering needs
Given the specific context of an organization’s security posture, this analysis helps identify vulnerabilities that are theoretically exploitable and practically feasible for attackers.
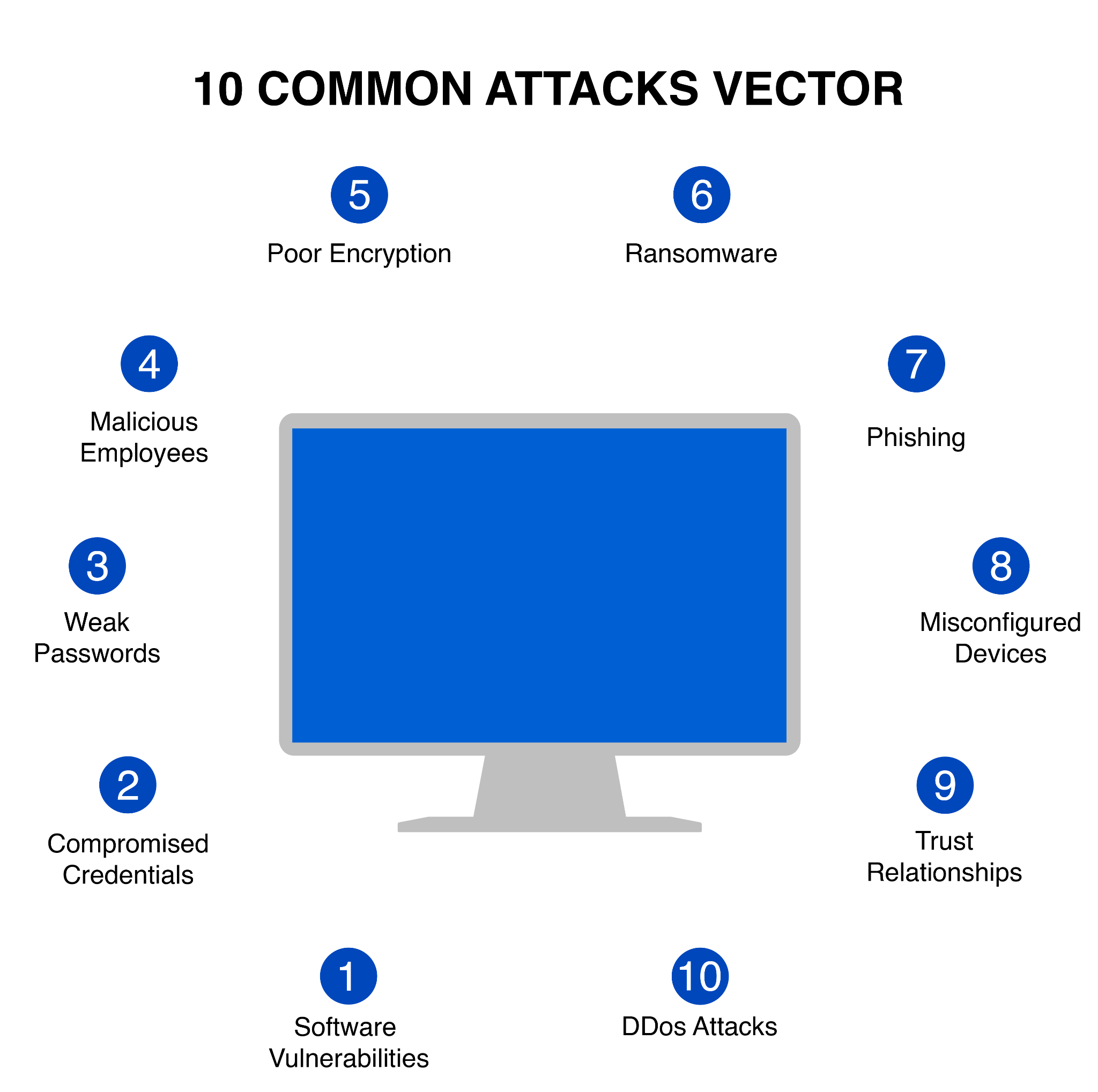
10 examples of common attack vectors. (Source)
Strategies for evaluating attack vector specificity
To accurately assess attack vector specificity, cybersecurity teams can:
- Conduct thorough assessments of their digital and physical security measures to understand potential exploitation paths.
- Utilize attack simulation tools that help identify exploitable vulnerabilities based on the current security environment.
- Engage in regular penetration testing to uncover vulnerabilities that could be exploited through specific attack vectors.
Impact of attack vector specificity on prioritization decisions
The specificity of an attack vector directly influences how vulnerabilities are prioritized. Vulnerabilities are exploitable through more accessible vectors, such as remotely without authentication, and are prioritized over those requiring physical access or high-level privileges. This prioritization ensures that defenses are concentrated on preventing the most likely and impactful exploitation scenarios.
Application Security in Vulnerability Prioritization
Application security plays a crucial role in the broader context of vulnerability management, focusing on protecting software applications from threats throughout the entire application lifecycle. In today’s agile and DevOps-driven environments, integrating security directly into the development process, known as DevSecOps, has become essential. This integration helps identify and remediate vulnerabilities in application code, dependencies, and third-party components early, reducing the attack surface. To keep an application safe, you need to use a mix of static application security testing (SAST), dynamic application security testing (DAST), and software composition analysis (SCA) tools to find and rank vulnerabilities based on how they might affect the application and the data it handles.
Cloud Security and Vulnerability Management
As organizations increasingly migrate to cloud environments, cloud security becomes an integral aspect of vulnerability management. Cloud security encompasses a range of practices and technologies designed to protect cloud computing environments against both internal and external cybersecurity threats. Effective cloud security and vulnerability management involve understanding the shared responsibility model, where security responsibilities are divided between the cloud service provider and the organization. Organizations must prioritize vulnerabilities within their cloud configurations, services, and containers to prevent unauthorized access and data breaches. Tools that provide cloud security posture management (CSPM) and container security solutions are vital for identifying misconfigurations, compliance violations, and vulnerabilities specific to cloud environments.
Real-world example
An illustrative case of attack vector specificity impacting prioritization is the discovery of vulnerabilities in VPN software. For instance, the CVE-2019-11510 vulnerability in Pulse Secure VPN allowed unauthenticated remote attackers to access files on the VPN server. Given the remote exploitability and the high potential impact, organizations prioritized patching this vulnerability to prevent unauthorized access and data breaches. Visit Pulse Secure VPN vulnerability and its implications for further information.
Privilege requirement assessment
Understanding the privilege level required to exploit a vulnerability is a cornerstone of an effective cybersecurity strategy. This assessment helps distinguish between vulnerabilities that any user could exploit and those that need higher-level administrative privileges. Given that vulnerabilities accessible to attackers with fundamental user rights pose a significant risk, prioritizing these for remediation is essential for enhancing system security.
Strategies for evaluating privilege requirements
In the context of evaluating privilege requirements, cybersecurity professionals can adopt several strategies:
- Conducting in-depth analysis of vulnerability disclosures to understand the nature of required privileges for exploitation.
- Utilizing advanced security assessment tools that simulate attack paths, determining whether a vulnerability can be exploited with limited user rights.
- Regularly review user privileges and apply the least privilege principle to minimize potential attack surfaces.
Integrating AI and expert systems in assessing vulnerabilities can significantly streamline this process, offering a more nuanced understanding of each vulnerability’s exploitability based on privilege requirements. Sophisticated tools that incorporate both artificial intelligence and expert cybersecurity insights can enhance the precision of these assessments.
Impact of privilege requirement on prioritization decisions
The level of privilege required for exploitation directly influences the prioritization of vulnerabilities. Those that can be exploited by an attacker with standard user privileges are typically addressed first, as they are accessible to a broader array of potential attackers and can lead to more severe security breaches. This prioritization strategy is crucial for directing remediation efforts toward vulnerabilities that pose the most significant immediate risk to organizational security.
Real-world example
An example of the critical role of privilege requirement assessment in vulnerability management is the exploitation of the CVE-2017-11882 vulnerability in Microsoft Office. This vulnerability allowed attackers to execute code remotely on a target system without requiring administrative privileges, making it a high-priority threat for organizations worldwide. The incident highlights the importance of quickly identifying and mitigating vulnerabilities that can be exploited with minimal privileges, underscoring the need for a sophisticated approach to vulnerability prioritization.
Incorporating advanced analytical tools and methodologies into the vulnerability management process can aid in accurately assessing and prioritizing vulnerabilities based on their privilege requirements, ultimately strengthening an organization’s cybersecurity posture.
Business Impact Assessment (BIA) integration with DSPM
Integrating Business Impact Assessment (BIA) with Data Security Posture Management (DSPM) tools like Big ID and Cyera revolutionizes vulnerability prioritization by mapping sensitive data to vulnerable assets. This approach identifies which systems are critical to business operations. It highlights the nature of the data at risk, elevating the prioritization process by factoring in data sensitivity and regulatory compliance implications.
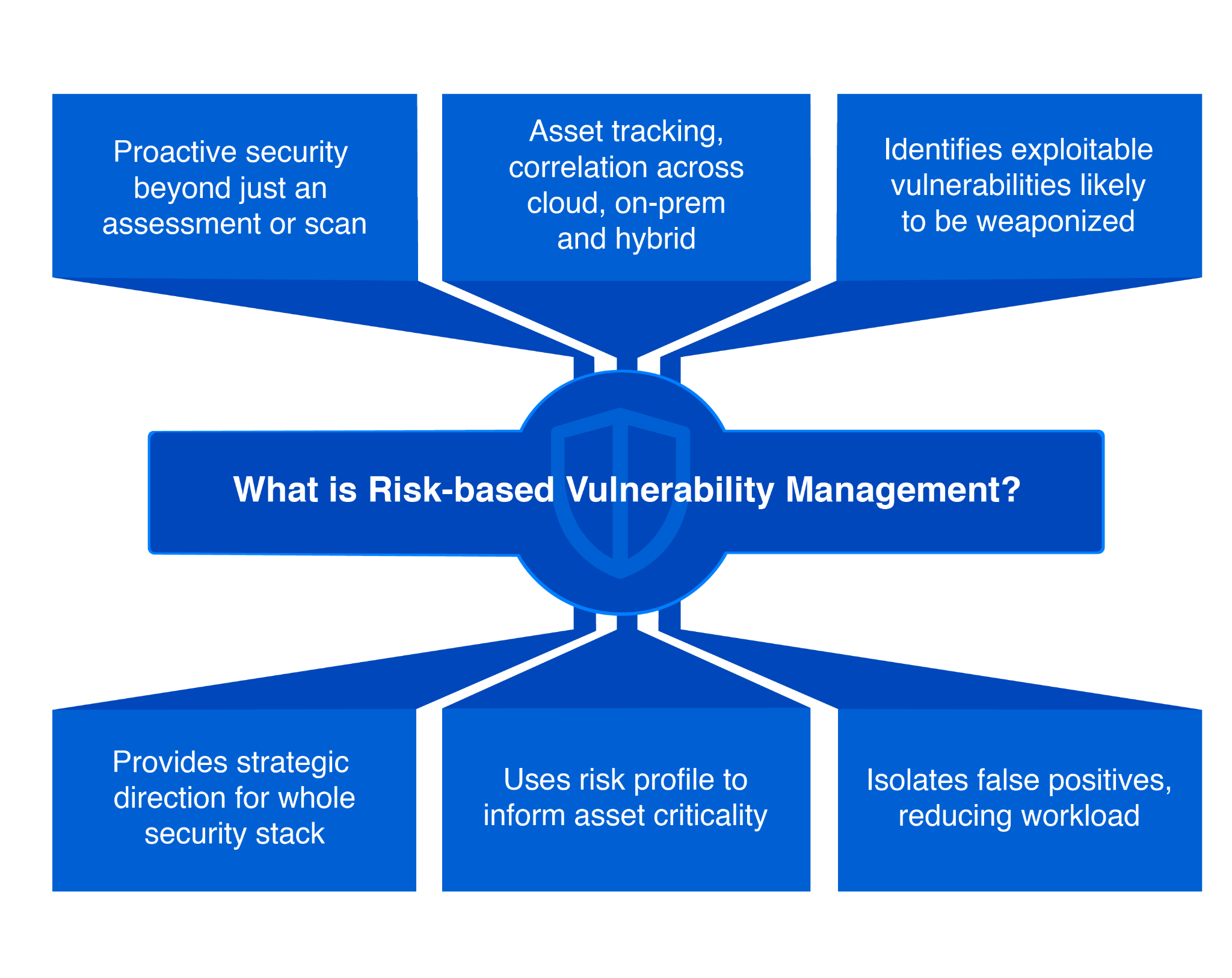
Graphic explaining some of the components of risk-based vulnerability management. (Source)
Risk-based vulnerability management
Risk-Based Vulnerability Management (RBVM) represents a strategic approach to cybersecurity that prioritizes threats based on their potential impact and likelihood of exploitation. It’s a proactive methodology beyond mere assessments or scans to view an organization’s security posture comprehensively. RBVM tracks assets across various environments, such as cloud, on-premises, and hybrid, while identifying and prioritizing exploitable vulnerabilities that attackers could weaponize. This process helps segregate false positives to reduce unnecessary workload, informs the strategic direction of the entire security stack, and uses a detailed risk profile to underline the criticality of different assets. Essentially, while RBVM focuses on the application security first platforms, its counterpart, Unified Vulnerability Management (UVM), is gaining traction for integrating additional data points like Data Security Posture Management (DSPM) and Cloud Security Posture Management (CSPM), offering a more unified approach. Any mention of RBVM must be contextualized within the larger security framework to ensure a comprehensive understanding of its role and importance.
Strategies for BIA and DSPM integration in vulnerability management
To harness the full potential of integrating BIA with DSPM tools, cybersecurity teams can:
- Leverage DSPM solutions to gain visibility into where sensitive or regulated data resides within the IT ecosystem.
- Align BIA processes with DSPM findings to assess the business impact of vulnerabilities on assets containing critical data.
- Prioritize vulnerabilities based on sensitive data, focusing remediation efforts on protecting high-value data assets.
This integration enables a more informed prioritization strategy, ensuring that vulnerabilities posing the most significant risk to sensitive data and critical business functions are addressed with urgency.
Impact of BIA and DSPM integration on prioritization decisions
The synergy between the BIA and DSPM tools significantly enhances vulnerability prioritization by clearly showing the potential business and compliance impacts of data breaches. This method allows organizations to prioritize vulnerabilities based on technical severity and the value and sensitivity of the data at risk, ensuring a data-centric approach to cybersecurity.
Embracing a Holistic Approach to Security
In today’s interconnected digital landscape, taking a holistic approach to security is more crucial than ever. Cybersecurity is no longer confined to isolated domains; it spans across application security (AppSec), cloud security posture management (CSPM), data security posture management (DSPM), and traditional vulnerability management tools. The ability to correlate findings across these areas is essential for a comprehensive understanding of an organization’s security posture. By integrating insights from various security domains, organizations can identify and prioritize risks more effectively, ensuring that no critical vulnerability is overlooked. This holistic view enables security teams to strategize remediation efforts that address the most pressing threats first, based on their potential impact across the entire digital ecosystem.
Paladin Cloud: A Unified Platform for Vulnerability Management
Paladin Cloud’s AI-powered prioritization engine exemplifies the power of this holistic approach. By leveraging advanced AI to analyze and correlate security data from AppSec, CSPM, DSPM, and other vulnerability management tools, Paladin Cloud provides a unified view of an organization’s security risks. This integration allows for sophisticated risk scoring, identifying not just isolated vulnerabilities but highlighting how they interact and compound across different domains. As a result, Paladin Cloud enables organizations to prioritize their response efforts more effectively, focusing on vulnerabilities that, if exploited, could have the most detrimental impact on their operations. Businesses now have access to Paladin Cloud, a comprehensive vulnerability management platform that reduces the complexity of contemporary cybersecurity and guarantees that every decision is based on a complete understanding of security risks.
Real-world example
Integrating BIA with DSPM tools is particularly relevant in compliance with regulations such as GDPR and CCPA, where data breaches can have significant legal and financial repercussions. For example, an organization using DSPM to identify assets storing personally identifiable information (PII) could prioritize patching vulnerabilities on these systems to mitigate the risk of data breaches and comply with data protection regulations.
By integrating BIA with DSPM solutions, organizations can achieve a more nuanced and practical approach to vulnerability prioritization. This strategy protects against cybersecurity threats and safeguards sensitive data, aligning cybersecurity efforts with broader business and compliance objectives.
Patch availability and viability
In the vulnerability management landscape, patches’ availability and viability are crucial in determining prioritization and remediation strategies. Patch availability refers to whether a security fix is accessible for a known vulnerability, while viability concerns the patch’s applicability and potential impact on existing systems without introducing new issues.
Strategies for assessing patch availability and viability
- Regular Monitoring for Patch Releases: Stay informed about new patches through official vendor announcements and cybersecurity news feeds. Tools that aggregate and alert for new patch releases can streamline this process.
- Testing Patches in a Controlled Environment: Before widespread deployment, assess patches in a test environment that mirrors live systems to evaluate their impact and effectiveness. This step is crucial to ensuring the patch does not adversely affect system functionality or introduce new vulnerabilities.
- Prioritizing Patches Based on Risk: Evaluate the risk associated with the vulnerability and the patch’s potential to mitigate this risk effectively. Prioritization should consider the severity of the vulnerability, its exploitability, and the criticality of the affected system to business operations.
- Leveraging Automated Patch Management Solutions: Automated tools can help manage patching by scheduling and deploying patches based on predefined policies, significantly reducing the manual workload and ensuring timely application.
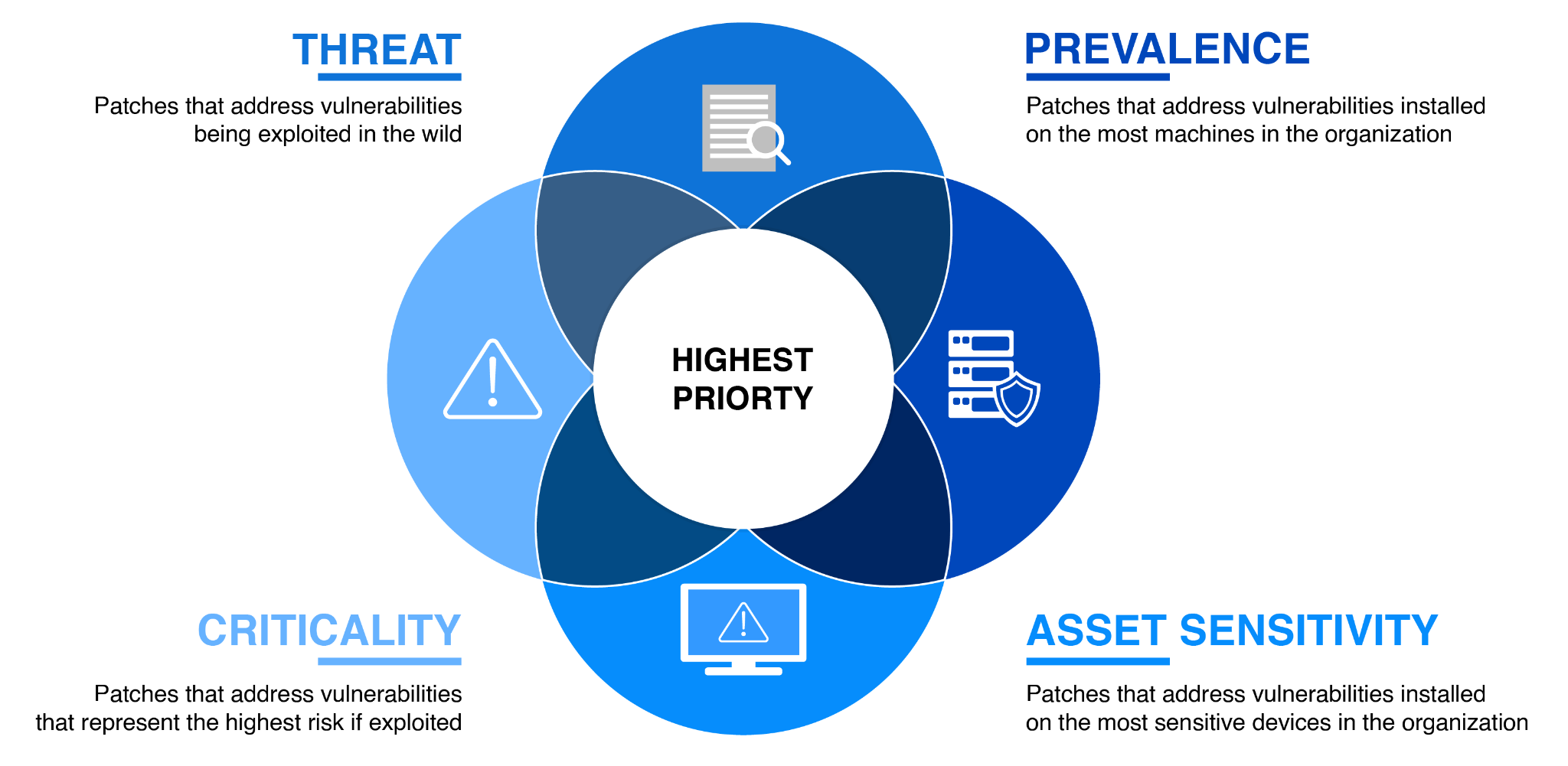
Graphic showing some of the criteria for prioritizing patches for deployment (Source)
Challenges in patch management
- Compatibility Issues: Patches may not be compatible with all systems or applications, potentially leading to operational disruptions.
- Delayed Patch Availability: Vendors may not immediately release patches for newly discovered vulnerabilities, leaving systems exposed.
- Resource Constraints: Limited IT resources can hinder the timely testing and deployment of patches across all affected systems.
Integrating technology for effective patch management
Unified vulnerability management platforms can significantly enhance the patch management process by offering features that automate the monitoring and deployment of patches. By integrating patch availability and viability assessments into the broader vulnerability management strategy, it helps ensure that patches are applied promptly and effectively, minimizing exposure to known vulnerabilities. Additionally, such platforms can provide insights into the potential business impact of using or delaying a patch, allowing for more informed decision-making.
Real-world example
A notable example of patch management’s critical role is the response to the Apache Log4j vulnerability (CVE-2021-44228). Organizations that quickly assessed the availability and viability of patches could mitigate the risk more effectively, demonstrating the importance of a proactive and informed approach to patch management.
Compliance and regulatory requirements
Compliance and regulatory requirements play a pivotal role in shaping vulnerability management strategies. Organizations must navigate a complex landscape of industry standards and legal mandates, ensuring their cybersecurity practices protect against threats and adhere to regulatory expectations. This alignment is crucial for avoiding legal penalties, maintaining customer trust, and safeguarding the organization’s reputation.
Strategies for aligning vulnerability management with compliance
- Understanding Regulatory Landscapes: Stay informed about the compliance requirements relevant to your industry, such as GDPR for data protection, HIPAA for healthcare information, or PCI DSS for payment card security. This knowledge forms the foundation of a compliance-aligned vulnerability management strategy.
- Mapping Vulnerabilities to Compliance Standards: Identify how specific vulnerabilities may impact compliance with regulatory standards. This involves assessing the potential for data breaches, unauthorized access, or other security incidents that could violate regulatory obligations.
- Integrating Compliance into Risk Assessments: Incorporate compliance considerations into your vulnerability risk assessment framework. This approach ensures that vulnerabilities posing a significant compliance risk are prioritized for remediation.
- Documenting and Reporting for Compliance: Maintain comprehensive records of vulnerability assessments, remediation actions, and compliance efforts. Documentation is critical for demonstrating due diligence and compliance in audits and regulatory reviews.
Challenges in balancing security and compliance
- Evolving Regulatory Requirements: Keeping pace with changes in compliance standards can be challenging, requiring ongoing education and adaptation of cybersecurity strategies.
- Resource Allocation: Balancing the resources needed for compliance with those required for broader cybersecurity initiatives can strain IT budgets and personnel.
- Overemphasis on Compliance: Focusing too narrowly on compliance can lead to a checkbox mentality where meeting the minimum requirements takes precedence over addressing broader security risks.
Leveraging technology for compliance-driven vulnerability management
Technological solutions, such as those offered by Paladin Cloud, can streamline the integration of compliance and regulatory requirements into vulnerability management processes. These platforms can automate the tracking and reporting of compliance-related vulnerabilities, offer insights into the compliance implications of security gaps, and guide remediation strategies that align with security best practices and regulatory mandates.
Real-world example
An example of the critical intersection between compliance and vulnerability management is the response to vulnerabilities affecting financial data processing systems. Organizations subject to PCI DSS must swiftly address such vulnerabilities to prevent unauthorized access to cardholder data, demonstrating the importance of a compliance-informed approach to cybersecurity.
Historical data and trend analysis
Historical data and trend analysis are invaluable cybersecurity tools that enable organizations to anticipate potential vulnerabilities and respond proactively. Cybersecurity teams can identify patterns and trends indicating future threats by analyzing past security incidents and vulnerability exploits. This foresight allows for prioritizing vulnerabilities that are more likely to be exploited based on historical evidence.
Strategies for implementing historical data and trend analysis
- Collecting and analyzing historical vulnerability data: Maintain a comprehensive database of past vulnerabilities and their exploitation patterns. This data should include information on the types of vulnerabilities most frequently exploited, the sectors or types of applications most affected, and the time taken to develop and deploy exploits.
- Leveraging threat intelligence platforms: Utilize threat intelligence platforms that provide access to a wide range of historical data on cybersecurity threats. These platforms can offer insights into the evolving tactics, techniques, and procedures (TTPs) used by threat actors, helping to predict potential future attacks.
- Applying predictive analytics: Employ predictive analytics tools to analyze historical vulnerability data and forecast future trends. This can help identify vulnerabilities that, while not yet exploited, possess characteristics similar to those targeted in the past.
Challenges in utilizing historical data and trend analysis
- Data overload: The sheer volume of data can be overwhelming, making it easier to extract actionable insights with the right tools and expertise.
- Rapidly evolving threat landscape: The fast-paced evolution of cyber threats means that historical data may quickly become outdated, requiring continuous updates and analysis.
- Bias towards known vulnerabilities: There’s a risk of focusing too heavily on vulnerabilities that have been exploited in the past, potentially overlooking emerging threats that have not yet manifested in historical data.
Enhancing vulnerability management with historical insights
Incorporating historical data and trend analysis into vulnerability management processes can significantly enhance an organization’s ability to address threats preemptively. Vulnerability management platforms can facilitate this integration by offering advanced analytics and threat intelligence capabilities. These tools can sift through vast amounts of historical data, identify relevant trends, and provide recommendations for prioritizing vulnerabilities based on past incidents and emerging patterns.
Real-world example
A notable example of the practical application of historical data and trend analysis in cybersecurity is identifying and mitigating ransomware threats. By analyzing trends in ransomware attacks, organizations can identify common vulnerabilities that have been exploited in past incidents, such as unpatched software or insecure remote access protocols, and prioritize these areas for immediate remediation.
How to avoid common vulnerability prioritization pitfalls
Effective vulnerability prioritization is essential for maintaining robust cybersecurity defenses. However, several challenges and pitfalls can undermine these efforts, leading to misallocated resources, overlooked vulnerabilities, and increased risk. Recognizing and addressing these challenges is crucial for any cybersecurity strategy.
- Over-reliance on automated scanning tools: While automated vulnerability scanners are invaluable for identifying potential vulnerabilities, relying solely on these tools without manual verification can fail to contextualize the findings.
- Ignoring business context: Not all vulnerabilities are created equal, and their impact can vary significantly depending on the business context.
- Underestimating internal threats: External threats often receive the most attention in vulnerability management programs. However, malicious or accidental internal threats can exploit vulnerabilities just as effectively.
- Patch management challenges: The rush to patch vulnerabilities can sometimes lead to disruptions in business operations or the introduction of new vulnerabilities.
- Data overload: The sheer volume of vulnerabilities identified can be overwhelming, leading to analysis paralysis.
- Lack of expertise: Properly assessing and prioritizing vulnerabilities requires a deep understanding of cybersecurity principles and the latest threat landscape.
- Compliance-driven focus: While compliance with regulatory standards is crucial, allowing compliance requirements to dictate vulnerability prioritization can lead to a security posture that meets regulatory standards but is otherwise inadequate.
Strategies to overcome vulnerability management pitfalls
To navigate the pitfalls of vulnerability prioritization effectively, organizations can adopt several strategic approaches, leveraging advanced technology, tooling, and integrations provided by platforms like Paladin Cloud:
- Use AI and expert insights for enhanced analysis: Counter the limitations of automated scanning tools by integrating solutions that combine AI-driven analysis with human expertise.
- Conduct business impact-centric prioritization: Utilize tools that directly integrate Business Impact Assessments (BIA) into the vulnerability management process.
- Achieve comprehensive visibility for internal and external threats: Adopt platforms that offer visibility into internal and external threat landscapes.
- Be sophisticated with patch management: Implement a nuanced patch management strategy with the help of platforms that facilitate the careful deployment and testing of patches.
- Use modern tooling for efficient management of vulnerability overload: Leverage platforms that prioritize vulnerabilities based on real-world risk, business impact, and compliance requirements.
- Augment team expertise: Enhance your team’s capabilities with continuous training and support from platforms that offer up-to-date threat intelligence and recommendations.
- Balance compliance and security: Utilize tools that help maintain regulatory compliance without compromising a comprehensive risk-based security strategy.
Last thoughts on how to prioritize vulnerabilities
In business, a growing need to prioritize vulnerabilities cannot be overstated. Most organizations must face a landscape rife with potential threats where there simply aren’t enough financial and operational resources to address every vulnerability. For example, The Red Hat Product Security Risk Report 2022 identified 1,656 vulnerabilities. If we assume a cost of $1,000 per fix, it would cost upwards of $1.6 million to address all of them. In contrast, a focused strategy targeting only those vulnerabilities deemed critical, necessary, or already exploited as ‘risky’ could reduce cost to approximately $295,000 while still drastically reducing risk. This strategic prioritization not only represents a significant cost saving but also ensures that resources are allocated where they can substantially impact an organization’s security posture.
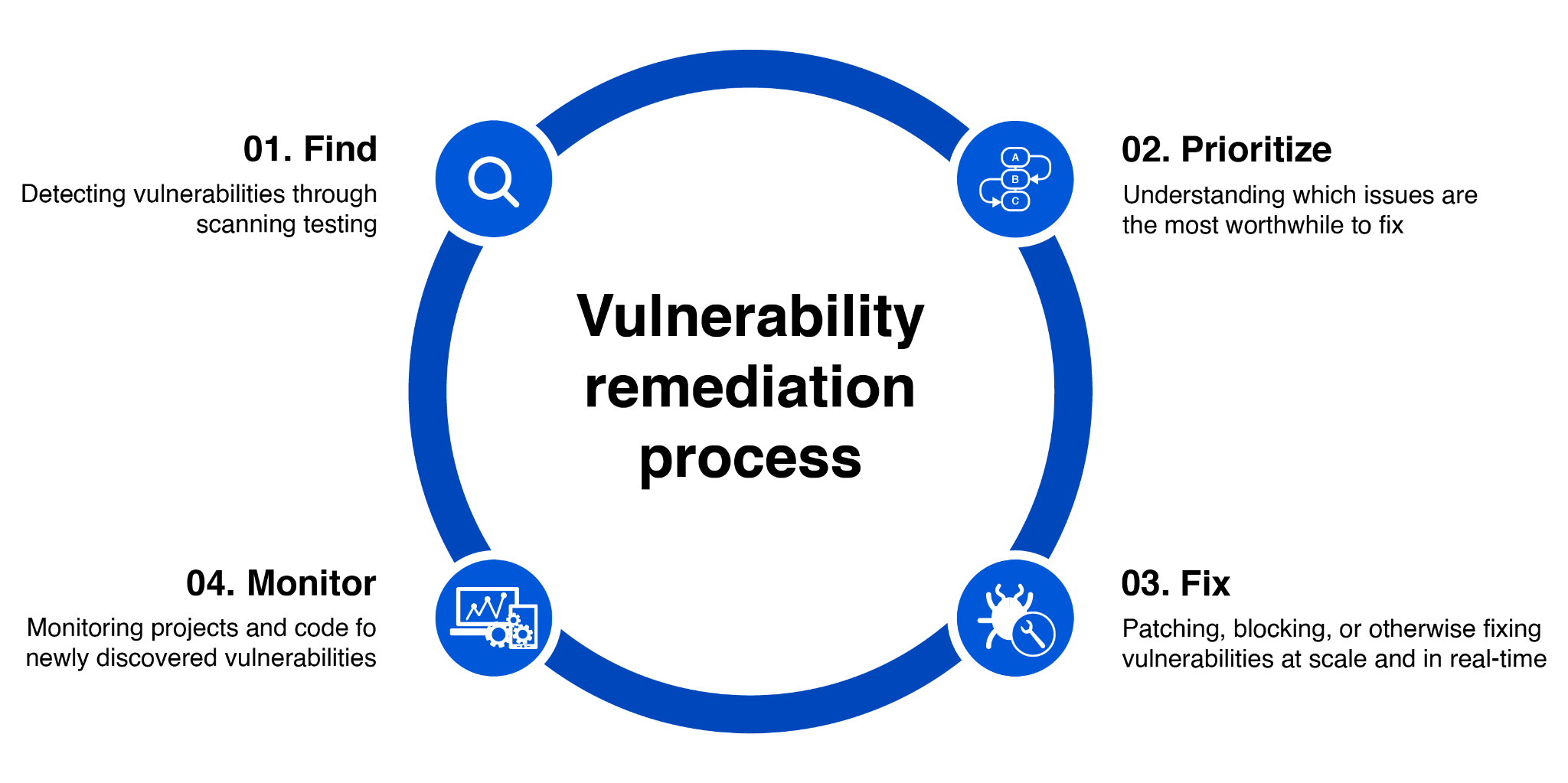
Graphics showing a simple vulnerability remediation process. (Source)
The essence of vulnerability prioritization lies in its ability to guide organizations in deploying their defenses more judiciously. It’s about making informed decisions that balance the cost of remediation against the potential risk of exploitation. In this context, Paladin Cloud’s AI-powered prioritization engine emerges as a critical tool for businesses to navigate these complex decisions. Paladin Cloud’s engine uses Generative AI to help generate risk scores across existing security tools by integrating and correlating individual alerts and incorporating the considerations highlighted throughout this article: exploit availability, attack vector specificity, privilege requirements, business impact, compliance needs, and historical trends. These scores empower organizations to identify and focus on ‘risky’ vulnerabilities, ensuring that investment in cybersecurity yields the highest possible return regarding risk reduction.
Businesses can transcend conventional, frequently reactive cybersecurity measures thanks to this strategic approach to vulnerability management. Instead, organizations can adopt a proactive stance, prioritizing and addressing vulnerabilities that pose the most significant threat to their operations and data integrity. By doing so, they safeguard their digital assets and customer trust and optimize their cybersecurity investments, achieving a more secure and resilient digital environment.